Procedure
- Choose Devices > VPN > Remote Access.
- Select a Remote Access policy and click Edit .
- Select a connection profile and click Edit .
- Click Add to add a group policy, or click Edit Group Policy > General > Split Tunneling .
Full Answer
How to configure split tunneling for remote access VPN?
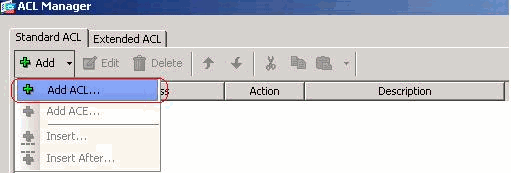
Complete these steps in order to configure your tunnel group to allow split tunneling for the users in the group. Choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies, and choose the Group Policy in which you want to enable local LAN access. Then click Edit.
How do I enable split tunneling in a tunnel group?
Complete these steps in order to configure your tunnel group to allow split tunneling for the users in the group. Choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies, and choose the Group Policy in which you want to enable local LAN access. Then click Edit. Click Split Tunneling.
How to configure the SSL VPN on ASA with Split tunneling?
Complete these steps in order to configure the SSL VPN on ASA with split tunneling: Choose Configuration > Remote Access VPN > Network (Client) Access > Address Management > Address Pools > Add in order to create an IP address pool vpnpool. Click Apply. Equivalent CLI Configuration:
How to allow DNS traffic through remote access VPN tunnel?
Configure split-tunnel in group policy to allow DNS traffic through remote access VPN tunnel if the DNS server is reachable through VNP network. For more information, see Configure Group Policy Objects.
Does Cisco AnyConnect allow split tunneling?
Dynamic Split Tunnel Include AnyConnect will send only the domains listed in the configuration over the secure vpn tunnel and all other traffic will be sent in the clear.
What is split tunneling in remote access VPN?
Split-tunneling is the process of allowing a remote VPN user to access a public network, such as the Internet, at the same time that the user is allowed to access resources on the VPN. This system of network access enables the user to access remote networks, at the same time as accessing the public network.
Where is split tunneling defined for remote access clients on an ASA?
1. Launch the ASDM > Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Select your policy. 2. Edit > Select Advanced > Split Tunneling. 3.
Does Open VPN have split tunneling?
In the Admin Web UI, you can start split tunneling with a simple click of a toggle button. Under Configuration > VPN Settings > Routing, switch “Should client Internet traffic be routed through the VPN?” to No. Once set to 'no', traffic destined to your private networks will traverse the VPN.
What is split tunneling Cisco VPN?
What is Split Tunneling? VPN split tunneling lets you send some of your application or device traffic through an encrypted VPN, while other applications or devices have direct access to the internet.
What is the advantage of split tunneling?
Advantages. One advantage of using split tunneling is that it alleviates bottlenecks and conserves bandwidth as Internet traffic does not have to pass through the VPN server. Another advantage is in the case where a user works at a supplier or partner site and needs access to network resources on both networks.
Does Cisco AnyConnect route all traffic?
With AnyConnect, the client passes traffic to all sites specified in the split tunneling policy you configured, and to all sites that fall within the same subnet as the IP address assigned by the ASA. For example, if the IP address assigned by the ASA is 10.1.
What VPN types are supported by ASA?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
How do I enable local LAN access on Cisco VPN?
Right click the Cisco AnyConnect client. Left click on Open AnyConnect. Select Advanced Windows. From the Preferences tab, ensure the Allow local (LAN) access when using VPN (if configured), is check.
What is the difference between a tunnel mode VPN and a split tunneling VPN?
VPN Connection Types Full tunnel is generally recommended because it is more secure. Split Tunnel - Routes and encrypts all OSU-bound requests over the VPN. Traffic destined to sites on the Internet (including Zoom, Canvas, Office 365, and Google) does not go through the VPN server in split tunnel mode.
How do I create a VPN tunnel between two sites?
0:525:14How To Create a Secure Tunnel Between Two RV130W RoutersYouTubeStart of suggested clipEnd of suggested clipIn the policy configuration window give the configuration a name then choose your exchange mode onceMoreIn the policy configuration window give the configuration a name then choose your exchange mode once we've done that we'll select our local identifier from the drop-down menu.
Should I enable split tunneling?
