Go to Devices > VPN > Remote Access > Add a new configuration. This will copy whole configuration along with certificates and AnyConnect packages to FTD appliance. To connect to FTD you need to open a browser, type DNS name or IP address pointing to the outside interface, in this example https://vpn.cisco.com.
Full Answer
How to set up remote access on FTD appliance?
2. Remote access wizard Go to Devices > VPN > Remote Access > Add a new configuration. This will copy whole configuration along with certificates and AnyConnect packages to FTD appliance.
What VPNs are supported with FTD secure gateway?
The only supported VPN client is the Cisco AnyConnect Secure Mobility Client. No other clients or native VPNs are supported. Clientless VPN is not supported for VPN connectivity; it is only used to deploy the AnyConnect client using a web browser. The following AnyConnect features are not supported when connecting to an FTD secure gateway:
How do I set up a VPN in FTD?
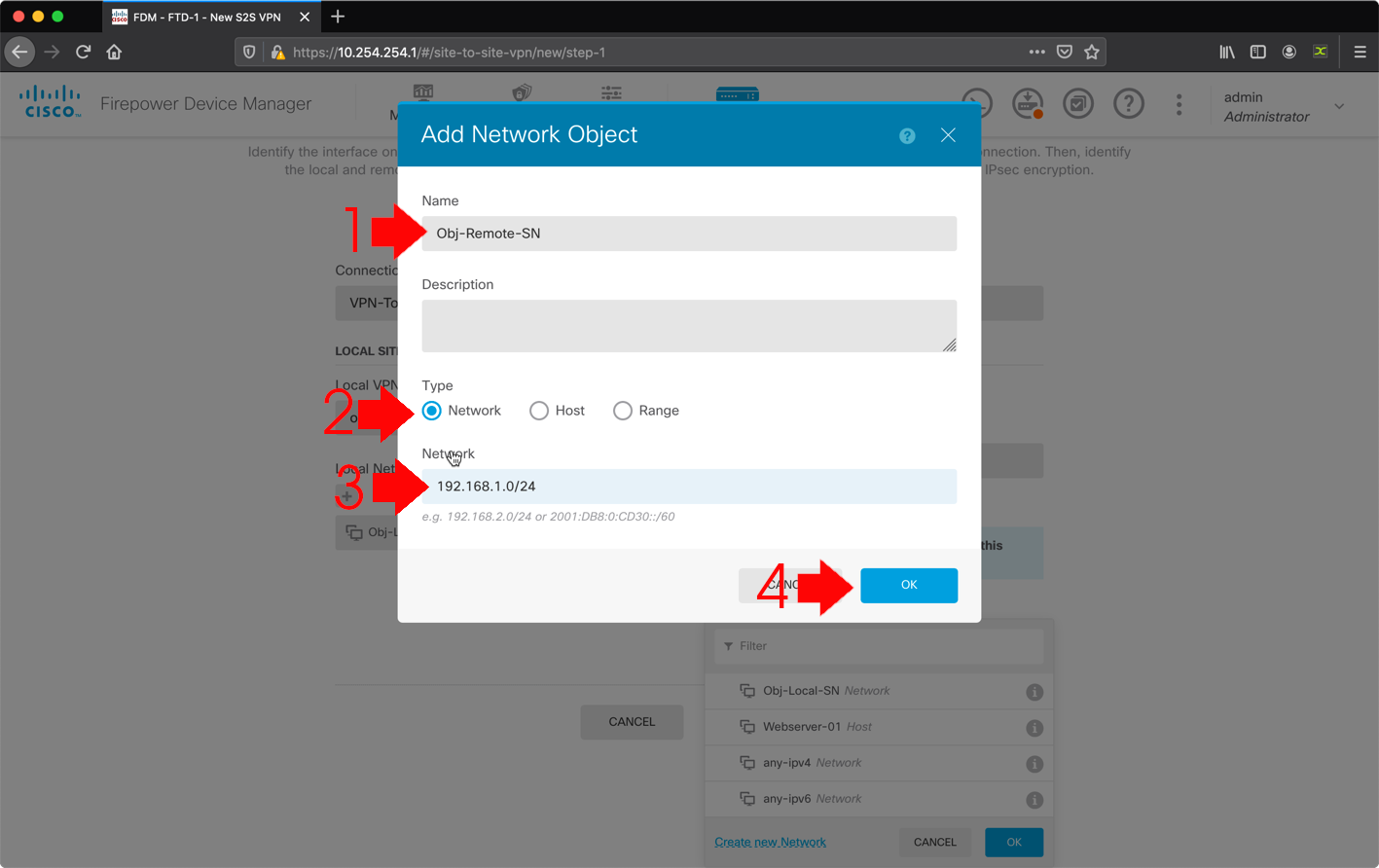
Navigate to Objects > Users > Add User. Add VPN Local users that will connect to FTD via Anyconnect. Create local Users as shown in the image. Navigate to Objects > Certificates > Add Internal Certificate . Configure a certificate as shown in the image.
