Take the ethernet cable out of the WAN/Internet port on the FiOS router and put it into your PIX 501 outside interface. Configure the PIX 501's outside interface to accept a dynamically assigned IP...make sure you setup your NAT. Then take the FiOS router and connect it to your switch and/or another port on the PIX 501.
Full Answer
Does Cisco secure PIX firewall support Easy VPN?
This example uses Cisco Easy VPN to set up the secure channel and the PIX Firewall is configured as an Easy VPN server. In Cisco Secure PIX Firewall software release 6.3 and later, the new international encryption standard AES is supported for securing site-to-site and remote access VPN connections.
What encryption algorithms does the PIX firewall support?
The PIX Firewall supports AES key sizes of 128, 192, and 256 bits. The VPN Client supports AES as an encryption algorithm starting with Cisco VPN Client release 3.6.1. The VPN Client supports key sizes of 128 bits and 256 bits only.
How do I connect to a Pix using a group?
In the Connection Entry field, assign a name to the new entry that is created. In the Host field, type the IP address of the public interface of the PIX. Select the Authentication tab, and then type the group name and password (twice - for confirmation). This needs to match the information entered on the PIX using the vpngroup password command.

How do I setup a VPN on my Cisco router?
Steps for setting up a VPNStep 1: Line up key VPN components. ... Step 2: Prep devices. ... Step 3: Download and install VPN clients. ... Step 4: Find a setup tutorial. ... Step 5: Log in to the VPN. ... Step 6: Choose VPN protocols. ... Step 7: Troubleshoot. ... Step 8: Fine-tune the connection.
How do I setup a Cisco site to site VPN?
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel. ... Step 2: Create IPSec Transform (ISAKMP Phase 2 policy) ... Step 3: Create Crypto Map. ... Step 4: Apply Crypto Map to the Public Interface.
How do I connect to Cisco PIX?
ContinuingStep 1 - Get a Console Terminal.Step 5 - Identify Each Interface.Step 12 - Add Telnet Console Access.Step 2 - Get the Most Current.Software.Step 6 - Let Users Start Connections.Step 13 - Add Server Access.Step 3 - Configure Network Routing.More items...
How do I configure my PIX firewall?
Step 1 - Get the Most Current Software. ... Step 2 - Get a Console Terminal. ... Step 3 - Configure Network Routing. ... Step 4 - Start Configuring PIX Firewall. ... Step 5 - Identify Each Interface. ... Step 6 - Let Users Start Connections.
How do I setup a VPN tunnel?
Preshared key authenticationIn the administration interface, go to Interfaces.Click Add > VPN Tunnel.Type a name of the new tunnel.Set the tunnel as active and type the hostname of the remote endpoint. ... Select Type: IPsec.Select Preshared key and type the key.More items...
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is the function and role of Cisco Secure PIX Firewall?
The PIX Firewall allows secure access to the Internet from within existing private networks and the ability to expand and reconfigure TCP/IP networks without being concerned about a shortage of IP addresses.
How do I assign an IP address to a firewall in Asa?
Set a Static IP for your Cisco ASA5505 FirewallOpen the ASDM and log into your device.Under Configuration, Interfaces, select the Outside interface and hit Edit.In the 'IP Address' box, click the radio for 'Use Static IP'Select an IP address, and use '255.255. ... Hit ok, then apply.More items...•
How configure firewall Cisco Packet Tracer?
Step 3: Configuring the firewall in a server and blocking packets and allowing web browser.Click on server0 then go to the desktop.Then click on firewall IPv4.Turn on the services.First, Deny the ICMP protocol and set remote IP to 0.0. ... Then, allow the IP protocol and set remote IP to 0.0. ... And add them.
How configure firewall in ASA step by step?
Table of ContentsStep1: Configure the internal interface vlan.Step 2: Configure the external interface vlan (connected to Internet)Step 3: Assign Ethernet 0/0 to Vlan 2.Step 4: Enable the rest interfaces with no shut.Step 5: Configure PAT on the outside interface.Step 6: Configure default route.
How do I create a site-to-site VPN?
To set up a Site-to-Site VPN connection using a virtual private gateway, complete the following steps:Prerequisites.Step 1: Create a customer gateway.Step 2: Create a target gateway.Step 3: Configure routing.Step 4: Update your security group.Step 5: Create a Site-to-Site VPN connection.More items...
