The NAT rule tells the ASA not to translate traffic between the two networks. When the remote user has established the VPN, he or she will be unable to access anything on the Internet…only the remote network is reachable. For security reasons this is a good practice as it forces you to send all traffic through the ASA.
Full Answer
What is the Nat rule in a VPN?
The NAT rule tells the ASA not to translate traffic between the two networks. When the remote user has established the VPN, he or she will be unable to access anything on the Internet…only the remote network is reachable. For security reasons this is a good practice as it forces you to send all traffic through the ASA.
What is Cisco ASA remote access VPN?
Cisco ASA Remote Access VPN. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network. The Cisco VPN client is end-of-life and has been replaced by the Cisco Anyconnect Secure Mobility Client.
How do I connect to the ASA from another computer?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
Should I exempt VPN traffic from Nat?
If you do not exempt VPN traffic from NAT, ensure that the existing NAT rules for the outside and inside interfaces do not apply to the RA VPN pool of addresses. NAT exempt rules are manual static identity NAT rules for a given source/destination interface and network combination, but they are not reflected in the NAT policy, they are hidden.
How do I allow VPN through Cisco firewall?
SolutionCreate a Static (One-To-One) NAT so that the ASA that has a private IP on its outside interface, (192.168. ... Allow UDP 500 (ISAKMP) from the ASA (1.1. ... Allow UDP 4500 (NAT-TRAVERSAL) from the ASA (1.1. ... Allow UDP 500 (ISAKMP) from the ASA (192.168. ... Allow UDP 4500 (NAT-TRAVERSAL) from the ASA (192.168.
What is remote access VPN Cisco?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network such as the Internet. Remote access VPNs for IPsec IKEv2. 8.4(1) Added IPsec IKEv2 support for the AnyConnect Secure Mobility Client.
What is NAT exempt Cisco ASA?
NAT exemption allows you to exclude traffic from being translated with NAT. One scenario where you usually need this is when you have a site-to-site VPN tunnel.
How do I add a NAT rule in Asa?
There are four steps involved in enabling static NAT:Create the network object and static NAT statement. ... Create a NAT statement identifying the outside interface. ... Build the Access-Control List. ... Apply the ACL to the outside interface using the Access-Group command: access-group OutsideToWebServer in interface outside.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How does VPN remote access work?
The remote access VPN does this by creating a tunnel between an organization's network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
What are different types of NAT in Asa?
Cisco ASA NAT – Contents:Static NAT.Static PAT.Dynamic PAT.Dynamic NAT.
How NAT works in ASA firewall?
Network Address Translation is used for the translation of private IP addresses into public IP addresses while accessing the internet. NAT generally operates on a router or firewall. In this type of NAT, multiple private IP addresses are mapped to a pool of public IP addresses.
What is a no NAT rule?
No NAT rules are configured (at Policies > NAT) by specifying the desired match conditions (zone, IP, etc.) and leaving the source translation and destination translation fields blank. It is also possible to specify a list of IP addresses or IP address ranges in a NAT rule.
What is difference between auto NAT and manual NAT in Asa?
An Auto-NAT rule only uses the source address and port when matching and translating. Manual NAT can match and translate source and destination addresses and ports. In both cases, the Translated Source may be the IP of the egress interface or an object. The PAT Pool option is available when using dynamic translations.
What steps do you take to configure a NAT rule?
Let's take the following steps to set this up:Determine which IP addresses will be used for translation.Set up the necessary proxy-ARPs.Set up the necessary static host routes.Create the necessary network objects.Make the necessary modifications to anti-spoofing.More items...•
What is auto NAT in Cisco ASA?
Auto NAT is configured using the following steps: Create a network object. Within this object define the Real IP/Network to be translated. Also within this object you can use the the nat commands to specify whether the translation will be dynamic or static.
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
Introduction
This document describes how to configure the Cisco 5500 Series Adaptive Security Appliance (ASA) to act as a remote VPN server using the Adaptive Security Device Manager (ASDM) or CLI and NAT the Inbound VPN Client traffic.
Prerequisites
This document assumes that the ASA is fully operational and configured to allow the Cisco ASDM or CLI to make configuration changes. The ASA is also assumed to be configured for Outbound NAT. Refer to Allow Inside Hosts Access to Outside Networks with the use of PAT for more information on how to configure Outbound NAT.
