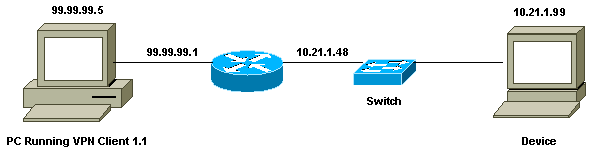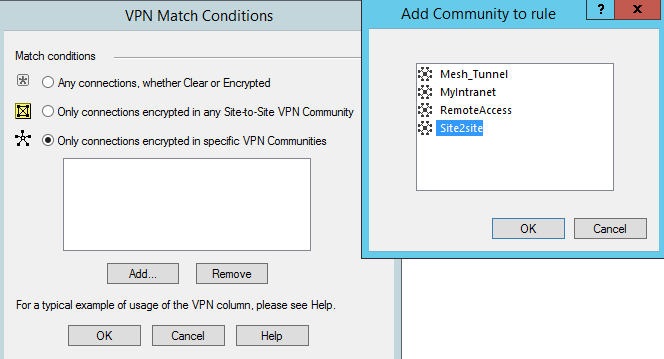
You could have a router like the Cisco RV220W that supports ten site-to-site VPN
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
Full Answer
How to enable Cisco AnyConnect VPN through remote desktop?
To enable Cisco Anyconnect VPN through a remote desktop you must first create an Anyconnect Client Profile. The client profile is basically a XML file that gets pushed out to the client upon VPN establishment. This XML file can be created using a text editor or ASDM. I wouldn’t recommend using anything but the ASDM to create this file as you will see.
How to connect to Cisco router using telnet?
- The “ line vty ” command enable the telnet and the “ 0″ is just let a single line or session to the router. ...
- The “ password ” command set the “ Pass123 ” as a password for telnet. ...
- The “ login ” command authenticate and ask you the password of telnet. ...
- The “ logging synchronous ” command stops any message output from splitting your typing.
What is Cisco Systems VPN client?
Cisco Systems VPN Client is a software application for connecting to virtual private networks based on Internet Key Exchange version 1.. On July 29, 2011, Cisco announced the end of life of the product. No further product updates were released after July 30, 2012, and support ceased on July 29, 2014. The Support page with documentation links was taken down on July 30, 2016, replaced with an ...
How to configure Cisco IP SLA?
These steps are:
- Creating IP SLA Operation
- Configure IP SLA Operation as ICMP Echo
- Set repeat frequency
- Configure Schedule
- Save The configuration
What is remote access VPN vs site to site?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How do I setup a Cisco VPN site to site?
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel. ... Step 2: Create IPSec Transform (ISAKMP Phase 2 policy) ... Step 3: Create Crypto Map. ... Step 4: Apply Crypto Map to the Public Interface.
What is the difference between site to site VPN and client to site VPN?
In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. In remote access VPN, Individual users are connected to the private network. 2. Site to site VPN does not need setup on each client.
Is Cisco AnyConnect a remote access VPN?
Anyconnect VPN offers full network access. The remote user will use the anyconnect client to connect to the ASA and will receive an IP address from a VPN pool, allowing full access to the network. Above we have the ASA firewall with two security zones: inside and outside.
What is site-to-site VPN?
A site-to-site virtual private network (VPN) refers to a connection set up between multiple networks. This could be a corporate network where multiple offices work in conjunction with each other or a branch office network with a central office and multiple branch locations.
Which is a requirement of a site-to-site VPN?
It requires hosts to use VPN client software to encapsulate traffic. It requires the placement of a VPN server at the edge of the company network.
Which ones are two main types of site to site VPN?
Virtual Private Network (VPN) is basically of 2 types:Remote Access VPN: Remote Access VPN permits a user to connect to a private network and access all its services and resources remotely. ... Site to Site VPN: A Site-to-Site VPN is also called as Router-to-Router VPN and is commonly used in the large companies.
What are the three types of VPNs?
The Three Main Types of VPNs VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
What is difference between SSL VPN and remote access VPN?
While an IPsec VPN allows users to connect remotely to an entire network and all its applications, SSL VPNs give users remote tunneling access to a specific system or application on the network. Choosing the right application comes down to a balance of convenience for the end-user and security for the organization.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
What type of VPN is Cisco AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
Does Cisco AnyConnect work anywhere?
Cisco AnyConnect Secure Mobility Client empowers employees to work from anywhere on company laptops or personal mobile devices. It also provides the visibility and control security teams need to identify who and which devices are accessing their infrastructure.
How do I setup a Cisco VPN on my router?
6:3815:11How to Setup a Cisco Router VPN (Site-to-Site) - YouTubeYouTubeStart of suggested clipEnd of suggested clipPre share and now we need to identify our. Key itself. So we'll type crypto AIESEC imp key is VPNMorePre share and now we need to identify our. Key itself. So we'll type crypto AIESEC imp key is VPN key and this is just a text string but it has to match on both ends of the connection.
How do I setup a VPN connection?
Open your phone's Settings app.Tap Network & internet. VPN. If you can't find it, search for "VPN." If you still can't find it, get help from your device manufacturer.Tap the VPN you want.Enter your username and password.Tap Connect. If you use a VPN app, the app opens.
How do I setup a VPN tunnel?
Both endpoints use the same password for authentication:In the administration interface, go to Interfaces.Click Add > VPN Tunnel.Type a name of the new tunnel.Set the tunnel as active and type the hostname of the remote endpoint. ... Select Type: IPsec.Select Preshared key and type the key.More items...
What are the two types of VPN connections choose two?
Virtual Private Network (VPN) is basically of 2 types:Remote Access VPN: Remote Access VPN permits a user to connect to a private network and access all its services and resources remotely. ... Site to Site VPN: A Site-to-Site VPN is also called as Router-to-Router VPN and is commonly used in the large companies.
