How do I enable IPsec IKEv2 on ASA?
To enable IPsec IKEv2, you must configure the IKEv2 settings on the ASA and also configure IKEv2 as the primary protocol in the client profile. The IKEv2enabled profile must be deployed to the endpoint computer, otherwise the client attempts to connect using SSL. !
How is the IKEv2 session completed?
The IKEv2 session is completed by the ASA, final configuration (configuration reply with values such as an assigned IP address), transform sets, and traffic selectors are pushed to the VPN client. There is currently no specific troubleshooting information available for this configuration.
How to use AnyConnect VPN with Asa?
The remote user will open a web browser, enters the IP address of the ASA and then it will automatically download the anyconnect VPN client and establishes the connection. Here’s the topology that we will use:
What are the security zones for the ASA firewall?
Above we have the ASA firewall with two security zones: inside and outside. The remote user is located somewhere on the outside and wants remote access with the Anyconnect VPN client. R1 on the left side will only be used so that we can test if the remote user has access to the network.
How do I access my Cisco ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
How do I enable IKEv2 on Cisco ASA?
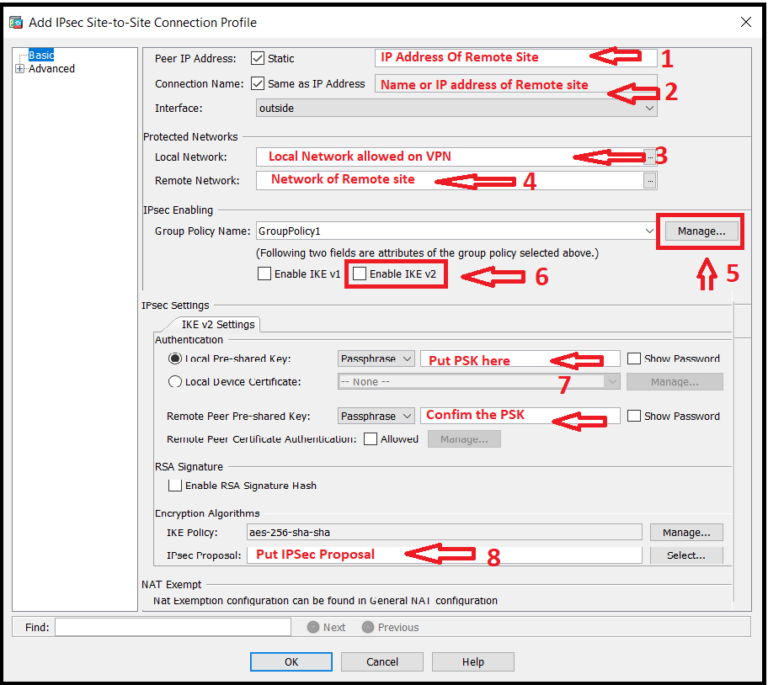
Configure the remote IPsec tunnel pre-shared key or certificate trustpoint. Create a crypto map and match based on the previously created ACL....IPsec IKEv2 Example.1Create and enter IKEv2 policy configuration mode.asa1(config)#crypto ikev2 policy 12Configure an encryption method.asa1(config-ikev2-policy)#encryption aes17 more rows•Nov 15, 2013
Does Cisco ASA support IKEv2?
IKEv2 has been published in RFC 5996 in September 2010 and is fully supported on Cisco ASA firewalls.
What is remote access VPN Cisco?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network such as the Internet. Remote access VPNs for IPsec IKEv2. 8.4(1) Added IPsec IKEv2 support for the AnyConnect Secure Mobility Client.
How do I set up IKEv2?
Use the IKEv2 Setup Wizard(Fireware v12. 3 or higher) Select VPN > Mobile VPN.In the IKEv2 section, select Configure. The Mobile VPN with IKEv2 page appears.(Fireware v12. 2.1 or lower) Select VPN > Mobile VPN with IKEv2. ... Click Run Wizard.Click Next.Type the domain name or IP address for client connections.
How do I enable IKEv2?
To enable IKEv2 on a crypto interface, attach an IKEv2 profile to the crypto map or IPsec profile applied to the interface. You need not enable IKEv1 on individual interfaces because IKEv1 is enabled globally on all interfaces in the router.
How does IKEv2 VPN Work?
How Does IKEv2 Work? Using a Diffie–Hellman key exchange algorithm, the protocol sets up a secure communication channel between your device and the VPN server. IKEv2 then uses that secure communication channel to establish what is called a security association.
Which is better IKEv2 or IPsec?
IPSec is considered secure and reliable, while IKEv2 is extremely fast and stable – IKEV2 offers quick re-connections when switching networks or during sudden drops. Thus, a combination of IKEv2/IPsec forms one of the best VPN protocols that exhibits the advantages of the two.
What is the difference between IKEv1 and IKEv2?
IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). IKEv2 has Built-in NAT-T functionality which improves compatibility between vendors. IKEv2 supports EAP authentication. IKEv2 has the Keep Alive option enabled as default.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Where is Cisco VPN client configuration file?
Hello, in Windows OS the . pcf files is located at C:\Programs files\Cisco Systems\VPN Client\Profiles.
How do I set up AnyConnect on ASA?
Configure AnyConnect ConnectionsConfigure the ASA to Web-Deploy the Client.Enable Permanent Client Installation.Configure DTLS.Prompt Remote Users.Enable AnyConnect Client Profile Downloads.Enable AnyConnect Client Deferred Upgrade.Enable DSCP Preservation.Enable Additional AnyConnect Client Features.More items...•
How do I troubleshoot IKEv2?
