
Click the Base 64 radio button as the encoding method, and click Download CA certificate. Save the CA certificate with the certnew.cer name on your computer. Go to Configuration > Remote Access VPN > Certificate Management > CA Certificates in the ASA firewall. Click on the "Add" button, the "Install Certificate" window will open.
Can the adaptive security appliance (Asa) remotely access a VPN?
In its place, only certificate-based authentication can be used to allow the Adaptive Security Appliance (ASA) to permit users to remotely access Virtual Private Network (VPN). This white paper focuses on implementing all of the functionality natively on the Cisco ASA 5500 with the Cisco VPN Client.
How to enable SSL certificate authentication in ASA?
(Feature in the ASA 8.2.x release, using pre-8.2.x ASA code it will require to globally enabling the certificate authentication with the command "ssl certificate-authentication interface <interface> port <portnum>").
How do I configure Cisco AnyConnect for remote access?
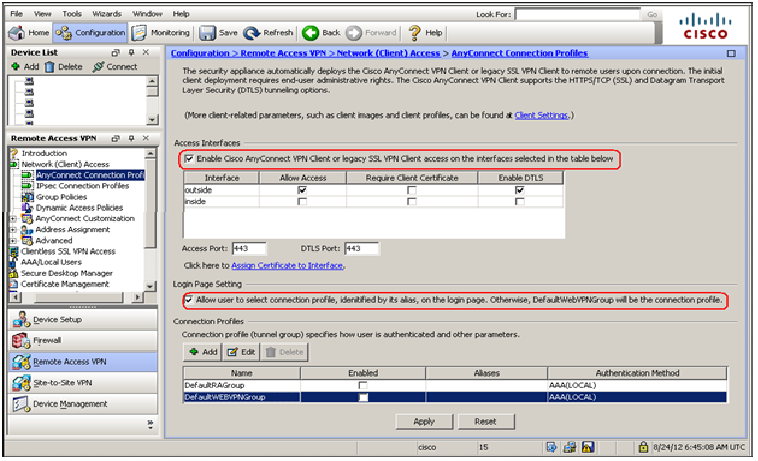
Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles. Check the box "Enable Cisco AnyConnect VPN Client or legacy SSL Client". Then select the interface where the AnyConnect clients will be connecting to (in this example the outside interface).
How to install CA certificate in ASA firewall?
Click the Base 64 radio button as the encoding method, and click Download CA certificate. Save the CA certificate with the certnew.cer name on your computer. Go to Configuration > Remote Access VPN > Certificate Management > CA Certificates in the ASA firewall. Click on the "Add" button, the "Install Certificate" window will open.
Which certificate does Cisco AnyConnect use?
The CA certificate must be downloaded from the CA server and installed in the ASA. Complete these steps in order to download the CA certificate from the CA server. Perform the web login into the CA server CA-server with the help of the credentials supplied to the VPN server.
Where is AnyConnect certificate stored?
Export the client certificate The client certificates that you generated are, by default, located in 'Certificates - Current User\Personal\Certificates'.
Does AnyConnect require a certificate?
Since Anyconnect is based on SSL VPN, so the first time you try to connect , you get prompted with certificate on the ASA.
How do I add a certificate to ASA AnyConnect?
In ASDM select "Configuration" and then "Device Management." Click "Advanced" and then "SSL Settings." From "Certificates," choose the interface used to terminate WebVPN sessions, and then choose "Edit." From the "Certificate" drop-down, select the newly installed certificate, then "OK," and then "Apply."
How do I get a VPN certificate?
Navigate to Microsoft Windows Certificate Enrollment page: http:///CertSrv.When prompted for authentication, enter username and password of a Domain User.Click Request a certificate.Click advanced certificate request.Select Administrator or User under Certificate Template.More items...
How do I fix VPN certificate validation failure?
The most common reason for certificate validation failure on VPN is an expired certificate. VPN certificates are essential because they are a more secure way for authentication than preshared keys. Users reported that updating the certificate will solve the certificate validation failure error.
