See more
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
How do I configure IPsec VPN site to site?
To configure a route-based or policy-based IPsec VPN using autokey IKE:Configure interfaces, security zones, and address book information. ... Configure Phase 1 of the IPsec VPN tunnel. ... Configure Phase 2 of the IPsec VPN tunnel. ... Configure a security policy to permit traffic from the source zone to the destination zone.More items...
What is IPsec remote access VPN?
The IPsec Remote Access feature introduces server support for the Cisco VPN Client (Release 4. x and 5. x) software clients and the Cisco VPN hardware clients. This feature allows remote users to establish the VPN tunnels to securely access the corporate network resources.
How do I set up IPsec on my Iphone?
Configure the Apple iOS DeviceOn the Apple iOS device, tap Settings > General > VPN > Add VPN Configuration.On the Add VPN configuration screen, tap the IPSec tab.Configure the following settings: Server – The IP address or FQDN that the VPN service is listening on (e.g., 62.99. ... Tap Save in the top right corner.
What is the difference between VPN and IPSec?
SSL VPNs. The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
How IPSec VPN works step by step?
Authenticates and protects the identities of the IPSec peers. Negotiates a matching IKE SA policy between peers to protect the IKE exchange. Performs an authenticated Diffie-Hellman exchange with the end result of having matching shared secret keys. Sets up a secure tunnel to negotiate IKE phase two parameters.
Is Cisco AnyConnect IPSec or SSL?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
What is difference between SSL VPN and remote access VPN?
While an IPsec VPN allows users to connect remotely to an entire network and all its applications, SSL VPNs give users remote tunneling access to a specific system or application on the network. Choosing the right application comes down to a balance of convenience for the end-user and security for the organization.
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How do I setup a Cisco VPN on my iPhone?
1:442:52Cisco Tech Talk: How to Access VPN on an iPhone and iPad - YouTubeYouTubeStart of suggested clipEnd of suggested clipApplication from the App Store. We'll launch the app then tap connections. And add VPN connection inMoreApplication from the App Store. We'll launch the app then tap connections. And add VPN connection in the pop-up window we'll type in our server IP address which is the public IP of our r.v router.
What is IKEv2?
IKEv2 (Internet Key Exchange version 2) is a VPN encryption protocol responsible for request and response actions. It handles the SA (security association) attribute within an authentication suite called IPSec.
How do I set up FortiClient on my iPad?
FortiClient VPN - iPad, iPhone, iPod Touch SSL ConfigurationOpen the Apple store on your Apple Device.Search for FortiClient VPN.Tap Get.Once the installation is complete tap Open.On the Privacy Policy highlights screen tap 'I accept'On the support information screen tap 'I accept'More items...•
How do I connect my site-to-site VPN?
To set up a Site-to-Site VPN connection using a virtual private gateway, complete the following steps:Prerequisites.Step 1: Create a customer gateway.Step 2: Create a target gateway.Step 3: Configure routing.Step 4: Update your security group.Step 5: Create a Site-to-Site VPN connection.More items...
What is needed for a site-to-site VPN?
In order to set up an internet-based site-to-site VPN between two sites, a VPN gateway (router, firewall, VPN concentrator, or security appliance) such as the Cisco Adaptive Security Appliance (ASA) is required at both sites.
How do I enable IPSec?
How do I enable IPSec on a machine?Right click on 'My Network Places' and select Properties.Right click on 'Local Area Connection' and select Properties.Select 'Internet Protocol (TCP/IP)' and click Properties.Click the Advanced button.Select the Options tab.Select 'IP security' and click Properties.More items...
How do I enable IPSec on my router?
Choose the menu Status > System Status and Network > LAN. Check the VPN Router B. Choose the menu Status > System Status and Network > LAN. (1) Choose the menu VPN > IPSec > IPSec Policy and click Add to load the following page on the VPN router.
How does IPSec work?
In IPSec tunnel mode, the entire original IP datagram is encrypted, and it becomes the payload in a new IP packet. This mode allows a network device, such as a router, to act as an IPSec proxy. That is, the router performs encryption on behalf of the hosts. The source router encrypts packets and forwards them along the IPSec tunnel. The destination router decrypts the original IP datagram and forwards it on to the destination system. Tunnel mode protects against traffic analysis; with tunnel mode, an attacker can only determine the tunnel endpoints and not the true source and destination of the packets passing through the tunnel, even if they are the same as the tunnel endpoints.
What is IPSEC security?
IPSec is a framework of open standards, developed by the Internet Engineering Task Force (IETF), that provides data confidentiality, data integrity, and data authentication between participating peers. IPSec provides these security services at the IP layer; it uses IKE to handle negotiation of protocols and algorithms based on local policy, and to generate the encryption and authentication keys to be used by IPSec. IPSec can be used to protect one or more data flows between a pair of hosts, between a pair of security Cisco 7200 series routers, or between a security Cisco 7200 series router and a host.
