
Cisco supports several types of VPN implementations on the ASA but they are generally categorized as either “ IPSec
IPsec
Internet Protocol Security (IPsec) is a protocol suite for secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session. IPsec includes protocols for establishing mutual authentication between agents at the beginning …
- Internet Protocol Security (IPSec)
- Layer 2 Tunneling Protocol (L2TP)
- Point to Pint Tunneling Protocol (PPTP)
- SSTP (Secure Socket Tunneling Protocol)
- Internet Key Exchange version 2 (IKEv2)
- Secure Socces Layer (SSL) and Transport Layer Security (TLS)
- OpenVPN.
- Secure Shell (SSH)
What is remote access with IPsec VPN?
It runs between ASA-to-ASA or ASA-to-Cisco Router. Remote Access with IPSec VPN Client: A VPN client software is installed on user’s PC to provide remote access to the central network.
What are remote access VPN connection profiles?
Remote access VPN connection profiles define the characteristics that allow external users to make a VPN connection to the system using the AnyConnect Client.
Which interface should I choose for my remote access VPN connection?
Outside Interface —The interface to which users connect when making the remote access VPN connection. Although this is normally the outside (Internet-facing) interface, choose whichever interface is between the device and the end users you are supporting with this connection profile.
What types of VPNs are supported by Cisco ASA?
Cisco supports several types of VPN implementations on the ASA but they are generally categorized as either “ IPSec Based VPNs ” or “ SSL Based VPNs “. The first category uses the IPSec protocol for secure communications while the second category uses SSL.
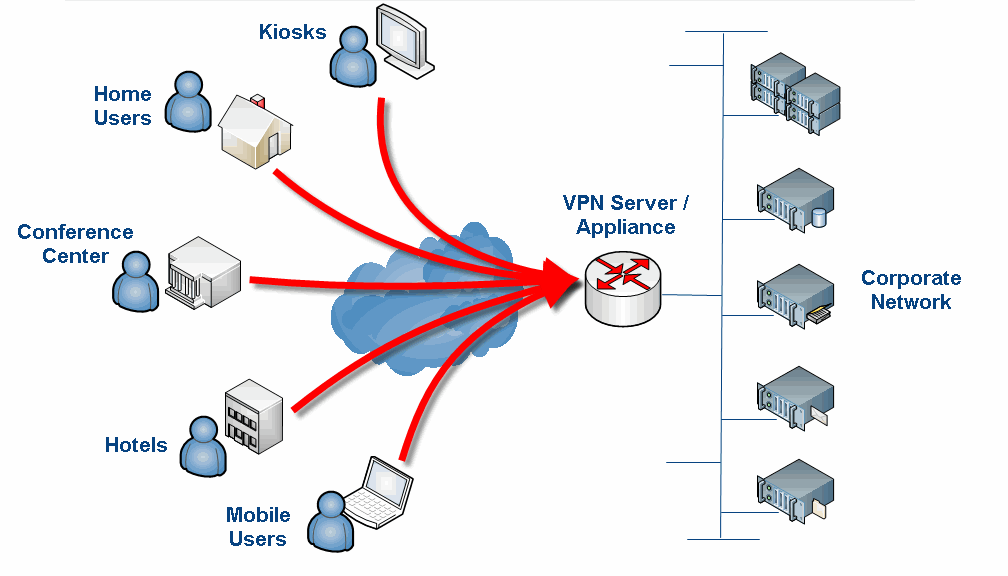
What type of VPN is Cisco VPN?
These solutions are built on five underlying VPN technologies: Dynamic Multipoint VPN (DMVPN), Easy VPN, GRE tunneling, standard IP Security (IPsec), and the new Group Encrypted Transport VPN (GET-VPN). Each technology has it benefits and is customized to meet specific deployment requirements.
What are different VPN types?
The four main types of VPN are:Remote access VPNs.Personal VPN services.Mobile VPNs.Site-to-site VPNs.
What is Cisco remote access VPN?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
What are the two types of VPN access?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
What are 3 types of VPN tunnels?
We'll look at three of the most common: IPsec tunnels, Dynamic multi point VPNs, and MPLS-based L3VPNs.IPsec Tunnels. In principle, a network-based VPN tunnel is no different from a client-based IPsec tunnel. ... Dynamic Multi point VPN (DMVPN) ... MPLS-based L3VPN.
How many types of VPN do we have?
The Three Main Types of VPNs VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site.
Is Cisco AnyConnect a VPN?
