Can I use IKEv2 with Cisco ASA remote access VPN?
Note: you can use IKEv2 for Remote Access VPN as well but it will need to work with remote authentication server (RADIUS) when you configure on Cisco ASA and it will not allow you to create users locally. but you might be able to do a workaround if you edit the group policy after you finish the configuration like below:
How do I enable IPsec IKEv2 on AnyConnect?
NOTE: The AnyConnect client protocol defaults to SSL. To enable IPsec IKEv2, you must configure the IKEv2 settings on the ASA and also configure IKEv2 as the primary protocol in the client profile. The IKEv2enabled profile must be deployed to the endpoint computer, otherwise the client attempts to connect using SSL.
How do I set up an IKEv2 profile?
An IKEv2 profile must be configured and must be attached to either a crypto map or an IPSec profile on both the IKEv2 initiator and responder. Use the command set ikev2-profile profile-name to attach the profile.
How do I enable privileged exec mode in IKEv2?
Enables privileged EXEC mode. Enter your password if prompted. Enters global configuration mode. Specifies the IKEv2 authorization policy and enters IKEv2 authorization policy configuration mode. Specifies the Dynamic Host Configuration Protocol (DHCP) server to lease an IP address which is assigned to the remote access client.
How do I enable IKEv2 on my Cisco router?
To enable IKEv2 on a crypto interface, attach an IKEv2 profile to the crypto map or IPsec profile applied to the interface. You need not enable IKEv1 on individual interfaces because IKEv1 is enabled globally on all interfaces in the router.
Does Cisco AnyConnect use IKEv2?
Each of those products only supported their own protocol however with the introduction of Anyconnect Secure Mobility Client 3.0, the client can now use IPsec (IKEv2) or SSL for the transport of the VPN connection.
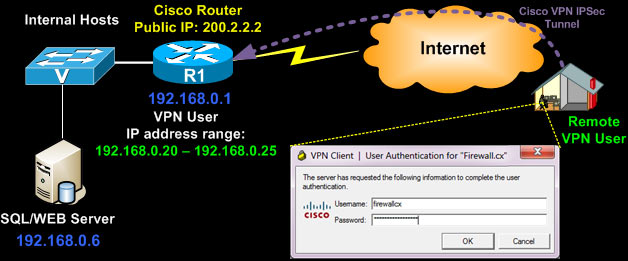
What is Cisco remote access VPN?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
What is Cisco Flex VPN?
FlexVPN is Cisco's implementation of the IKEv2 standard featuring a unified paradigm and CLI that combines site to site, remote access, hub and spoke topologies and partial meshes (spoke to spoke direct).
What type of VPN is Cisco AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
Does Cisco AnyConnect use IPsec or SSL?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Is Cisco AnyConnect a VPN?
Cisco AnyConnect Client helps us to make secure , safe and reliable VPN connection to our organization's private network with multiple security services to safe and protect company's data. It gives freedom to employees to get connected from anywhere anytime, thus making life easier for remote workers.
What is IKEv2?
IKEv2 (Internet Key Exchange version 2) is a VPN encryption protocol responsible for request and response actions. It handles the SA (security association) attribute within an authentication suite called IPSec.
What is difference between Getvpn and FlexVPN?
GET VPN is used for site-to-site only, whereas FLEX VPN is able to work with site-to-site and Remote Access (RA VPN) deployments at once. GET VPN was designed to take advantage of the inherent full-mesh capabilities of MPLS networks.
What is a DMVPN router?
A dynamic multipoint virtual private network (DMVPN) is a secure network that exchanges data between sites/routers without passing traffic through an organization's virtual private network (VPN) server or router, located at its headquarters.
How does Cisco VPN client work?
The VPN takes your computer's request and sends it to a website or system. The requested data is then forwarded back to you through that same secure connection. At CMU, we use the Cisco AnyConnect Secure Mobility Client to connect to the network through VPN.
What is VPN and why do I need it?
VPN stands for virtual private network. In basic terms, a VPN provides an encrypted server and hides your IP address from corporations, government agencies and would-be hackers. A VPN protects your identity even if you are using public or shared Wi-Fi, and your data will be kept private from any prying internet eyes.
How much does Cisco VPN cost?
OverviewAdditional DetailsPrice:$101.00MSRP:$150.53Mfr Part #:ASA-AC-E-5515=SHI Part #:254045704 more rows
How do I connect to ASU VPN?
Open the “Cisco AnyConnect Secure Mobility Client”. Give the vpn server address as “sslvpn.asu.edu/2fa” and click on connect. 2. Then use your ASURITE User ID and Password, click on OK you will be connected to VPN.
How many exchanges does IKEv2 use?
IKEv2 uses two exchanges (a total of 4 messages) to create an IKE SA and a pair of IPSec SAs. To create multiple pairs of IPSec SAs, only one additional exchange is needed for each additional pair of SAs. 2. Different authentication methods. – IKEv2 supports EAP authentication.
