How to connect Cisco ASA on PC?
- Connect the network cable from the modem to port 0 (default outside port) on the ASA.
- Connect your computer to one of the other ports on the ASA, which should be on the inside network by default.
- Open a browser on your computer and go to 192.168.
- Click Run ASDM.
- Log in.
How to install ASDM on Cisco ASA?
That said, here goes:
- Make sure ASDM image has been uploaded to the ASA you're needing to connect to.
- Enable HTTP on the ASA you are wanting to connect to
- Browse to the ASA's IP address
- Download ASDM installer from the Firewall (after authenticating)
How do I install a Cisco VPN?
Installation
- After install please reboot your device.
- Launch/open Cisco AnyConnect program. You will need to enter the Server name the first time: Faculty and staff please enter: vpn.net.rpi.edu Students please enter: vpn.stu.rpi.edu
- Click connect.
- Enter your RCS username and password to login.
How to start Cisco VPN service?
How to start cisco vpn service in windows 10. Connect to the Cisco AnyConnect VPN Client Once Downloaded Windows. Verify that the connection address is vpnexcelsioredu. After clicking OKat the next screen click the Cisco AnyConnect. Start All Apps Cisco Cisco AnyConnect Secure Mobility Client. Icon located at the lower-right corner.
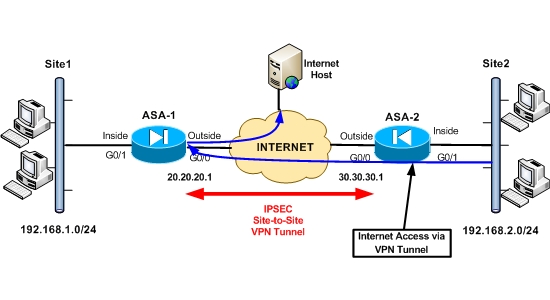
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
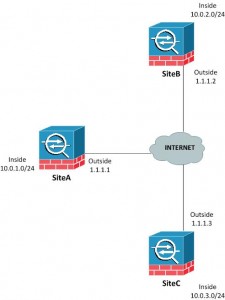
What is ASA site-to-site VPN?
Site-to-site IPsec VPNs are used to “bridge” two distant LANs together over the Internet. Normally on the LAN we use private addresses so without tunneling, the two LANs would be unable to communicate with each other.
What is difference between site-to-site VPN and IPSec VPN?
Site-to-Site VPN provides a site-to-site IPSec connection between your on-premises network and your virtual cloud network (VCN). The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
Is Cisco AnyConnect a remote access VPN?
Anyconnect VPN offers full network access. The remote user will use the anyconnect client to connect to the ASA and will receive an IP address from a VPN pool, allowing full access to the network. Above we have the ASA firewall with two security zones: inside and outside.
What is the difference between IKEv1 and IKEv2?
IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). IKEv2 has Built-in NAT-T functionality which improves compatibility between vendors. IKEv2 supports EAP authentication. IKEv2 has the Keep Alive option enabled as default.
What is phase1 and Phase 2 in VPN?
VPN negotiations happen in two distinct phases: Phase 1 and Phase 2. The main purpose of Phase 1 is to set up a secure encrypted channel through which the two peers can negotiate Phase 2. When Phase 1 finishes successfully, the peers quickly move on to Phase 2 negotiations.
What are the two types of site to site VPNs?
VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
Which ones are two main types of site to site VPN?
Virtual Private Network (VPN) is basically of 2 types:Remote Access VPN: Remote Access VPN permits a user to connect to a private network and access all its services and resources remotely. ... Site to Site VPN: A Site-to-Site VPN is also called as Router-to-Router VPN and is commonly used in the large companies.
Why do we need a site to site VPN?
A site-to-site virtual private network (VPN) is a connection between two or more networks, such as a corporate network and a branch office network. Many organizations use site-to-site VPNs to leverage an internet connection for private traffic as an alternative to using private MPLS circuits.
What type of VPN is Cisco AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
How do I enable Cisco AnyConnect VPN through remote Desktop?
The steps would be:Log into the ASDM.Go to Configuration, Remote Access VPN, Anyconnect Client Profile.Click Add and create a new profile and choose the Group Policy it should apply to.Click OK, and then at the Profile screen click "Apply" at the bottom (important)More items...•
Which is better SSL or IPSec VPN?
When it comes to corporate VPNs that provide access to a company network rather than the internet, the general consensus is that IPSec is preferable for site-to-site VPNs, and SSL is better for remote access.
What is the difference between VPN and SSL VPN?
Whereas an IPsec VPN enables connections between an authorized remote host and any system inside the enterprise perimeter, an SSL VPN can be configured to enable connections only between authorized remote hosts and specific services offered inside the enterprise perimeter.
Is site-to-site VPN secure?
Secure Connectivity: All traffic flowing over a site-to-site VPN is encrypted. This means that any business data crossing over the public Internet is encrypted, protecting it against eavesdropping and modification.
How does client to site VPN Work?
Data is transmitted from your client machine to a point in your VPN network. The VPN point encrypts your data and sends it through the internet. Another point in your VPN network decrypts your data and sends it to the appropriate internet resource, such as a web server, an email server, or your company's intranet.
Cisco ASA non-VPN Configurations
The interface configuration is self-explanatory, ASA has two interfaces, one for the user and another one for the Internet. The default route is pointing to the ISP router with a static route. There are two objects, one for the branch user subnet and another one for the HQ webserver subnet.
ASA VPN configurations IKEv1
Please note that if you already have another VPN tunnel then most likely most of the configurations are already done for you. So, please make sure not to change or override them.
ASA VPN configurations IKEv2
I'm going to remove all the IKEv1 related configurations and then re-configure the VPN using IKEv2. The configuration is almost identical to IKEv1.
How many interfaces does an ASA have?
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
What is VPN_POLICY?
The group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
When remote users connect to our WebVPN, do they have to use HTTPS?
The following option is not required but useful, whenever someone accesses the ASA through HTTP then they will be redirected to HTTPS:
What is AnyConnect VPN?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN. AnyConnect VPN. The clientless WebVPN method does not require a VPN client to be installed on the user’s computer. You just open your web browser, ...
What happens when a VPN user terminates a session?
Normally when the remote VPN user terminates the session, the anyconnect installer will be uninstalled. The anyconnect keep-installer installed command leaves it installed on the user’s computer.
What happens when you have an inbound access list?
When you have an inbound access-list on the outside interface then all your decrypted traffic from the SSL WebVPN has to match the inbound access-list. You can either create some permit statements for the decrypted traffic or you can just tell the ASA to let this traffic bypass the access-list:
Why does my client tries to download AnyConnect?
The client tries to download the Anyconnect automatically, this is because of the anyconnect ask none default anyconnect command that we used. Since we are using a self-signed certificate you will get the following error message:
What is the IP address of AnyConnect?
You can see that we received IP address 192.168.10.100 (the first IP address from the VPN pool). Anyconnect creates an additional interface, just like the legacy Cisco VPN client does.
What is an ayconnECT_policy?
The group policy is called “ANYCONNECT_POLICY” and it’s an internal group policy which means that we configure it locally on the ASA. An external group policy could be on a RADIUS server.