Does firepower Threat Defense Support remote access VPN?
Remote access wizard This document provides a configuration example for Firepower Threat Defense (FTD) version 6.2.2 and later, that allows remote access VPN to use Transport Layer Security (TLS) and Internet Key Exchange version 2 (IKEv2). As a client, Cisco AnyConnect will be used, which is supported on multiple platforms.

Does Cisco FTD support VPN?
VPN Topology The Firepower Management Center configures site-to-site VPNs on FTD devices only. You can select from three types of topologies, containing one or more VPN tunnels: • Point-to-point (PTP) deployments establish a VPN tunnel between two endpoints.
How does Cisco remote access VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
How do I create a FTD site to VPN?
2:2112:24Configuring IPSec Site to Site VPN in FTD using FMC - YouTubeYouTubeStart of suggested clipEnd of suggested clipIn the stop VPN topology view let's click Add VPN. And you have two options fire power device andMoreIn the stop VPN topology view let's click Add VPN. And you have two options fire power device and fire threat defense click on fire power threat defense to configure site-to-site VPN foresight to FTD.
How do I access Cisco VPN?
ConnectOpen the Cisco AnyConnect app.Select the connection you added, then turn on or enable the VPN.Select a Group drop-down and choose the VPN option that best suits your needs.Enter your Andrew userID and password.Tap Connect.
What type of VPN is AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
Is Cisco VPN client free?
AnyConnect is "free" and it should have come on a CD with your hardware. SmartNet on your hardware will entitle you to download the client as well as any updates via the Cisco website.
How do I check my Cisco FTD VPN status?
Verification and Monitoring Browse to System -> Health -> Events. Then click on VPN Status. The remaining verification takes place on the FTD CLI.
What is IKEv2?
IKEv2 (Internet Key Exchange version 2) is a VPN encryption protocol responsible for request and response actions. It handles the SA (security association) attribute within an authentication suite called IPSec.
What is site to site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
How do I access VPN?
Open your phone's Settings app.Tap Network & internet. VPN. If you can't find it, search for "VPN." If you still can't find it, get help from your device manufacturer.Tap the VPN you want.Enter your username and password.Tap Connect. If you use a VPN app, the app opens.
How do I get Cisco AnyConnect VPN client?
Download the software.Locate and open the downloaded install package.Click Next on the “welcome” screen.Agree to the Software License Agreement and click Next.Click Install to begin installation.You must have elevated privileges to install Cisco AnyConnect Secure Mobility Client.More items...
How do I enable local LAN access on Cisco VPN?
Right click the Cisco AnyConnect client. Left click on Open AnyConnect. Select Advanced Windows. From the Preferences tab, ensure the Allow local (LAN) access when using VPN (if configured), is check.
How do I enable Cisco AnyConnect VPN through remote Desktop?
The steps would be:Log into the ASDM.Go to Configuration, Remote Access VPN, Anyconnect Client Profile.Click Add and create a new profile and choose the Group Policy it should apply to.Click OK, and then at the Profile screen click "Apply" at the bottom (important)More items...
How does VPN authentication work?
A virtual private network (VPN) gives you online privacy and anonymity to secure user authentication by creating a private network from a public internet connection. VPNs mask your IP (Internet Protocol) address and establish a secure and encrypted connection to provide greater privacy than even a secure Wi-Fi spot.
