What is an ACL in Cisco ASA 5500?
An ACL is the central configuration feature to enforce security rules on your network. The Cisco ASA 5500 is the new Cisco firewall model series which followed the successful Cisco PIX firewall appliance. Cisco calls the ASA 5500 a “security appliance” instead of just a “hardware firewall”, because the ASA is not just a firewall.
How do VPN filters work on Cisco ASA firewall?
Within this article we will look into how VPN filters work and also how to configure them on a Cisco ASA firewall. As the name suggests VPN filters provide the ability to permit or deny post-decrypted traffic after it exits a tunnel and pre-encrypted traffic before it enters a tunnel.
How to filter VPN traffic using interface ACLS?
VPN traffic is not filtered by interface ACLs. The command no sysopt connection permit-vpn can be used in order to change the default behavior. In this case, two ACLs can be applied to user traffic: the interface ACL is checked first and then the vpn-filter.
Why is the access-list applied to the outside interface of Asa?
Although the webserver is placed in a DMZ zone, the access-list is applied to the outside interface of the ASA because this is where the traffic comes in. NOTE: From ASA version 8.3 and later, the example above must reference the real IP address configured on the Web Server and not the NAT IP.
How do I access my Cisco ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
What is remote access VPN Cisco?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network such as the Internet. Remote access VPNs for IPsec IKEv2. 8.4(1) Added IPsec IKEv2 support for the AnyConnect Secure Mobility Client.
What VPN types are supported by ASA?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
How do I enable VPN on ASA?
Set up VPN on a Cisco ASA deviceOpen ASDM.Go to Wizards VPN Wizards. IPsec (IKEv1) Remote Access VPN Wizard.Bypass the interface access lists: ... Click Next.Choose Microsoft Windows client using L2TP over IPsec and check the box for MS-CHAP-V2.Click Next.Authenticate the machine: ... Click Next.More items...
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What are the four types of VPN?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs....How Personal VPNs WorkInstall software from your VPN service provider onto your device. ... Connect to a server in your VPN provider's network.More items...•
What are 3 types of VPN tunnels?
We'll look at three of the most common: IPsec tunnels, Dynamic multi point VPNs, and MPLS-based L3VPNs.IPsec Tunnels. In principle, a network-based VPN tunnel is no different from a client-based IPsec tunnel. ... Dynamic Multi point VPN (DMVPN) ... MPLS-based L3VPN.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
How do I configure IPSec on ASA firewall?
To configure the IPSec VPN tunnel on Cisco ASA 55xx:Configure IKE. Establish a policy for the supported ISAKMP encryption, authentication Diffie-Hellman, lifetime, and key parameters. ... Create the Access Control List (ACL) ... Configure IPSec. ... Configure the Port Filter. ... Configure Network Address Translation (NAT)
How configure AnyConnect Cisco ASA?
5 Steps to Configure Cisco AnyConnect VPNConfigure AAA authentication. The first thing to configure is AAA authentication. ... Define VPN protocols. When users connect their VPN, they'll need an IP address for the VPN session. ... Configure tunnel groups. ... Set group policies. ... Apply the configuration. ... Authenticating logic flow.
Is Cisco AnyConnect SSL or IPSec?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
Can you create a specific IP address?
You can just create specific IP Address, vpn-filter, group-policy for the user that you want more restricted access, and leave the rest as what is currently configured.
Can you configure a VPN filter?
You can configure "vpn-filter" access-list to allow them to only access specific subnets.
Can you configure IP address for ASA?
If you are using ASA local database as the authentication server, you can configure specific IP Address for that user.
Does Cisco Umbrella block DNS?
I had in the past an issue when migrating Cisco Cloud Web Security to Cisco Umbrella for a Customer. The Cisco ASA Firewall blocks the DNScrypt provided by the Cisco Umbrella Virtual Appliance.The issue is solved by disabling DNS packet inspection between... view more
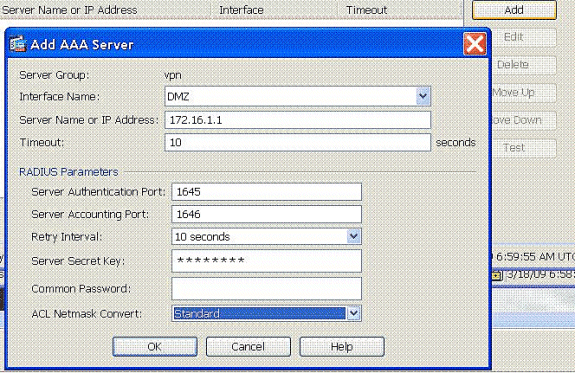
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
What happens if a Cisco VPN client has a different preshared key size?
If a Cisco VPN Client with a different preshared key size tries to connect, the client logs an error message indicating it failed to authenticate the peer.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
What is Cisco ASA 5500?
The Cisco ASA 5500 is the successor Cisco firewall model series which followed the successful Cisco PIX firewall appliance. Currently the newest generation of ASA is 5500-X series but the configuration on ACLs is the same. Cisco calls the ASA 5500 a “security appliance” instead of just a “hardware firewall”, because the ASA is not just a firewall.
Why is the access list applied to the outside interface of the ASA?
