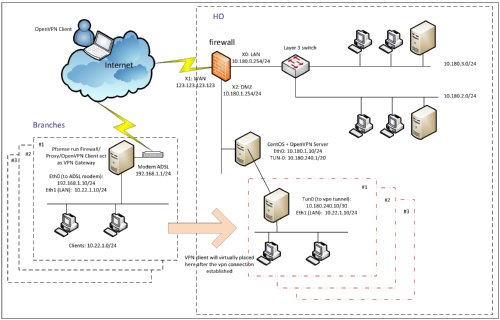
How to setup a remote access VPN?
Use a VPN Router with the built-in VPN server capability
- Launch a browser window from your PC connected to the routers’ network
- Enter the router IP address in the search to login into your router
- Enter the username and password of your router and login into it.
- Go to the Settings page and select VPN Service or setup page.
- Enable the VPN service by selecting the checkbox and apply
Can the Cisco ASA be used as a router?
The ASA is NOT a router, though and while you can do things on the ASA that can make it act something like a router it is important to understand the differences between true routing and what the ASA actually does.
How to connect Cisco ASA on PC?
- Connect the network cable from the modem to port 0 (default outside port) on the ASA.
- Connect your computer to one of the other ports on the ASA, which should be on the inside network by default.
- Open a browser on your computer and go to 192.168.
- Click Run ASDM.
- Log in.
How to setup a Cisco VPN?
How To Setup Vpn Cisco Rv340? February 18, 2022 by Cathie. Select Settings, VPN, and then add a VPN connection. Enter the public WAN IP address provided by your ISP, select a VPN type as PPTP, and enter the user name and password in the section below. The newly created PPTP VPN network adapter must now be connected.

What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
Can Cisco ASA do route based VPN?
ASA supports route-based VPN with the use of Virtual Tunnel Interfaces (VTIs) in version 9.8 and later.
How do I access my Cisco ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
Is Cisco AnyConnect a remote access VPN?
Anyconnect VPN offers full network access. The remote user will use the anyconnect client to connect to the ASA and will receive an IP address from a VPN pool, allowing full access to the network. Above we have the ASA firewall with two security zones: inside and outside.
Can a route based VPN connect to a policy-based VPN?
Route-based VPNs support NAT for st0 interfaces. Policy-based VPNs cannot be used if NAT is required for tunneled traffic. Proxy ID is supported for both route-based and policy-based VPNs.
What is the difference between route based and policy-based VPN?
Policy-based VPNs encrypt and encapsulate a subset of traffic flowing through an interface according to a defined policy (an access list). A route based VPN creates a virtual IPSec interface, and whatever traffic hits that interface is encrypted and decrypted according to the phase 1 and phase 2 IPSec settings.
What VPN types are supported by ASA?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
How do I configure AnyConnect on ASA 5505?
Quick guide: AnyConnect Client VPN on Cisco ASA 5505Click on Configuration at the top and then select Remote Access VPN.Click on Certificate Management and then click on Identity Certificates.Click Add and then Add a new identity certificate.Click New and enter a name for your new key pair (ex: VPN)More items...•
How do I configure AnyConnect?
5 Steps to Configure Cisco AnyConnect VPNConfigure AAA authentication. The first thing to configure is AAA authentication. ... Define VPN protocols. When users connect their VPN, they'll need an IP address for the VPN session. ... Configure tunnel groups. ... Set group policies. ... Apply the configuration. ... Authenticating logic flow.
What type of VPN is Cisco AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
What is site to site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
What are route-based VPN?
A route-based VPN is a configuration in which an IPsec VPN tunnel created between two end points is referenced by a route that determines which traffic is sent through the tunnel based on a destination IP address.
Does FTD support route-based VPN?
In November 2020 Cisco released the Firepower Threat Defence (FTD) and Firepower Management Centre (FMC) version 6.7. Supported from this version is the long-awaited Virtual Tunnel Interface (VTI) for route-based site-to-site VPNs.
Does Palo Alto support policy based VPN?
Palo Alto Network firewalls do not support policy-based VPNs. The policy-based VPNs have specific security rules/policies or access-lists (source addresses, destination addresses and ports) configured for permitting the interesting traffic through IPSec tunnels.
What is FMC in Cisco?
The Cisco Secure Firewall Management Center (FMC) is your administrative nerve center for managing critical Cisco network security solutions. It provides complete and unified management over firewalls, application control, intrusion prevention, URL filtering, and advanced malware protection.
What is ACL in VPN?
Note : An ACL for VPN traffic uses the source and destination IP addresses after Network Address Translation (NAT). NAT Exemption (optional): Typically, there must be no NAT performed on the VPN traffic. In order to exempt that traffic, you must create an identity NAT rule.
What is the default debug level in ASA?
Caution: On the ASA, you can set various debug levels; by default, level 1 is used. If you change the debug level, the verbosity of the debugs might increase. In, this case level 127 provides sufficient details for troubleshooting. Do this with caution, especially in production environments.
Can you use a ping to verify VPN connection?
You can use a ping in order to verify basic connectivity.
Can you edit IPsec files?
On Ubuntu, you would modify these two files with configuration parameters to be used in the IPsec tunnel. You can use your favorite editor to edit them.
Cisco ASA non-VPN Configurations
The interface configuration is self-explanatory, ASA has two interfaces, one for the user and another one for the Internet. The default route is pointing to the ISP router with a static route. There are two objects, one for the branch user subnet and another one for the HQ webserver subnet.
ASA VPN configurations IKEv1
Please note that if you already have another VPN tunnel then most likely most of the configurations are already done for you. So, please make sure not to change or override them.
ASA VPN configurations IKEv2
I'm going to remove all the IKEv1 related configurations and then re-configure the VPN using IKEv2. The configuration is almost identical to IKEv1.