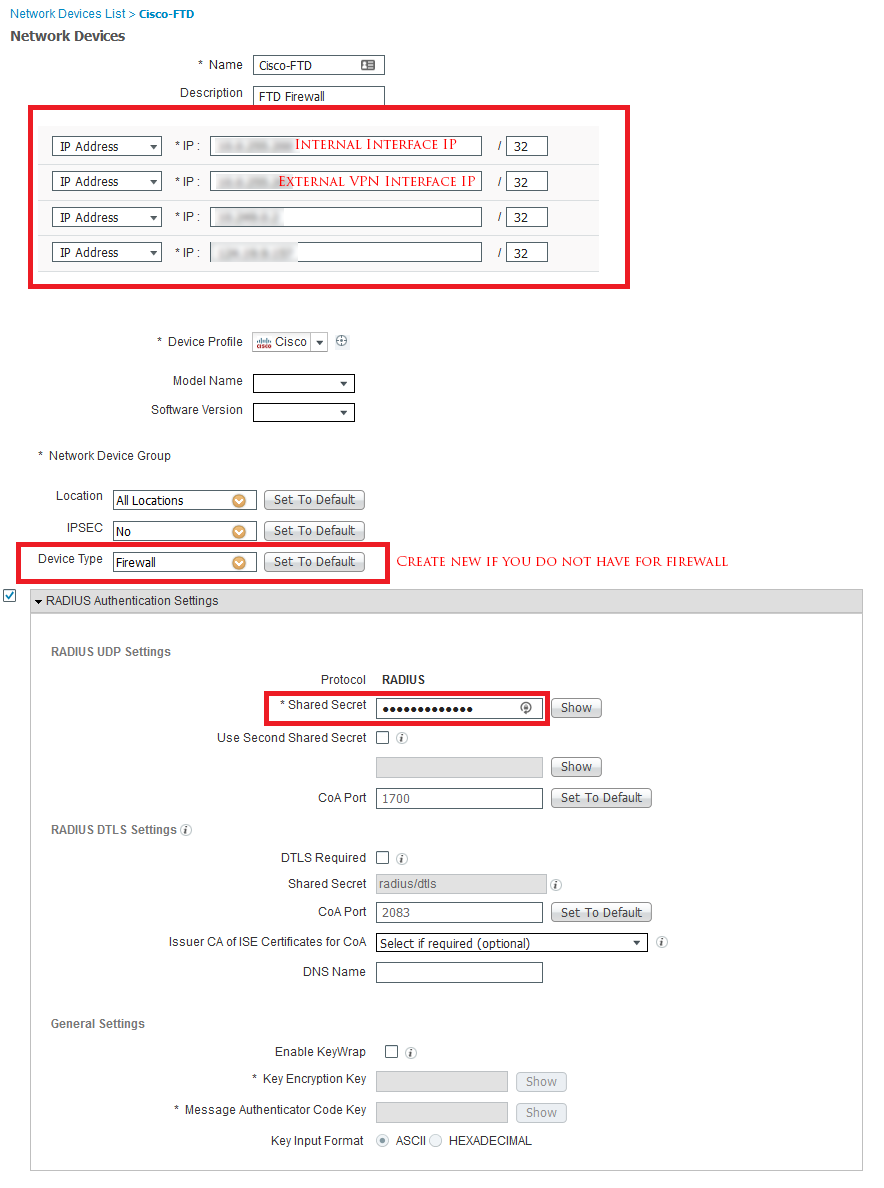
Procedure
- Choose Devices > VPN > Remote Access.
- Click (Add ()) Add to create a new Remote Access VPN Policy using a wizard that walks you through a basic policy configuration.
- Select the Target Devices and Protocols. ...
- Configure the Connection Profile and Group Policy settings. ...
Full Answer
How do I set up a VPN on firepower Management Center?
On your Firepower Management Center web interface, choose Devices > VPN > Remote Access. Existing remote access policies are listed. Select a remote access VPN policy and click Edit . Click Add and specify the following in the Add Connection Profile window: Connection Profile —Provide a name that the remote users will use for VPN connections.
How to configure remote access on firepower Management Center?