Does Cisco AnyConnect work anywhere?
Cisco AnyConnect Secure Mobility Client empowers employees to work from anywhere on company laptops or personal mobile devices. It also provides the visibility and control security teams need to identify who and which devices are accessing their infrastructure.
How does a VPN client work?
A VPN connection establishes a secure connection between you and the internet. Via the VPN, all your data traffic is routed through an encrypted virtual tunnel. This disguises your IP address when you use the internet, making its location invisible to everyone. A VPN connection is also secure against external attacks.
Introduction
This document describes how to configure the deploying of Remote Access Virtual Private Network (RA VPN) on Firepower Threat Defense (FTD) managed by the on-box manager Firepower Device Manager (FDM) running version 6.5.0 and above.
Background Information
Unable to configure FTD via FDM for Anyconnect clients to connect to the external interface while management is opened via the same interface. This is a known limitation of FDM. Enhancement request CSCvm76499 has been filed for this issue.
Prerequisites
Cisco recommends that you have knowledge of RA VPN configuration on FDM.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Where does remote access VPN problem originate?
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
How to complete a VPN connection?
To complete a VPN connection, your users must install the AnyConnect client software. You can use your existing software distribution methods to install the software directly. Or, you can have users install the AnyConnect client directly from the Firepower Threat Defense device.
How to use a VPN on a computer?
Step 1. Using a web browser, open https://ravpn-address , where ravpn-address is the IP address or hostname of the outside interface on which you are allowing VPN connections. You identify this interface when you configure the remote access VPN. The system prompts the user to log in. Step 2.
What is AnyConnect client profile?
AnyConnect client profiles are downloaded to clients along with the AnyConnect client software. These profiles define many client-related options, such as auto connect on startup and auto reconnect, and whether the end user is allowed to change the option from the AnyConnect client preferences and advanced settings.
How long is a VPN idle?
Idle Timeout —The length of time, in minutes, that the VPN connection can be idle before it is automatically closed, from 1-35791394. The default is 30 minutes. Browser Proxy During VPN Sessions —Whether proxies are used during a VPN session for Internet Explorer web browsers on Windows client devices.
What is a VPN?
Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a computer or other supported iOS or Android device connected to the Internet. This allows mobile workers to connect from their home networks or a public Wi-Fi network, for example.
Does an authentication server need to be available?
The authentication server must also be available through one of the data interfaces. Note. If the authentication server is on an external network, you need to configure a site-to-site VPN connection to the external network, and include the remote access VPN interface address within the VPN.
Where does remote access VPN problem originate?
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
Why create a VPN profile?
You can create a remote access VPN connection profile to allow your users to connect to your inside networks when they are on external networks, such as their home network . Create separate profiles to accommodate different authentication methods.
How to complete a VPN connection?
To complete a VPN connection, your users must install the AnyConnect client software. You can use your existing software distribution methods to install the software directly. Or, you can have users install the AnyConnect client directly from the Firepower Threat Defense device.
How to use a VPN on a computer?
Step 1. Using a web browser, open https://ravpn-address , where ravpn-address is the IP address or hostname of the outside interface on which you are allowing VPN connections. You identify this interface when you configure the remote access VPN. The system prompts the user to log in. Step 2.
What is AnyConnect client profile?
AnyConnect client profiles are downloaded to clients along with the AnyConnect client software. These profiles define many client-related options, such as auto connect on startup and auto reconnect, and whether the end user is allowed to change the option from the AnyConnect client preferences and advanced settings.
What is Cisco ISE?
Cisco ISE has a client posture agent that assesses an endpoint's compliance for criteria such as processes, files, registry entries, antivirus protection, antispyware protection, and firewall software installed on the host. Administrators can then restrict network access until the endpoint is in compliance or can elevate local user privileges so they can establish remediation practices. ISE Posture performs a client-side evaluation. The client receives the posture requirement policy from ISE, performs the posture data collection, compares the results against the policy, and sends the assessment results back to ISE.
Can Firepower Device Manager use SSL?