How do I create a tunnel between two Cisco routers?
0:449:43Create a Cisco IPsec protected tunnel interface! - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd if we want to build a tunnel let's go ahead and draw the tunnel. Visually. So we're working onMoreAnd if we want to build a tunnel let's go ahead and draw the tunnel. Visually. So we're working on building this logical tunnel that they can use to communicate with each other over the internet the
Which is a requirement of a site-to-site VPN?
It requires hosts to use VPN client software to encapsulate traffic. It requires the placement of a VPN server at the edge of the company network.
What is site-to-site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
Introduction
This document provides a sample configuration for the configuration of IPsec tunnels using ISAKMP profiles on a hub router with two PIX remote sites. One PIX remote site consists of LAN-to-LAN and the other consists of EzVPN Remote Access mode configuration.
Configure
In this section, you are presented with the information to configure the features described in this document.
Verify
This section provides information you can use to confirm your configuration is working properly. Refer to IP Security Troubleshooting - Understanding and Using debug Commands for additional verification/troubleshooting. If you should encounter any VPN Client issues or errors, refer to the VPN Client GUI Error Lookup Tool.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
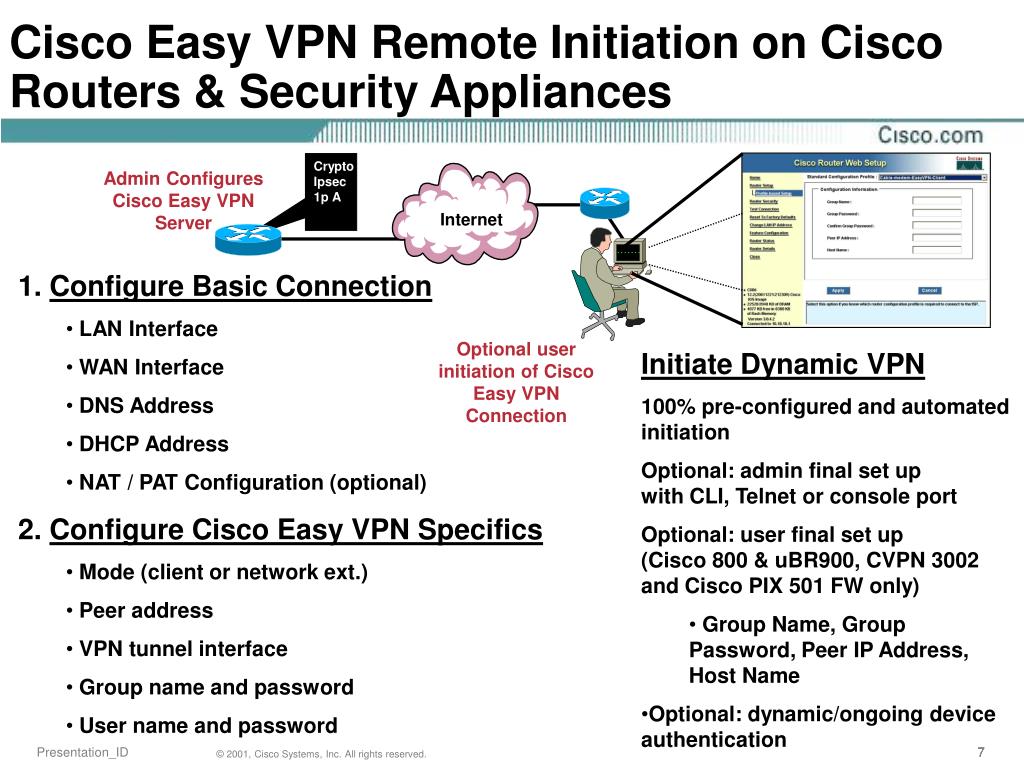
What is Cisco Easy VPN?
Cisco Easy VPN simplifies VPN deployment by making configuration and management of VPNs easy. It consists of the Cisco Easy VPN Server and the Cisco Easy VPN Remote. Minimal configuration is required on the Easy VPN Remote. The Easy VPN Remote initiates a connection. If authentication is successful, the Easy VPN Server pushes the VPN configuration down to it. More information on how to configure a PIX Firewall as an Easy VPN server is available at Managing VPN Remote Access.
How to create a new connection in VPN?
Launch the VPN Client application and click New to create a new connection entry.
