How do I set up remote access with Cisco ASA?
There are eight basic steps in setting up remote access for users with the Cisco ASA. Step 1. Configure an Identity Certificate Step 2. Upload the SSL VPN Client Image to the ASA Step 3. Enable AnyConnect VPN Access Step 4. Create a Group Policy Step 5. Configure Access List Bypass Step 6.
How to use AnyConnect VPN with Asa?
The remote user will open a web browser, enters the IP address of the ASA and then it will automatically download the anyconnect VPN client and establishes the connection. Here’s the topology that we will use:
What is the ASA VPN DDoS vulnerability?
A vulnerability in the remote access SSL VPN features of Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on an affected device.
How to use clientless WebVPN with Asa?
The clientless WebVPN method does not require a VPN client to be installed on the user’s computer. You just open your web browser, enter the IP address of the ASA and you will get access through a web portal. You only have limited access to a number of applications, for example: There is no full network access when you use clientless WebVPN.

How do I access my Cisco ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
How do I check my VPN traffic on ASA?
Hi, From the CLI use the command "show crypto ipsec sa" and confirm the encaps and decaps counters are increasing to confirm traffic is being sent/received over the VPN tunnel successfully. You can also use packet capture to confirm traffic is sent/received.
What is remote access VPN Cisco?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network such as the Internet. Remote access VPNs for IPsec IKEv2. 8.4(1) Added IPsec IKEv2 support for the AnyConnect Secure Mobility Client.
What VPN types are supported by ASA?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
Which command is used to check VPN tunnel is up or not?
This command “Show vpn-sessiondb anyconnect” command you can find both the username and the index number (established by the order of the client images) in the output of the “show vpn-sessiondb anyconnect” command.
How do I check my IPsec tunnel status?
To view status information about active IPsec tunnels, use the show ipsec tunnel command. This command prints status output for all IPsec tunnels, and it also supports printing tunnel information individually by providing the tunnel ID.
How does VPN remote access work?
The remote access VPN does this by creating a tunnel between an organization's network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How do I set up AnyConnect on ASA?
Configure AnyConnect ConnectionsConfigure the ASA to Web-Deploy the Client.Enable Permanent Client Installation.Configure DTLS.Prompt Remote Users.Enable AnyConnect Client Profile Downloads.Enable AnyConnect Client Deferred Upgrade.Enable DSCP Preservation.Enable Additional AnyConnect Client Features.More items...•
What are the four types of VPN?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs....How Personal VPNs WorkInstall software from your VPN service provider onto your device. ... Connect to a server in your VPN provider's network.More items...•
What are 3 types of VPN tunnels?
We'll look at three of the most common: IPsec tunnels, Dynamic multi point VPNs, and MPLS-based L3VPNs.IPsec Tunnels. In principle, a network-based VPN tunnel is no different from a client-based IPsec tunnel. ... Dynamic Multi point VPN (DMVPN) ... MPLS-based L3VPN.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
How many interfaces does an ASA have?
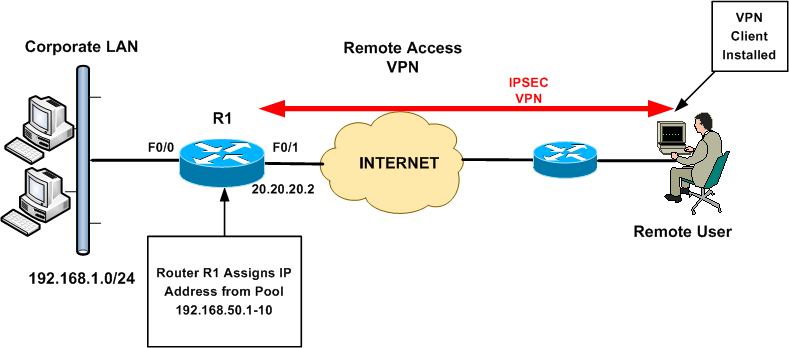
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
What is VPN_POLICY?
The group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
What version of Cisco 5500-X is ASA?
The information in this document is based on the Cisco 5500-X Series Adaptive Security Appliance (ASA) Version 9.1 (2).
What port does ACE access list vpnfilt-ra permit?
Note: The ACE access-list vpnfilt-ra permit tcp 10.10.10.1 255.255.255.255 eq 23 192.168.1.0 255.255.255.0 also allows the RA client to initiate a connection to the local network on any TCP port if it uses a source port of 23.
What is Cisco CLI Analyzer?
The Cisco CLI Analyzer ( registered customers only) supports certain show commands. Use the Cisco CLI Analyzer in order to view an analysis of show command output.
What is sysopt connection permit-vpn?
The sysopt connection permit-vpn command allows all the traffic that enters the security appliance through a VPN tunnel to bypass interface access lists. Group policy and per-user authorization access lists still apply to the traffic.
What is a VPN filter?
A vpn-filter is applied to postdecrypted traffic after it exits a tunnel and to preencrypted traffic before it enters a tunnel. An ACL that isused for a vpn-filter should NOT also be used for an interface access-group.
What is ACE in telnet?
This Access Control Entry (ACE) allows the AnyConnect client to Telnet to the local network:
When a VPN filter is applied to a VPN tunnel, what is the filter table?
