Configure the ASA 8.x with Adaptive Security Device Manager (ASDM) 6.x
- Choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies, and choose the Group Policy in which you want to enable local LAN access. ...
- Click Split Tunneling.
- Uncheck the Inherit box for Split Tunnel Policy, and chose Tunnel Network List Below.
- Connect to the ASA > Go to enable mode > Then to global configuration mode > Create an ACL that permits traffic from the network behind the ASA to any. ...
- Add the split tunnel to the policy you are using for you remote VPN, (if you are unsure issue a show run group-policy).
How to configure the SSL VPN on ASA with Split tunneling?
Complete these steps in order to configure the SSL VPN on ASA with split tunneling: Choose Configuration > Remote Access VPN > Network (Client) Access > Address Management > Address Pools > Add in order to create an IP address pool vpnpool. Click Apply. Equivalent CLI Configuration:
How to configure split tunneling for remote access VPN?
Complete these steps in order to configure your tunnel group to allow split tunneling for the users in the group. Choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies, and choose the Group Policy in which you want to enable local LAN access. Then click Edit.
How do I Turn Off Split tunneling in ASDM?
1. Launch the ASDM > Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Select your policy. 2. Edit > Select Advanced > Split Tunneling. 3. Next to Policy > Untick “Inherit” > Change to “Tunnel Network List Below”.
What is split tunneling and how do I enable it?
What is split tunneling? This is the process of letting a remote VPN user browse the web, and access local resources etc, from their location whilst connected to your VPN in this case via SSLVPN, but also from WebVPN or IPSEC VPN. Option 1 Enable Split Tunnel via Command Line.

Does Cisco AnyConnect allow split tunneling?
Dynamic Split Tunnel Include AnyConnect will send only the domains listed in the configuration over the secure vpn tunnel and all other traffic will be sent in the clear.
What is split tunneling in remote access VPN?
VPN Split Tunneling Definition Virtual private network (VPN) split tunneling lets you route some of your application or device traffic through an encrypted VPN, while other applications or devices have direct access to the internet.
How do I split tunnel VPN?
Get a VPN client with split tunneling Go to Settings > Network. Enable Split Tunnel and Allow LAN Traffic. Click Add Application and select a program. Select Bypass VPN if you want the program to stay connected to your home network.
Should you split tunnel VPN?
You should use VPN split tunneling if you want to protect sensitive data without sacrificing your internet speeds. If you're happy to split your online activity between things you want to keep private and things you're not worried about, then VPN split tunneling could work well for you.
What are the negative effects of split tunneling?
The cons of split tunneling: security compromises If the corporate VPN redirects internet traffic through a central point, then it can also redirect that traffic through system security devices such as intrusion prevention devices (IPS) for do deep packet inspection to look for malicious content.
What is a split tunnel VPN describe how a split tunnel VPN can add a layer of security while users are accessing applications via remote access?
Split Tunneling is a VPN feature that allows users to direct a portion of their internet traffic through an encrypted virtual private network while leaving the rest to be routed through a separate tunnel on the open network.
What is the difference between a tunnel mode VPN and a split tunneling VPN?
VPN Connection Types Full tunnel is generally recommended because it is more secure. Split Tunnel - Routes and encrypts all OSU-bound requests over the VPN. Traffic destined to sites on the Internet (including Zoom, Canvas, Office 365, and Google) does not go through the VPN server in split tunnel mode.
Is split tunneling insecure?
Split tunneling introduces some security challenges. Any data that does not traverse a secure VPN is not protected by the corporate firewall, endpoint detection and response system, antimalware and other security mechanisms, so it may be accessible and/or intercepted by ISPs and malicious hackers.
How do I know if my split tunnel is enabled?
You can check that split tunneling is enabled by entering the Get-VPNConnection command again. The split tunneling field should now be set to True.
Does ExpressVPN use split tunneling?
ExpressVPN for Mac, Windows, and Android With the split-tunneling feature in the ExpressVPN apps for Mac, Windows and Android, select which apps use the VPN and which apps don't when you're connected to ExpressVPN. (Split tunneling is not available for macOS 11 and above.)
What is the difference between a tunnel mode VPN and a split tunneling VPN?
VPN Connection Types Full tunnel is generally recommended because it is more secure. Split Tunnel - Routes and encrypts all OSU-bound requests over the VPN. Traffic destined to sites on the Internet (including Zoom, Canvas, Office 365, and Google) does not go through the VPN server in split tunnel mode.
What is split tunneling Nordvpn?
Split tunneling is an advanced VPN feature that lets you choose which apps need VPN protection and which can access the internet directly. The first group benefits from the safety of the secure tunnel of your VPN, while the second group enjoys faster speeds and access to local services.
What does full tunnel VPN mean?
