How to configure VPN access on iOS?
Now that you have what you need, you are ready to set up the manual connection:
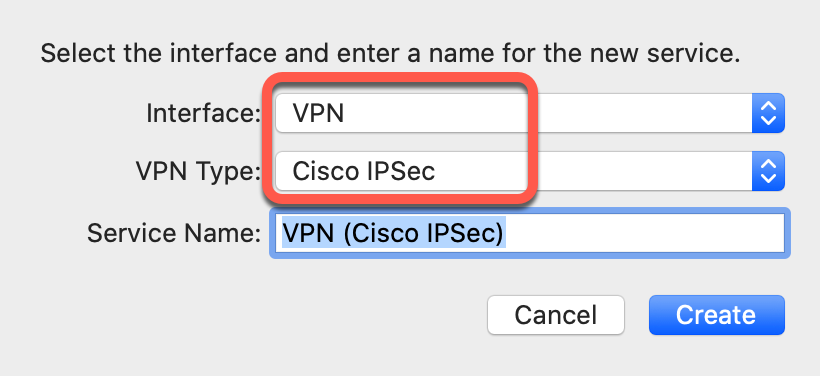
- Open your iOS device and navigate to: Settings > General > VPN > Add VPN configuration > Setup VPN configuration
- Select IKEv2 in the top of the menu and then enter the following settings: Description: Give your VPN connection a name Server: Enter the VPN server address provided to you ...
- Now, click Save to complete the manual setup.
How to install iOS in Cisco router?
Software Installation and Upgrade Procedures
- Select a Cisco IOS Software Image. Your first step in the upgrade procedure is to select the correct Cisco IOS software release and feature set.
- Download the Cisco IOS Software Image to the TFTP Server. ...
- Identify the File System to Copy the Image. ...
- Prepare for the Upgrade. ...
- Verify that the TFTP Server has IP Connectivity to the Router. ...
How to access remote computer via VPN?
Knowledge How do I remote into my computer at work from home using the VPN?
- Enable remote connection on your work computer. ...
- See How do I download and install the Cisco AnyConnect VPN client? ...
- Reboot your home computer
- After the reboot, go to your home computer's Windows Start Menu, search for Cisco AnyConnect VPN Client and open the program
- The AnyConnect window will come up and indicate that the VPN is "Ready to connect". ...
How to setup Cisco AnyConnect VPN Server?
Setup OpenConnect VPN Server for Cisco AnyConnect on Ubuntu 14.04 x64
- Installing ocserv. Since Ubuntu 14.04 does not ship with ocserv, we will have to download the source code and compile it.
- Configuring ocserv. A sample config file is placed under the directory ocser-0.9.2/doc. We will use this file as a template.
- Start ocserv and connect using Cisco AnyConnect. First, start ocserv. ...
See more
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
What is IPsec remote access VPN?
The IPsec Remote Access feature introduces server support for the Cisco VPN Client (Release 4. x and 5. x) software clients and the Cisco VPN hardware clients. This feature allows remote users to establish the VPN tunnels to securely access the corporate network resources.
Is Cisco VPN IPsec?
Cisco IPsec Technologies IPsec uses encryption technology to provide data confidentiality, integrity, and authenticity between participating peers in a private network. Cisco provides full Encapsulating Security Payload (ESP) and Authentication Header (AH) support.
What is Cisco remote access VPN?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
What is difference between IPsec and VPN?
The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
Is Cisco Anyconnect IPsec or SSL?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
How does Cisco IPSec work?
With the Cisco Secure VPN Client, you use menu windows to select connections to be secured by IPSec. When interesting traffic is generated or transits the IPSec client, the client initiates the next step in the process, negotiating an IKE phase one exchange.
How do I enable IPSec on a Cisco router?
To configure the IPSec VPN tunnel on Cisco 881 ISR:Configure the ISAKMP Policy. ... Enable NAT Keepalive. ... Configure the IPSec Peer. ... Define the IPSec Transform Set. ... Enable IPSec Fragmentation. ... Configure the IPSec Profile. ... Create the Tunnel Interfaces. ... Create the Access Control List (ACL)More items...
How do I enable IPSec?
How do I enable IPSec on a machine?Right click on 'My Network Places' and select Properties.Right click on 'Local Area Connection' and select Properties.Select 'Internet Protocol (TCP/IP)' and click Properties.Click the Advanced button.Select the Options tab.Select 'IP security' and click Properties.More items...
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Is Cisco AnyConnect a VPN?
Cisco AnyConnect Client helps us to make secure , safe and reliable VPN connection to our organization's private network with multiple security services to safe and protect company's data. It gives freedom to employees to get connected from anywhere anytime, thus making life easier for remote workers.
What are the benefits of IPsec?
IPsec provides the following security services for traffic at the IP layer: Data origin authentication—identifying who sent the data. Confidentiality (encryption)—ensuring that the data has not been read en route. Connectionless integrity—ensuring the data has not been changed en route.
What are the 3 protocols used in IPsec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Which is better IPsec or OpenVPN?