When a filter has been applied to a VPN tunnel, the filter rules are installed into the filter table. If the tunnel has a filter specified, then the filter table is checked prior to encryption and after decryption in order to determine whether the inner packet should be permitted or denied. USAGE.
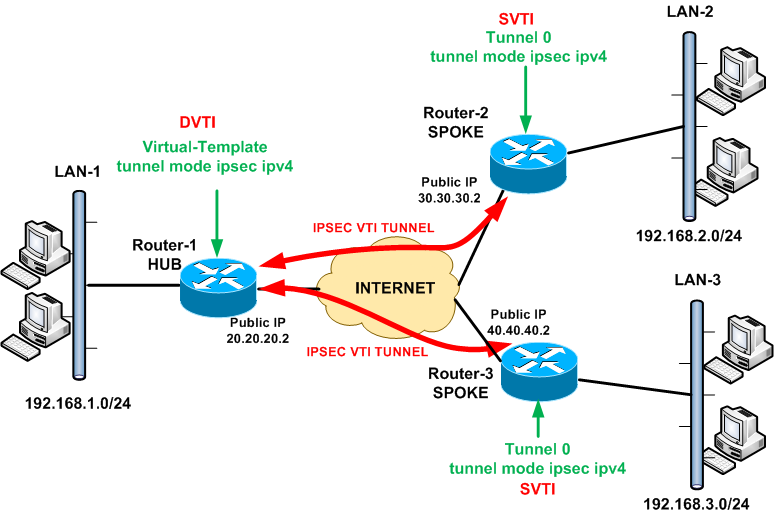
Which direction should you apply your acl to the VTI?
2) if you are using VTI apply your acl to the VTI in an outbound direction
When is Catalyst 8000 2021?
This event had place on Tuesday 22nd, June 2021 at 9hrs PDT Introduction This session provided a broad overview of the overall unified communications solutions available on the Catalyst 8000 family. Learn about the modular voice capabilities of the Cat... view more
Can routers support reflexive ACLs?
However routers support reflexive acls which means you can only allow traffic back in if you have initaited the connection so you could -
Do all ACLs have an IP address?
All acls have an implicit "deny ip any any" at the end so you blocked all traffic from your LAN to the internet with your acl.
What is AnyConnect VPN?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN. AnyConnect VPN. The clientless WebVPN method does not require a VPN client to be installed on the user’s computer. You just open your web browser, ...
When remote users connect to our WebVPN, do they have to use HTTPS?
The following option is not required but useful, whenever someone accesses the ASA through HTTP then they will be redirected to HTTPS:
What happens when a VPN user terminates a session?
Normally when the remote VPN user terminates the session, the anyconnect installer will be uninstalled. The anyconnect keep-installer installed command leaves it installed on the user’s computer.
What happens when you have an inbound access list?
When you have an inbound access-list on the outside interface then all your decrypted traffic from the SSL WebVPN has to match the inbound access-list. You can either create some permit statements for the decrypted traffic or you can just tell the ASA to let this traffic bypass the access-list:
Why does my client tries to download AnyConnect?
The client tries to download the Anyconnect automatically, this is because of the anyconnect ask none default anyconnect command that we used. Since we are using a self-signed certificate you will get the following error message:
What is the IP address of AnyConnect?
You can see that we received IP address 192.168.10.100 (the first IP address from the VPN pool). Anyconnect creates an additional interface, just like the legacy Cisco VPN client does.
What is an ayconnECT_policy?
The group policy is called “ANYCONNECT_POLICY” and it’s an internal group policy which means that we configure it locally on the ASA. An external group policy could be on a RADIUS server.
Introduction
Prerequisites
- Requirements
Cisco recommends that you have knowledge of these topics: 1. L2L VPN tunnels configuration 2. VPN Client Remote Access (RA) configuration 3. AnyConnect RA configuration - Components Used
The information in this document is based on the Cisco 5500-X Series Adaptive Security Appliance (ASA) Version 9.1(2). The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (defau…
Background Information
- The sysopt connection permit-vpncommand allows all the traffic that enters the security appliance through a VPN tunnel to bypass interface access lists. Group policy and per-user authorization access lists still apply to the traffic. A vpn-filter is applied to postdecrypted traffic after it exits a tunnel and to preencrypted traffic before it enters a tunnel. An ACL that isused for a vpn-filter s…
Configure
- VPN filters must be configured in inbound direction although rules are still applied bidirectionally. Enhancement CSCsf99428has been opened to support unidirectional rules, but it has not yet been scheduled/committed for implementation.
Verify
- Use this section in order to confirm that your configuration works properly. The Cisco CLI Analyzer (registered customers only) supports certain show commands. Use the Cisco CLI Analyzer in order to view an analysis of showcommand output. 1. show asp table filter [access-list <acl-name>] [hits] In order to debug the accelerated security path filter tables, use the show asp tabl…
Troubleshoot
- This section provides information you can use in order to troubleshoot your configuration. The Cisco CLI Analyzer (registered customers only) supports certain show commands. Use the Cisco CLI Analyzer in order to view an analysis of showcommand output. Note: Refer to Important Information on Debug Commands before you use debugcommands. 1. debug acl filter This com…