What does L2TP over IPsec stand for?
L2TP over IPSEC (Remote Access VPN) Hello Security Experts, My L2TP over IPSEC doesn't work, kindly help on my "phase2" of my L2TP over IPSEC...
What is an L2TP implementation?
L2TP implementation is a solution that provides a flexible, scalable remote network access environment without compromising corporate security or endangering mission-critical applications. Note L2TP is only supported in Microsoft Windows 2000.
How do I encrypt L2TP traffic?
Layer 2 tunneling protocols, such as L2TP, do not provide encryption mechanisms for the traffic it tunnels. Instead, they rely on other security protocols, such as IPSec, to encrypt their data. Use this sample configuration to encrypt L2TP traffic using IPSec for users who dial in.
What is the difference between L2TP tunnel and LNS?
L2TP tunnel is established between the L2TP Access Concentrator (LAC) and the L2TP Network Server (LNS). An IPSec tunnel is also established between these devices and all L2TP tunnel traffic is encrypted using IPSec.
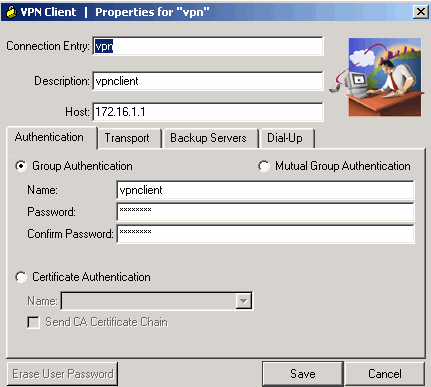
What is L2TP IPSec VPN?
About L2TP over IPsec/IKEv1 VPN Layer 2 Tunneling Protocol (L2TP) is a VPN tunneling protocol that allows remote clients to use the public IP network to securely communicate with private corporate network servers. L2TP uses PPP over UDP (port 1701) to tunnel the data. L2TP protocol is based on the client/server model.
Does Remote Access VPN use IPSec?
While Remote access VPN supports SSL and IPsec technology.
What is the difference between IPSec and L2TP?
L2TP. L2TP is a networking protocol used by the ISPs to enable VPN operations. /IPsec. IPsec is a protocol suite for secure IP communications that authenticates and encrypts each IP packet in a communication session.
What is Cisco Remote Access VPN?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
What is difference between SSL VPN and remote access VPN?
Whereas an IPsec VPN enables connections between an authorized remote host and any system inside the enterprise perimeter, an SSL VPN can be configured to enable connections only between authorized remote hosts and specific services offered inside the enterprise perimeter.
What is difference between site to site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
Which is better L2TP or IPSec?
Better Security Since L2TP doesn't have any encryption or authentication capabilities (both are key features of VPNs) on its own, IPSec VPN is often paired with it.
What are the three types of VPNs?
The Three Main Types of VPNs VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
How secure is L2TP IPSec VPN?
The L2TP protocol can be highly secure when used in conjunction with IPSec. It is highly compatible, working on operating systems like Windows and macOS by default. L2TP (and L2TP/IPSec) are relatively easy to set up due to their high compatibility. More firewall-friendly as it runs over UDP protocol.
How does a remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What type of VPN is Cisco AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
Is Cisco AnyConnect IPSec or SSL?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is the difference between IPsec and site to site VPN?
The main difference between IPsec and SSL VPNs is the endpoints for each protocol. While an IPsec VPN allows users to connect remotely to an entire network and all its applications, SSL VPNs give users remote tunneling access to a specific system or application on the network.
What type of protocols are used in VPNs?
6 common VPN protocolsOpenVPN. OpenVPN is a very popular and highly secure protocol used by many VPN providers. ... IPSec/IKEv2. IKEv2 sets the foundation for a secure VPN connection by establishing an authenticated and encrypted connection. ... WireGuard. ... SSTP. ... L2TP/IPSec. ... PPTP.
How do I configure IPsec remote access VPN in Sophos XG?
Configure IPsec remote access VPN with Sophos Connect clientSpecify the settings on the Sophos Connect client page.Send the configuration file to users.Add a firewall rule.Send the Sophos Connect client to users. ... Users install the client, import the configuration file into the client, and establish the connection.
What is L2TP VPN?
Layer 2 Tunneling Protocol (L2TP) is a VPN tunneling protocol that allows remote clients to use the public IP network to securely communicate with private corporate network servers. L2TP uses PPP over UDP (port 1701) to tunnel the data.
What is ASA tunnel mode?
By default, the ASA uses IPsec tunnel mode—the entire original IP datagram is encrypted, and it becomes the payload in a new IP packet. This mode allows a network device, such as a router, to act as an IPsec proxy. That is, the router performs encryption on behalf of the hosts. The source router encrypts packets and forwards them along the IPsec tunnel. The destination router decrypts the original IP datagram and forwards it on to the destination system. The major advantage of tunnel mode is that the end systems do not need to be modified to receive the benefits of IPsec. Tunnel mode also protects against traffic analysis; with tunnel mode, an attacker can only determine the tunnel endpoints and not the true source and destination of the tunneled packets, even if they are the same as the tunnel endpoints.
Introduction
Layer 2 tunneling protocols, such as L2TP, do not provide encryption mechanisms for the traffic it tunnels. Instead, they rely on other security protocols, such as IPSec, to encrypt their data. Use this sample configuration to encrypt L2TP traffic using IPSec for users who dial in.
Prerequisites
This document requires a basic understanding of IPSec protocol. To learn more about IPSec, please refer to An Introduction to IP Security (IPSec) Encryption.
Configure
In this section, you are presented with the information to configure the features described in this document.
Verify
This section provides information you can use to confirm your configuration is working properly.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
What is VPN on Cisco router?
This chapter explains the basic tasks for configuring an IP-based, remote access Virtual Private Network (VPN) on a Cisco 7200 series router. In the remote access VPN business scenario, a remote user running VPN client software on a PC establishes a connection to the headquarters Cisco 7200 series router.
What is Cisco IOS firewall proxy?
Using the Cisco IOS firewall authentication proxy feature , network administrators can apply specific security policies on a per-user basis. Users can be identified and authorized on the basis of their per-user policy, and access privileges tailored on an individual basis are possible, in contrast with general policy applied across multiple users.