In site-to-site connections, OpenVPN functions faster and provides more security than IPsec. IPsec encryption operates on a kernel level, whereas OpenVPN functions in user space. Therefore, in terms of endpoint performance, IPsec is more favorable. With OpenVPN, you're limited to the capacity of the software.
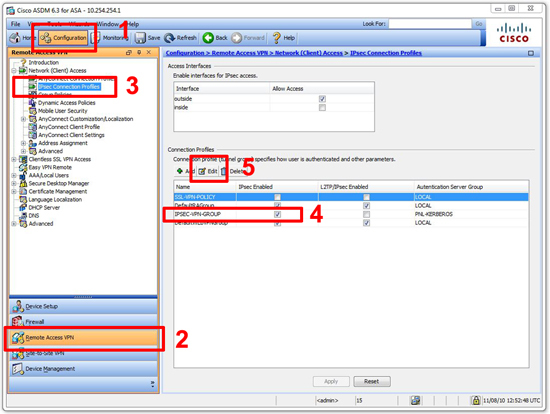
Step1. Define the authentication and authorization methods used
In this case, we’re defining a new group called VPN which will use the local database for authenticating and authorizing the user.
Step 3. Define the VPN client group profile
We are going to name the group VPNGROUP. This is the group name that will be entered in the VPN client. Enter the preshared secret here, and a POOL name, which defines what IPs that will be handed out to the VPN clients. Then assign the name of the ACL that will be used to define the encrypted traffic that will be allowed through the VPN.
Step 4. Create a the address Pool and the access-list used for traffic encryption
Setup the IP ranged to be assigned to the address pool. In this case the starting IP is 10.100.3.1 and the last IP that can be assigned is 10.100.3.254
Step 7. Lastly, assign the crypto map to the internet interface
We were unable to load Disqus Recommendations. If you are a moderator please see our troubleshooting guide.
How does IPSec work?
In IPSec tunnel mode, the entire original IP datagram is encrypted, and it becomes the payload in a new IP packet. This mode allows a network device, such as a router, to act as an IPSec proxy. That is, the router performs encryption on behalf of the hosts. The source router encrypts packets and forwards them along the IPSec tunnel. The destination router decrypts the original IP datagram and forwards it on to the destination system. Tunnel mode protects against traffic analysis; with tunnel mode, an attacker can only determine the tunnel endpoints and not the true source and destination of the packets passing through the tunnel, even if they are the same as the tunnel endpoints.
What is IPSEC security?
IPSec is a framework of open standards, developed by the Internet Engineering Task Force (IETF), that provides data confidentiality, data integrity, and data authentication between participating peers. IPSec provides these security services at the IP layer; it uses IKE to handle negotiation of protocols and algorithms based on local policy, and to generate the encryption and authentication keys to be used by IPSec. IPSec can be used to protect one or more data flows between a pair of hosts, between a pair of security Cisco 7200 series routers, or between a security Cisco 7200 series router and a host.
What is Cisco IOS firewall?
Cisco IOS software provides an extensive set of security features with which you can configure a simple or elaborate firewall, according to your particular requirements. When you configure Cisco IOS firewall features on your Cisco router, you turn your router into an effective, robust firewall.
What is the simplest way to connect to the Internet?
The simplest connectivity to the Internet is to use a single device to provide the connectivity and firewall function to the Internet. With everything being in a single device, it is easy to address translation and termination of the VPN tunnels. Complexity arises when you need to add extra Cisco 7200 series routers to the network. This normally leads people into building a network where the corporate network touches the Internet through a network called the DMZ, or demilitarized zone.
Where is NAT configured?
NAT is configured on the router at the border of a stub domain (referred to as the inside network) and a public network such as the Internet (referred to as the outside network ). NAT translates the internal local addresses to globally unique IP addresses before sending packets to the outside network.
Do IKE policies require companion configuration?
Depending on which authentication method you specify in your IKE policies, you need to complete an additional companion configuration before IKE and IPSec can successfully use the IKE policies.
Does Cisco 7200 support intrusion detection?
Note Although Cisco 7200 series routers support intrusion detection features, intrusion detection configuration procedures are not explained in this guide. For detailed information on intrusion detection, refer to the Intrusion Detection Planning Guide.
What is IPSEC VPN?
IPSec VPN is a security feature that allow you to create secure communication link (also called VPN Tunnel) between two different networks located at different sites. Cisco IOS routers can be used to setup VPN tunnel between two sites. Traffic like data, voice, video, etc. can be securely transmitted through the VPN tunnel.
How many phases are there in IPSEC?
There are two phases in IPSec configuration called Phase 1 and Phase 2. Let’s start the configuration with R1. Before you start configuring the IPSec VPN, make sure both routers can reach each other. I have already verified that both routers can ping each other so let’s start the VPN configuration. Step 1.
What is the IP address of R2?
The two sites have static public IP address as shown in the diagram. R1 is configured with 70.54.241.1/24 and R2 is configured with 199.88.212.2/24 IP address. As of now, both routers have very basic setup like, IP addresses, NAT Overload, default route, hostnames, SSH logins, etc.