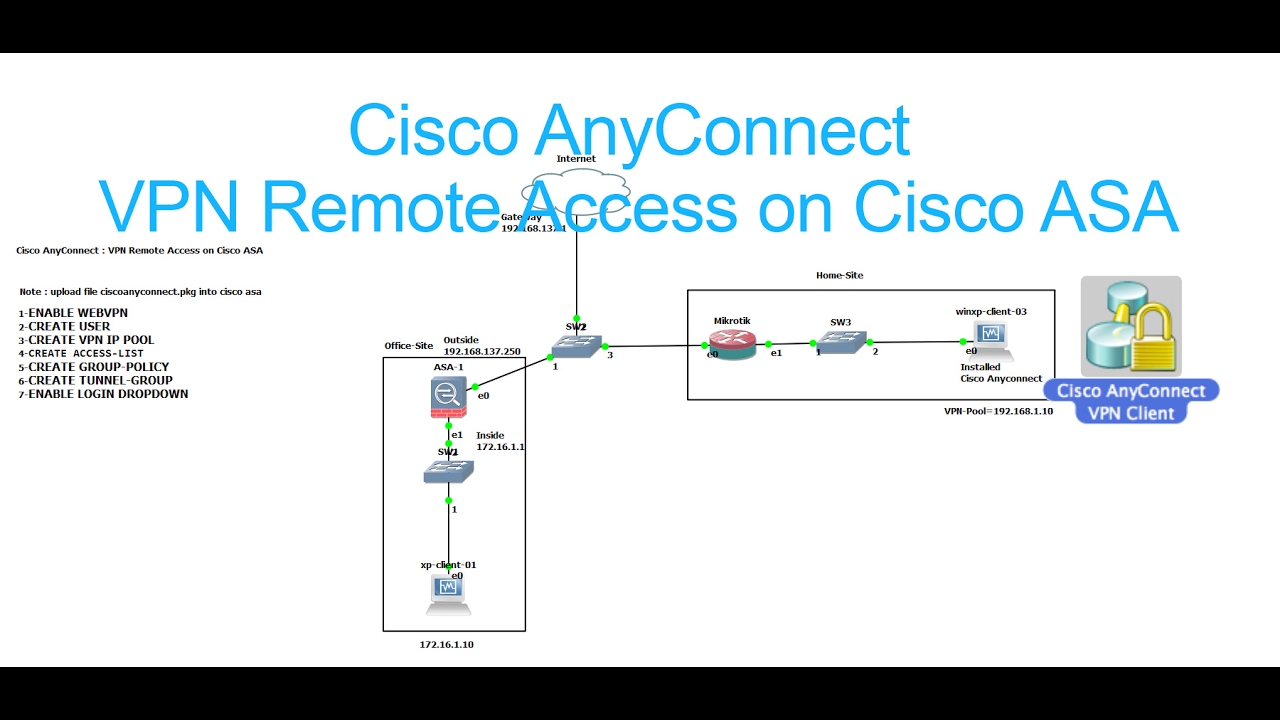
- Configure an Identity Certificate.
- Upload the SSL VPN Client Image to the ASA.
- Enable AnyConnect VPN Access.
- Create a Group Policy.
- Configure Access List Bypass.
- Create a Connection Profile and Tunnel Group.
- Configure NAT Exemption.
How to setup a remote access VPN?
Use a VPN Router with the built-in VPN server capability
- Launch a browser window from your PC connected to the routers’ network
- Enter the router IP address in the search to login into your router
- Enter the username and password of your router and login into it.
- Go to the Settings page and select VPN Service or setup page.
- Enable the VPN service by selecting the checkbox and apply
Can the Cisco ASA be used as a router?
The ASA is NOT a router, though and while you can do things on the ASA that can make it act something like a router it is important to understand the differences between true routing and what the ASA actually does.
How to connect Cisco ASA on PC?
- Connect the network cable from the modem to port 0 (default outside port) on the ASA.
- Connect your computer to one of the other ports on the ASA, which should be on the inside network by default.
- Open a browser on your computer and go to 192.168.
- Click Run ASDM.
- Log in.
How to setup a Cisco VPN?
How To Setup Vpn Cisco Rv340? February 18, 2022 by Cathie. Select Settings, VPN, and then add a VPN connection. Enter the public WAN IP address provided by your ISP, select a VPN type as PPTP, and enter the user name and password in the section below. The newly created PPTP VPN network adapter must now be connected.

How do I do remote desktop using Cisco VPN client?
Go to the Cisco Anyconnect VPN program, enter your HSPH PIN password, and click accept. 2. Go to “Remote Desktop”, your IP address should already be there from the initial setup, click connect. You should be taken to your “office” desktop, maybe to your login page.
What is remote access VPN Cisco?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network such as the Internet. Remote access VPNs for IPsec IKEv2. 8.4(1) Added IPsec IKEv2 support for the AnyConnect Secure Mobility Client.
How do I connect to Cisco VPN client?
2:026:36Working with the Cisco VPN Client. (IPSEC) - YouTubeYouTubeStart of suggested clipEnd of suggested clipYou need to put the IP address of the Cisco device that you are connecting.MoreYou need to put the IP address of the Cisco device that you are connecting.
Can Cisco ASA do route based VPN?
ASA supports route-based VPN with the use of Virtual Tunnel Interfaces (VTIs) in version 9.8 and later.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How do I set up AnyConnect on ASA?