Although the webserver is placed in a DMZ zone, the access-list is applied to the outside interface of the ASA because this is where the traffic comes in.
What is an ACL in a firewall?
An ACL is a list of rules with permit or deny statements. Basically an Access Control List enforces the security policy on the network. The ACL (list of policy rules) is then applied to a firewall interface, either on the inbound or on the outbound traffic direction. If the ACL is applied on the inbound traffic direction (in), ...
What happens at the end of an ACL?
At the end of the ACL, the firewall inserts by default an implicit DENY ALL statement rule which is not visible in the configuration.
What is the purpose of a network firewall?
Having said that, the purpose of a network firewall is to protect computer and IT resources from malicious sources by blocking and controlling traffic flow. The Cisco ASA firewall achieves this traffic control using Access Control Lists (ACL).
What is ACL permit or deny?
The ACL permit or deny statements basically consist of source and destination IP addresses and ports.
Is ACL evaluated first for inbound traffic?
Similarly, a scenario with inbound traffic (outside to inside) works again the same way. That is, an ACL is evaluated first for inbound traffic and then a NAT translation rule is applied
What is Cisco AnyConnect Secure Mobility Solution?
The Cisco AnyConnect Secure Mobility Solution provides a comprehensive, highly secure enterprise mobility solution. the Cisco AnyConnect Secure Mobility Solution continues to lead with next-generation security and encryption, including support for the Suite B set of cryptographic algorithms, and support for IPv6 networks. More importantly, it adapts its tunneling protocol to the most efficient method. In the present scenario, we have to configure Anyconnect SSL remote access VPN for Sales department and Engineering department of a company. Engineering users will have to be provided with access to web server as well as FTP server, while sales users may only have access to the web server.
What is active/active failover?
Active/Active failover is only available to security appliances in multiple context mode. In an Active/Active failover configuration, both security appliances can pass network traffic. In Active/Active failover, you divide the security contexts on the security appliance into failover groups. A failover group is simply a logical group of one or more security contexts. You can create a maximum of two failover groups on the security appliance. The admin context is always a member of failover group 1. Any unassigned security contexts are also members of failover group 1 by default. We have already seen the configuration for Active/Standby failover in the previous article. This article focuses on how to configure an Active/Active Failover configuration on ASA Security Appliance. Network Diagram (Physical Topology)
Does Cisco AnyConnect support SSL VPN?
Even after the release of Cisco AnyConnect Secure Mobility Client which supports SSL VPN in addition to IKEv2 remote-access IPSec VPN, still out there are number of people who use legacy Cisco VPN client to connect IKEv1 remote-access IPSec VPN.
When is ACL applied to an interface?
When an ACL is applied to an interface, we define when it should permit (or deny) traffic that is either going in or out of the interface.
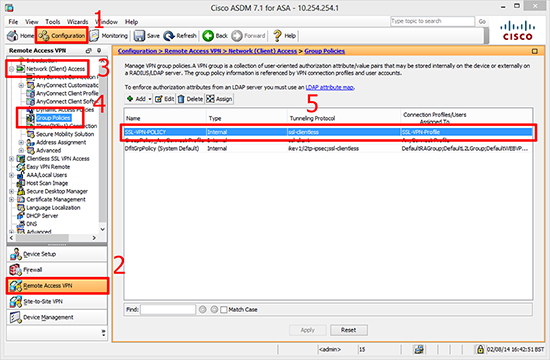
What is VPN filter?
As the name suggests VPN filters provide the ability to permit or deny post-decrypted traffic after it exits a tunnel and pre-encrypted traffic before it enters a tunnel.
Introduction
Prerequisites
- Requirements
Cisco recommends that you have knowledge of these topics: 1. L2L VPN tunnels configuration 2. VPN Client Remote Access (RA) configuration 3. AnyConnect RA configuration - Components Used
The information in this document is based on the Cisco 5500-X Series Adaptive Security Appliance (ASA) Version 9.1(2). The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (defau…
Background Information
- The sysopt connection permit-vpncommand allows all the traffic that enters the security appliance through a VPN tunnel to bypass interface access lists. Group policy and per-user authorization access lists still apply to the traffic. A vpn-filter is applied to postdecrypted traffic after it exits a tunnel and to preencrypted traffic before it enters a tunnel. An ACL that isused for a vpn-filter s…
Configure
- VPN filters must be configured in inbound direction although rules are still applied bidirectionally. Enhancement CSCsf99428has been opened to support unidirectional rules, but it has not yet been scheduled/committed for implementation.
Verify
- Use this section in order to confirm that your configuration works properly. The Cisco CLI Analyzer (registered customers only) supports certain show commands. Use the Cisco CLI Analyzer in order to view an analysis of showcommand output. 1. show asp table filter [access-list <acl-name>] [hits] In order to debug the accelerated security path filter tables, use the show asp tabl…
Troubleshoot
- This section provides information you can use in order to troubleshoot your configuration. The Cisco CLI Analyzer (registered customers only) supports certain show commands. Use the Cisco CLI Analyzer in order to view an analysis of showcommand output. Note: Refer to Important Information on Debug Commands before you use debugcommands. 1. debug acl filter This com…