
What is the IKEv2 protocol in Cisco IOS software?
The following sections describe the constructs of the IKEv2 protocol in Cisco IOS software: An IKEv2 proposal is a collection of transforms used in the negotiation of IKE SAs as part of the IKE_SA_INIT exchange. The transform types used in the negotiation are as follows:
What is Internet Key Exchange version 2 (IKEv2)?
This module describes the Internet Key Exchange Version 2 (IKEv2) protocol. IKEv2 is the supporting protocol for IP Security Protocol (IPsec) and is used for performing mutual authentication and establishing and maintaining security associations (SAs). Your software release may not support all the features documented in this module.
How do I enable privileged exec mode in IKEv2?
Enables privileged EXEC mode. Enter your password if prompted. Enters global configuration mode. Specifies the IKEv2 authorization policy and enters IKEv2 authorization policy configuration mode. Specifies the Dynamic Host Configuration Protocol (DHCP) server to lease an IP address which is assigned to the remote access client.
How do I display the IKEv2 policy for a proposal?
(Optional) Displays the IKEv2 proposal. After you create the IKEv2 proposal, the proposal must be attached to a policy to pick the proposal for negotiation. For information on completing this task, see the Configuring the IKEv2 Policy section. Use the show crypto ikev2 policy command to display the IKEv2 default policy.
Does Cisco AnyConnect use IKEv2?
Each of those products only supported their own protocol however with the introduction of Anyconnect Secure Mobility Client 3.0, the client can now use IPsec (IKEv2) or SSL for the transport of the VPN connection.
How do I use Cisco AnyConnect on my Iphone?
VPN - Setup and Connect using the AnyConnect App for iOSInstall AnyConnect from the App Store . ... Open the AnyConnect app.Tap Add New VPN Connection.Tap Description.Enter in a name for your connection.Tap Server Address.Enter vpn.colorado.edu then tap Save. ... With the connection selected, tap the ON/OFF button.More items...
What is FlexVPN?
FlexVPN is Cisco's implementation of the IKEv2 standard featuring a unified paradigm and CLI that combines site to site, remote access, hub and spoke topologies and partial meshes (spoke to spoke direct).
How do I enable IKEv2 on my Cisco router?
To enable IKEv2 on a crypto interface, attach an IKEv2 profile to the crypto map or IPsec profile applied to the interface. You need not enable IKEv1 on individual interfaces because IKEv1 is enabled globally on all interfaces in the router.
Can I use Cisco VPN on iPad?
1:442:52Cisco Tech Talk: How to Access VPN on an iPhone and iPad - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd we'll navigate to our end client in order to access your personal VPN from your iPhone or iPadMoreAnd we'll navigate to our end client in order to access your personal VPN from your iPhone or iPad you'll first need to download the Cisco anyconnect. Application from the App Store.
Can you install Cisco AnyConnect on an iPad?
Go to the iTunes App Store. Download and install: AnyConnect Security Mobility Client. Find the newly installed AnyConnect application.
What is difference between Getvpn and FlexVPN?
GET VPN is used for site-to-site only, whereas FLEX VPN is able to work with site-to-site and Remote Access (RA VPN) deployments at once. GET VPN was designed to take advantage of the inherent full-mesh capabilities of MPLS networks.
What is the difference between DMVPN and FlexVPN?
In its essence, FlexVPN is the same as DMVPN. Connections between devices are still point-to-point GRE tunnels, spoke-to-spoke connectivity is still achieved with NHRP redirect message, IOS routers even run the same NHRP code for both DMVPN and FlexVPN, which also means that both are Cisco's proprietary technologies.
Is DMVPN Cisco proprietary?
This is a Cisco proprietary protocol. The Dynamic Multipoint Virtual Point Network feature allows you to easily scale your enterprise network. Even small companies use DMVPN with IPSec.
What is IKEv2 on Iphone?