What does show crypto ipsec SA mean?
In addition, the output shows the remote peer's actual IP address, the IP address assigned, the local IP address and interface, and the applied crypto map.
What is remote access VPN?
Remote Access VPNs address the requirement of the mobile workforce to securely connect to the organization's network. Mobile users are able to set up a secure connection using the VPN Client software installed on their PCs. The VPN Client initiates a connection to a central site device configured to accept these requests. In this example, the central site device is a PIX Firewall configured as an Easy VPN server which uses dynamic crypto maps.
What is the key size of Cisco VPN?
The VPN Client supports AES as an encryption algorithm starting with Cisco VPN Client release 3.6.1. The VPN Client supports key sizes of 128 bits and 256 bits only.
How to connect to gateway?
In order to connect to the gateway using the new connection entry, select the connection entry by clicking on it once and then click the Connect icon. A double-click on the connection entry has the same effect.
Can VPN tunnel be used to ping?
It is sometimes observed that although the VPN tunnel is established successfully, users are not able to perform common tasks such as ping network resources, log on to the domain, or browse network neighborhood. More information on troubleshooting such problems is available in Troubleshooting Microsoft Network Neighborhood After Establishing a VPN Tunnel With the Cisco VPN Client.
Question
I need to set-up a VPN to a remote user. I am using a PIX 501 and cisco vpn client software to accomplish this. I used the VPN wizard but do not know which IP address to enter . Can someone please help with step by step instructions for configuring the pix.
Pix 501 and vpn set up instructions
I need to set-up a VPN to a remote user. I am using a PIX 501 and cisco vpn client software to accomplish this. I used the VPN wizard but do not know which IP address to enter . Can someone please help with step by step instructions for configuring the pix.
What is remote access VPN?
When you select this option, the system displays a series of panels that let you enter the configuration required for this type of VPN. With a remote access VPN, your local PIX Firewall provides secure connectivity between individual remote users and the LAN resources protected by your local PIX Firewall.
What is a site to site VPN?
With a site-to-site VPN, your local PIX Firewall provides secure connectivity between your LAN and a LAN in a different geographic location.
What is the difference between the outside and inside VPN?
Use the selection list to select the interface on which the current VPN tunnel will be enabled. The outside interface is the lower security interface on your PIX Firewall, while the inside interface is the higher security interface.
How to access home page?
You can access the Home page any time by clicking Home on the main toolbar.
Should IP address be kept on individual lines?
entry should be kept on an individual line. The IP address should
How to keep RAS connections active after log off?
In order to remain connected after you log off, enable the KeepRasConnections key in the registry on the RAS client.
How does Pix 7.0 work?
Note: PIX 7.0 uses the inspect rpc command to handle RPC packets. The inspect sun rpc command enables or disables application inspection for the Sun RPC protocol. Sun RPC services can run on any port on the system. When a client attempts to access an RPC service on a server, it must find out which port that particular service runs on. It does this by querying the portmapper process on the well-known port number 111. The client sends the RPC program number of the service, and gets back the port number. From this point on, the client program sends its RPC queries to that new port.
What is debug PPP IO?
debug ppp io —Displays the packet information for the PPTP PPP virtual interface.
Can PPTP and IPsec be made separate?
In this example, a single pool for IPsec and PPTP is configured. However, the pools can also be made separate.
Does Pix work with Cisco VPN?
Note: This was tested on PIX Software Release 6.3.3 but should work on release 5.2.x and 5.3.1. PIX Software Release 6.x is required for the Cisco VPN Client 3.x and 4.x. (Support for the Cisco VPN 3000 Client 2.5 is added in PIX Software Release 5.2.x. The configuration also works for PIX Software Release 5.1.x, except for the Cisco VPN 3000 Client part.) IPsec and PPTP/Microsoft Point-to-Point Encryption (MPPE) should be made to work separately first. If they do not work separately, they do not work together.
Introduction
Prerequisites
- Requirements
There are no specific requirements for this document. - Components Used
The information in this document is based on these software and hardware versions: 1. Cisco Secure PIX Firewall Appliance 501 that runs 6.3(3) 2. Cisco Router 1750 that runs Cisco IOS® Software Release 12.3.9a 3. Cisco Secure PIX Firewall Appliance 506 that runs 6.3(3) 4. Cisco V…
Background Information
Configurations
Verify
Troubleshoot
Related Information