Suggestions: Troubleshoot connectivity between Aviatrix gateway and peer VPN router. Verify that both VPN settings use the same IKEv2 version. Verify that all IKEv2/IPsec algorithm parameters (i.e., Authentication/DH Groups/Encryption) match on both VPN configuration.
What ports does IKEv2 use?
IKEv2 uses UDP ports 500 and 4500 for communication.
Which is better IKEv2 or IPsec?
IPSec is considered secure and reliable, while IKEv2 is extremely fast and stable – IKEV2 offers quick re-connections when switching networks or during sudden drops. Thus, a combination of IKEv2/IPsec forms one of the best VPN protocols that exhibits the advantages of the two.
What is the difference between IKEv1 and IKEv2?
IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). IKEv2 has Built-in NAT-T functionality which improves compatibility between vendors. IKEv2 supports EAP authentication. IKEv2 has the Keep Alive option enabled as default.
What is AnyConnect's default IKE?
Note: AnyConnect uses '*$AnyConnectClient$*' as its default IKE identity of type key-id. However, this identity can be manually changed in the AnyConnect profile to match deployment needs.
When to use profile in AnyConnect?
The profile is used when it is being selected from the drop-down list of AnyConnect address bar. The name that will appear is the same name as specified in "Display Name" in AnyConnect profile editor. In this example the user should select the following:
What is the filename for AnyConnect XML?
Note: The filename used for AnyConnect XML profile should be acvpn.xml.
How to restart AnyConnect?
It's not sufficient to close the AnyConnect window. The process can be restarted by right-clicking AnyConnect icon in the Windows tray and selecting "Quit" option:
How to save a profile in XML?
Save the profile by going to FIle -> Save As. The XML equivalent of the profile:
Does AnyConnect need to be delivered to the client machine?
Note: The AnyConnect profile needs to be delivered to the client machine. Please refer to the next section for more information.
Does Flex Server support local user authentication?
Local user authentication is now supported on the Flex Server and remote authentication is optional. This is ideal for small scale deployments with less number of remote access users and in environments with no access to an external Authentication, Authorization, and Accounting (AAA) server. However, for large scale deployments and in scenarios where per-user attributes are desired it is still recommended to use an external AAA sever for authentication and authorization. The AnyConnect-EAP implementation permits the use of Radius for remote authentication, authorization and accounting.
When remote users connect to our WebVPN, do they have to use HTTPS?
The following option is not required but useful, whenever someone accesses the ASA through HTTP then they will be redirected to HTTPS:
What happens when a VPN user terminates a session?
Normally when the remote VPN user terminates the session, the anyconnect installer will be uninstalled. The anyconnect keep-installer installed command leaves it installed on the user’s computer.
What is AnyConnect VPN?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN. AnyConnect VPN. The clientless WebVPN method does not require a VPN client to be installed on the user’s computer. You just open your web browser, ...
What is the IP address of AnyConnect?
You can see that we received IP address 192.168.10.100 (the first IP address from the VPN pool). Anyconnect creates an additional interface, just like the legacy Cisco VPN client does.
What is an ayconnECT_policy?
The group policy is called “ANYCONNECT_POLICY” and it’s an internal group policy which means that we configure it locally on the ASA. An external group policy could be on a RADIUS server.
Does Outlook have full network access?
Microsoft Outlook Web Access. There is no full network access when you use clientless WebVPN. Anyconnect VPN offers full network access. The remote user will use the anyconnect client to connect to the ASA and will receive an IP address from a VPN pool, allowing full access to the network. In this lesson we will use clientless WebVPN only for ...
Does ASA assign IP addresses?
The ASA will assign IP addresses to all remote users that connect with the anyconnect VPN client. We’ll configure a pool with IP addresses for this:
What is Cisco AnyConnect Secure Mobility Solution?
The Cisco AnyConnect Secure Mobility Solution provides a comprehensive, highly secure enterprise mobility solution. the Cisco AnyConnect Secure Mobility Solution continues to lead with next-generation security and encryption, including support for the Suite B set of cryptographic algorithms, and support for IPv6 networks. More importantly, it adapts its tunneling protocol to the most efficient method. AnyConnect client can be used to connect both SSL VPN as well as IKEv2 IPSec VPN. In this document we will see how to configure only IKEv2 IPSec VPN.
What is active/active failover?
Active/Active failover is only available to security appliances in multiple context mode. In an Active/Active failover configuration, both security appliances can pass network traffic. In Active/Active failover, you divide the security contexts on the security appliance into failover groups. A failover group is simply a logical group of one or more security contexts. You can create a maximum of two failover groups on the security appliance. The admin context is always a member of failover group 1. Any unassigned security contexts are also members of failover group 1 by default. We have already seen the configuration for Active/Standby failover in the previous article. This article focuses on how to configure an Active/Active Failover configuration on ASA Security Appliance. Network Diagram (Physical Topology)

Prerequisites
- Requirements
Cisco recommends that you have knowledge of these topics: 1. Basic VPN and IKEv2 knowledge 2. Basic Authentication, Authorization, and Accounting (AAA) and RADIUS knowledge 3. Experience with ASA VPN configuration 4. Experience with Identity Services Engine (ISE) configu…
Background Information
- AnyConnect Secure Mobility Client Considerations
The native Windows IKEv2 client does not support split tunnel (there are no CONF REPLY attributes which could be accepted by the Windows 7 client), so the only possible policy with the Microsoft client is to tunnel all traffic (0/0 traffic selectors). If there is a need for a specific split t…
Configure
- Note: Use the Command Lookup Tool (registeredcustomers only) in order to obtain more information on the commands used in this section.
Verify
- Use this section to confirm that your configuration works properly. The Output Interpreter Tool (registered customers only) supports certain show commands. Use the Output Interpreter Tool in order to view an analysis of showcommand output.
Related Information