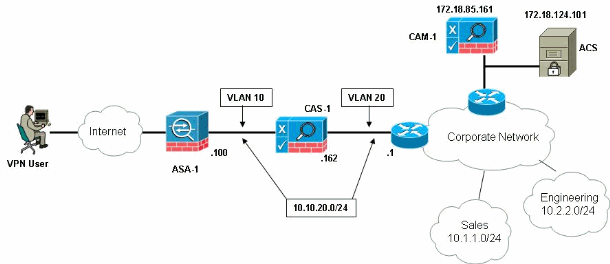
Cisco Remote Access VPN Setup
- Click Device, then click Setup Connection Profile in the Remote Access VPN group. (Click View Configuration if you...
- Configure the connection profile settings:Connection Profile Name —Enter a name, for example, Corporate-RAVPN.AD...
- Connection Profile Name —Enter a name, for example, Corporate-RAVPN.
- AD Realm/Directory Server for User Authentication —Select the identity realm used for authenticating remote users. If...
- AnyConnect Packages —Upload AnyConnect clients for each operating system you will support.
- Configure an Identity Certificate.
- Upload the SSL VPN Client Image to the ASA.
- Enable AnyConnect VPN Access.
- Create a Group Policy.
- Configure Access List Bypass.
- Create a Connection Profile and Tunnel Group.
- Configure NAT Exemption.
How do I set up a Cisco VPN?
- Download the VPN installer from MIT's download page, Cisco AnyConnect VPN Client for Windows. ...
- Find and double click the downloaded file named 'anyconnect-win-4.5.XXXXXX.exe', where XXXXXX is the sub-version number of the installer.
- On the following screen titled 'Welcome to the Cisco AnyConnect Secure Mobility Client Setup Wizard', click Next.
How to enable Cisco AnyConnect VPN through remote desktop?
To enable Cisco Anyconnect VPN through a remote desktop you must first create an Anyconnect Client Profile. The client profile is basically a XML file that gets pushed out to the client upon VPN establishment. This XML file can be created using a text editor or ASDM. I wouldn’t recommend using anything but the ASDM to create this file as you will see.
How to set up your Cisco VPN Server?
To set up a Windows 11 VPN connection, use these steps:
- Open Settings.
- Click on Network & internet.
- Click the VPN page from the right side. ...
- In the "VPN connections" setting, click the Add VPN button. ...
- Use the "VPN provider" drop-down menu and select the Windows (built-in) option.
How do I connect a Cisco router?
Router setup steps
- Decide where to place the router. The best place for a wireless business router is in an open area of the workplace, as you'll benefit from even coverage.
- Connect to the Internet. To solve the "long-distance" problem when connecting a router, you can use a CAT5e or CAT6 cable to connect the router to the ISP ...
- Configure the wireless router gateway. ...
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How does Cisco remote access VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
Can I use a VPN for remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How do I enable Cisco AnyConnect VPN through Remote Desktop?
The steps would be:Log into the ASDM.Go to Configuration, Remote Access VPN, Anyconnect Client Profile.Click Add and create a new profile and choose the Group Policy it should apply to.Click OK, and then at the Profile screen click "Apply" at the bottom (important)More items...
What VPN protocol does Cisco AnyConnect use?
TLSCisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
Is Cisco AnyConnect IPsec or SSL?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
What is the difference between remote access and VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What is the difference between RDS RDP and VPN?
Unlike VPN, RDP typically enables users to access applications and files on any device, at any time, over any type of connection. The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN.
Where is the Cisco AnyConnect Configuration file?
Resolution:Operating SystemLocationWindows 8%ProgramData%\Cisco\Cisco AnyConnect Secure Mobility Client\ProfileWindows 10%ProgramData%\Cisco\Cisco AnyConnect Secure Mobility Client\ProfileMac OS X/opt/cisco/anyconnect/profileLinux/opt/cisco/anyconnect/profile3 more rows•Apr 27, 2022
How do I create a Cisco AnyConnect profile?
I found the below for ASA/ASDM:Navigate to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile.Choose Add.Give the profile a name.Choose the Umbrella Security Roaming Client type from the Profile Usage drop-down list.More items...
What is the RDP port number?
Select TCP, enter “80,443,3389,20009” in the Specific local ports field and click Next.
How do I use Cisco VPN?
ConnectOpen the Cisco AnyConnect app.Select the connection you added, then turn on or enable the VPN.Select a Group drop-down and choose the VPN option that best suits your needs.Enter your Andrew userID and password.Tap Connect.
How does VPN authentication work?
A virtual private network (VPN) gives you online privacy and anonymity to secure user authentication by creating a private network from a public internet connection. VPNs mask your IP (Internet Protocol) address and establish a secure and encrypted connection to provide greater privacy than even a secure Wi-Fi spot.
Does Cisco AnyConnect work anywhere?
Cisco AnyConnect Secure Mobility Client empowers employees to work from anywhere on company laptops or personal mobile devices. It also provides the visibility and control security teams need to identify who and which devices are accessing their infrastructure.
How does a VPN client work?