Background Information
Remote access configurations provide secure remote access for Cisco VPN clients, such as mobile users. A remote access VPN lets remote users securely access centralized network resources. The Cisco VPN Client complies with the IPSec protocol and is specifically designed to work with the security appliance.
Configurations
Complete these steps in order to configure the Cisco ASA as a remote VPN server with ASDM:
Verify
Attempt to connect to the Cisco ASA through the Cisco VPN Client in order to verify that the ASA is successfully configured.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
How many interfaces does an ASA have?
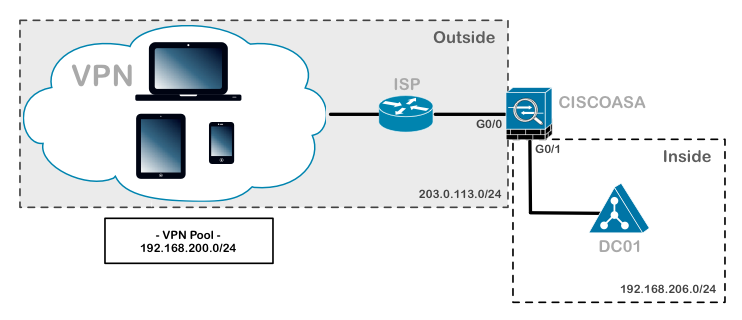
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
What is VPN_POLICY?
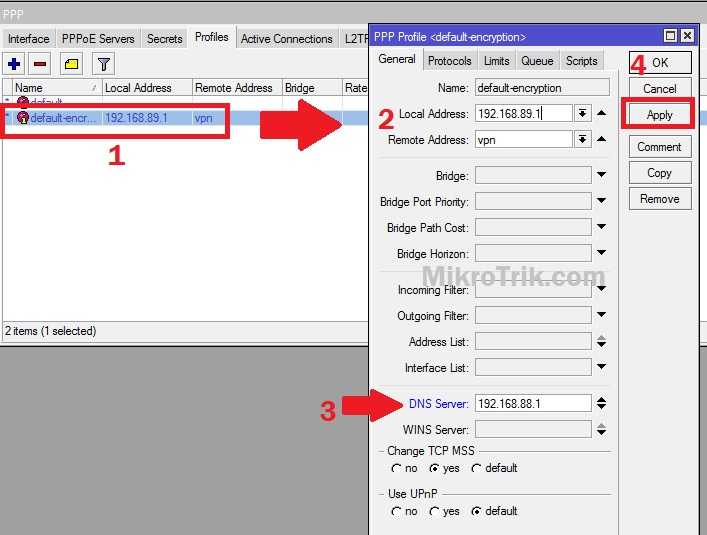
The group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
What is remote access VPN?
In remote access VPN, you might want users on the remote networks to access the Internet through your device. However, because the remote users are entering your device on the same interface that faces the Internet (the outside interface), you need to bounce Internet traffic right back out of the outside interface. This technique is sometimes called hair pinning.
Where does remote access VPN problem originate?
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
How to view VPN configuration?
Click Device, then click View Configuration in the Site-to-Site VPN group.
How to use a VPN on a computer?
Step 1. Using a web browser, open https://ravpn-address , where ravpn-address is the IP address or hostname of the outside interface on which you are allowing VPN connections. You identify this interface when you configure the remote access VPN. The system prompts the user to log in. Step 2.
How to complete a VPN connection?
To complete a VPN connection, your users must install the AnyConnect client software. You can use your existing software distribution methods to install the software directly. Or, you can have users install the AnyConnect client directly from the Firepower Threat Defense device.
What is AnyConnect client profile?
AnyConnect client profiles are downloaded to clients along with the AnyConnect client software. These profiles define many client-related options, such as auto connect on startup and auto reconnect, and whether the end user is allowed to change the option from the AnyConnect client preferences and advanced settings.
How long is a VPN idle?
Idle Timeout —The length of time, in minutes, that the VPN connection can be idle before it is automatically closed, from 1-35791394. The default is 30 minutes. Browser Proxy During VPN Sessions —Whether proxies are used during a VPN session for Internet Explorer web browsers on Windows client devices.
Problem
I have answered a lot of questions in forums, that are worded something like, “When I have a remote client connected to my firewall VPN they lose Internet access!” Traditionally that’s exactly what the ‘default’ remote VPN solution (IPSEC or AnyConnect) gave you.
Solution
At this point I’m assuming you have a remote VPN setup and working, if not you need to do that first, here are some walk-throughs I’ve already done to help you set that up.
