How do I enable IPsec IKEv2 on ASA?
To enable IPsec IKEv2, you must configure the IKEv2 settings on the ASA and also configure IKEv2 as the primary protocol in the client profile. The IKEv2enabled profile must be deployed to the endpoint computer, otherwise the client attempts to connect using SSL. !
How does IPsec work on the Cisco ASA?
IPsec can be configured on the Cisco Adaptive Security Appliance (ASA) to secure data going between LAN devices (LAN-to-LAN) and between a LAN device and an IPsec client (e.g., Windows, Linux, or Mac clients). Sean Wilkins goes over the high-level basics of how IPsec operates and how it can be configured on a Cisco ASA.
How to add a trusted root certificate to Asa?
So to really solve this issue, you have to create an own CA and import the root certificate of that CA as trusted root certificate on the host where the anyconnect client runs. Then you have to enroll the trustpoint configured on the ASA with "enroll terminal", sign the displayed csr with your trusted CA and import that certificate to your ASA.
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is dynamic crypto map?
Dynamic crypto maps define policy templates in which not all the parameters are configured. This lets the ASA receive connections from peers that have unknown IP addresses, such as remote access clients.
What is Cisco AnyConnect Secure Mobility Solution?
The Cisco AnyConnect Secure Mobility Solution provides a comprehensive, highly secure enterprise mobility solution. the Cisco AnyConnect Secure Mobility Solution continues to lead with next-generation security and encryption, including support for the Suite B set of cryptographic algorithms, and support for IPv6 networks. More importantly, it adapts its tunneling protocol to the most efficient method. AnyConnect client can be used to connect both SSL VPN as well as IKEv2 IPSec VPN. In this document we will see how to configure only IKEv2 IPSec VPN.
What is active/active failover?
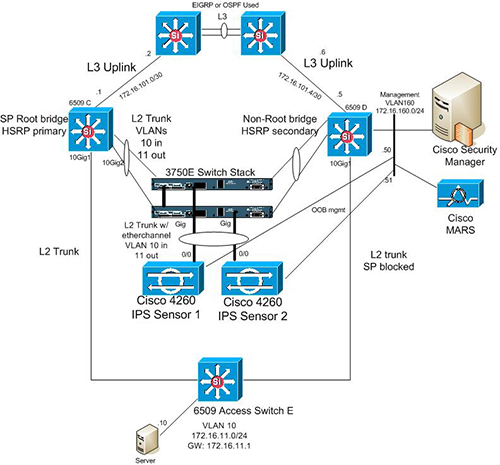
Active/Active failover is only available to security appliances in multiple context mode. In an Active/Active failover configuration, both security appliances can pass network traffic. In Active/Active failover, you divide the security contexts on the security appliance into failover groups. A failover group is simply a logical group of one or more security contexts. You can create a maximum of two failover groups on the security appliance. The admin context is always a member of failover group 1. Any unassigned security contexts are also members of failover group 1 by default. We have already seen the configuration for Active/Standby failover in the previous article. This article focuses on how to configure an Active/Active Failover configuration on ASA Security Appliance. Network Diagram (Physical Topology)
Who is the target audience for this informational advisory?
The target audiences for this informational advisory are customers who have deployed Cisco ASA/FTD devices as remote access VPN endpoints and are performing any client-based certificate authentication.
Is Cisco Product Security Incident Response Team aware of public announcements?
The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability that is described in this advisory.
Can a trustpoint be used for VPN?
When a new certificate is imported to the configuration, the default settings for the trustpoint usage are for ipsec-client and ssl-client validation, so by default, that trustpoint can be used to authenticate VPN users. If the trustpoint's intended use is only as a server identity certificate and the corresponding certificate authority trust should not be used for VPN validation, the ASA/FTD administrator has to configure the device as such using the validation-usage command.
Introduction
Background Information
- AnyConnect Secure Mobility Client Considerations
The native Windows IKEv2 client does not support split tunnel (there are no CONF REPLY attributes which could be accepted by the Windows 7 client), so the only possible policy with the Microsoft client is to tunnel all traffic (0/0 traffic selectors). If there is a need for a specific split t…
Configure
- Note: Use the Command Lookup Tool (registeredcustomers only) in order to obtain more information on the commands used in this section.
Verify
- Use this section to confirm that your configuration works properly. The Output Interpreter Tool (registered customers only) supports certain show commands. Use the Output Interpreter Tool in order to view an analysis of showcommand output.
Related Information