Split tunneling saves you plenty of VPN-related time and hassle, but it also reduces your security. Every time you look at an app or a website and decide its traffic doesn't need to pass through the tunnel, you're taking a risk (even if only small) with your online privacy.
What is the difference between a tunnel mode VPN and a split tunneling VPN?
VPN Connection Types Full tunnel is generally recommended because it is more secure. Split Tunnel - Routes and encrypts all OSU-bound requests over the VPN. Traffic destined to sites on the Internet (including Zoom, Canvas, Office 365, and Google) does not go through the VPN server in split tunnel mode.
Is split tunneling good?
The pros of split tunneling: speed and performance One of the major advantages to split tunneling is it represents the best of both worlds: the speed and performance of an unencrypted link, but the data security when and where you need it. Think of the alternative— if everything has to pass through the VPN tunnel.
When would you want to use a split tunnel for users?
Split tunneling allows you to connect to two networks simultaneously. In this way, you can be on your local corporate network as usual, while simultaneously accessing a foreign network. And you don't need to sacrifice either connection.
How do you implement split tunneling?
Configuring Split Tunnel for WindowsNavigate to Control Panel > Network and Sharing Center > Change Adapter Settings.Right click on the VPN connection, then choose Properties.Select the Networking tab.Select Internet Protocol Version 4 (TCP/IPv4) and click Properties.Click Advanced.More items...•
How to test if VPN is split tunneling?
An additional way to test that the VPN Client is configured for split tunneling while tunneled to the ASA is to use the ping command at the Windows command line. The local LAN of the VPN Client is 192.168.0.0/24 and another host is present on the network with an IP address of 192.168.0.3.
How does VPN work with ASA?
In a basic VPN Client to ASA scenario, all traffic from the VPN Client is encrypted and sent to the ASA no matter what its destination is. Based on your configuration and the number of users supported, such a set up can become bandwidth intensive. Split tunneling can work to alleviate this problem since it allows users to send only that traffic which is destined for the corporate network across the tunnel. All other traffic such as instant messaging, email, or casual browsing is sent out to the Internet via the local LAN of the VPN Client.
How to see VPN logs?
In order to view the log, go to the Log tab in the VPN Client. Then click on Log Settings in order to adjust what is logged. In this example, IKE is set to 3 - High while all other log elements are set to 1 - Low.
Why connect VPN client to VPN concentrator?
Connect your VPN Client to the VPN Concentrator in order to verify your configuration.
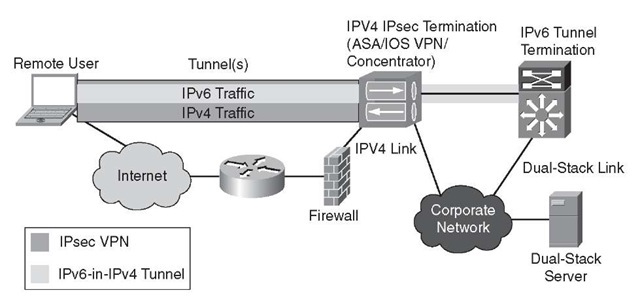
How many ACE entries are needed for split tunnel?
There is a restriction with the number of entries in an ACL used for split tunnel. It is recommended not to use more than 50-60 ACE entries for satisfactory functionality. You are advised to implement the subnetting feature to cover a range of IP addresses.
Which configuration is the most secure?
Note: Full tunneling is considered the most secure configuration because it does not enable simultaneous device access to both the Internet and the corporate LAN. A compromise between full tunneling and split tunneling allows VPN Clients local LAN access only.
Where is VPN located?
The VPN Client is located on a typical SOHO network and connects across the Internet to the main office.
How to enable SSL VPN on Cisco AnyConnect?
Choose Configuration > Remote Access VPN > Network (Client) Access > SSL VPN Connection Profiles and under Access Interfaces , click the check boxes Allow Access and Enable DTLS for the outside interface. Also, check the Enable Cisco AnyConnect VPN Client or legacy SSL VPN Client access on the interface selected in the table below check box in order to enable SSL VPN on the outside interface.
What is Cisco AnyConnect VPN?
This configuration allows the client secure access to corporate resources via SSL while giving unsecured access to the Internet using split tunneling.
How to check webvpn session in ASDM?