Option 1 (Split Tunneling)
Rather than re-invent the wheel, I’ve already covered this before in the following article.
Option 2 (Tunnel All Split Tunneling)
1. Connect to the ASA > Go to enable mode > Then to global configuration mode.
Introduction
This blog is a follow-up to a previous post on CISCO ASAv in OCI. If you did not read it, I strongly encourage you to.
Configuration
Connect to Cisco's website and navigate to the AnyConnect software and download the .pkg for your operating system.
Conclusion
In this blog, we focused on configuring the Remote Access VPN on CISCO ASA which uses Local authentication (credentials stored on the ASA).
Introduction
Prerequisites
- Requirements
This document assumes that the ASA is fully operational and configured to allow the Cisco ASDM or CLI to make configuration changes. The ASA is also assumed to be configured for Outbound NAT. Refer to Allow Inside Hosts Access to Outside Networks with the use of PATfor more infor… - Components Used
The information in this document is based on these software and hardware versions: 1. Cisco Adaptive Security Appliance Software version 7.x and later 2. Adaptive Security Device Manager version 5.x and later 3. Cisco VPN Client version 4.x and later The information in this document …
Background Information
- Remote access configurations provide secure remote access for Cisco VPN clients, such as mobile users. A remote access VPN lets remote users securely access centralized network resources. The Cisco VPN Client complies with the IPSec protocol and is specifically designed to work with the security appliance. However, the security appliance can establish IPSec connectio…
Configurations
- Configure the ASA/PIX as a Remote VPN Server with ASDM
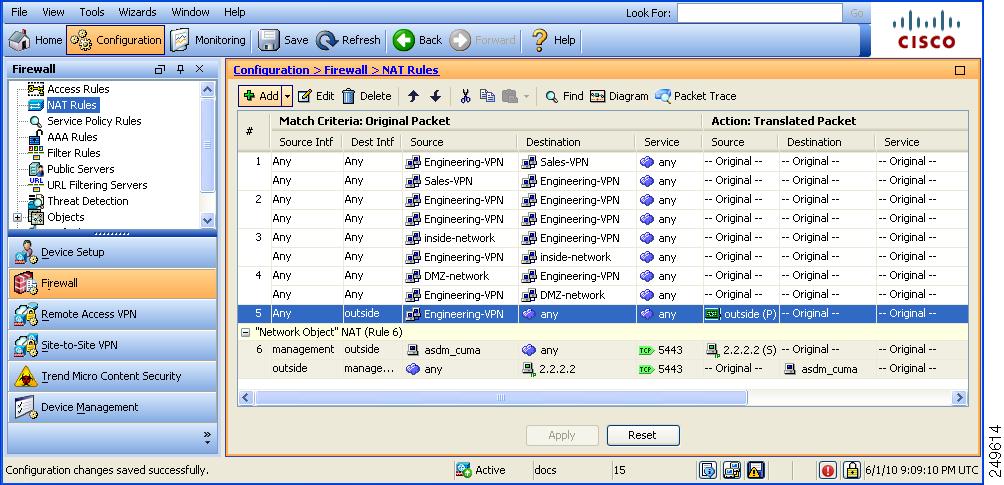
Complete these steps in order to configure the Cisco ASA as a remote VPN server with ASDM: 1. Open your browser and enter https://<IP_Address of the interface of ASA that has been configured for ASDM Access> in order to access the ASDM on the ASA. Make sure to authorize any warning… - Configure the ASA/PIX to NAT Inbound VPN Client Traffic with ASDM
Complete these steps in order to configure the Cisco ASA to NAT Inbound VPN Client traffic with ASDM: 1. Choose Configuration > Firewall > Nat Rules, and click Add. In the drop-down list, select Add Dynamic NAT Rule. 2. In the Add Dynamic NAT Rule window, choose Outside as the Interfac…
Verify
- Attempt to connect to the Cisco ASA through the Cisco VPN Client in order to verify that the ASA is successfully configured. 1. Click New. 2. Fill in the details of your new connection. The Host field must contain the IP address or hostname of the previously configured Cisco ASA. The Group Authentication information must correspond to that used in step 4. Click Savewhen you are finis…
Troubleshoot
- This section provides information you can use to troubleshoot your configuration. The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of showcommand output. Refer to Most Common L2L and Remote Access IPSec VPN Troubleshooting Solutionsfor more information on how to troubleshoot Site-Site VPN.
Related Information