On your Firepower Management Center web interface, choose Devices > VPN > Remote Access. Step 2 Select a remote access policy and click Edit; or click Add to create a new remote access VPN policy.
How do I configure the remote access VPN connection profile?
Configure the remote access VPN connection profile. Click Device, then click Setup Connection Profile in the Remote Access VPN group. (Click View Configuration if you already configured a profile). For existing connections, click Edit to modify the profile. Configure the connection profile settings:
How do I change the remote access VPN policy for devices?
Ensure that you have configured remote access VPN using the Remote Access Policy wizard with a connection profile. On your Firepower Management Center web interface, choose Devices > VPN > Remote Access. Existing remote access policies are listed. Select a remote access VPN policy and click Edit .
What is the rule for remote access VPN?
Before deploying the remote access VPN policy, you must update the access control policy on the targeted Firepower Threat Defense device with a rule that allows VPN traffic. The rule must allow all traffic coming in from the outside interface , with source as the defined VPN pool networks and destination as the corporate network.
How to change VPN settings on Firepower?
On the Firepower Management Center web interface, choose Devices > VPN > Remote Access, choose and edit a listed RA VPN policy, then choose the Advanced tab.
What is AnyConnect profile?
An AnyConnect client profile is a group of configuration parameters stored in an XML file that the client uses to configure its operation and appearance. These parameters (XML tags) include the names and addresses of host computers and settings to enable more client features.
What is Cisco AnyConnect Secure Mobility?
The Cisco AnyConnect Secure Mobility client provides secure SSL or IPsec (IKEv2) connections to the Firepower Threat Defense device for remote users with full VPN profiling to corporate resources. Without a previously-installed client, remote users can enter the IP address of an interface configured to accept clientless VPN connections in their browser to download and install the AnyConnect client. The Firepower Threat Defense device downloads the client that matches the operating system of the remote computer. After downloading, the client installs and establishes a secure connection. In case of a previously installed client, when the user authenticates, the Firepower Threat Defense device, examines the version of the client, and upgrades the client if necessary.
How to upload Cisco AnyConnect client image?
You can upload the Cisco AnyConnect Mobility client image to the Firepower Management Center by using the AnyConnect File object. For more information, see FTD File Objects. For more information about the client image, see Cisco AnyConnect Secure Mobility Client Image .
What is the only VPN client?
The only supported VPN client is the Cisco AnyConnect Secure Mobility Client. No other clients or native VPNs are supported. Clientless VPN is not supported for VPN connectivity; it is only used to deploy the AnyConnect client using a web browser.
How to add IPv4 to address pool?
Select the Add icon in the Address Pools window to add a new IPv4 or IPv6 address pool. When you choose the IPv4 pool, provide a starting and ending IP address. When you choose to include a new IPv6 address pool, enter Number of Addresses in the range 1-16384. Select the Allow Overrides option to avoid conflicts with IP address when objects are shared across many devices. For more information, see Address Pools .
When a local realm is created and local users are added, can you add it to a remote access VPN to?
When a local realm is created and local users are added, you can add it to a remote access VPN to enable local user authentication.
What is the only VPN client?
The only supported VPN client is the Cisco AnyConnect Secure Mobility Client. No other clients or native VPNs are supported. Clientless VPN is not supported for VPN connectivity; it is only used to deploy the AnyConnect client using a web browser.
What is AnyConnect profile?
An AnyConnect client profile is a group of configuration parameters stored in an XML file that the client uses to configure its operation and appearance. These parameters (XML tags) include the names and addresses of host computers and settings to enable more client features.
What is Cisco AnyConnect Secure Mobility?
The Cisco AnyConnect Secure Mobility client provides secure SSL or IPsec (IKEv2) connections to the Firepower Threat Defense device for remote users with full VPN profiling to corporate resources. Without a previously-installed client, remote users can enter the IP address of an interface configured to accept clientless VPN connections in their browser to download and install the AnyConnect client. The Firepower Threat Defense device downloads the client that matches the operating system of the remote computer. After downloading, the client installs and establishes a secure connection. In case of a previously installed client, when the user authenticates, the Firepower Threat Defense device, examines the version of the client, and upgrades the client if necessary.
How to check VPN banner?