What is phase 2 of IKEv1?
IKEv1 phase 2 negotiation aims to set up the IPSec SA for data transmission. This process uses the fast exchange mode (3 ISAKMP messages) to complete the negotiation.
Does Cisco use encryption?
Delivery of Cisco cryptographic products does not imply third-party authority to import , export, distribute or use encryption. Importers, exporters, distributors and users are responsible for compliance with U.S. and local country laws. By using this product you agree to comply with applicable laws and regulations.
How to enable IKEv2?
To enable IKEv2 on a crypto interface, attach an IKEv2 profile to the crypto map or IPsec profile applied to the interface.
What is IKEv2 client?
Microsoft Windows 7 IKEv2 client sends IP address as IKE identity that prevents Cisco IOS IKEv2 RA server from segregating remote users based on IKE identity. To allow the Windows 7 IKEv2 client to send email address (user@domain) as IKE identity, apply the hotfix documented in KB675488 http://support.microsoft.com/kb/975488 on Microsoft Windows 7 and specify the email address string in either the user name field when prompted or the CommonName field in the certificate depending on the authentication method.
What is the name mangler in IKEv2?
Perform this task to specify the IKEv2 name mangler, which is used to derive a name for the authorization requests. The name is derived from specified portions of different forms of remote IKE identities or the EAP identity. The name mangler specified here is referred to in the IKEv2 profile.
What is an IKEv2 keyring?
An IKEv2 keyring is a repository of symmetric and asymmetric preshared keys and is independent of the IKEv1 keyring. The IKEv2 keyring is associated with an IKEv2 profile and hence, caters to a set of peers that match the IKEv2 profile. The IKEv2 keyring gets its VRF context from the associated IKEv2 profile.
How to disable NAT-T encapsulation?
Similar, to IKEv1, NAT-T is auto detected. To disable NAT-T encapsulation, use the no crypto ipsec nat-transparency udp-encapsulation command.
What happens after you create an IKEv2 proposal?
After you create the IKEv2 proposal, the proposal must be attached to a policy to pick the proposal for negotiation. For information on completing this task, see the Configuring the IKEv2 Policy section.
What is IKEv2 RA?
The IKEv2 RA server supports user and group authorizations. You can configure user authorizations, group authorizations, both, or none. The username for the user and group authorizations can be directly specified or derived from the peer IKEv2 identity using a name mangler. Group authorization can be local and external-AAA based, while user authorization can only be external-AAA based. The IKEv2 authorization policy serves as a container of IKEv2 local AAA group authorization parameters.
What does IKE stand for in IPSEC?
IKE stands for Internet Key exchange, it is the version 2 of the IKE and it has been created to provide a better solution than IKEv1 in setting up security association (SA) in IPSEC.
Which is newer, IPSEC or crypto?
NOTE: you can also create a crypto map which is the legacy way, while IPSEC profile is the newer way.
IKEv2 IPSec Remote Access VPN with Anyconnect on Cisco ASA
The Cisco AnyConnect Secure Mobility Solution provides a comprehensive, highly secure enterprise mobility solution. the Cisco AnyConnect Secure Mobility Solution continues to lead with next-generation security and encryption, including support for the Suite B set of cryptographic algorithms, and support for IPv6 networks.
Filtering Routes in BGP using Route-maps and Prefix-list
Order of preference of attributes in BGP The order of preference varies based on whether the attributes are applied for inbound updates or outbound updates.
Ansible-playbook for backing up running config of Cisco IOS
This ansible-playbook can be used to backup running configuration from Cisco IOS devices. You can refer to my earlier post Getting Started with your first ansible-playbook for Network Automation to know about the parameters used in this playbook.
Export or Backup Azure Virtual Networks or Subnet information into CSV using PowerShell
There may be times when you want to get a report that contains information of all VNETS along with their subnets and address prefixes. You might have question, how to export or backup Azure VNET or subnets information into CSV.
Ansible Playbook for Network OS Upgrade with pre and post checks
You have 100s of network switches or routers that you need to upgrade. How much time would it take for you to do the upgrades? There are a lot number of sub-tasks involved while upgrading IOS image of a Cisco router or a switch.
Export or Backup Azure Route Table into CSV using PowerShell
There could be many use cases where you may want to export Azure route tables into CSV. Here is the PowerShell script that you can use to export Azure Route Tables into CSV using PowerShell script. This script will export Azure Route Tables along with routes of all Active subscriptions into a CSV.
Download Visio Stencils for Network Topology
Microsoft Visio is a great way to draft network diagrams for documentation, and network diagrams looks more nice if correct icons are used for the devices. So, download the Visio stencils from the following link. If you have more such links, you can post them in comments and they will be added here.