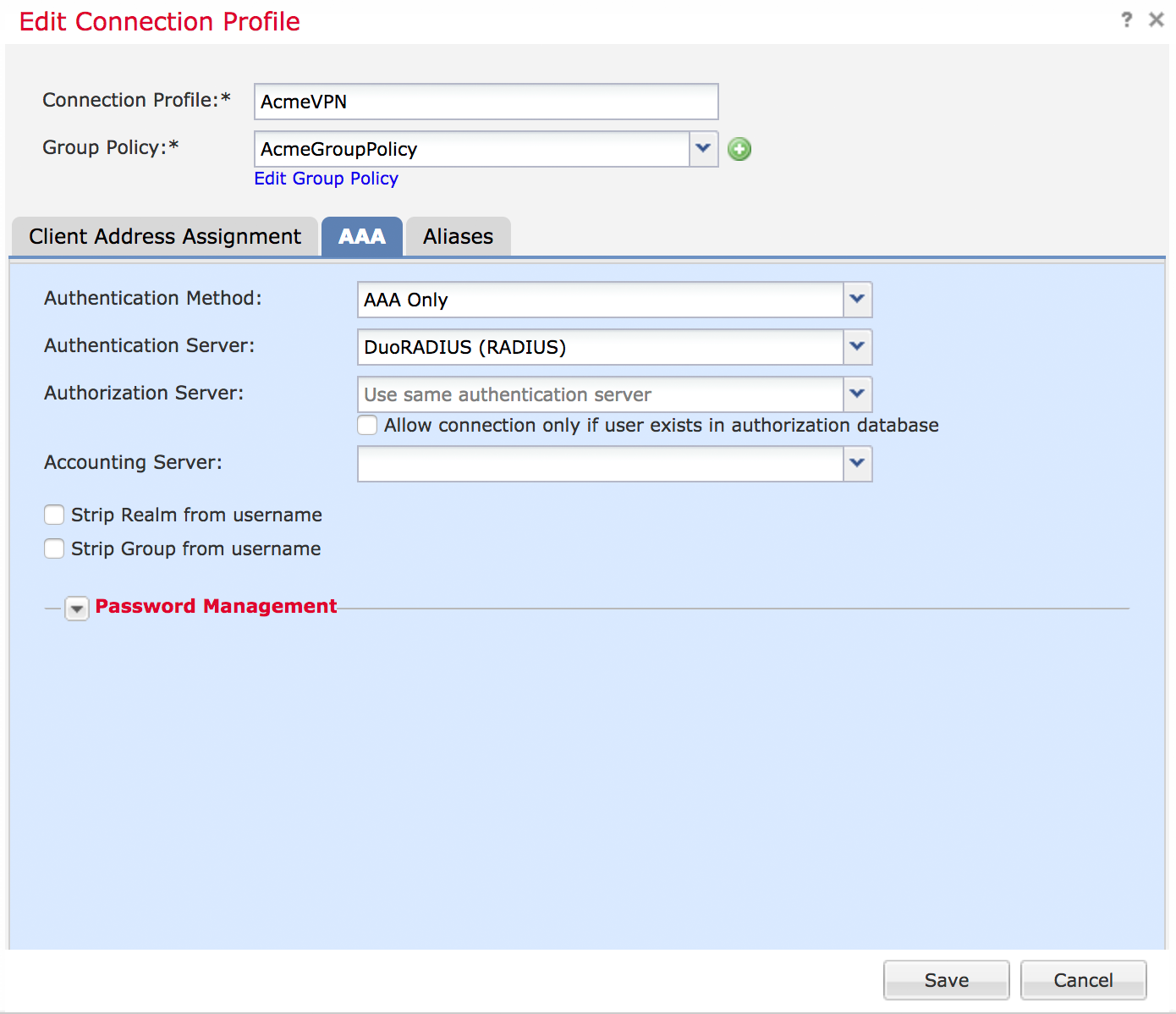
How does the RA VPN work with the FTD device?
The remote user starts an RA VPN session, using the AnyConnect client, with the FTD device. The FTD device sends a RADIUS Access-Request message for that user to the ISE server.
How do I configure remote access VPN with firepower threat defense?
You can use Firepower Device Manager to configure remote access VPN over SSL using the AnyConnect client sofware. When the AnyConnect client negotiates an SSL VPN connection with the Firepower Threat Defense device, it connects using Transport Layer Security (TLS) or Datagram Transport Layer Security (DTLS).
What types of VPN connections does the firepower Management Center support?
The Firepower Management Center supports the following types of VPN connections: Remote Access VPNs on Firepower Threat Defense devices. Remote access VPNs are secure, encrypted connections, or tunnels, between remote users and your company’s private network.
How do I configure web redirection on a Cisco FTD device?
Common Tasks —Select Web Redirection (CWA, MDM, NSP, CPP), then select Client Provisioning (Posture), and enter the name of the redirect ACL you configured on the FTD device. In Value, select Client Provisioning Portal if it is not already selected. The Attribute Details should show two cisco-av-pair values, for url-redirect-acl and url-redirect.
