Step 1. Go to Applications > Utilities then launch the Terminal.app application. Step 2. Enter the ssh command and then the IP address to access the CLI of the switch.
Full Answer
How to configure SSH to remotely access a Cisco router or switch?
Step 1: First step in configuring SSH to securely access the CLI interface of a Cisco Router or Switch remotely is to create a local user database for user authentication. Follow these steps to create a local user with username "jajish" and password as "OmniSecuPass" and with a privilege level 15.
How do I know if SSH is enabled on a switch?
5. Verify SSH access From the switch, if you do ‘sh ip ssh’, it will confirm that the SSH is enabled on this cisco device. After the above configurations, login from a remote machine to verify that you can ssh to this cisco switch.
How to configure a Cisco switch for remote management?
To accomplish this, the following will be done: (i) Assign IP addresses, subnetmask and default gateways. Implementation. The following configuration commands will the required to configure a Cisco switch for remote management.
How to configure SSH to use local username and password?
But here we configure ssh to use local username and password. Configure the router to accept only ssh connection with “ transport input ssh ” command. Configure ssh to version 2 using “ IP ssh version 2 ” and set the authentication times to 3 with “ IP ssh authentication-retries 3 ” command.
See more
Can you SSH into Cisco switch?
From the switch, if you do 'sh ip ssh', it will confirm that the SSH is enabled on this cisco device. After the above configurations, login from a remote machine to verify that you can ssh to this cisco switch. In this example, 192.168. 101.2 is the management ip-address of the switch.
What is SSH in Cisco switch?
SSH is a secure method for remote access to your router or switch, unlike telnet. SSH requires a RSA public/private key pair. SSH version 2 is more secure than version 1. Make sure you have an IOS image that supports crypto features, otherwise you can't use SSH.
When using SSH to remote access a Cisco router can you see the terminal password Why or why not?
Cisco 5. When using SSH to remotely access a Cisco router, can you see the terminal password? Why or why not? No, because it is Linux based and they do not show the passwords so you are not able to even guess it.
What is the difference in line vty 0 4 and 5 15?
VTY lines are usually used for creating out-of-band management sessions to devices. If a password is not supplied on a vty line, that line cannot be used for managing the device. In some cases administrators may decide to let junior staff to use lines 0 - 4 and senior staff to use lines 5 - 15.
How do I SSH from command prompt?
You can start an SSH session in your command prompt by executing ssh user@machine and you will be prompted to enter your password. You can create a Windows Terminal profile that does this on startup by adding the commandline setting to a profile in your settings. json file inside the list of profile objects.
How do I enable SSH?
Activate or deactivate the SSH serversudo rm -f /etc/ssh/sshd_not_to_be_run sudo systemctl enable ssh sudo systemctl start ssh.sudo mv /etc/init/ssh.conf.back /etc/init/ssh.conf sudo start ssh.sudo systemctl stop ssh sudo systemctl disable ssh.sudo stop ssh sudo mv /etc/init/ssh.conf /etc/init/ssh.conf.back.
Is Vty Telnet or SSH?
An efficient way to manage remote devices is to use VTY access, which is CLI-based remote access using Telnet or SSH. Video Player is loading.
Which two steps are required before SSH can be enabled on a Cisco router?
Cryptography.Cryptographic hash function.
What is login local Vty?
login is used on vty and console and means that the password that is user for its authentication, is configured under vty and console as well. Login local, means that authentication uses locally configured credentials using the. username
What does Vty stand for?
Virtual TeletypeWhat Does Virtual Teletype (VTY) Mean? Virtual teletype (VTY) is a command line interface (CLI) created in a router and used to facilitate a connection to the daemon via Telnet, a network protocol used in local area networks. To connect to a VTY, users must present a valid password.
How many Vty lines does a switch have?
The virtual terminal or “VTY” lines are virtual lines that allow connecting to the device using telnet or Secure Shell (SSH). Cisco devices can have up to 16 VTY lines.
What is Vty password?
The term “vty” stands for Virtual teletype. VTY is a virtual port and used to get Telnet or SSH access to the device. VTY is solely used for inbound connections to the device. These connections are all virtual with no hardware associated with them. Related Blog – VTY Password.
What is the SSH protocol?
