How can I control who can access the virtual terminal lines (vtys)?
You can control who can access the virtual terminal lines (vtys) to a router by applying an access list to inbound vtys. You can also control the destinations that the vtys from a router can reach by applying an access list to outbound vtys. Your software release may not support all the features documented in this module.
What is a VTY line on a router?
When a telnet or ssh connection is made to the router, the router associates this connection with a virtual terminal (VTY) line. Configuring access control to the VTY lines is important, because normally you require only the network administrators to make a telnet or ssh connection to the router.
How do I access VTY without authentication?
If you input the no login command on the VTY line, you can access to VTY by Telnet without authentication. However, it is not recommended for security reasons because if you know your router’s IP address, anyone can access to Telnet. Domain name and host name configuration.
Is it possible to use an extended access list with VTY?
I do not remember that specific post but will lay out the issues again. The optimum solution for access-class applied on vty is to use a standard access list. It is possible to use an extended access list in the access-class but when you do the "destination" address must be any (which sort of defeats the purpose of using extended access lists).

Which command Let us assign an ACL to a VTY line?
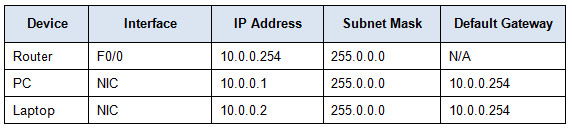
To configure standard or extended ACL on a vty line, we use the 'access-class {access-list-number|access-list-name} {in|out}' configuration commands. We enter the command under the vty line configuration mode. For our example, we have routers R1, R2, and R3 here. We want R1 to allow connections with R2 but not with R3.
Which can be performed on a Cisco router to control access to its Vty ports?
You can control who can access the virtual terminal lines (vtys) to a router by applying an access list to inbound vtys. You can also control the destinations that the vtys from a router can reach by applying an access list to outbound vtys.
What type of ACL is best for Vty access on a port and why standard or extended?
To secure virtual terminals, you can use both types of access lists, but it is recommended to use a standard access list. A standard access list provides the following advantages over an extended access list. You can apply a standard ACL directly on VTY lines. But you can't apply an extended ACL on VTY lines.
Which of the following commands will put an access list on a Vty line?
Controlling Outbound Access to a vtyenable.configure terminal.access-list access-list-number deny {destination [destination-wildcard] | any} [log]access-list access-list-number permit {source [source-wildcard] | any} [log]line vty line-number [ending-line-number]access-class access-list-number out.exit.More items...•
What is the difference in line vty 0 4 and 5 15?
VTY lines are usually used for creating out-of-band management sessions to devices. If a password is not supplied on a vty line, that line cannot be used for managing the device. In some cases administrators may decide to let junior staff to use lines 0 - 4 and senior staff to use lines 5 - 15.
What is the purpose of ACL 110?
ACL 110 permits traffic originating from any address on the 92.128. 2.0 network. The 'any' statement means that the traffic is allowed to have any destination address with the limitation of going to port 80.
What is the difference between a standard ACL and an extended ACL?
ACL Details and Examples Standard Access lists match only based on the source IP address of the packet. Extended Access lists can match on source and destination address, in addition to port, protocol, and many other fields.
How many ACL can be applied to an interface on a Cisco router?
Guidelines for ACL Creation For example, a dual-stacked (that is, IPv4 and IPv6) router interface can have up to four ACLs applied. Specifically, a router interface can have one outbound IPv4 ACL, one inbound IPv4 ACL, one inbound IPv6 ACL, and one outbound IPv6 ACL.
What is ACL in Cisco router?
An access control list (ACL) consists of one or more access control entries (ACEs) that collectively define the network traffic profile. This profile can then be referenced by Cisco IOS XR Software software features such as traffic filtering, priority or custom queueing, and dynamic access control.
What is Vty line access?
line vty 0 4. access-class in. this automatically allows telnet to all IP addresses of multilayer switch from source 10.1.1.11/32. usually we allow telnet connections from NOC IP subnets.
What are the requirements for using a Vty virtual terminal connection to a Cisco device?
What are the requirements for connecting a VTY (virtual terminal) to a Cisco device? A VTY connection connects through a LAN or WAN interface configured on the device. Use a program (such as PuTTY) to open the command line interface. This is an example of in-band management.
What is the use of line Vty 0 4?
