
In the configuration utility, on the Configuration tab, expand Citrix Gateway > Policies > Auditing. In Name, type a name for the policy. Select one of the following: Syslog if you want to send the logs to a Syslog server. Nslog to store the logs on Citrix Gateway.
Full Answer
What is remote PC access in Citrix Virtual Apps?
Remote PC Access is a feature of Citrix Virtual Apps and Desktops that enables organizations to easily allow their employees to access corporate resources remotely in a secure manner. The Citrix platform makes this secure access possible by giving users access to their physical office PCs.
How to configure logging on Citrix gateway?
When you configure logging on Citrix Gateway, you can choose to store the audit logs on Citrix Gateway or send them to a syslog server. You use the configuration utility to create auditing policies and configure settings to store the audit logs. In the configuration utility, on the Configuration tab, expand Citrix Gateway > Policies > Auditing.
How to manage multiple users with remote access to Citrix Workspace?
Install the Citrix Workspace app on each client device that accesses the office PC. Multiple users with remote access to the same office PC see the same icon in Citrix Workspace app. When any user remotely logs on to the PC, that resource appears as unavailable to other users.
What is Citrix and how does it work?
The Citrix platform makes this secure access possible by giving users access to their physical office PCs. If users can access their office PCs, they can access all the applications, data, and resources they need to do their work.
How to change Citrix auditing policy?
How to remove auditing policy from Citrix?
Is Citrix translated?
About this website
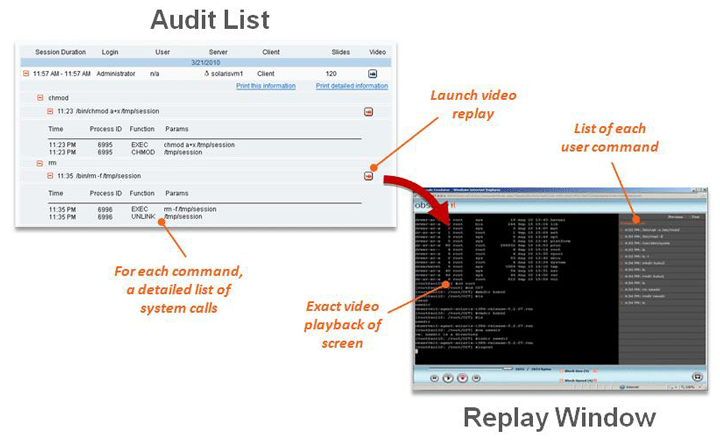
How do I check my Citrix Receiver logs?
Browse to the appropriate Log location for your OS.Receiver Log: %USERPROFILE%\AppData\Local\Citrix\Receiver for Windows 7.Authentication Manager Logs: %USERPROFILE%\AppData\Local\Citrix\Receiver\AuthManager\Tracing.
Where can I find Citrix logs?
Citrix Workspace AppLog FilePurposeLocationSelfService.logReceiver Logging – SelfService%localappdata%\Citrix\SelfServicetrace-pnsson.logSingle Sign On logsC:\Program Files(x86)\Citrix\Online Plugin\Logs(custom path can be set)Receiver_Browser.logReceiver Logging – Browser%localappdata%\Citrix\Browser2 more rows•Jun 13, 2020
How do I read Citrix Workspace logs?
View logs in the Event Viewer > Applications and Services Logs > Norskale Broker Service pane. Citrix WEM Infrastructure Service Debug. log. The log that lets you troubleshoot issues with the Citrix WEM infrastructure service (Norskale Broker Service.exe).
Where are Citrix VDA logs stored?
Verbose logs are generated in following path: C:\Program Files\Citrix\Receiver Storefront\Admin\Trace C:\Program Files\Citrix\Receiver StoreFront\logs Ica.
What is CTX log?
CTX-Logging. This module contains a Cortex subtask which allows users to log information to the database in a structured format.
How do I check logs in Citrix netscaler?
To search all Citrix ADM system audit log messages present in the Citrix ADM software, from the Citrix ADM GUI, navigate to Settings > Audit Log Messages. The new filter categories are instance, module, event, severity, and message.
What does Citrix WEM do?
WEM is a flexible tool that can help improve Citrix deployments by decreasing logon times, improving system performance, streamlining the admin experience, and providing users with the best possible experience.