A VPN connection establishes a secure connection between you and the internet. Via the VPN, all your data traffic is routed through an encrypted virtual tunnel. This disguises your IP address when you use the internet, making its location invisible to everyone. A VPN connection is also secure against external attacks.
Where does remote access VPN problem originate?
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
How to complete a VPN connection?
To complete a VPN connection, your users must install the AnyConnect client software. You can use your existing software distribution methods to install the software directly. Or, you can have users install the AnyConnect client directly from the Firepower Threat Defense device.
How to use a VPN on a computer?
Step 1. Using a web browser, open https://ravpn-address , where ravpn-address is the IP address or hostname of the outside interface on which you are allowing VPN connections. You identify this interface when you configure the remote access VPN. The system prompts the user to log in. Step 2.
What is AnyConnect client profile?
AnyConnect client profiles are downloaded to clients along with the AnyConnect client software. These profiles define many client-related options, such as auto connect on startup and auto reconnect, and whether the end user is allowed to change the option from the AnyConnect client preferences and advanced settings.
How long is a VPN idle?
Idle Timeout —The length of time, in minutes, that the VPN connection can be idle before it is automatically closed, from 1-35791394. The default is 30 minutes. Browser Proxy During VPN Sessions —Whether proxies are used during a VPN session for Internet Explorer web browsers on Windows client devices.
What is a VPN?
Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a computer or other supported iOS or Android device connected to the Internet. This allows mobile workers to connect from their home networks or a public Wi-Fi network, for example.
Does an authentication server need to be available?
The authentication server must also be available through one of the data interfaces. Note. If the authentication server is on an external network, you need to configure a site-to-site VPN connection to the external network, and include the remote access VPN interface address within the VPN.
How to configure a policy map?
To configure a policy map and create class policies (including a default class) comprising the service policy, use the first global configuration command to specify the policy-map name. Then use the following policy-map configuration commands to configure policy for a standard class and the default class. For each class that you define, you can use one or more of the following policy-map configuration commands to configure class policy. For example, you might specify bandwidth for one class and both bandwidth and queue limit for another class.
What is Cisco IOS firewall?
Cisco IOS software provides an extensive set of security features with which you can configure a simple or elaborate firewall, according to your particular requirements. When you configure Cisco IOS firewall features on your Cisco router, you turn your router into an effective, robust firewall.
How does IPSec work?
In IPSec tunnel mode, the entire original IP datagram is encrypted, and it becomes the payload in a new IP packet. This mode allows a network device, such as a router, to act as an IPSec proxy. That is, the router performs encryption on behalf of the hosts. The source router encrypts packets and forwards them along the IPSec tunnel. The destination router decrypts the original IP datagram and forwards it on to the destination system. Tunnel mode protects against traffic analysis; with tunnel mode, an attacker can only determine the tunnel endpoints and not the true source and destination of the packets passing through the tunnel, even if they are the same as the tunnel endpoints.
What is IPSEC used for?
IPSec can be used to protect one or more data flows between a pair of hosts, between a pair of security Cisco 7200 series routers, or between a security Cisco 7200 series router and a host.
Where is NAT configured?
NAT is configured on the router at the border of a stub domain (referred to as the inside network) and a public network such as the Internet (referred to as the outside network ). NAT translates the internal local addresses to globally unique IP addresses before sending packets to the outside network.
What is class map configuration?
Use the class-map configuration command to define a traffic class and the match criteria that will be used to identify traffic as belonging to that class. Match statements can include criteria such as protocol, ACL, IP precedence value, or interface identifier. The match criteria is defined with one or more of the match statements entered within the class-map configuration mode listed in the table below:
About Remote Access IPsec VPNs
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network. The Internet Security Association and Key Management Protocol, also called IKE, is the negotiation protocol that lets the IPsec client on the remote PC and the ASA agree on how to build an IPsec Security Association.
Configuration Examples for Remote Access IPsec VPNs
The following example shows how to configure a remote access IPsec/IKEv1 VPN:
Configuration Examples for Standards-Based IPSec IKEv2 Remote Access VPN in Multiple-Context Mode
The following examples show how to configure ASA for Standards-based remote access IPsec/IKEv2 VPN in multi-context mode. The examples provide information for the System Context and User Context configurations respectively.
Configuration Examples for AnyConnect IPSec IKEv2 Remote Access VPN in Multiple-Context Mode
The following examples show how to configure ASA for AnyConnect remote access IPsec/IKEv2 VPN in multi-context mode. The examples provide information for the System Context and User Context configurations respectively.
What is the advantage of Easy VPN?
The main advantage of Easy VPN is that IPSec policies are centrally managed on the server (Head end router providing IPSec feature) and are pushed to client devices. This policy push is known as Mode Configuration. This requires minimum configuration on the end-user side. The IPSec policies can be configured on a RADIUS server and then downloaded to an Easy VPN server, further reducing configuration required on the Easy VPN server.
What is a remote control policy?
Controlling policy for remote access through a RADIUS server is only a single example among multiple available. There is lot that can be achieved with a RADIUS server and AAA protocol. This not only helps in centralizing everything but helps you strengthen your security posture. If a policy needs to be updated, the time it takes to propagate the updated policies is greatly reduced. This could result in lowering operational costs in the long run.