You can check the banner settings under Group Policy > General Settings> Banner. Edit the connect profile you have created for management VPN tunnel. Click Edit Group Policy> AnyConnect> Management Profile. Click the Management VPN Profiledrop-down and select the management profile file object you have created.
How to create an IP pool in Firepower?
Also, you can create an IP pool in Firepower Management Center using the Objects > Object Management > Address Pools path. For more information, see Address Pools .
Can Firepower Threat Defense resolve IP addresses?
Without DNS, the devices cannot resolve AAA server names, named URLs, and CA Servers with FQDN or Hostnames. It can only resolve IP addresses.
How to create a null route for remote access?
create a null route for network used for remote access users, defined in section c. Just go to Devices > Device Management > Edit > Routing > Static Route > Add route:
What version of VPN is Firepower Threat Defense?
This document provides a configuration example for Firepower Threat Defense (FTD) version 6.2.2 and later, that allows remote access VPN to use Transport Layer Security (TLS) and Internet Key Exchange version 2 (IKEv2). As a client, Cisco AnyConnect will be used, which is supported on multiple platforms.
What certificates are needed for AnyConnect?
Certificates are essential when you configure AnyConnect. Only RSA based certificates are supported in SSL and IPSec. Elliptic Curve Digital Signature Algorithm certificates (ECDSA) are supported in IPSec, but it's not possible to deploy new AnyConnect package or XML profile when ECDSA based certificate is used. It means that you can use it for IPSec, but you will have to predeploy AnyConnect package and XML profile to every user and any change in XML profile will have to be manually reflected on each client (bug: CSCtx42595 ). Additionally the certificate should have Subject Alternative Name extension with DNS name and/or IP address to avoid errors in web browsers.
How to connect to FTD?
To connect to FTD you need to open a browser, type DNS name or IP address pointing to the outside interface, in this example https://vpn.cisco.com. You will then have to login using credentials stored in RADIUS server and follow instructions on the screen. Once AnyConnect installs, you then need to put the same address in AnyConnect window and click Connect.
How to get a certificate for FTD appliance?
There are several methods to obtain a certificate on FTD appliance, but the safe and easy one is to create a Certificate Signing Request (CSR), sign it and then import certificate issued for public key, which was in CSR. Here is how to do that:
Can VPN traffic come from pool?
This means, that you need to allow traffic coming from pool of addresses on outside interface via Access Control Policy. Although the pre-filter or access-control rule is added intending to allow VPN traffic only, if clear-text traffic happens to match the rule criteria, it is erroneously permitted.
What version of FTD is required for FMC?
Note: This feature requires the FMC to be on version 6.7.0 whereas the managed FTD could be on any version higher than 6.3.0
What is RA VPN?
This document describes how to configure Remote Access VPN (RA VPN) with Lightweight Directory Access Protocol (LDAP) Authentication and Authorization on a Firepower Threat Defense (FTD) managed by a Firepower Management Center (FMC).
What is the No Access Group Policy?
The No-Access group-policy has the Simultaneous Login Per User setting set to 0 (To not allow users to be able to login if they receive the default No- Access group- policy).
Does RA VPN require FlexConfig?
This feature, with version 6.7.0, has now been integrated with the RA VPN configuration wizard on the FMC and does not require the use of FlexConfig anymore.
What is the rule for remote access VPN?
Before deploying the remote access VPN policy, you must update the access control policy on the targeted Firepower Threat Defense device with a rule that allows VPN traffic. The rule must allow all traffic coming in from the outside interface , with source as the defined VPN pool networks and destination as the corporate network.
How to change VPN settings on Firepower?
On the Firepower Management Center web interface, choose Devices > VPN > Remote Access, choose and edit a listed RA VPN policy, then choose the Advanced tab.
What is Cisco AnyConnect Secure Mobility?
The Cisco AnyConnect Secure Mobility client provides secure SSL or IPsec (IKEv2) connections to the Firepower Threat Defense device for remote users with full VPN profiling to corporate resources. Without a previously-installed client, remote users can enter the IP address of an interface configured to accept clientless VPN connections in their browser to download and install the AnyConnect client. The Firepower Threat Defense device downloads the client that matches the operating system of the remote computer. After downloading, the client installs and establishes a secure connection. In case of a previously installed client, when the user authenticates, the Firepower Threat Defense device, examines the version of the client, and upgrades the client if necessary.