How do I check Cisco VPN certificate?
Start-> type certmgr.exe Check if the Personal store or the Machine Store, to see if the Identity certificate is installed after that double click on the certificate and you will be able to see the details.
What is certificate based VPN?
You can use certificates for authentication in both the policy-based and route-based VPNs. A certificate authority (CA) issues certificates as proof of identity. Gateways that form a VPN tunnel are configured to trust the CA that signed the other gateway's certificate.
How do I renew Cisco AnyConnect VPN certificate?
It's quite easy:Generate a new named RSA pub/priv keypair of 2048 Bit.Configure a new trustpoint with the new labeled key.Generate a new CSR based on the new trustpoint.Get your new certificate with the CSR.Import the certificate into the trustpoint.Change the public interface to use the new trustpoint.Done!
How do I upload a certificate to Asa?
In ASDM select Configuration and then Device Management.Click Advanced and then SSL Settings.From Certificates, choose the interface used to terminate WebVPN sessions. Click Edit.From the Certificate drop-down, select the newly installed certificate. Click OK. Click Apply.
How do I import a certificate to Asa?
Click Configuration > Device Management. Click Certificate Management > Identity Certificates. Select the identity certificate you created (The Expiry Date should display Pending) Click Install.
What is identity certificate in Cisco ASA?
The Identity certificates are attached to the interface with the purpose to make the ASA a trusted server, for example if you have an identity certificate with the CN vpn.cisco.com the Anyconnect users needs to type that domain to connect and avoid any pop-up of untrusted connections.
How do I check Cisco VPN certificate?
Start-> type certmgr.exe Check if the Personal store or the Machine Store, to see if the Identity certificate is installed after that double click on the certificate and you will be able to see the details.
How do I renew Cisco Anyconnect VPN certificate?
It's quite easy:Generate a new named RSA pub/priv keypair of 2048 Bit.Configure a new trustpoint with the new labeled key.Generate a new CSR based on the new trustpoint.Get your new certificate with the CSR.Import the certificate into the trustpoint.Change the public interface to use the new trustpoint.Done!
Why does Cisco not recommend self signed certificates?
Cisco does not recommend use of a self-signed certificate because of the possibility that a user could inadvertently configure a browser to trust a certificate from a rogue server. There is also the inconvenience to users to have to respond to a security warning when it connects to the secure gateway.
What is a CSR certificate?
Once the private/public Rivest-Shamir-Adleman (RSA) or Elliptic Curve Digital Signature Algorithm (ECDSA) keypair is generated ( Appendix A details the difference between the use of RSA or ECDSA), a Certficate Signing Request (CSR) is created. A CSR is basically a PKCS10 formatted message that contains the public key and identity information of the requesting host. PKI Data Formats explains the different certificate formats applicable to the ASA and Cisco IOS ®.
What is OpenSSL config?
OpenSSL makes use of the OpenSSL config file to pull the attributes to be used in the CSR generation. This process results in the generation of a CSR and a Private Key. Caution: Ensure that the Private key that is generated is not shared with anyone else as this might compromise the integrity of the certificate.
What is ECDSA compared to RSA?
This means that with ECDSA the same level of security as RSA can be achieved, but with smaller keys. This reduces computation time and increases the connection times for sites that use ECDSA certificates.
How to add a certificate to a PKCS12 file?
Click the Import the identity certificate from a file radio button. Enter the passphrase used to create the PKCS12 file. Browse and select the PKCS12 file. Enter the certificate passphrase. Click Add Certificate . Navigate to Configuration > Remote Access VPN > Advanced, and choose SSL Settings.
Do you need to copy certificates from primary to secondary ASA?
There is no need to manually copy the certificates from the Primary to Secondary ASA as the certificates should be synced between the ASAs as long as Stateful Failover is configured. If on initial setup of failover, the certificates are not seen on the Standby device, issue the command write standby in order to force a sync.
Where does remote access VPN problem originate?
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
Why create a VPN profile?
