Configuration Remote Access VPN on ASA interface configuration: hostname (config)# interface ethernet0 hostname (config-if)# ip address 10.10.4.200 255.255.0.0 hostname (config-if)# nameif outside hostname (config)# no shutdown
Full Answer
How to setup a remote access VPN?
Use a VPN Router with the built-in VPN server capability
- Launch a browser window from your PC connected to the routers’ network
- Enter the router IP address in the search to login into your router
- Enter the username and password of your router and login into it.
- Go to the Settings page and select VPN Service or setup page.
- Enable the VPN service by selecting the checkbox and apply
Can the Cisco ASA be used as a router?
The ASA is NOT a router, though and while you can do things on the ASA that can make it act something like a router it is important to understand the differences between true routing and what the ASA actually does.
How to connect Cisco ASA on PC?
- Connect the network cable from the modem to port 0 (default outside port) on the ASA.
- Connect your computer to one of the other ports on the ASA, which should be on the inside network by default.
- Open a browser on your computer and go to 192.168.
- Click Run ASDM.
- Log in.
How to setup a Cisco VPN?
How To Setup Vpn Cisco Rv340? February 18, 2022 by Cathie. Select Settings, VPN, and then add a VPN connection. Enter the public WAN IP address provided by your ISP, select a VPN type as PPTP, and enter the user name and password in the section below. The newly created PPTP VPN network adapter must now be connected.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
How many interfaces does an ASA have?
What is the default LAN to LAN tunnel group?
What files can Cisco AnyConnect have?
What is the first phase of ISAKMP?
Is Mobike available on ASA?
Do you need a mask for a VPN?
See 4 more
About this website
How do I access my ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
What is remote access VPN Cisco?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network such as the Internet. Remote access VPNs for IPsec IKEv2. 8.4(1) Added IPsec IKEv2 support for the AnyConnect Secure Mobility Client.
How do I enable VPN on ASA?
Set up VPN on a Cisco ASA deviceOpen ASDM.Go to Wizards VPN Wizards. IPsec (IKEv1) Remote Access VPN Wizard.Bypass the interface access lists: ... Click Next.Choose Microsoft Windows client using L2TP over IPsec and check the box for MS-CHAP-V2.Click Next.Authenticate the machine: ... Click Next.More items...
How configure AnyConnect Cisco ASA?
5 Steps to Configure Cisco AnyConnect VPNConfigure AAA authentication. The first thing to configure is AAA authentication. ... Define VPN protocols. When users connect their VPN, they'll need an IP address for the VPN session. ... Configure tunnel groups. ... Set group policies. ... Apply the configuration. ... Authenticating logic flow.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How does VPN remote access work?
The remote access VPN does this by creating a tunnel between an organization's network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
How is Cisco VPN configured?
Steps for setting up a VPNStep 1: Line up key VPN components. ... Step 2: Prep devices. ... Step 3: Download and install VPN clients. ... Step 4: Find a setup tutorial. ... Step 5: Log in to the VPN. ... Step 6: Choose VPN protocols. ... Step 7: Troubleshoot. ... Step 8: Fine-tune the connection.
How do I configure IPSec on ASA firewall?
To configure the IPSec VPN tunnel on Cisco ASA 55xx:Configure IKE. Establish a policy for the supported ISAKMP encryption, authentication Diffie-Hellman, lifetime, and key parameters. ... Create the Access Control List (ACL) ... Configure IPSec. ... Configure the Port Filter. ... Configure Network Address Translation (NAT)
Is Cisco AnyConnect SSL or IPSec?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
How do I configure AnyConnect on ASA 5505?
Quick guide: AnyConnect Client VPN on Cisco ASA 5505Click on Configuration at the top and then select Remote Access VPN.Click on Certificate Management and then click on Identity Certificates.Click Add and then Add a new identity certificate.Click New and enter a name for your new key pair (ex: VPN)More items...•
How does Cisco AnyConnect VPN client work?
When a user opens a VPN session using Cisco AnyConnect, the AnyConnect client connects to the adaptive security appliance using SSL. The client authenticates with the adaptive security appliance and is assigned an internal IP address on the network.
Does Cisco AnyConnect route all traffic?
With AnyConnect, the client passes traffic to all sites specified in the split tunneling policy you configured, and to all sites that fall within the same subnet as the IP address assigned by the ASA. For example, if the IP address assigned by the ASA is 10.1.
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.9
Bias-Free Language. The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality.
What is Security Association Lifetime - Cisco site to site VPN
Usage Guidelines IPSec security associations use shared secret keys. These keys and their security associations time out together. Assuming that the particular crypto map entry does not have lifetime values configured, when the router requests new security associations during security association negotiation, it will specify its global lifetime value in the request to the peer; it will use ...