How do I collect logs for Citrix Workspace app on Mac?
Collecting logs:Open Citrix Workspace app.Right-click on Citrix Workspace in the toolbar and click Preferences > Advanced.Select Logging.Select one of the following session log levels: ... Select one of the following store log levels: ... Click Email Log Files to collect and share logs as a .
How do I log into Citrix on a Mac?
Citrix Receiver - In order to access your remote desktop the “Citrix Receiver” application is required. From your browser navigate to: https://remote.collierschools.com Page 2 The following login page will appear. Enter your network credentials and click “Log On”. Click the “Receiver for Mac” under Links.
What is VDA in Citrix?
Virtual Delivery Agent (VDA) VDAs establish and manage the connection between the machine and the user device. VDAs also verify that a Citrix license is available for the user or session, and apply policies that are configured for the session.
What is syslog in netscaler?
Syslog is the standard used for logging information. Syslog enables isolation of the system that generates information and the system that stores the information.
What is Mcsdif VHDX?
mcsdif. vhdx is spiking which is causing the cache drive to fill up. This can cause performance issues, a hung server or a server to crash.
How do I collect logs for Citrix Workspace app on Mac?
Collecting logs:Open Citrix Workspace app.Right-click on Citrix Workspace in the toolbar and click Preferences > Advanced.Select Logging.Select one of the following session log levels: ... Select one of the following store log levels: ... Click Email Log Files to collect and share logs as a .
What is Citrix scout used for?
Introduction. Citrix Scout collects diagnostics that can be used for proactive maintenance in your XenApp and XenDesktop deployment. Citrix offers comprehensive, automated analysis through Citrix Insight Services. You can also use Scout to troubleshoot issues, either on your own or with guidance from Citrix Support.
What is syslog in netscaler?
Syslog is the standard used for logging information. Syslog enables isolation of the system that generates information and the system that stores the information.
Viewing the ADC Logs - NetScaler Application Delivery Controller ...
Hi all, I needs a view historical logs on the ADC. I have managed to locate them on the System>Diagnostics>Maintenance>Delete/Download log files. I have downloaded them to my machine.. however is there a way to view the logs as notepad doesnt seem to cut it Adil
How find the last time user has logged in to the Citrix-environment?
Hi! I have the following problem; I need to find out when a user has logged in to our Citrix-environment the last time. We are using XenDEsktop 7.14.1 from which we publish desktops and apps to users. I need this information from all of our Citrix users. The problem is that I cannot simply check ...
Solved: Generate a Citrix Login history for a user without having any ...
Version: Citrix Xenapp 6.5 I need to generate a login report for Citrix for the past month for a specific user. Problem is I don't have any tools like EdgeSight to can be used. I only have 3 Citrix Servers. Is there an script/query I can do to find out if users logged in from any of those servers?
What is remote access in Citrix?
Remote PC Access is a feature of Citrix Virtual Apps and Desktops that enables organizations to easily allow their employees to access corporate resources remotely in a secure manner. The Citrix platform makes this secure access possible by giving users access to their physical office PCs. If users can access their office PCs, they can access all the applications, data, and resources they need to do their work. Remote PC Access eliminates the need to introduce and provide other tools to accommodate teleworking. For example, virtual desktops or applications and their associated infrastructure.
When does the remote user have preference over the local user?
By default, the remote user has preference over the local user when the connection message is not acknowledged within the timeout period. To configure the behavior, use this setting:
What does VDA do when it is remote?
If the VDA detects that it is running on a virtual machine, it automatically disables Remote PC Access mode. To enable Remote PC Access mode, add the following registry setting:
Why is my local monitor not blank?
If the Windows PC’s local monitor is not blank while there is an active HDX session (the local monitor displays what’s happening in the session) it is likely due to issues with the GPU vendor’s driver. To resolve the issue, give the Citrix Indirect Display driver (IDD) higher priority than the graphic card’s vendor driver by setting the following registry value:
How to allow remote access to go into sleep mode?
To allow a Remote PC Access machine to go into a sleep state, add this registry setting on the VDA, and then restart the machine. After the restart, the operating system power saving settings are respected. The machine goes into sleep mode after the preconfigured idle timer passes. After the machine wakes up, it reregisters with the Delivery Controller.
How to stop remote user session?