Cisco AnyConnect Client helps us to make secure , safe and reliable VPN connection to our organization's private network with multiple security services to safe and protect company's data. It gives freedom to employees to get connected from anywhere anytime, thus making life easier for remote workers.
What VPN types are supported by ASA?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I know my VPN type?
When you first set up a VPN connection by opening the Network preference, clicking the plus (+) button near the bottom-left corner of the window, choosing VPN from the Interface pop-up menu, and selecting the kind of protocol you'll use from the VPN Type menu, the Service Name field will display the protocol in ...
What is L2TP IPsec VPN?
About L2TP over IPsec/IKEv1 VPN Layer 2 Tunneling Protocol (L2TP) is a VPN tunneling protocol that allows remote clients to use the public IP network to securely communicate with private corporate network servers. L2TP uses PPP over UDP (port 1701) to tunnel the data. L2TP protocol is based on the client/server model.
Which type of VPN is best?
The Best VPN Service for 2022NordVPN - Best VPN for Privacy.Surfshark - Best VPN for Security.Private Internet Access VPN - Best VPN for Windows.IPVanish - Best VPN for Android.Ivacy - Most Affordable.Atlas VPN - Best Data Breach Monitoring.ExpressVPN - Best Encryption.PureVPN - Best Server Base.More items...
What VPN type should I use?
Many VPN experts recommend OpenVPN as the most secure protocol. It uses 256-bit encryption as a default but also offers other ciphers such as 3DES (triple data encryption standard), Blowfish, CAST-128, and AES (Advanced Encryption Standard).
How do I know my VPN type?
When you first set up a VPN connection by opening the Network preference, clicking the plus (+) button near the bottom-left corner of the window, choosing VPN from the Interface pop-up menu, and selecting the kind of protocol you'll use from the VPN Type menu, the Service Name field will display the protocol in ...
What is Phase 1 and Phase 2 in VPN?
VPN negotiations happen in two distinct phases: Phase 1 and Phase 2. The main purpose of Phase 1 is to set up a secure encrypted channel through which the two peers can negotiate Phase 2. When Phase 1 finishes successfully, the peers quickly move on to Phase 2 negotiations.
What is L2TP IPsec VPN?
About L2TP over IPsec/IKEv1 VPN Layer 2 Tunneling Protocol (L2TP) is a VPN tunneling protocol that allows remote clients to use the public IP network to securely communicate with private corporate network servers. L2TP uses PPP over UDP (port 1701) to tunnel the data. L2TP protocol is based on the client/server model.
Where does remote access VPN problem originate?
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
How to complete a VPN connection?
To complete a VPN connection, your users must install the AnyConnect client software. You can use your existing software distribution methods to install the software directly. Or, you can have users install the AnyConnect client directly from the Firepower Threat Defense device.
How to see what session a VPN is on?
Use the show vpn-sessiondb anyconnect command to view detailed information about current AnyConnect VPN sessions.
How to use a VPN on a computer?
Step 1. Using a web browser, open https://ravpn-address , where ravpn-address is the IP address or hostname of the outside interface on which you are allowing VPN connections. You identify this interface when you configure the remote access VPN. The system prompts the user to log in. Step 2.
Why create a VPN profile?
You can create a remote access VPN connection profile to allow your users to connect to your inside networks when they are on external networks, such as their home network . Create separate profiles to accommodate different authentication methods.
What is Cisco ISE?
Cisco ISE has a client posture agent that assesses an endpoint's compliance for criteria such as processes, files, registry entries, antivirus protection, antispyware protection, and firewall software installed on the host. Administrators can then restrict network access until the endpoint is in compliance or can elevate local user privileges so they can establish remediation practices. ISE Posture performs a client-side evaluation. The client receives the posture requirement policy from ISE, performs the posture data collection, compares the results against the policy, and sends the assessment results back to ISE.
Can Firepower Device Manager use SSL?
You can use Firepower Device Manager to configure remote access VPN over SSL using the AnyConnect client sofware. When the AnyConnect client negotiates an SSL VPN connection with the Firepower Threat Defense device, it connects using Transport Layer Security (TLS) or Datagram Transport Layer Security (DTLS).
What is remote access VPN?
Remote Access VPN is the first of the two VPN types. Remote Access VPN is the VPN type with which, users can access the private networks over internet remotely. This type of VPN, provides network access chance to remote users, travelling employees, any workers far away from its company. Remote Access VPN is usually used in ...
What is the most important protocol for VPN?
One of the most important Protocols of VPN is IPSec. IPSec is a VPN Protocol that provides secure connection over IP networks. With this VPN protocol authentication and encryption are used. There are different type of IPSec and with this type of IPSec, there are different encryption modes. These are Transport Mode and Tunneling Mode.