SSH or Secure Shell is a network communication protocol that enables two computers to communicate (c.f http or hypertext transfer protocol, which is the protocol used to transfer hypertext such as web pages) and share data.
What port does SSH use?
port 22By default, the SSH server still runs in port 22.
What is the option for SSH?
The SSH options page allows the RAD to determine the specifics of the SSH protocol that should be used to connect to the devices. Set up SSH options by selecting the SSH Options sub-tab from the Resource Access Data dialog....Setting up SSH options.OptionDescriptionSSH OptionDescriptionSSH TypeSelect from the available SSH types.2 more rows
How do I SSH?
2:056:04Learn SSH In 6 Minutes - Beginners Guide to SSH Tutorial - YouTubeYouTubeStart of suggested clipEnd of suggested clipYourself to the remote server which can either be a password or a key we'll look at keys in a momentMoreYourself to the remote server which can either be a password or a key we'll look at keys in a moment but first let's make a connection to a remote server with a password.
How to remotely access Cisco switch?
The Cisco Business Managed Switches can be remotely accessed and configured through the Command Line Interface (CLI). Accessing the CLI allows commands to be entered in a terminal-based window. If you prefer to configure using terminal commands on your switch through the CLI rather than the web-based utility, this would be an easier alternative. Certain tasks such as Layer 3 mode enabling can only be performed through the CLI.
How to access CLI on switch?
This article provides instructions on how to access the CLI of your switch through SSH or Telnet using the following clients: 1 PuTTY - A standard Telnet and SSH client. You can download an installer here and install in your Windows computer. 2 Terminal - An application that is pre-installed in every Mac OS X computer. It is also known as the shell or the console.
How to remotely access CLI?
In order to remotely access the CLI of your switch, you must use an SSH or Telnet client. You must also enable the Telnet and SSH service on your switch first before you can access it remotely.
How long does it take for SSH to disconnect?
The SSH sessions disconnect automatically after the idle time configured in the switch has passed. The default idle session timeout for SSH is 10 minutes.
What port number to use for SSH?
Step 3. Enter 22 as the port number to be used for the SSH session in the Port field.
Do you need to set IP address for SSH?
Important: Before you make an SSH or Telnet connection to the switch, you must set the IP address for the switch. For instructions, click here.
What is SSH on Cisco router?
The Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. The best-known example application is for remote login to computer systems by users.
What is SSH in network?
SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with an SSH server. Common applications include remote command-line login and remote command execution, but any network service can be secured with SSH.
Objective
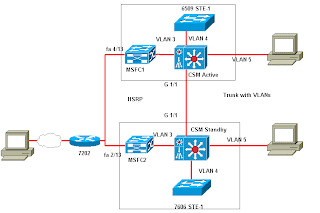
The objective of this lab is to configure the switch for remote management such that the laptop PC residing on a remote network be used to login and manage it via ssh . To accomplish this, the following will be done:
Implementation
The following configuration commands will the required to configure a Cisco switch for remote management. The commands used here a for the lab represented in the network topology used here. However, the solution can be achieved in many different ways.
Verification
To verify that I have configured the Cisco switch for remote management via ssh, I try to access the switch using the laptop on the network 192.168.0.0/24 using ssh. Remember that both the laptop and the switch are on different networks. See the result below.
Does the default gateway include the mask?
Configuration of default gateway takes place in the configuration mode and the command does not include the mask for the ip.
Can you use static NAT on a router?
You can use static nat on your router for this issue. Your switch doesn't support to nat.
Is Cisco hosting the IT Blog Awards 2021?
The 2021 IT Blog Awards, hosted by Cisco, is now open for submissions. Submit your blog, vlog or podcast today. For more information, including category details, the process, past winners and FAQs, check out: https://www.cisco.com/c/en/us/t... view more
Enable Cisco SSH
Would you like to learn how to enable Cisco SSH remote access using the command-line? In this tutorial, we are going to show you all the steps required to configure the SSH remote access on a Cisco Switch 2960 or 3750 using the command-line.
Cisco Switch Playlist
On this page, we offer quick access to a list of videos related to Cisco Switch.
What is SSH in network?