How to upload Cisco AnyConnect client image?
You can upload the Cisco AnyConnect Mobility client image to the Firepower Management Center by using the AnyConnect File object. For more information, see FTD File Objects. For more information about the client image, see Cisco AnyConnect Secure Mobility Client Image .
What is the only VPN client?
The only supported VPN client is the Cisco AnyConnect Secure Mobility Client. No other clients or native VPNs are supported. Clientless VPN is not supported for VPN connectivity; it is only used to deploy the AnyConnect client using a web browser.
How to change Firepower policy?
On your Firepower Management Center web interface, choose Policies > Access Control > Identity and lick New Policy .
What to do if AAA server is on data interface?
If you place a AAA server on a data interface, be sure the management-only routing policies do not match traffic destined for a data interface. For example, if you have a default route through the Diagnostic interface, then traffic will never fall back to the data routing table. Use the show route management-only and show route commands to verify routing determination.
How to safeguard Firepower Management Center?
Security Requirements. To safeguard the Firepower Management Center, you should install it on a protected internal network. Although the FMC is configured to have only the necessary services and ports available, you must make sure that attacks cannot reach it (or any managed devices) from outside the firewall.
What ports does Firepower use?
By default, Firepower appliances are configured to connect to the internet on ports 443/tcp (HTTPS) and 80/tcp (HTTP). If you do not want your appliances to have direct access to the internet, you can configure a proxy server.
When to verify connectivity with syslog server?
Verify connectivity with the syslog server when configuring audit logging.
Do NTP servers need internet access?
Any appliance using an external NTP server must have internet access.
Can FMC and managed devices be connected?
If the FMC and its managed devices reside on the same network, you can connect the management interfaces on the devices to the same protected internal network as the FMC. This allows you to securely control the devices from the FMC.
Do you have to configure the cloud connection on both peers?
You must also configure the cloud connection on both peers (configuration is not synced).
Is inter-appliance communication encrypted?
Regardless of how you deploy your appliances, inter-appliance communication is encrypted. However, you must still take steps to ensure that communications between appliances cannot be interrupted, blocked, or tampered with; for example, with a distributed denial of service (DDoS) or man-in-the-middle attack.
The Remote Access VPN Identity Source
Firepower Threat Defense provides secure gateway capabilities that support remote access SSL and IPsec-IKEv2 VPNs. The full tunnel client, AnyConnect Secure Mobility Client, provides secure SSL and IPsec-IKEv2 connections to the security gateway for remote users.
Troubleshoot the Remote Access VPN Identity Source
For other related troubleshooting information, see Troubleshoot Realms and User Downloads, Troubleshoot User Control, and VPN Troubleshooting for Firepower Threat Defense.
Introduction
Requirements
- Cisco recommends that you have knowledge of these topics: 1. Basic VPN, TLS and IKEv2 knowledge 2. Basic Authentication, Authorization, and Accounting (AAA) and RADIUS knowledge 3. Experience with Firepower Management Center
Components Used