What is Cisco IOS firewall?
Cisco IOS software provides an extensive set of security features with which you can configure a simple or elaborate firewall, according to your particular requirements. When you configure Cisco IOS firewall features on your Cisco router, you turn your router into an effective, robust firewall.
What is the simplest way to connect to the Internet?
The simplest connectivity to the Internet is to use a single device to provide the connectivity and firewall function to the Internet. With everything being in a single device, it is easy to address translation and termination of the VPN tunnels. Complexity arises when you need to add extra Cisco 7200 series routers to the network. This normally leads people into building a network where the corporate network touches the Internet through a network called the DMZ, or demilitarized zone.
Where is NAT configured?
NAT is configured on the router at the border of a stub domain (referred to as the inside network) and a public network such as the Internet (referred to as the outside network ). NAT translates the internal local addresses to globally unique IP addresses before sending packets to the outside network.
Do IKE policies require companion configuration?
Depending on which authentication method you specify in your IKE policies, you need to complete an additional companion configuration before IKE and IPSec can successfully use the IKE policies.
Does Cisco 7200 support intrusion detection?
Note Although Cisco 7200 series routers support intrusion detection features, intrusion detection configuration procedures are not explained in this guide. For detailed information on intrusion detection, refer to the Intrusion Detection Planning Guide.
Step1. Define the authentication and authorization methods used
In this case, we’re defining a new group called VPN which will use the local database for authenticating and authorizing the user.
Step 3. Define the VPN client group profile
We are going to name the group VPNGROUP. This is the group name that will be entered in the VPN client. Enter the preshared secret here, and a POOL name, which defines what IPs that will be handed out to the VPN clients. Then assign the name of the ACL that will be used to define the encrypted traffic that will be allowed through the VPN.
Step 4. Create a the address Pool and the access-list used for traffic encryption
Setup the IP ranged to be assigned to the address pool. In this case the starting IP is 10.100.3.1 and the last IP that can be assigned is 10.100.3.254
Step 7. Lastly, assign the crypto map to the internet interface
We were unable to load Disqus Recommendations. If you are a moderator please see our troubleshooting guide.
What is IPSEC VPN?
IPSec VPN is a security feature that allow you to create secure communication link (also called VPN Tunnel) between two different networks located at different sites. Cisco IOS routers can be used to setup VPN tunnel between two sites. Traffic like data, voice, video, etc. can be securely transmitted through the VPN tunnel.
How many phases are there in IPSEC?
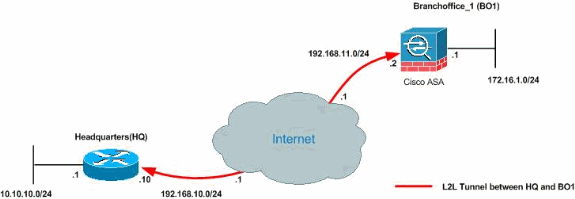
There are two phases in IPSec configuration called Phase 1 and Phase 2. Let’s start the configuration with R1. Before you start configuring the IPSec VPN, make sure both routers can reach each other. I have already verified that both routers can ping each other so let’s start the VPN configuration. Step 1.
What is the IP address of R2?
The two sites have static public IP address as shown in the diagram. R1 is configured with 70.54.241.1/24 and R2 is configured with 199.88.212.2/24 IP address. As of now, both routers have very basic setup like, IP addresses, NAT Overload, default route, hostnames, SSH logins, etc.
What is the IP address of a VPN pool?
Lastly, users authenticating to this group will obtain their IP address from the pool named ' VPN-Pool ' that provides the range of IP address: 192.168.0.20 up to 192.168.0.25.
What is VPN access?
Remote VPN access is an extremely popular service amongst Cisco routers and ASA Firewalls. The flexibility of having remote access to our corporate network and its resources literally from anywhere in the world, has proven extremely useful and in many cases irreplaceable. All that is required is fast Internet connection and your user credentials to log in – all the rest are taken care by your Cisco router or firewall appliance.
What is the second last step in ISAKMP?
Second-last step is to create one last ISAKMP profile to connect the VPN group with the virtual template:
What is the IP address of access list 120?
The access-list 120 tells the router to tunnel all traffic from the three networks to our VPN clients who's IP address will be in the 192.168.0.0/24 range!
What is the last step in VPN?
Last step is the creation of our access lists that will control the VPN traffic to be tunnelled, effectively controlling what our VPN users are able to access remotely.
What does IP unnumbered do?
Setting an interface as an ip unnumbered enables IP processing through it without assigning an explicit IP address, however you must bind it to a physical interface that does have an IP address configured, usually your LAN interface:
How many users can connect to CCLIENT VPN?
Users authenticating to this group will have their DNS set to 10.0.0.10. A maximum of 5 users are allowed to connect simultaneously to this group and will have access to the resources governed by access-list 120.