You can use Firepower Device Manager to configure remote access VPN over SSL using the AnyConnect client sofware. When the AnyConnect client negotiates an SSL VPN connection with the Firepower Threat Defense device, it connects using Transport Layer Security (TLS) or Datagram Transport Layer Security (DTLS).
What is Cisco AnyConnect Secure Mobility?
The Cisco AnyConnect Secure Mobility client provides secure SSL or IPsec (IKEv2) connections to the Firepower Threat Defense device for remote users with full VPN profiling to corporate resources. Without a previously-installed client, remote users can enter the IP address of an interface configured to accept clientless VPN connections in their browser to download and install the AnyConnect client. The Firepower Threat Defense device downloads the client that matches the operating system of the remote computer. After downloading, the client installs and establishes a secure connection. In case of a previously installed client, when the user authenticates, the Firepower Threat Defense device, examines the version of the client, and upgrades the client if necessary.
What is the only VPN client?
The only supported VPN client is the Cisco AnyConnect Secure Mobility Client. No other clients or native VPNs are supported. Clientless VPN is not supported for VPN connectivity; it is only used to deploy the AnyConnect client using a web browser.
What is AnyConnect profile?
An AnyConnect client profile is a group of configuration parameters stored in an XML file that the client uses to configure its operation and appearance. These parameters (XML tags) include the names and addresses of host computers and settings to enable more client features.
How to check VPN banner?
You can check the banner settings under Group Policy > General Settings> Banner. Edit the connect profile you have created for management VPN tunnel. Click Edit Group Policy> AnyConnect> Management Profile. Click the Management VPN Profiledrop-down and select the management profile file object you have created.
What is TLS in security?
When the client negotiates a connection with the security appliance, the client connects using Transport Layer Security (TLS), and optionally, Datagram Transport Layer Security (DTLS). DTLS avoids latency and bandwidth problems associated with some SSL connections and improves the performance of real-time applications that are sensitive to packet delays.
Can you disable VPN connection profile?
When you want to enforce a single connection profile on a user or user group, you can choose to disable the connection profile so that the group alias or URLs are not available for the users to select when they connect using the AnyConnect VPN client.
Is VPN load balancing disabled?
VPN load balancing is disabled by default. You must explicitly enable VPN load balancing. Only the FTD devices that are co-located can be added to a load-balancing group. A load-balancing group must have a minimum of two FTD devices.

Requirements
- Cisco recommends that you have knowledge of these topics: 1. Basic VPN, TLS and IKEv2 knowledge 2. Basic Authentication, Authorization, and Accounting (AAA) and RADIUS knowledge 3. Experience with Firepower Management Center
Components Used
- The information in this document is based on these software and hardware versions: 1. Cisco FTD 6.2.2 2. AnyConnect 4.5
Configuration
- 2. Remote access wizard
1. Go to Devices > VPN > Remote Access > Add a new configuration. 2. Name the profile according to your needs, select FTD device: 1. In step Connection Profile, type Connection Profile Name, select Authentication Server and Address Poolswhich you have created earlier: 1. Click o…
Connection
- To connect to FTD you need to open a browser, type DNS name or IP address pointing to the outside interface, in this example https://vpn.cisco.com. Youwill then have to login using credentials stored in RADIUS server and follow instructions on the screen. Once AnyConnect installs, you then need to put the same address in AnyConnect window and click Connect.
Limitations
- Currently unsupported on FTD, but available on ASA: 1. Double AAA Authentication 2. Dynamic Access Policy 3. Host Scan 4. ISE posture 5. RADIUS CoA 6. VPN load-balancer 7. Local authentication (Enhancement: CSCvf92680 ) 8. LDAP attribute map 9. AnyConnect customization 10. AnyConnect scripts 11. AnyConnect localization 12. Per-app VPN 13. SCEP proxy 14. WSA in…
Security Considerations
- You need to remember that by default, sysopt connection permit-vpn option is disabled. This means, that you need to allow traffic coming from pool of addresses on outside interface via Access Control Policy. Although the pre-filter or access-control rule is added intending to allow VPN traffic only, if clear-text traffic happens to match the rule criteria, it is erroneously permitted…