Configure via ASDM 1) Start ASDM 2) Wizards -> VPN Wizards -> AnyConnect Wizard 3) Configure a name for the tunnel group - RemoteAccessIKEv2 4) Configure the connection protocols. It is possible to have both SSL
Transport Layer Security
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), both of which are frequently referred to as 'SSL', are cryptographic protocols designed to provide communications security over a computer network. Several versions of the protocols are in widespread use in applications such as web browsing, email, Internet faxing, instant messaging, and voice-over-IP (VoIP).
Full Answer
What is a remote access VPN?
Remote access VPNs are used by remote clients to log in to a corporate network. The example in this chapter illustrates the configuration of a remote access VPN that uses the Cisco Easy VPN and an IPSec tunnel to configure and secure the connection between the remote client and the corporate network.
How is a VPN connection created with an IPsec server?
After the IPSec server has been configured, a VPN connection can be created with minimal configuration on an IPSec client, such as a supported Cisco 870 series access router. When the IPSec client initiates the VPN tunnel connection, the IPSec server pushes the IPSec policies to the IPSec client and creates the corresponding VPN tunnel connection.
How to configure a VPN using Easy VPN and an IPSEC tunnel?
Configuring a VPN Using Easy VPN and an IPSec Tunnel 1 Remote, networked users 2 VPN client—Cisco 870 series access route ... 3 Router—Providing the corporate office ne ... 4 VPN server—Easy VPN server; for example, ... 5 Corporate office with a network address ... 1 more rows ...
How do I configure a remote-access VPN tunnel in Cisco ASA?
Select the type of remote-access VPN tunnel. The current version of Cisco ASA supports only Cisco IPSec remote-access VPNs, which is the default remote-access VPN tunnel type, as shown in Figure 21-23. Click Next to move to the VPN Client Tunnel Group Name and Authentication Method window.
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
How do I configure IPsec VPN site to site?
To configure a route-based or policy-based IPsec VPN using autokey IKE:Configure interfaces, security zones, and address book information. ... Configure Phase 1 of the IPsec VPN tunnel. ... Configure Phase 2 of the IPsec VPN tunnel. ... Configure a security policy to permit traffic from the source zone to the destination zone.More items...
What is IPsec remote access VPN?
The IPsec Remote Access feature introduces server support for the Cisco VPN Client (Release 4. x and 5. x) software clients and the Cisco VPN hardware clients. This feature allows remote users to establish the VPN tunnels to securely access the corporate network resources.
How do I setup a VPN tunnel on a Cisco router?
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel. ... Step 2: Create IPSec Transform (ISAKMP Phase 2 policy) ... Step 3: Create Crypto Map. ... Step 4: Apply Crypto Map to the Public Interface.
How IPSec VPN works step by step?
Authenticates and protects the identities of the IPSec peers. Negotiates a matching IKE SA policy between peers to protect the IKE exchange. Performs an authenticated Diffie-Hellman exchange with the end result of having matching shared secret keys. Sets up a secure tunnel to negotiate IKE phase two parameters.
What is the difference between VPN and IPSec?
SSL VPNs. The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
Is Cisco AnyConnect IPSec or SSL?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What ports do I forward for IPSec VPN?
A: To make IPSec work through your firewalls, you should open UDP port 500 and permit IP protocol numbers 50 and 51 on both inbound and outbound firewall filters. UDP Port 500 should be opened to allow Internet Security Association and Key Management Protocol (ISAKMP) traffic to be forwarded through your firewalls.
How do I enable IPSec on a Cisco router?
To configure the IPSec VPN tunnel on Cisco 881 ISR:Configure the ISAKMP Policy. ... Enable NAT Keepalive. ... Configure the IPSec Peer. ... Define the IPSec Transform Set. ... Enable IPSec Fragmentation. ... Configure the IPSec Profile. ... Create the Tunnel Interfaces. ... Create the Access Control List (ACL)More items...
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I know if my IPSec tunnel is up on a Cisco router?