Configure AnyConnect ConnectionsConfigure the ASA to Web-Deploy the Client.Enable Permanent Client Installation.Configure DTLS.Prompt Remote Users.Enable AnyConnect Client Profile Downloads.Enable AnyConnect Client Deferred Upgrade.Enable DSCP Preservation.Enable Additional AnyConnect Client Features.More items...•
Is Cisco VPN client free?
Cisco AnyConnect is a free, easy to use, and worthwhile VPN client for Microsoft Windows computers. It's secure and doesn't require a lot of maintenance.
What is the use of Cisco VPN client?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
What is the difference between remote access and a VPN?
In a policy-based VPN configuration, the action must be permit and must include a tunnel. Route-based VPNs support the exchange of dynamic routing information through VPN tunnels. You can enable an instance of a dynamic routing protocol, such as OSPF, on an st0 interface that is bound to a VPN tunnel.Comparing Policy-Based and Route-Based VPNs | Junos OShttps://www.juniper.net › junos › vpn-ipsec › topics › taskhttps://www.juniper.net › junos › vpn-ipsec › topics › taskSearch for: What is the difference between route-based and policy-based VPN?
What is the difference between site-to-site VPN and remote access VPN?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.Cisco Adaptive Security Appliances (ASA) Firewall and Virtual Private ...https://www.commoncriteriaportal.org › files › epfiles › S...https://www.commoncriteriaportal.org › files › epfiles › S...Search for: What VPN types are supported by ASA?
How does Cisco AnyConnect VPN Work?
A route-based VPN is a configuration in which an IPsec VPN tunnel created between two end points is referenced by a route that determines which traffic is sent through the tunnel based on a destination IP address.Route-Based IPsec VPNs | Junos OS - Juniper Networkshttps://www.juniper.net › vpn-ipsec › topics › topic-maphttps://www.juniper.net › vpn-ipsec › topics › topic-mapSearch for: What is route-based VPN?
What are the two types of VPN connections?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
How many interfaces does an ASA have?
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
What is VPN_POLICY?
The group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
Problem
I have answered a lot of questions in forums, that are worded something like, “When I have a remote client connected to my firewall VPN they lose Internet access!” Traditionally that’s exactly what the ‘default’ remote VPN solution (IPSEC or AnyConnect) gave you.
Solution
At this point I’m assuming you have a remote VPN setup and working, if not you need to do that first, here are some walk-throughs I’ve already done to help you set that up.
Option 1 (Split Tunneling)
Rather than re-invent the wheel, I’ve already covered this before in the following article.
Option 2 (Tunnel All Split Tunneling)
1. Connect to the ASA > Go to enable mode > Then to global configuration mode.
What version of ASA is AnyConnect?
The ASA supports the AnyConnect client firewall feature with ASA version 8.3 (1) or later, and ASDM version 6.3 (1) or later. This section describes how to configure the client firewall to allow access to local printers, and how to configure the client profile to use the firewall when the VPN connection fails.
What is DPD in ASA?
Dead Peer Detection (DPD) ensures that the ASA (gateway) or the client can quickly detect a condition where the peer is not responding, and the connection has failed. To enable dead peer detection (DPD) and set the frequency with which either the AnyConnect client or the ASA gateway performs DPD, do the following:
What is ACL AnyConnect_Client_Local_Print?
The ACL AnyConnect_Client_Local_Print is provided with ASDM to make it easy to configure the client firewall. When you choose that ACL for Public Network Rule in the Client Firewall pane of a group policy, that list contains the following ACEs:
Does ASA support LDAP?
The other parameters are valid for AAA servers that support such notification; that is, RADIUS, RADIUS with an NT server, and LDAP servers. The ASA ignores this command if RADIUS or LDAP authentication has not been configured.
Does AnyConnect SSL VPN work with IPsec?
This feature applies to connectivity between the ASA gateway and the AnyConnect SSL VPN Client only. It does not work with IPsec since DPD is based on the standards implementation that does not allow padding, and CLientless SSL VPN is not supported.
What is Cisco AnyConnect Secure Mobility Solution?
The Cisco AnyConnect Secure Mobility Solution provides a comprehensive, highly secure enterprise mobility solution. the Cisco AnyConnect Secure Mobility Solution continues to lead with next-generation security and encryption, including support for the Suite B set of cryptographic algorithms, and support for IPv6 networks. More importantly, it adapts its tunneling protocol to the most efficient method. In the present scenario, we have to configure Anyconnect SSL remote access VPN for Sales department and Engineering department of a company. Engineering users will have to be provided with access to web server as well as FTP server, while sales users may only have access to the web server.
What is active/active failover?
Active/Active failover is only available to security appliances in multiple context mode. In an Active/Active failover configuration, both security appliances can pass network traffic. In Active/Active failover, you divide the security contexts on the security appliance into failover groups. A failover group is simply a logical group of one or more security contexts. You can create a maximum of two failover groups on the security appliance. The admin context is always a member of failover group 1. Any unassigned security contexts are also members of failover group 1 by default. We have already seen the configuration for Active/Standby failover in the previous article. This article focuses on how to configure an Active/Active Failover configuration on ASA Security Appliance. Network Diagram (Physical Topology)
Does Cisco AnyConnect support SSL VPN?
Even after the release of Cisco AnyConnect Secure Mobility Client which supports SSL VPN in addition to IKEv2 remote-access IPSec VPN, still out there are number of people who use legacy Cisco VPN client to connect IKEv1 remote-access IPSec VPN.