You can create a remote access VPN connection profile to allow your users to connect to your inside networks when they are on external networks, such as their home network . Create separate profiles to accommodate different authentication methods.
How to complete a VPN connection?
To complete a VPN connection, your users must install the AnyConnect client software. You can use your existing software distribution methods to install the software directly. Or, you can have users install the AnyConnect client directly from the Firepower Threat Defense device.
How to use a VPN on a computer?
Step 1. Using a web browser, open https://ravpn-address , where ravpn-address is the IP address or hostname of the outside interface on which you are allowing VPN connections. You identify this interface when you configure the remote access VPN. The system prompts the user to log in. Step 2.
What is AnyConnect client profile?
AnyConnect client profiles are downloaded to clients along with the AnyConnect client software. These profiles define many client-related options, such as auto connect on startup and auto reconnect, and whether the end user is allowed to change the option from the AnyConnect client preferences and advanced settings.
What is the primary identity source?
Primary Identity Source for User Authentication —The primary identity source used for authenticating remote users. End users must be defined in this source or the optional fallback source to complete a VPN connection. Select one of the following:
Where is change of authorization policy configured?
Most of the Change of Authorization policy is configured in the ISE server. However, you must configure the FTD device to connect to ISE correctly. The following procedure explains how to configure the FTD side of the configuration.
Introduction
Prerequisites
- Requirements
This document requires access to a trusted third-party Certificate Authority (CA) for certificate enrollment. Examples of third-party CA vendors include, but are not limited to, Baltimore, Cisco, Entrust, Geotrust, G, Microsoft, RSA, Thawte, and VeriSign. Before you start, verify that the ASA h… - Components Used
This document uses an ASA 5500-X that runs software version 9.4.1 and ASDM version 7.4(1). The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your netwo…
Configure
- The SSL protocol mandates that the SSL Server provide the client with a server certificate for the client to perform server authentication. Cisco does not recommend use of a self-signed certificate because of the possibility that a user could inadvertently configure a browser to trust a certificate from a rogue server. There is also the inconvenience to users to have to respond to a security w…
Verify
- Use these steps in order to verify successful installation of the third-party Vendor Certificate and use for SSLVPN connections.
Frequently Asked Questions
- 1. What is the best way to transfer identity certificates out of one ASA onto a different ASA?
Export the certificate along with the keys to a PKCS12 file. Use this command in order to export the certificate via the CLI from the original ASA: Corresponding ASDM configuration: Use this command in order to import the certificate via CLI to the target ASA: Corresponding ASDM confi… - 2. How to generate SSL certificates for use with VPN Load Balancing ASAs?
There are multiple methods that can be used to set up ASAs with SSL certificates for a VPN Load Balancing environment. 1. Use a single Unified Communications/Multiple Domains Certificate (UCC) which has the load-balancing FQDN as the DN and each of the ASA FQDNs as a separate …
Troubleshoot
- Troubleshooting Commands
These debug commands are to be collected on the CLI in the case of an SSL Certificate Installation failure: debug crypto ca 255 debug crypto ca messages 255 debug crypto ca transactions 255 - Common Issues
Untrusted certificate warning when using a valid third-party SSL certificate on the external interface on ASA running 9.4(1) and later. Solution: This issue presents itself when an RSA keypair is used with the certificate. On ASA versions from 9.4(1) onwards, all the ECDSA and RSA cipher…
Appendix
- Appendix A: ECDSA or RSA
The ECDSA algorithm is a part of the Elliptic curve cryptography (ECC) and uses an equation of an elliptic curve to generate a Public Key whereas the RSA algorithm uses the product of two primes plus a smaller number to generate the Public Key. This means that with ECDSA the same level o… - Appendix B: Use OpenSSL to Generate a PKCS12 Certificate from an Identity Certificate, CA Certi…
1. Ensure that OpenSSL is installed on the system that this process is run on. For Mac OSX and GNU/Linux users, this will be installed by default. 2. Switch to a working directory.On Windows: By default, the utilities are installed in C:\Openssl\bin. Open a command prompt in this location.On …
Related Information