In a full-tunnel VPN scenario, whenever the user connects to the enterprise network, all network connections go through the enterprise network. Whenever the user starts a new YouTube video or Netflix movie, all network packets traverse through the enterprise network.
How do I know if my split tunnel is enabled?
You can check that split tunneling is enabled by entering the Get-VPNConnection command again. The split tunneling field should now be set to True.
Introduction
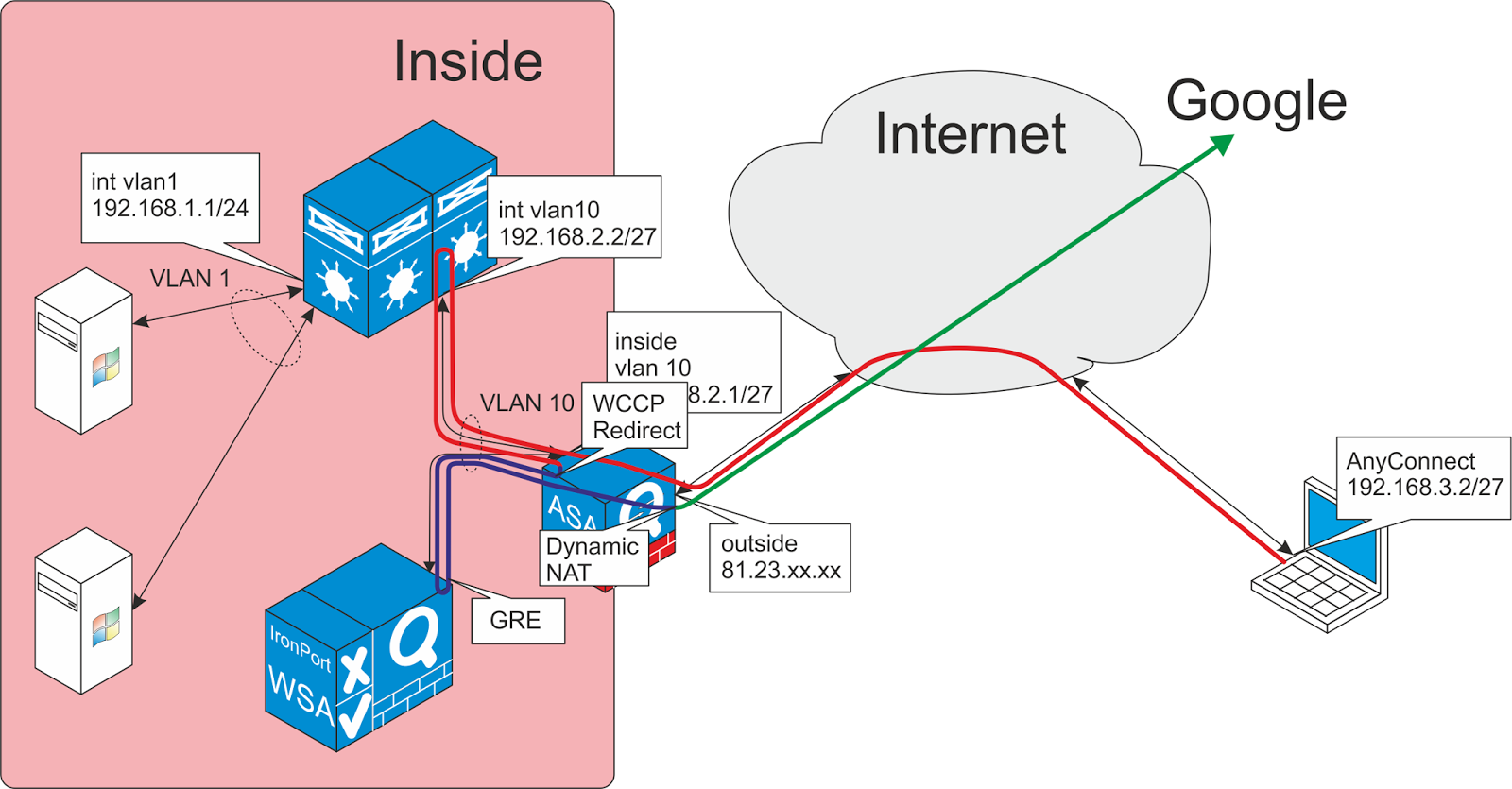
This document provides step-by-step instructions on how to allow Cisco AnyConnect VPN client access to the Internet while they are tunneled into a Cisco Adaptive Security Appliance (ASA) 8.0.2. This configuration allows the client secure access to corporate resources via SSL while giving unsecured access to the Internet using split tunneling.
Prerequisites
Ensure that you meet these requirements before you attempt this configuration:
Background Information
The Cisco AnyConnect VPN Client provides secure SSL connections to the security appliance for remote users. Without a previously installed client, remote users enter the IP address in their browser of an interface configured to accept SSL VPN connections.