Updated crypto map ACL on ASA, but entry not seen in ipsec sa
ASA5512 running 9.1(2) I see a strange issue on the ASA and want to confirm if this is normal operation. The crypto map “outside_cryptomap_1” doesn’t seem to have the ipsec sa details for the complete access-list entries. For example this is the entry for the source (vpn nat pool) to destination (...
Cisco ASA single isakmp policy for multiple crypto map
We are going to setup multiple site-to-site tunnels to our remote office and every tunnel configuration is identical (same hash,encryption etc).. The question is: Do I need to create a separate isakmp policy for each tunnel or do I just define a single policy and it will share the policy with multiple crypto map (phase 2) configurations?. I have the following policy:
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
Is Mobike available on ASA?
Mobike is available by default on ASAs since version 9.8 (1), meaning Mobike is “always on.” Mobike is enabled for each SA only when the client proposes it and the ASA accepts it. This negotiation occurs as part of the IKE_AUTH exchange.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
How many interfaces does an ASA have?
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
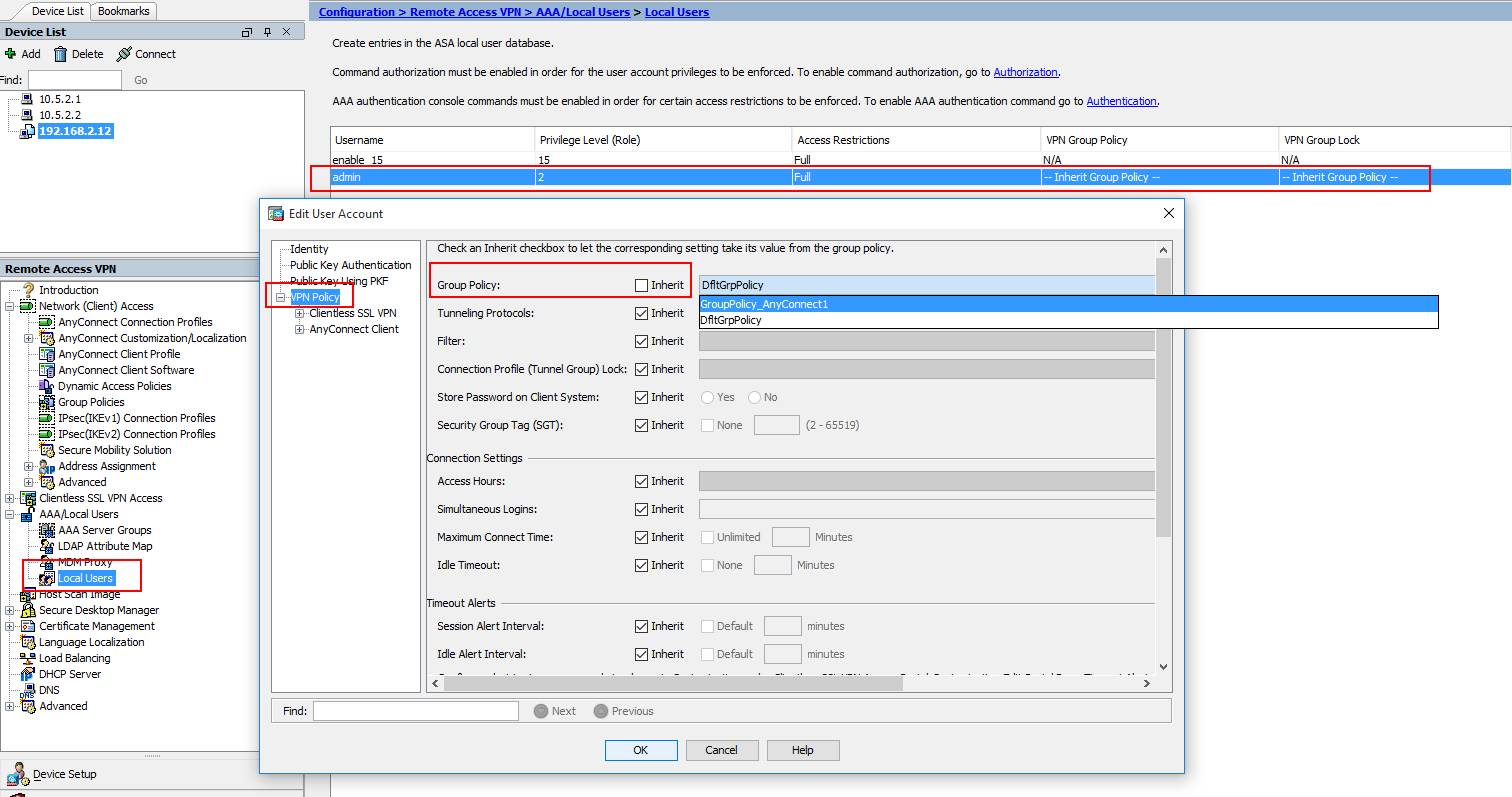
What is VPN_POLICY?