VTY is a virtual port and used to get Telnet or SSH access to the device. VTY is solely used for inbound connections to the device. These connections are all virtual with no hardware associated with them. The abstract “0 – 4” means that the device can allow 5 simultaneous virtual connections which may be Telnet or SSH.
Which of the following interfaces can be used to manage the router choose three?
A router has many Ethernet ports to provide access to devices on the network. The console ports, management interface, and auxiliary port can all be used to manage the router.
Which type of access is secured on a Cisco router or switch with the enable secret command?
privileged EXEC modeWhich type of access is secured on a Cisco router or switch with the enable secret command? The enable secret command secures access to the privileged EXEC mode of a Cisco router or switch.
Which type of Cisco console cable is used to connect a laptop to the console port on a Cisco router?
RJ-45Connecting a Terminal or PC to the Console Port Connect the RJ-45 end of a DB-9-to-RJ-45 serial cable to the RJ-45 Console port on the router.
How many ways can you access a router?
You can connect to your router in two ways: wirelessly or using an Ethernet cable.
How to accept VTY access from remote user?
To accept VTY access from a remote user, you basically have to authenticate; in the case of Telnet access, you can authenticate with a password on the VTY line or with a username/password defined by the router.
What is VTY Access?
An efficient way to manage remote devices is to use VTY access, which is CLI-based remote access using Telnet or SSH.
When you remotely log in to a Cisco router or switch via Telnet/SSH, what is the output?
When you remotely log in to a Cisco router or Catalyst switch via Telnet/SSH, no logs are output by default. If you want to output the log of the remote login destination, enter the terminal monitor command in privileged EXEC mode.
Can Cisco routers use SSH?
Cisco routers and Catalyst switches can also provide VTY access to other devices as an SSH client. use the following commands in user EXEC or privileged EXEC mode to remotely log in to other devices as an SSH client.
Can you enable SSH on VTY?
You can enable SSH on VTY. SSH is enabled by default by transport input all, so you don’t need to configure it.SSH requires username and password authentication. login local command to enable username and password authentication.
What is restricted vty?
Restricts incoming connections between a particular vty (into a Cisco device) and the networking devices associated with addresses in the access list.
What is the benefit of controlling access to a virtual terminal line?
By applying an access list to an inbound vty, you can control who can access the lines to a router. By applying an access list to an outbound vty, you can control the destinations that the lines from a router can reach.
When a standard access list is applied to a line with the access class out command, what is the address?
When a standard access list is applied to a line with the access-class out command, the address specified in the access list is not a source address (as it is in an access list applied to an interface), but a destination address.
Is Cisco a trademark?
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Telnet and SSH
Telnet and SSH are two of the most popular protocols used for remote management. Both protocols come in two parts: server and client. The Server part is installed on the system that you want to access remotely. The client part is installed on the system that you want to use to access the server system remotely.
Using a standard ACL to secure VTY lines
To secure VTY lines, create a standard ACL that only permits the IP addresses you want to allow and apply this ACL to the VTY lines that you want to protect. Once the ACL is applied, the router will permit only the allowed IP addresses to access the VTY lines.
Enabling Telnet
By default, a router supports five telnet sessions. The following commands enable all telnet sessions and set the password 'telnet' for all sessions.
Telnet enabled Packet Tracer Lab
The following link provides the telnet enabled packet tracer lab of this example.
Requirements
Now suppose, we don't want to allow the Sales and Server sections to access the router's virtual terminals. We want to allow only the Manager section to access the router's virtual terminals. For this, we have to create and apply an access list on the router that allows only the Manager section to access virtual terminals.
Verifying the ACL implementation
To verify the ACL implementation, access the router's virtual terminal from PC2 again. This time the router will not let you access the virtual terminal.
Configured Packet Tracer Lab
The following link provides the configured packet tracer lab of the above example.
What is the IP address of the ACL?
To create a Standard Access Control List (ACL), to allow telnet or SSH connection only from Workstation06 (IP address - 172.18.0.12/16) (172.18.0.0/16 network) to Router03, we use the "access-list" IOS command from the global configuration mode of Router03, as shown below.
Why is it important to configure VTY?
Configuring access control to the VTY lines is important, because normally you require only the network administrators to make a telnet or ssh connection to the router. To configure Standrad Access Control Lists (ACL) to your VTY lines (telnet or ssh) follow these steps.