In ASDM, choose Monitoring > VPN > VPN Statistics > Sessions in order to know the current WebVPN sessions in the ASA.
How to enable SSL VPN?
Choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies in order to create an internal group policy clientgroup. Under the General tab, select the SSL VPN Client check box in order to enable the WebVPN as tunneling protocol.
What is debug webvpn?
debug webvpn svc <1-255> —Provi des the real time webvpn events in order to establish the session.
Where to download AnyConnect VPN client?
Note: Download the AnyConnect VPN Client package (anyconnect-win*.pkg) from the Cisco Software Download ( registered customers only) . Copy the AnyConnect VPN client to the ASA's flash memory, which is to be downloaded to the remote user computers in order to establish the SSL VPN connection with the ASA. Refer to the Installing the AnyConnect Client section of the ASA configuration guide for more information.
What command to use to terminate SVC sessions?
Similarly, you can use the vpn-sessiondb logoff svc command in order to terminate all the SVC sessions.
What is dynamic split exclude tunneling?
Using Dynamic Split Exclude tunneling, Anyconnect dynamically resolves the IPv4/IPv6 address of the hosted application and makes necessary changes in the routing table and filters to allow the connection to be made outside the tunnel.
What version of ASA is needed for dynamic split tunneling?
ASA version 9.0 or later is needed to use Dynamic Split Tunneling custom attributes.
How to verify AnyConnect group policy?
In order to verify that the AnyConnect users are assigned to the correct Anyconnect group-policy, you can run the command ' show vpn-sessiondb anyconnect filter name <username> '
How to add anyconnect to remote access?
Navigate to Configuration > Remote Access VPN > Network (Client) Access > Advanced > AnyConnect Custom Attribute Names. click Add button, and set the dynamic-split-exclude-domains attribute created earlier from Type, an arbitrary name and Values, as shown in the image:
Is Cisco.com encrypted?
In this example, you have configured www.cisco.com under Dynamic Tunnel Exclusion list and the Wireshark capture collected on the AnyConnect client's physical interface confirms that the traffic to www.cisco.com (173.37.145.84), is not encrypted by DTLS.
Can anyconnect be split tunneled?
With the advent of cloud-hosted computer resources, services may resolve to a different IP address based on the location of the user or based on the load of the cloud-hosted resources. Since Anyconnect Secure Mobility Client provides split-tunneling to static subnet range, host or pool of IPV4 or IPV6, it becomes difficult for Network Administrators to exclude domains/FQDNs while configuring AnyConnect. For example, a Network Administrator might want to exclude the Cisco.com domain from Split tunnel configuration but the DNS mapping for Cisco.com might change since it is cloud-hosted.
What is the rule for remote access VPN?
Before deploying the remote access VPN policy, you must update the access control policy on the targeted Firepower Threat Defense device with a rule that allows VPN traffic. The rule must allow all traffic coming in from the outside interface , with source as the defined VPN pool networks and destination as the corporate network.
What is the only VPN client?
The only supported VPN client is the Cisco AnyConnect Secure Mobility Client. No other clients or native VPNs are supported. Clientless VPN is not supported for VPN connectivity; it is only used to deploy the AnyConnect client using a web browser.
What is AnyConnect profile?
An AnyConnect client profile is a group of configuration parameters stored in an XML file that the client uses to configure its operation and appearance. These parameters (XML tags) include the names and addresses of host computers and settings to enable more client features.
How to change VPN settings on Firepower?
On the Firepower Management Center web interface, choose Devices > VPN > Remote Access, choose and edit a listed RA VPN policy, then choose the Advanced tab.
What is Cisco AnyConnect Secure Mobility?
The Cisco AnyConnect Secure Mobility client provides secure SSL or IPsec (IKEv2) connections to the Firepower Threat Defense device for remote users with full VPN profiling to corporate resources. Without a previously-installed client, remote users can enter the IP address of an interface configured to accept clientless VPN connections in their browser to download and install the AnyConnect client. The Firepower Threat Defense device downloads the client that matches the operating system of the remote computer. After downloading, the client installs and establishes a secure connection. In case of a previously installed client, when the user authenticates, the Firepower Threat Defense device, examines the version of the client, and upgrades the client if necessary.
How to upload Cisco AnyConnect client image?