The group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
When remote users connect to our WebVPN, do they have to use HTTPS?
The following option is not required but useful, whenever someone accesses the ASA through HTTP then they will be redirected to HTTPS:
What happens when a VPN user terminates a session?
Normally when the remote VPN user terminates the session, the anyconnect installer will be uninstalled. The anyconnect keep-installer installed command leaves it installed on the user’s computer.
What happens when you have an inbound access list?
When you have an inbound access-list on the outside interface then all your decrypted traffic from the SSL WebVPN has to match the inbound access-list. You can either create some permit statements for the decrypted traffic or you can just tell the ASA to let this traffic bypass the access-list:
What is AnyConnect VPN?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN. AnyConnect VPN. The clientless WebVPN method does not require a VPN client to be installed on the user’s computer. You just open your web browser, ...
Why does my client tries to download AnyConnect?
The client tries to download the Anyconnect automatically, this is because of the anyconnect ask none default anyconnect command that we used. Since we are using a self-signed certificate you will get the following error message:
What is the IP address of AnyConnect?
You can see that we received IP address 192.168.10.100 (the first IP address from the VPN pool). Anyconnect creates an additional interface, just like the legacy Cisco VPN client does.
What is an ayconnECT_policy?
The group policy is called “ANYCONNECT_POLICY” and it’s an internal group policy which means that we configure it locally on the ASA. An external group policy could be on a RADIUS server.
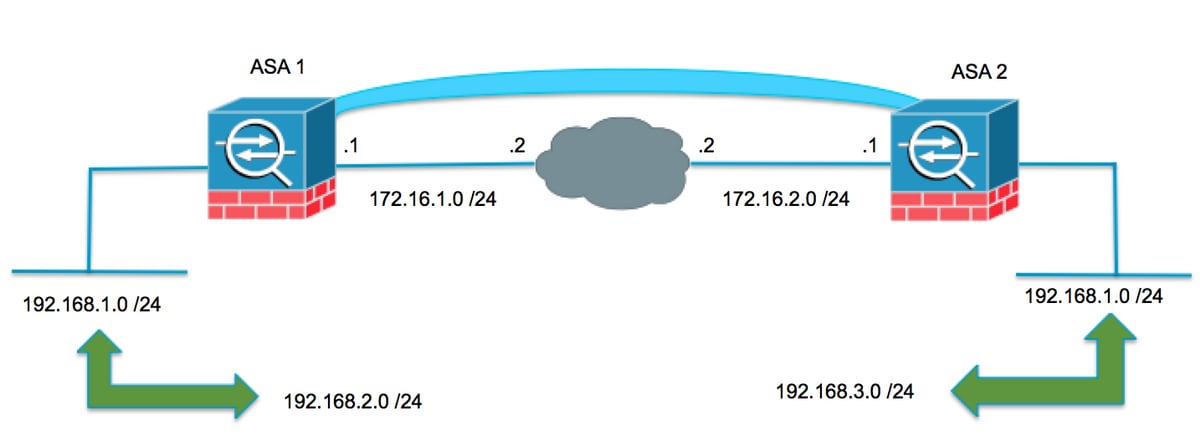
Cisco ASA non-VPN Configurations
The interface configuration is self-explanatory, ASA has two interfaces, one for the user and another one for the Internet. The default route is pointing to the ISP router with a static route. There are two objects, one for the branch user subnet and another one for the HQ webserver subnet.
ASA VPN configurations IKEv1
Please note that if you already have another VPN tunnel then most likely most of the configurations are already done for you. So, please make sure not to change or override them.
ASA VPN configurations IKEv2
I'm going to remove all the IKEv1 related configurations and then re-configure the VPN using IKEv2. The configuration is almost identical to IKEv1.
Overview
This is a configuration example of an AnyConnect SSL VPN on a Cisco ASA. This example uses ASA version 9.12 (3)12 and AnyConnect version 4.7.04056. You will need the AnyConnect packages for your OS on the ASA.
Configuration
Create the ip local pool to use for the SSL VPN. This is the subnet that users will get an IP address on when they connect to the SSL VPN. In this example, the users on the SSL VPN will get an IP address between 172.16.254.2 and 172.16.254.254.
Verification
In a web browser, navigate to the "group-url" that was configured for the SSL VPN. In this example, we'd navigate to https://1.1.1.1/ssl and login with the user we created. After logging in, the ASA would ask us to download the AnyConnect package for our OS. Once installed, we can login with the user we created and join the SSL VPN.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
Is Mobike available on ASA?
Mobike is available by default on ASAs since version 9.8 (1), meaning Mobike is “always on.” Mobike is enabled for each SA only when the client proposes it and the ASA accepts it. This negotiation occurs as part of the IKE_AUTH exchange.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.