Internet Key Exchange version 2 (IKEv2) is the default VPN setting for iOS. The IKEv2 is used to create a security association in the IPSec (Internet Protocol Security) suite. A security association (SA) establishes shared security attributes between two network entities to support secure communication.
How do I implement IKEv2?
Introduction.Prerequisites.Step 1 — Installing StrongSwan.Step 2 — Creating a Certificate Authority.Step 3 — Generating a Certificate for the VPN Server.Step 4 — Configuring StrongSwan.Step 5 — Configuring VPN Authentication.Step 6 — Configuring the Firewall & Kernel IP Forwarding.More items...•
Which is better IKEv2 or IPSec?
IPSec is considered secure and reliable, while IKEv2 is extremely fast and stable – IKEV2 offers quick re-connections when switching networks or during sudden drops. Thus, a combination of IKEv2/IPsec forms one of the best VPN protocols that exhibits the advantages of the two.
How do I connect to Cisco AnyConnect?
ConnectOpen the Cisco AnyConnect app.Select the connection you added, then turn on or enable the VPN.Select a Group drop-down and choose the VPN option that best suits your needs.Enter your Andrew userID and password.Authenticate with 2fa (DUO).Tap Connect.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
What is Cisco on my Iphone?
Cisco Secure Client (including AnyConnect VPN) provides reliable and easy-to-deploy encrypted network connectivity from any Apple iOS by delivering persistent corporate access for users on the go.
What is Cisco AnyConnect app?
The Cisco AnyConnect Secure Mobility Client for Android provides seamless and secure remote access to enterprise networks. AnyConnect allows installed applications to communicate as though connected directly to the enterprise network.
How to enable IKEv2?
To enable IKEv2 on a crypto interface, attach an IKEv2 profile to the crypto map or IPsec profile applied to the interface.
What is IKEv2 client?
Microsoft Windows 7 IKEv2 client sends IP address as IKE identity that prevents Cisco IOS IKEv2 RA server from segregating remote users based on IKE identity. To allow the Windows 7 IKEv2 client to send email address (user@domain) as IKE identity, apply the hotfix documented in KB675488 http://support.microsoft.com/kb/975488 on Microsoft Windows 7 and specify the email address string in either the user name field when prompted or the CommonName field in the certificate depending on the authentication method.
What is the name mangler in IKEv2?
Perform this task to specify the IKEv2 name mangler, which is used to derive a name for the authorization requests. The name is derived from specified portions of different forms of remote IKE identities or the EAP identity. The name mangler specified here is referred to in the IKEv2 profile.
What is an IKEv2 keyring?
An IKEv2 keyring is a repository of symmetric and asymmetric preshared keys and is independent of the IKEv1 keyring. The IKEv2 keyring is associated with an IKEv2 profile and hence, caters to a set of peers that match the IKEv2 profile. The IKEv2 keyring gets its VRF context from the associated IKEv2 profile.
How to disable NAT-T encapsulation?
Similar, to IKEv1, NAT-T is auto detected. To disable NAT-T encapsulation, use the no crypto ipsec nat-transparency udp-encapsulation command.
What happens after you create an IKEv2 proposal?
After you create the IKEv2 proposal, the proposal must be attached to a policy to pick the proposal for negotiation. For information on completing this task, see the Configuring the IKEv2 Policy section.
What is IKEv2 RA?
The IKEv2 RA server supports user and group authorizations. You can configure user authorizations, group authorizations, both, or none. The username for the user and group authorizations can be directly specified or derived from the peer IKEv2 identity using a name mangler. Group authorization can be local and external-AAA based, while user authorization can only be external-AAA based. The IKEv2 authorization policy serves as a container of IKEv2 local AAA group authorization parameters.
What is remote access VPN?