Configure
In this section, you are presented with the information to configure the features described in this document.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Problem
This is a simple job to do from command line, however the world is full of people who would rather spend an hour in the ASDM working out how to do it! So I’ve included both methods.
What is split tunneling?
This is the process of letting a remote VPN user browse the web, and access local resources etc, from their location whilst connected to your VPN in this case via SSLVPN, but also from WebVPN or IPSEC VPN.
Option 1 Enable Split Tunnel via Command Line
1. Connect to the ASA > Go to enable mode > Then to global configuration mode > Create an ACL that permits traffic from the network behind the ASA to any. ( Note: Add additional ACL’s for additional internal networks).
Enable Split Tunnel on an older (PIX Firewall)
Type help or '?' for a list of available commands. PetesPIX> enable Password: ****** PetesPIX# configure terminal PetesPIX (config)# access-list Split-Tunnel permit ip 10.0.0.0 255.255.255.0 any PetesPIX (config)# vpngroup RemoteVPN split-tunnel Split-Tunnel
Option 2 Enable Split Tunnel via ASDM
1. Launch the ASDM > Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Select your policy.
Problem
I have answered a lot of questions in forums, that are worded something like, “When I have a remote client connected to my firewall VPN they lose Internet access!” Traditionally that’s exactly what the ‘default’ remote VPN solution (IPSEC or AnyConnect) gave you.
Solution
At this point I’m assuming you have a remote VPN setup and working, if not you need to do that first, here are some walk-throughs I’ve already done to help you set that up.
Option 1 (Split Tunneling)
Rather than re-invent the wheel, I’ve already covered this before in the following article.
Option 2 (Tunnel All Split Tunneling)
1. Connect to the ASA > Go to enable mode > Then to global configuration mode.

Introduction
Prerequisites
- Requirements
This document assumes that a working remote access VPN configuration already exists on the ASA. Refer to PIX/ASA 7.x as a Remote VPN Server using ASDM Configuration Exampleif one is not already configured. - Components Used
The information in this document is based on these software and hardware versions: 1. Cisco ASA 5500 Series Security Appliance Software version 7.x and later 2. Cisco Systems VPN Client version 4.0.5 Note: This document also contains the PIX 6.x CLI configuration that is compatibl…
Background Information
- In a basic VPN Client to ASA scenario, all traffic from the VPN Client is encrypted and sent to the ASA no matter what its destination is. Based on your configuration and the number of users supported, such a set up can become bandwidth intensive. Split tunneling can work to alleviate this problem since it allows users to send only that traffic which is destined for the corporate ne…
Verify
- Follow the steps in these sections in order to verify your configuration. 1. Connect with the VPN Client 2. View the VPN Client Log 3. Test Local LAN Access with Ping
Troubleshoot
- Limitation with Number of Entries in a Split Tunnel ACL
There is a restriction with the number of entries in an ACL used for split tunnel. It is recommended not to use more than 50-60 ACE entries for satisfactory functionality. You are advised to implement the subnetting feature to cover a range of IP addresses.
Related Information
Introduction
Prerequisites
- Requirements
Ensure that you meet these requirements before you attempt this configuration: 1. ASA Security Appliance needs to run version 8.x 2. Cisco AnyConnect VPN Client 2.x Note: Download the AnyConnect VPN Client package (anyconnect-win*.pkg) from the Cisco Software Download (regi… - Components Used
The information in this document is based on these software and hardware versions: 1. Cisco 5500 Series ASA that runs software version 8.0(2) 2. Cisco AnyConnect SSL VPN Client version for Windows 2.0.0343 3. PC which runs Microsoft Visa, Windows XP SP2 or Windows 2000 Prof…
Background Information
- The Cisco AnyConnect VPN Client provides secure SSL connections to the security appliance for remote users. Without a previously installed client, remote users enter the IP address in their browser of an interface configured to accept SSL VPN connections. Unless the security appliance is configured to redirect http:// requests to https://, users must enter the URL in the form https://…
Configure
- In this section, you are presented with the information to configure the features described in this document. Note: Use the Command Lookup Tool (registeredcustomers only) to obtain more information on the commands used in this section.
Verify
- Use this section to confirm that your configuration works properly. The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of showcommand output. 1. show webvpn svc—Displays the SVC images stored in the ASA flash memory. ciscoasa#show webvpn svc1. disk0:/anyconnect-win-2.0.0343-k9.pkg 1 CIS…
Troubleshoot
- This section provides information you can use to troubleshoot your configuration. 1. vpn-sessiondb logoff name<username> —Command to logoff the SSL VPN session for the particular username. ciscoasa#vpn-sessiondb logoff name ssluser1Do you want to logoff the VPN session(s)? [confirm] YINFO: Number of sessions with name "ssluser1" logged off : 1ciscoasa#C…
Related Information