What is access list 55?
The IOS command "access-list 55 deny any" deny any other traffic.
What is the new management feature of Cisco 12.3T?
One of the biggest new management features of 12.3T and 12.4 mainline is the ability to use extended access-lists to permit particular traffic to establish an exec session to the vty lines of a Cisco device using a particular protocol; ie , telnet and/or ssh.
What is the IP address of R3?
Configure the IP address 10.1.1.3/24 on the FastEthernet0/0 interface of R3
What port is used for telnet?
Step 3. – Permit the network range 10.1.1.0/24 to use telnet or ssh. This objective will require two access list entries, one for telnet (tcp port 23) and one for ssh (tcp port 22) as shown below;
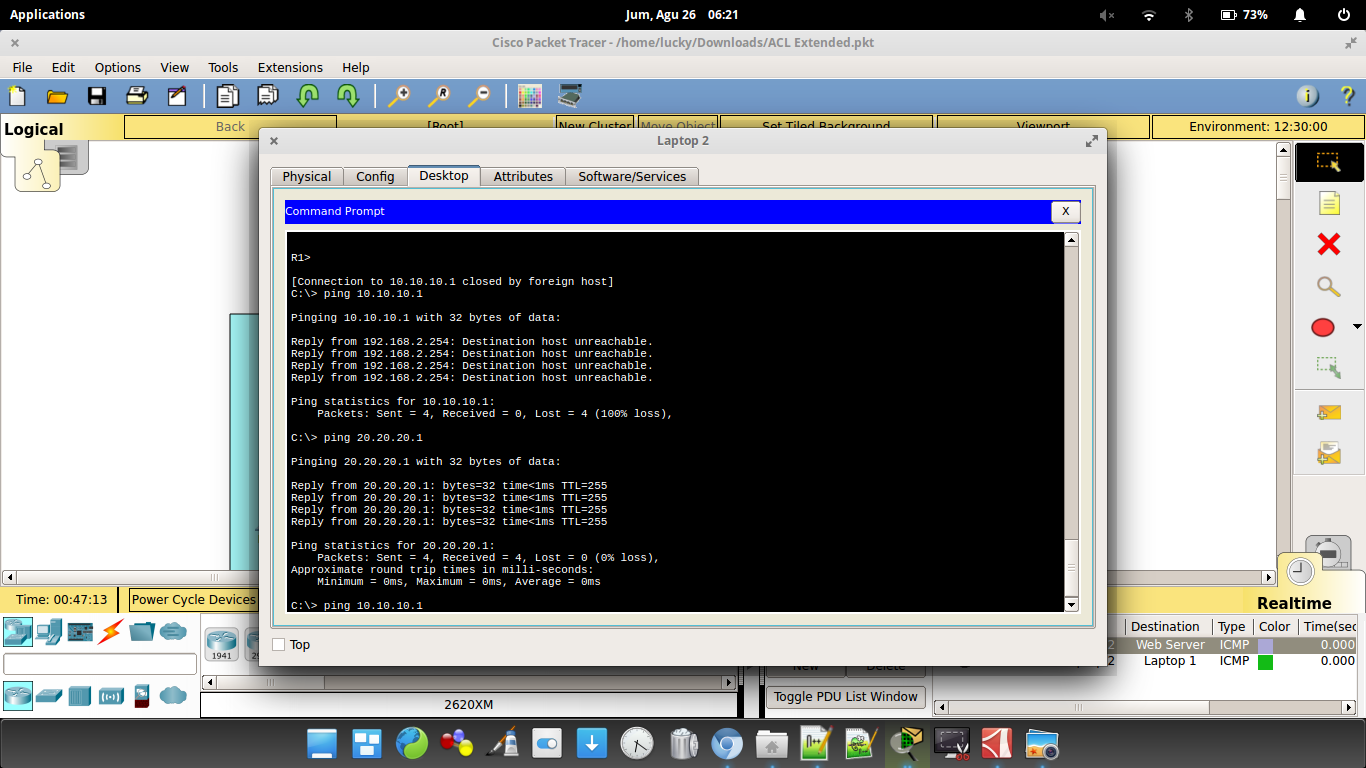
How to verify telnet was denied?
You can verify that telnet was indeed denied using the vty line ACL on R1 by executing the show access-list command in privileged mode . This will show you a hit count number beside each access control list entry;