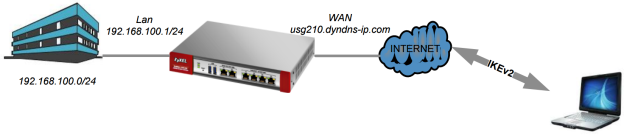
Remote Access VPN allows end-clients using various Operating Systems to securely connect to their Corporate or Home networks through non-secure medium such as the Internet. In the presented scenario, VPN tunnel is being terminated on a Cisco IOS Router using IKEv2 protocol.
When connecting in AnyConnect, should you be prompted for a password?
When connecting in AnyConnect, you should be prompted for a password. In this example, it is User3 that was created
What is the above configuration?
The above configuration is provided for reference to show a minimalistic working configuration.
Which algorythm is supported by AnyConnect?
On the AnyConnect side, as of the AnyConnect 3.1 version, NSA's Suite B algorythm suite is supported.
Which routers support NGC?
When choosing NGC configuration, make sure that both client software and headend hardware support it. ISR generation 2 and ASR 1000 routers are recommended as headends because of their hardware support for NGC.
Does CN have to be the same hostname?
CN in IOS identity certificate has to be equal hostname in the ACS XML profile.
Can AnyConnect see split tunneling?
In the Advanced options of AnyConnect in VPN you can check Route Details to see the Split Tunneling networks:
What is IKEv2?
Internet Key Exchange Version 2 (IKEv2), a next-generation key management protocol based on RFC 4306, is an enhancement of the IKE Protocol. IKEv2 is used for performing mutual authentication and establishing and maintaining security associations (SAs).
What is FlexVPN RA?
The FlexVPN RA - Aggregate Auth Support for AnyConnect feature implements aggregate authentication method by extending support for Cisco AnyConnect client that uses the proprietary AnyConnect EAP authentication method to establish a secure tunnel over the Internet between Cisco AnyConnect client and FlexVPN server.
Configuring Internet Key Exchange Version 2 (IKEv2) and FlexVPN Remote Access
This module describes IKEv2 CLI and is divided into basic and advanced sections.
Configuring FlexVPN Server
This module describes FlexVPN server features, IKEv2 commands required to configure FlexVPN server, remote access clients and the supported RADIUS attributes.
Configuring FlexVPN Client
This module describes FlexVPN client features and the IKEv2 commands required for FlexVPN client.
Configuring FlexVPN Spoke to Spoke
This module describes the FlexVPN Spoke to Spoke feature and the IKEv2 commands required for FlexVPN Spoke to Spoke.
Configuring IKEv2 Load Balancer
This module describes the IKEv2 Load Balancer Support feature and the IKEv2 commands required to configure the IKEv2 Load Balancer.
Configuring IKEv2 Reconnect
The IOS IKEv2 support for AutoReconnect feature of AnyConnect feature helps in reestablishing IKEv2 negotiation without user interaction with the Cisco AnyConnect client.
Configuring MPLS over FlexVPN
The MPLS over FlexVPN feature implements Multiprotocol Label Switching (MPLS) over a dynamically established IPsec tunnel thereby supporting duplicate address spaces.
Introduction
This document describes how to configure strongSwan as a remote access IPSec VPN client that connects to Cisco IOS ® software.
Configure
Notes: Use the Command Lookup Tool ( registered customers only) in order to obtain more information on the commands used in this section. The Output Interpreter Tool ( registered customers only) supports certain show commands.
Verify
Use this section in order to confirm that your configuration works properly.
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Summary
This document described the configuration of a strongSwan client that connects as an IPSec VPN client to Cisco IOS software.

Introduction
Prerequisites
Background
iOS Initial Configuration
ACS Initial Configuration
iOS FlexVPN Configuration
- You need to create IKEv2 proposal and policy (you might not have to, refer to CSCtn59317 ). Policy is created only for one of the IP addresses (10.1.1.2) in this example. Then, create an IKEV2 profile and IPsec profile that will bind to Virtual-Template. Make sure you are turning off http-url cert, as advised in the configuration guide. In this exa...
Windows Configuration
Tests
Verification
Known Caveats and Issues