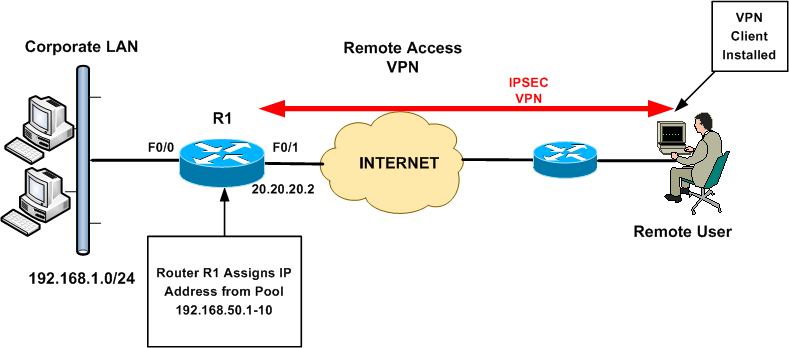
Does FTD support VPN?
VPN Topology The Firepower Management Center configures site-to-site VPNs on FTD devices only. You can select from three types of topologies, containing one or more VPN tunnels: • Point-to-point (PTP) deployments establish a VPN tunnel between two endpoints.
What is Cisco remote access VPN?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
How do I check the site-to-site VPN on Cisco FTD?
In order to monitor the tunnel status, navigate to the CLI of the FTD or ASA. From the FTD CLI, verify phase-1 and phase-2 with the command show crypto ikev2 sa. This section provides information you can use in order to troubleshoot your configuration.
What is the difference between Cisco firepower and FTD?
FTD runs on either the new 4100 and 9300 series or the ASA appliances (except 5585-X). FirePOWER appliances run only the legacy FirePOWER image and will not run FTD image.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How do I create a site to site VPN on Cisco FMC?
2:2812:24Configuring IPSec Site to Site VPN in FTD using FMC - YouTubeYouTubeStart of suggested clipEnd of suggested clipIn the stop VPN topology view let's click Add VPN. And you have two options fire power device andMoreIn the stop VPN topology view let's click Add VPN. And you have two options fire power device and fire threat defense click on fire power threat defense to configure site-to-site VPN foresight to FTD.
What is site to site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
What is Sysopt connection permit VPN?
The sysopt connection permit-vpn command allows all the traffic that enters the security appliance through a VPN tunnel to bypass interface access lists, while a vpn-filter is applied to postdecrypted traffic after it exits a tunnel and to preencrypted traffic before it enters a tunnel.
Is Cisco FTD a firewall?
In Chapter 1 you learned that Firepower Threat Defense software is unified software that provides next-generation firewall services, including the following: Stateful firewall capabilities. Static and dynamic routing.
What is difference between ASA and FTD?
The main difference between Cisco FTD and ASA is that ASA provides accessibility to VPN, IDS, IPS, anti-malware, and anti-virus services which are not available in Cisco FTD. Whereas, if we compare both the two security appliances based on their performance, FTD easily replaces ASA.
What is difference between FTD and FMC?
2:056:23FMC vs FDM - YouTubeYouTubeStart of suggested clipEnd of suggested clipThis FMC can manage FTD five power defence on any of your hardware power platform. And it can manageMoreThis FMC can manage FTD five power defence on any of your hardware power platform. And it can manage FTD virtual form it can manage firepower on running on sound K and eight K series platform.
How does Cisco VPN client work?
The VPN takes your computer's request and sends it to a website or system. The requested data is then forwarded back to you through that same secure connection. At CMU, we use the Cisco AnyConnect Secure Mobility Client to connect to the network through VPN.
What is VPN and why do I need it?
VPN stands for virtual private network. In basic terms, a VPN provides an encrypted server and hides your IP address from corporations, government agencies and would-be hackers. A VPN protects your identity even if you are using public or shared Wi-Fi, and your data will be kept private from any prying internet eyes.
Is Cisco AnyConnect VPN free?
Cisco AnyConnect is a free, easy to use, and worthwhile VPN client for Microsoft Windows computers. It's secure and doesn't require a lot of maintenance.
Is Cisco VPN good?
Great tool for managing remote workers The application offers a secure connection to corporate networks. It is quite easy to use and does not require much training for new employees when compared with other VPN applications.
What is remote access VPN?
Remote access VPNs are secure, encrypted connections, or tunnels, between remote users and your company’s private network. The connection consists of a VPN endpoint device, which is a workstation or mobile device with VPN client capabilities, and a VPN headend device, or secure gateway, at the edge of the corporate private network.
How Secure Should a VPN Connection Be?
Because a VPN tunnel typically traverses a public network, most likely the Internet, you need to encrypt the connection to protect the traffic. You define the encryption and other security techniques to apply using IKE polices and IPsec proposals.
How does a VPN work point to point?
In a point-to-point VPN topology, two endpoints communicate directly with each other. You configure the two endpoints as peer devices, and either device can start the secured connection.
Why use PKI in VPN?
Using a PKI improves the manageability and scalability of your VPN since you do not have to configure pre-shared keys between all the encrypting devices. Instead, you individually enroll each participating device with a CA server, which is explicitly trusted to validate identities and create an identity certificate for the device. When this has been accomplished, each participating peer sends their identity certificate to the other peer to validate their identities and establish encrypted sessions with the public keys contained in the certificates. See Certificate Enrollment Objects for details on enrolling FTD devices.
What is VPN connection?
A virtual private network (VPN) connection establish es a secure tunnel between endpoints over a public network such as the Internet.
Is Firepower Threat Defense VPN available?
There is no specific licensing for enabling Firepower Threat Defense VPN, it is available by default.
Can FTD devices pass through access control?
On a FTD device, by default no traffic is allowed to pass through access-control without explicit permission. VPN tunnel traffic as well, is not relayed to the endpoints until it has passed through Snort. Incoming tunnel packets are decrypted before being sent to the Snort process. Snort processes outgoing packets before encryption.