By default, a remote user’s session is automatically disconnected when a local user initiates a session on that machine (by pressing CTRL+ATL+DEL). To prevent this automatic action, add the following registry entry on the office PC, and then restart the machine.
Can I use remote access on my laptop?
Ensure that the Delivery Controllers or Cloud Connectors can be reached from the Wi-Fi network. You can use Remote PC Access on laptop computers. Ensure the laptop is connected to a power source instead of running on the battery. Configure the laptop power options to match the options of a desktop PC.
Why is Citrix remote access important?
Remote access is great for teleworkers, contractors, those who work from home , or individuals displaced from their home office due to natural disaster or other circumstances. It is valuable for businesses to have a strategy for allowing remote access to their users. Employees may have the flexibility to work from home, or have a plan in place if they are not able to go into the office during a natural disaster. View Citrix Remote PC Access
What is Citrix Networking?
With Citrix Networking and SmartAccess, organizations have the capability to control printers, client devices, session connectivity, and reactive security postures. Admins are also able to leverage the full capabilities of Citrix Analytics to collect data for improving app performance, supporting continuous operations, and enhancing security.
What are the benefits of remote access?
Remote access can bring many benefits to a business, from lowering costs to increasing worker satisfaction and productivity.
What is remote access?
Remote access is the act of connecting to IT services, applications or data from a location other than headquarters or a location closest to the data center. This connection allows users to access a network or computer remotely via an internet connection or telecommunications. Secure remote access benefits include: ...
How does remote access benefit a business?
Remote access can bring many benefits to your business, from lowering costs to increasing worker satisfaction and productivity.
How does secure remote access work?
Every remote worker needs a way to connect with remote desktop services and applications that won't slow down their workflows. At the same time, IT administrators must manage those connections to ensure they don't leave the network open to threats.
Why is secure remote access important to remote work security?
Secure remote access approaches are so vital because it’s now impossible to control security at the endpoint. Each user in a remote or hybrid workforce is connecting to the network from a different type of computer or smartphone, and they’re using a variety of internet connections to log in.
What are Windows login rights?
The Windows logon rights are: log on locally, log on through Remote Desktop Services, log on over the network (access this computer from the network), log on as a batch job, and log on as a service. For computer accounts, grant computers only the logon rights they require.
How to resume local access?
To resume local access, the user presses Ctrl-Alt-Del on the local PC and then logs on with the same credentials used by the remote session. The user can also resume local access by inserting a smart card or leveraging biometrics, if your system has appropriate third-party Credential Provider integration. This default behavior can be overridden by enabling Fast User Switching via Group Policy Objects (GPOs) or by editing the registry.
What is a logon rights?
Manage logon rights. Logon rights are required for both user accounts and computer accounts. As with Microsoft Windows privileges, logon rights continue to be applied to desktops in the usual way: configure logon rights through User Rights Assignment and group memberships through Group Policy.
How to check XML trust setting?
To check the XML trust setting’s current value, run Get-BrokerSite and inspect the value of TrustRequestsSentToTheXMLServicePort.
What is pooled desktop?
If a desktop is a pooled desktop rather than a dedicated desktop, the user must be trusted in respect of all other users of that desktop, including future users. All users of the desktop need to be aware of the potential permanent risk to their data security posed by this situation.
What is managed user device?
Managed user devices are under administrative control; they are either under your own control, or the control of another organization that you trust. You may configure and supply user devices directly to users; alternatively, you may provide terminals on which a single desktop runs in full-screen-only mode. Follow the general security best practices described above for all managed user devices. This release has the advantage that minimal software is required on a user device.
Do you grant users the login rights?
For user accounts, grant users only the logon rights they require.
What is Citrix ADC appliance?
The Citrix ADC appliance evaluates all the policies that are bind to true.
How to configure policy based logging?
To configure policy-based logging, you configure an audit-message action that uses Advanced policy expressions to specify the format of the audit messages. And associate the action with a policy. The policy can be bound either globally or to a load balancing or content switching virtual server. You can use audit-message actions to log messages at various log levels, either in syslog format only or in both syslog and new nslog formats
What is binding audit log policies?
Binding audit-log policies to global entities. You must globally bind the audit log policies to global entities such SYSTEM, VPN, Citrix ADC AAA and so on. You can do it to enable logging of all Citrix ADC system events. By defining the priority level, you can set the evaluation order of the audit server logging. Priority 0 is the highest and is evaluated first. The higher the priority number, the lower is the priority of evaluation.