What is VPN connection?
A VPN connection is commonly utilized in connecting a second office to the main office, or allowing a remote worker to connect to the computer network of the office, even if he is not physically connected to the network infrastructure.
What is a remote host?
The local and the remote hosts may be a computer, or another network whose settings have been synchronized to allow them to communicate. This is true on all types of VPN. It typically allows both networks to have access to the resources on both sides of the connection. A VPN connection is commonly utilized in connecting a second office to ...
What is WAN1 in VPN?
The options are: WAN1 — This option will use the IP address of the Wide Area Network 1 (WAN1) interface of the remote router for the VPN connection. WAN2 — This option will use the IP address of the WAN2 interface of the remote router for the VPN connection. WAN2 is not available in single-WAN routers.
What is WAN1 in router?
The options are: WAN1 — This option will use the IP address of the Wide Area Network 1 (WAN1) interface of the local router for the VPN connection. WAN2 — This option will use the IP address of the WAN2 interface of the local router for the VPN connection. WAN2 is not available in single-WAN routers.
What is subnet in VPN?
Subnet — This option allows the remote side of the VPN to access the local hosts in the specified subnet. IP Address — This option allows the remote side of the VPN to access the local host with the specified IP address. Any — This option allows the remote side of the VPN to access any of the local hosts.
What is static IP?
Static IP — This option will let the remote router use the static IP address of the local router when establishing a VPN connection. If this option is chosen on the local router, the remote router should also be configured with the same option.
What does FQDN mean in VPN?
FQDN — This option will use the Fully Qualified Domain Name (FQDN) of the local route when establishing the VPN connection.
How does IPSec work?
In IPSec tunnel mode, the entire original IP datagram is encrypted, and it becomes the payload in a new IP packet. This mode allows a network device, such as a router, to act as an IPSec proxy. That is, the router performs encryption on behalf of the hosts. The source router encrypts packets and forwards them along the IPSec tunnel. The destination router decrypts the original IP datagram and forwards it on to the destination system. Tunnel mode protects against traffic analysis; with tunnel mode, an attacker can only determine the tunnel endpoints and not the true source and destination of the packets passing through the tunnel, even if they are the same as the tunnel endpoints.
What is IPSEC security?
IPSec is a framework of open standards, developed by the Internet Engineering Task Force (IETF), that provides data confidentiality, data integrity, and data authentication between participating peers. IPSec provides these security services at the IP layer; it uses IKE to handle negotiation of protocols and algorithms based on local policy, and to generate the encryption and authentication keys to be used by IPSec. IPSec can be used to protect one or more data flows between a pair of hosts, between a pair of security Cisco 7200 series routers, or between a security Cisco 7200 series router and a host.
What is Cisco IOS firewall?
Cisco IOS software provides an extensive set of security features with which you can configure a simple or elaborate firewall, according to your particular requirements. When you configure Cisco IOS firewall features on your Cisco router, you turn your router into an effective, robust firewall.
How does extranet work?
In the extranet scenario, the headquarters and business partner are connected through a secure IPSec tunnel and the business partner is given access only to the headquarters public server to perform various IP-based network tasks, such as placing and managing product orders.
What is the simplest way to connect to the Internet?
The simplest connectivity to the Internet is to use a single device to provide the connectivity and firewall function to the Internet. With everything being in a single device, it is easy to address translation and termination of the VPN tunnels. Complexity arises when you need to add extra Cisco 7200 series routers to the network. This normally leads people into building a network where the corporate network touches the Internet through a network called the DMZ, or demilitarized zone.
Where is NAT configured?
NAT is configured on the router at the border of a stub domain (referred to as the inside network) and a public network such as the Internet (referred to as the outside network ). NAT translates the internal local addresses to globally unique IP addresses before sending packets to the outside network.
Does Cisco 7200 support intrusion detection?
Note Although Cisco 7200 series routers support intrusion detection features, intrusion detection configuration procedures are not explained in this guide. For detailed information on intrusion detection, refer to the Intrusion Detection Planning Guide.
What is site to site VPN?
Site-to-Site VPN is also known as Router-to-Router VPN. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. Multiple users are not allowed in Site-to-Site VPN.
What is remote access VPN?
Remote access VPN. 1. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. In remote access VPN, Individual users are connected to the private network. 2.
What is a Site-to-Site VPN?
Whereas remote-access VPNs securely connect individual devices to a remote LAN, site-to-site VPNs securely connect two or more LANs in different physical locations. Site-to-site VPNs use the public internet to extend your company’s network across multiple office locations.
What is a Remote-Access VPN?
Remote-access VPNs are more closely related to the consumer VPNs we use to protect our personal identities and data.
What is MPLS VPN?
Unlike internet-based site-to-site site VPNs in which a company uses its own infrastructure, MPLS VPN uses proprietary infrastructure owned by the VPN. This MPLS network, including its cloud, functions as the tunnel by which a company creates virtual connections between office sites.
What is a VPN gateway?
The VPN gateway encrypts the incoming traffic (to you) which is then received by your VPN client. Remote-access VPNs are not just a way for out-of-office employees to remotely access your company’s private network.
How does a VPN gateway work?
The VPN gateway then decrypts your traffic and relays the data to the LAN. Not only is all traffic sent through the virtual tunnel secured, but any traffic you receive from the local network (or its servers) also travels through this tunnel in reverse and is secured.
Why do businesses use VPNs?
VPNs were first used by businesses to extend private networks over the public internet, allowing remote workers to connect to a company’s LAN (local area network).
What is IPSec security?
IPSec secures IP packets one at a time, and in doing so, reliably provides WAN traffic with confidentiality (all bits are encrypted), integrity (no bits were tampered with during transmission), and authentication.