You can upload the Cisco AnyConnect Mobility client image to the Firepower Management Center by using the AnyConnect File object. For more information, see FTD File Objects. For more information about the client image, see Cisco AnyConnect Secure Mobility Client Image .
How to add IPv4 to address pool?
Select the Add icon in the Address Pools window to add a new IPv4 or IPv6 address pool. When you choose the IPv4 pool, provide a starting and ending IP address. When you choose to include a new IPv6 address pool, enter Number of Addresses in the range 1-16384. Select the Allow Overrides option to avoid conflicts with IP address when objects are shared across many devices. For more information, see Address Pools .
Introduction
Prerequisites
- Requirements
This document assumes that a working remote access VPN configuration already exists on the ASA. Refer to PIX/ASA 7.x as a Remote VPN Server using ASDM Configuration Exampleif one is not already configured. - Components Used
The information in this document is based on these software and hardware versions: 1. Cisco ASA 5500 Series Security Appliance Software version 7.x and later 2. Cisco Systems VPN Client version 4.0.5 Note: This document also contains the PIX 6.x CLI configuration that is compatibl…
Background Information
- In a basic VPN Client to ASA scenario, all traffic from the VPN Client is encrypted and sent to the ASA no matter what its destination is. Based on your configuration and the number of users supported, such a set up can become bandwidth intensive. Split tunneling can work to alleviate this problem since it allows users to send only that traffic which is destined for the corporate ne…
Configure Split Tunneling on The Asa
- Configure the ASA 7.x with Adaptive Security Device Manager (ASDM) 5.x
Complete these steps in order to configure your tunnel group to allow split tunneling for the users in the group. 1. Choose Configuration > VPN > General > Group Policy and select the Group Policy that you wish to enable local LAN access in. Then click Edit. 2. Go to the Client Configuration tab… - Configure the ASA 8.x with Adaptive Security Device Manager (ASDM) 6.x
Complete these steps in order to configure your tunnel group to allow split tunneling for the users in the group. 1. Choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies, and choose the Group Policy in which you want to enable local LAN access. Then click …
Verify
- Follow the steps in these sections in order to verify your configuration. 1. Connect with the VPN Client 2. View the VPN Client Log 3. Test Local LAN Access with Ping
Troubleshoot
- Limitation with Number of Entries in a Split Tunnel ACL
There is a restriction with the number of entries in an ACL used for split tunnel. It is recommended not to use more than 50-60 ACE entries for satisfactory functionality. You are advised to implement the subnetting feature to cover a range of IP addresses.
Related Information
Introduction
Prerequisites
- Requirements
Ensure that you meet these requirements before you attempt this configuration: 1. ASA Security Appliance needs to run version 8.x 2. Cisco AnyConnect VPN Client 2.x Note: Download the AnyConnect VPN Client package (anyconnect-win*.pkg) from the Cisco Software Download (regi… - Components Used
The information in this document is based on these software and hardware versions: 1. Cisco 5500 Series ASA that runs software version 8.0(2) 2. Cisco AnyConnect SSL VPN Client version for Windows 2.0.0343 3. PC which runs Microsoft Visa, Windows XP SP2 or Windows 2000 Prof…
Background Information
- The Cisco AnyConnect VPN Client provides secure SSL connections to the security appliance for remote users. Without a previously installed client, remote users enter the IP address in their browser of an interface configured to accept SSL VPN connections. Unless the security appliance is configured to redirect http:// requests to https://, users must enter the URL in the form https://…
Configure
- In this section, you are presented with the information to configure the features described in this document. Note: Use the Command Lookup Tool (registeredcustomers only) to obtain more information on the commands used in this section.
Verify
- Use this section to confirm that your configuration works properly. The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of showcommand output. 1. show webvpn svc—Displays the SVC images stored in the ASA flash memory. ciscoasa#show webvpn svc1. disk0:/anyconnect-win-2.0.0343-k9.pkg 1 CIS…
Troubleshoot
- This section provides information you can use to troubleshoot your configuration. 1. vpn-sessiondb logoff name<username> —Command to logoff the SSL VPN session for the particular username. ciscoasa#vpn-sessiondb logoff name ssluser1Do you want to logoff the VPN session(s)? [confirm] YINFO: Number of sessions with name "ssluser1" logged off : 1ciscoasa#C…
Related Information