- The information in this document is based on these software and hardware versions: 1. Cisco FTD 6.2.2 2. AnyConnect 4.5
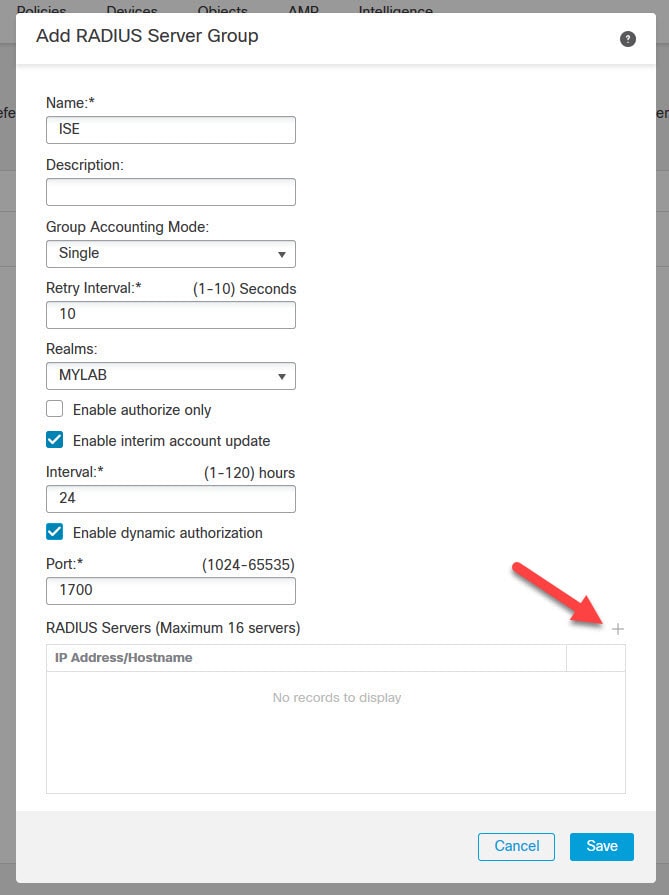
Configuration
- 2. Remote access wizard
1. Go to Devices > VPN > Remote Access > Add a new configuration. 2. Name the profile according to your needs, select FTD device: 1. In step Connection Profile, type Connection Profile Name, select Authentication Server and Address Poolswhich you have created earlier: 1. Click o…
Connection
- To connect to FTD you need to open a browser, type DNS name or IP address pointing to the outside interface, in this example https://vpn.cisco.com. Youwill then have to login using credentials stored in RADIUS server and follow instructions on the screen. Once AnyConnect installs, you then need to put the same address in AnyConnect window and click Connect.
Limitations
- Currently unsupported on FTD, but available on ASA: 1. Double AAA Authentication 2. Dynamic Access Policy 3. Host Scan 4. ISE posture 5. RADIUS CoA 6. VPN load-balancer 7. Local authentication (Enhancement: CSCvf92680 ) 8. LDAP attribute map 9. AnyConnect customization 10. AnyConnect scripts 11. AnyConnect localization 12. Per-app VPN 13. SCEP proxy 14. WSA in…
Security Considerations
- You need to remember that by default, sysopt connection permit-vpn option is disabled. This means, that you need to allow traffic coming from pool of addresses on outside interface via Access Control Policy. Although the pre-filter or access-control rule is added intending to allow VPN traffic only, if clear-text traffic happens to match the rule criteria, it is erroneously permitted…
Introduction
Prerequisites
- Requirements
Cisco recommends that you have knowledge of these topics: 1. Basic understanding of RA VPN working. 2. Understanding of navigating through the FMC. 3. Configuration of LDAP services on Microsoft Windows Server. - Components Used
The information in this document is based on these software versions: 1. Cisco Firepower Management Center (FMC) version 6.7.0 2. Cisco Firepower Threat Defense (FTD) version 6.7.0 3. Windows Windows Server 2012, configured as LDAP server Note: The information in this docum…
Background Information
- LDAP is an open, vendor-neutral, industry-standard application protocol to access and maintain distributed directory information services. An LDAP attribute map equates attributes that exist in the Active Directory (AD) or LDAP server with Cisco attribute names. Then, when the AD or LDAP server returns authentication responses to the FTD device during a remote access VPN connecti…
Configuration Steps on Fmc
- REALM / LDAP Server Configuration
Note: The steps mentioned are only required if configuring a new REALM / LDAP server. If you have a pre-exisiting server which could be used for authentication in RA VPN, then navigate to RA VPN Configuration. Step 1. Navigate to System> Integration, as shown in this image. Step 2. As … - RA VPN Configuration
The following steps are needed to configure the Group Policy which will be assigned to Authorized VPN users. If the Group Policy is already defined, move to Step 5. Step 1. Navigate to Objects > Object Management. Step 2: On the Left pane navigate to VPN > Group Policy. Step 3: …
Verify
- On the AnyConect client, login using Valid VPN User group Credentials and you get the correct group policy assigned by the LDAP Attribute map: From LDAP Debug Snippet (debug ldap 255) you can see there is a match on the LDAP Attribute Map: On the AnyConect client, login using an Invalid VPN User group Credentials and you get the No-Access group policy.