Network administrators must disable telnet and use only SSH wherever possible. SSH (Secure Shell) is a protocol which define how to connect securely over a network. SSH (Secure Shell) protocol provides the three main ideas of security authentication, confidentiality (via encryption) and integrity of data transfer over a network.
What port number does SSH use?
SSH uses TCP as its transport layer protocol and uses well-kown port number 22.
What is SSH authentication?
SSH supports Authentication to reliably determine the identity of the connecting computer, encryption to scramble data so that only the intended recipient only can read it and Integrity to guarantees the data sent over the network is not changed by a third party. SSH has two main versions, SSH1 and SSH2.
What is the default device name for RSA encryption?
Before generating RSA encryption keys, you must change the default hostname of a Cisco Router or Switch. The default device name of a Cisco Router is "Router" and default device name of a Cisco Switch is "Switch". You must configure a domain name also before generating RSA keys. Follow these Cisco IOS CLI commands to configure a hostname, ...
What is Cisco Secure Endpoint?
Cisco Secure Endpoint New packages fit for every organization Every Cisco Secure Endpoint (formerly AMP for Endpoints) package comes with Cisco SecureX built-in. It’s our cloud-native platform that integrates all your security solutions into one view wit... view more
Do you need to set IP domain name for generating key?
Apart from those commands as sandeep stated here... you need to set ip domain-name as well for generating the key. Because you key will get generated based on your hostname... i.e. .
Is Cisco 1841 compatible with Cisco 1841?
Those advanced IP Services are compatible with cisco 1841 routers..... current IOS is in specific to broadband which has some limited facilities..... for eg advip ios has much more features of IP SLA but broadband IOS has only IP SLA Responder feature.... Like this way you have many other differences mate....
Is Cisco Secure a partner of IBM?
This month, we're excited to bring awareness to a newly formed partnership between Cisco Secure and IBM. Securing today's dynamic enterprise applications is critical. With hybrid and multi-cloud adoption, traditional network-based security ran into limita... view more
Does Cisco IOS support SSH?
You will need an image that supports SSH (images with k9) Yes. Starting with Cisco IOS Software Release 12.4 (1), SSH is supported in all images with the following exceptions: IP Base without Crypto and Enterprise Base without Crypto. Use this command: Router (config)# crypto key generate rsa.
How to enable SSH on Cisco?
Follow the steps mentioned below, which will enable SSH access to your Cisco devices. Once you enable SSH, you can access it remotely using PuTTY or any other SSH client. 1. Setup Management IP. First, make sure you have performed basic network configurations on your switch. For example, assign default gateway, assign management ip-address, etc.
What is the IP address of 101 VLAN?
In the following example, the management ip address is set as 192.168.101.2 in the 101 VLAN. The default gateway points to the firewall, which is 192.168.101.1
Does a router need RSA keys?
The switch or router should have RSA keys that it will use during the SSH process. So, generate these using crypto command as shown below.

Introduction
Prerequisites
- Requirements
The Cisco IOS image used must be a k9(crypto) image in order to support SSH. For example c3750e-universalk9-tar.122-35.SE5.taris a k9 (crypto) image. - Components Used
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command. The informati…
Test Authentication
- Authentication Test without SSH
First test the authentication without SSH to make sure that authentication works with the router Carter before you add SSH. Authentication can be with a local username and password or with an authentication, authorization, and accounting (AAA) server that runs TACACS+ or RADIUS. (Auth… - Authentication Test with SSH
In order to test authentication with SSH, you have to add to the previous statements in order to enable SSH on Carter and test SSH from the PC and UNIX stations. At this point, the show crypto key mypubkey rsacommand must show the generated key. After you add the SSH configuration, …
Debug and Show Commands
- Before you issue the debug commands described here, refer to Important Information on Debug Commands. Certain show commands are supported by the Output Interpreter Tool (registered to customers only), which allows you to view an analysis of showcommand output. 1. debug ip ssh Displays debug messages for SSH. 2. show ssh Displays the status of SSH server connectio…
Sample Debug Output
- Server Debug
Note: This is Solaris machine output.
Tips
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configur…
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configured for the router. Each SSH connection uses a vtyresource.
- SSH uses either local security or the security protocol configured through AAA on your router for user authentication. When you configure AAA, you must ensure that the console is not run under AAA....