What VPN license is used with IKEv1 and IPsec?
IPsec remote access VPN using IKEv1 and IPsec site-to-site VPN using IKEv1 or IKEv2 uses the Other VPN license that comes with the base license. See Cisco ASA Series Feature Licenses for maximum values per model.
How do I set up VPN on a Cisco ASA device?
Set up VPN on a Cisco ASA device. To set up a Cisco ASA device with a Chrome OS-compatible VPN, use the Cisco Adaptive Security Device Manager (ASDM) tool. Note: These instructions assume that you're using ASDM version 6.4. Step 1: Set up your VPN settings. Open ASDM. Go to Wizards VPN Wizards IPsec (IKEv1) Remote Access VPN Wizard.
How to troubleshoot IPsec IKEv1 tunnel negotiation on an ASA firewall?
In order to troubleshoot IPSec IKEv1 tunnel negotiation on an ASA firewall, you can use these debug commands: Note: If the number of VPN tunnels on the ASA is significant, the debug crypto condition peer A.B.C.D command should be used before you enable the debugs in order to limit the debug outputs to include only the specified peer.
What is IKEv1 protocol used for?
IKE is a protocol that is used to set up the keys for negotiating the IPsec VPN. IPsec uses IKE for creating a virtual tunnel between two sites IKE has 2 versions. We will use IKEV1 for IPSEC VPN. We have two branches (Branch 1 and Branch 2) and we have to protect traffic over the ISP of branches.

How do I access my Cisco ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
What is remote access VPN Cisco?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network such as the Internet. Remote access VPNs for IPsec IKEv2. 8.4(1) Added IPsec IKEv2 support for the AnyConnect Secure Mobility Client.
Does ASA support route based VPN?
The ASA supports a logical interface called Virtual Tunnel Interface (VTI). As an alternative to policy based VPN, a VPN tunnel can be created between peers with Virtual Tunnel Interfaces configured. This supports route based VPN with IPsec profiles attached to the end of each tunnel.
What VPN types are supported by ASA?
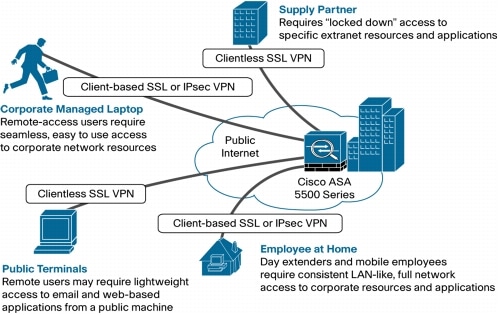
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
How does a remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What is the difference between route-based and policy based VPN?
In a policy-based VPN configuration, the action must be permit and must include a tunnel. Route-based VPNs support the exchange of dynamic routing information through VPN tunnels. You can enable an instance of a dynamic routing protocol, such as OSPF, on an st0 interface that is bound to a VPN tunnel.
What is route-based VPN?
A route-based VPN is a configuration in which an IPsec VPN tunnel created between two end points is referenced by a route that determines which traffic is sent through the tunnel based on a destination IP address.
Does FTD support route-based VPN?
In November 2020 Cisco released the Firepower Threat Defence (FTD) and Firepower Management Centre (FMC) version 6.7. Supported from this version is the long-awaited Virtual Tunnel Interface (VTI) for route-based site-to-site VPNs.
What are the four types of VPN?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs....How Personal VPNs WorkInstall software from your VPN service provider onto your device. ... Connect to a server in your VPN provider's network.More items...•
What are 3 types of VPN tunnels?
We'll look at three of the most common: IPsec tunnels, Dynamic multi point VPNs, and MPLS-based L3VPNs.IPsec Tunnels. In principle, a network-based VPN tunnel is no different from a client-based IPsec tunnel. ... Dynamic Multi point VPN (DMVPN) ... MPLS-based L3VPN.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
Where to enable IKEv1?
You must enable IKEv1 on the interface that terminates the VPN tunnel. Typically, this is the outside (or public) interface. In order to enable IKEv1, enter the crypto ikev1 enable <interface-name> command in global configuration mode: crypto ikev1 enable outside.
What is IKEv1 policy match?
Note: An IKEv1 policy match exists when both of the policies from the two peers contain the same authentication, encryption, hash, and Diffie-Hellman parameter values. For IKEv1, the remote peer policy must also specify a lifetime less than or equal to the lifetime in the policy that the initiator sends. If the lifetimes are not identical, then the ASA uses the shorter lifetime.
What is IKEv1 transform set?
An IKEv1 transform set is a combination of security protocols and algorithms that define the way that the ASA protects data. During IPSec Security Association (SA) negotiations, the peers must identify a transform set or proposal that is the same for both of the peers. The ASA then applies the matched transform set or proposal in order to create an SA that protects data flows in the access list for that crypto map.
How to check if IKEv1 is up?