You can do a "show crypto ipsec sa detail" and a "show crypto isakmp sa detail" both of them will give you the remaining time of the configured lifetime. By default the router has 3600 seconds as lifetime for ipsec and 86400 seconds for IKE.
How do I connect my site-to-site VPN?
To set up a Site-to-Site VPN connection using a virtual private gateway, complete the following steps:Prerequisites.Step 1: Create a customer gateway.Step 2: Create a target gateway.Step 3: Configure routing.Step 4: Update your security group.Step 5: Create a Site-to-Site VPN connection.More items...
What is needed for a site-to-site VPN?
In order to set up an internet-based site-to-site VPN between two sites, a VPN gateway (router, firewall, VPN concentrator, or security appliance) such as the Cisco Adaptive Security Appliance (ASA) is required at both sites.
How do I enable IPSec?
How do I enable IPSec on a machine?Right click on 'My Network Places' and select Properties.Right click on 'Local Area Connection' and select Properties.Select 'Internet Protocol (TCP/IP)' and click Properties.Click the Advanced button.Select the Options tab.Select 'IP security' and click Properties.More items...
How do I enable IPSec on my router?
Choose the menu Status > System Status and Network > LAN. Check the VPN Router B. Choose the menu Status > System Status and Network > LAN. (1) Choose the menu VPN > IPSec > IPSec Policy and click Add to load the following page on the VPN router.
What happens if a Cisco VPN client has a different preshared key size?
If a Cisco VPN Client with a different preshared key size tries to connect, the client logs an error message indicating it failed to authenticate the peer.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
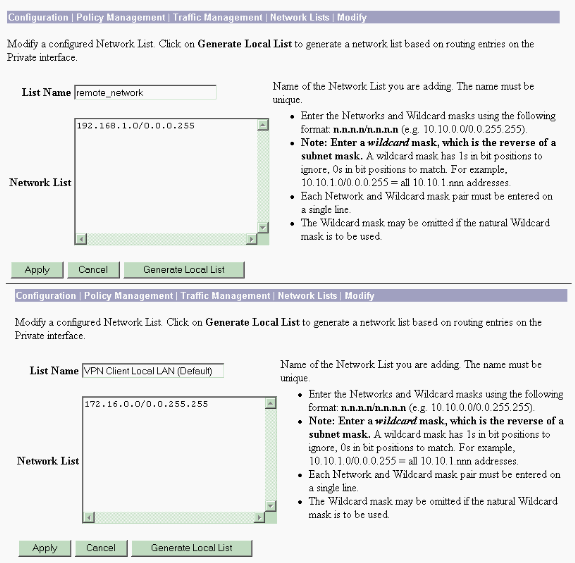
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
Which router is used for terminating IPSEC VPN?
In most real networks, the border router which connects the site to the Internet is used also for terminating the IPSEC VPN tunnel.
What is IPSEC protocol?
IPSEC is an IETF security standard. It is basically a suit of several protocols that offer secure communication over insecure paths.
What is phase 2 in a crypto map?
Phase 2: In this Phase we configure a crypto map and crypto transform sets. In general, Phase 2 deals with traffic management of the actual data communication between sites. The transform sets configured here, define what authentication and encryption protocols will be used on the data traffic.
How many phases are there in IPSEC?
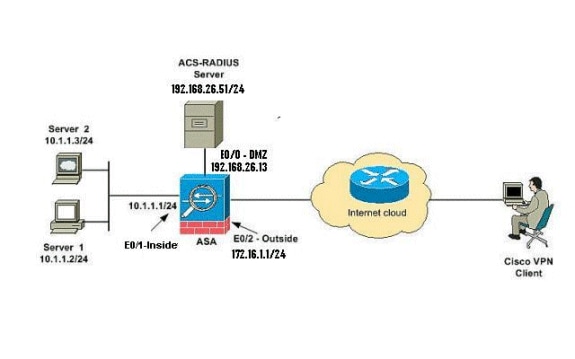
We will be using the example diagram above for the configuration scenario. Generally, there are two Phases for IPSEC VPN:
Why does a border router need NAT?
This border router must also perform NAT in order to provide access to the private LAN IP addresses to the Internet.