What is VPN security?
By encrypting the connections, VPN provides security in this type communication. Basically this security is provided over a VPN Tunnel and provide a trusted connection by avoiding any hacker attacks. Different VPN types and Protocols of VPN provide various secured connections. There are two main VPN Types.
What is site to site VPN?
Site to Site VPN is the VPN type that is used between different locations of companies. With this VPN type company sites which are in geographically different places are connected over internet securily.
What is extranet VPN?
In Extranet Based VPN , different companies are connected over internet. As the name of the VPN implies, here, each company is connected to an external company.
How many subsites are there in VPN?
There are two diferent sub Site to Site VPN types. These are:
Is IPSEC tunneling or transfer mode?
These are Transport Mode and Tunneling Mode. In transfer mode oly the message in the traffic is encrypted. On the other hand, in tunneling mode, whole data is encrypted. IPSec is a little difficult to build and it is also expensive solution if you compare with other VPN solutions.
What are the different types of VPNs?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs. In this guide, we explain how each of these VPN types work and when to use them.
How to use remote access VPN?
To use a remote access VPN on your device you typically need to install client software or configure your device’s operating system to connect to the VPN. There also needs to be a VPN server on the network end of the connection.
What is a VPN service?
A personal VPN service connects you to a VPN server, which then acts as a middleman between your device and the online services you want to access.
Why use mobile VPN?
Mobile VPNs tend to be used to ensure consistent availability for mobile workers, or for the convenience of having a VPN that tolerates connection changes. For example:
What is the problem with IPsec tunnels?
The problem with IPsec tunnels is that IPsec connects two points to each other. In a site-to-site network, for example, IPsec could be used to connect two routers to each other.
What is intranet VPN?
Intranet-Based VPN: When the networks being connected belong to a single company, the combined VPN is known as an intranet-based VPN. This enables a company to establish a single wide area network (WAN) that spans two or more of its offices. Users in the company can access resources from other sites as easily as if they were on their own site.
How many types of VPN are there?
The four types of VPN outlined here have different applications, making it easy to choose between them.
Which VPN combines the best from both IPSec and SSL?
From the description above you can understand that the AnyConnect WebVPN technology combines the best from both IPSec based VPNs and SSL based VPNs.
What is IPSEC VPN?
Remote Access with IPSec VPN Client: A VPN client software is installed on user’s PC to provide remote access to the central network. Uses the IPSec protocol and provides full network connectivity to the remote user. The users use their applications at the central site as they normally would without a VPN in place.
What is AnyConnect VPN?
The AnyConnect VPN client is a lightweight Java client (around 3MB) which can be installed or uninstalled from the remote user’s PC dynamically.
Which protocol is used for secure communication?
The first category uses the IPSec protocol for secure communications while the second category uses SSL.
What is clientless mode?
Clientless Mode WebVPN: This is the first implementation of SSL WebVPN supported from ASA version 7.0 and later. It lets users establish a secure remote access VPN tunnel using just a Web browser. There is no need for a software or hardware VPN client. However, only limited applications can be accessed remotely.
When remote users connect to our WebVPN, do they have to use HTTPS?
The following option is not required but useful, whenever someone accesses the ASA through HTTP then they will be redirected to HTTPS:
What is AnyConnect VPN?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN. AnyConnect VPN. The clientless WebVPN method does not require a VPN client to be installed on the user’s computer. You just open your web browser, ...
What happens when a VPN user terminates a session?
Normally when the remote VPN user terminates the session, the anyconnect installer will be uninstalled. The anyconnect keep-installer installed command leaves it installed on the user’s computer.
What happens when you have an inbound access list?
When you have an inbound access-list on the outside interface then all your decrypted traffic from the SSL WebVPN has to match the inbound access-list. You can either create some permit statements for the decrypted traffic or you can just tell the ASA to let this traffic bypass the access-list:
Why does my client tries to download AnyConnect?
The client tries to download the Anyconnect automatically, this is because of the anyconnect ask none default anyconnect command that we used. Since we are using a self-signed certificate you will get the following error message:
What is the IP address of AnyConnect?
You can see that we received IP address 192.168.10.100 (the first IP address from the VPN pool). Anyconnect creates an additional interface, just like the legacy Cisco VPN client does.
What is an ayconnECT_policy?
The group policy is called “ANYCONNECT_POLICY” and it’s an internal group policy which means that we configure it locally on the ASA. An external group policy could be on a RADIUS server.