In order to verify whether the IKEv1 Phase 1 is up on the IOS, enter the show crypto isakmp sa command. The expected output is to see the ACTIVE state:
What is the connection profile type for a LAN-to-LAN tunnel?
For a LAN-to-LAN tunnel, the connection profile type is ipsec-l2l. In order to configure the IKEv1 preshared key, enter the tunnel-group ipsec-attributes configuration mode:
What to do if ASA is not configured?
If the ASA interfaces are not configured, ensure that you configure at least the IP addresses, interface names, and security-levels:
What is packet tracer in ASA?
Note: On the ASA, the packet-tracer tool that matches the traffic of interest can be used in order to initiate the IPSec tunnel (such as packet-tracer input inside tcp 10.10.10.10 12345 10.20.10.10 80 detailed for example).
What is Cisco AnyConnect Secure Mobility Solution?
The Cisco AnyConnect Secure Mobility Solution provides a comprehensive, highly secure enterprise mobility solution. the Cisco AnyConnect Secure Mobility Solution continues to lead with next-generation security and encryption, including support for the Suite B set of cryptographic algorithms, and support for IPv6 networks. More importantly, it adapts its tunneling protocol to the most efficient method. In the present scenario, we have to configure Anyconnect SSL remote access VPN for Sales department and Engineering department of a company. Engineering users will have to be provided with access to web server as well as FTP server, while sales users may only have access to the web server.
What is active/active failover?
Active/Active failover is only available to security appliances in multiple context mode. In an Active/Active failover configuration, both security appliances can pass network traffic. In Active/Active failover, you divide the security contexts on the security appliance into failover groups. A failover group is simply a logical group of one or more security contexts. You can create a maximum of two failover groups on the security appliance. The admin context is always a member of failover group 1. Any unassigned security contexts are also members of failover group 1 by default. We have already seen the configuration for Active/Standby failover in the previous article. This article focuses on how to configure an Active/Active Failover configuration on ASA Security Appliance. Network Diagram (Physical Topology)
Does Cisco AnyConnect support SSL VPN?
Even after the release of Cisco AnyConnect Secure Mobility Client which supports SSL VPN in addition to IKEv2 remote-access IPSec VPN, still out there are number of people who use legacy Cisco VPN client to connect IKEv1 remote-access IPSec VPN.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
What happens if a Cisco VPN client has a different preshared key size?
If a Cisco VPN Client with a different preshared key size tries to connect, the client logs an error message indicating it failed to authenticate the peer.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
What is priority in IKE?
Priority uniquely identifies the Internet Key Exchange (IKE) policy and assigns a priority to the policy. Use an integer from 1 to 65,534, with 1 being the highest priority and 65,534 the lowest.
What is IKE (IKEV1 and IKEV2)?
It stands for Internet Key Exchange. IKE is a protocol that is used to set up the keys for negotiating the IPsec VPN. IPsec uses IKE for creating a virtual tunnel between two sites
What is IPsec?
IPsec VPN (internet protocol security) is a protocol or method to encrypt the traffic between two branches or sites. It is used to secure the traffic over an untrusted network, and we can understand by its name that it provides security of INSIDE network IPs.
What is a VPN connection profile?
In general speak a connection profile defines the properties of how the VPN will run and what access will be permitted. It is called as such in the ASDM but through the CLI we need to configure a tunnel-group
What is encryption domain?
The encryption domain specifies traffic that should be encapsulated within IPSec prior to leaving the external interface. Any traffic not matching this ACL will be sent out the interface in plain text, assuming it does not match any other configured VPNs.
How many interfaces does an ASA have?
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
What is VPN_POLICY?
The group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
Cisco ASA non-VPN Configurations
The interface configuration is self-explanatory, ASA has two interfaces, one for the user and another one for the Internet. The default route is pointing to the ISP router with a static route. There are two objects, one for the branch user subnet and another one for the HQ webserver subnet.
ASA VPN configurations IKEv1
Please note that if you already have another VPN tunnel then most likely most of the configurations are already done for you. So, please make sure not to change or override them.
ASA VPN configurations IKEv2
I'm going to remove all the IKEv1 related configurations and then re-configure the VPN using IKEv2. The configuration is almost identical to IKEv1.
How to make a VPN on a laptop?
On your desktop, click the wireless network icon. At the bottom of the drop-down, select Open Network Preferences. On the bottom left of the box that appears, click the + sign. In the box that appears: In the "Interface" drop-down, select VPN. In the "VPN Type" drop-down, select L2TP over IPsec. Click Create.
How to open a webpage served by a server behind the firewall?
If the status shows as "Connected," open a new Chrome tab and try to open a webpage served by a server behind the firewall. You can also open a terminal window and use ping/SSH.
How to use pre-shared key?
To use a pre-shared key (passphrase), select Pre-Shared Key-PSK and set the PSK. Click Next. Choose how to authenticate users. (You can assume you're using a local user database, which is the default.) Click Next. Enter at least one username and password, then click Add. Click Next.