What is a syslog action?
A syslog action contains a reference to a syslog server. It specifies which information to log and mentions how to log that information.
What is audit log?
Audit-logging displays status information from different modules so that an administrator can see event history in the chronological order. Main components of an Audit framework are ‘audit action’, ‘audit policy’. ‘Audit action’ describes Audit Server configuration information whereas ‘audit policy’ links a bind entity to an ‘audit action’. The audit policies use ‘Classic Policy Engine’ (CPE) framework or Progress Integration (PI) framework to link ‘audit action’ to ‘system global bind entities’.
Is Citrix translated?
The official version of this content is in English. Some of the Citrix documentation content is machine translated for your convenience only. Citrix has no control over machine-translated content, which may contain errors, inaccuracies or unsuitable language. No warranty of any kind, either expressed or implied, is made as to the accuracy, reliability, suitability, or correctness of any translations made from the English original into any other language, or that your Citrix product or service conforms to any machine translated content, and any warranty provided under the applicable end user license agreement or terms of service, or any other agreement with Citrix, that the product or service conforms with any documentation shall not apply to the extent that such documentation has been machine translated. Citrix will not be held responsible for any damage or issues that may arise from using machine-translated content.
Can you bind audit log policies to global entities?
Currently, the Advanced expression can bind audit-log policies only to System global entities. Note. When you bind a policy to global entities, you must bind it to a system global entity of the same expression. For example, you cannot bind a classic policy to an advanced global entity or bind an advanced policy to a classic global entity.
Can ADM pull information from Netscaler?
If they were always connecting through the Netscaler you should be able to pull that information with ADM.
Is the Citrix agenda online?
The Citrix Converge 2021 agenda is now online
How to request remote access VA?
You may request remote access by visiting the Remote Access Self Service Portal ( only available while on VA's internal network).
How to disable automatic server selection in VPN?
In the VPN tab of the setting screen, uncheck Enable automatic server selection. Close the settings.
How to enable TLS 1.1?
To enable TLS within Internet Explorer: Select ‘Tools’, then ‘Internet Options’, then the ‘Advanced’ tab. Enable the checkbox for ‘Use TL S 1.1’ (found towards the end of the list).
Is VA responsible for non-VA websites?
This page includes links to other websites outside our control and jurisdiction. VA is not responsible for the privacy practices or the content of non-VA Web sites. We encourage you to review the privacy policy or terms and conditions of those sites to fully understand what information is collected and how it is used.
How to access Citrix hard drive?
Here are steps to access files on your local computer's hard drive, optical disks, or thumb drives. From Inside of the Citrix desktop. Click on the Windows Start Button and click on Computer. Below those drives, you will see another set of drives under the Other category .
Can you move files between Citrix desktops?
You should be able to save and move files freely between the Citrix desktop drives and your local computer drives if you wish to do so. Keep in mind, Virsage backs up your files inside the Citrix desktop only.
How to change Citrix auditing policy?
In the configuration utility, on the Configuration tab, expand Citrix Gateway > Policies > Auditing. Select either Syslog or Nslog. In the details pane, click a policy and then click Open.
How to remove auditing policy from Citrix?
When you remove an auditing policy, the policy is unbound automatically. In the configuration utility, on the Configuration tab, expand Citrix Gateway > Policies > Auditing. Select either Syslog or Nslog. In the details pane, click a policy and then click Remove.
Is Citrix translated?
The official version of this content is in English. Some of the Citrix documentation content is machine translated for your convenience only. Citrix has no control over machine-translated content, which may contain errors, inaccuracies or unsuitable language. No warranty of any kind, either expressed or implied, is made as to the accuracy, reliability, suitability, or correctness of any translations made from the English original into any other language, or that your Citrix product or service conforms to any machine translated content, and any warranty provided under the applicable end user license agreement or terms of service, or any other agreement with Citrix, that the product or service conforms with any documentation shall not apply to the extent that such documentation has been machine translated. Citrix will not be held responsible for any damage or issues that may arise from using machine-translated content.

Considerations
Deployment Considerations
Machine Catalog Considerations
Linux VDA Considerations
Technical Requirements and Considerations
Configuration Sequence
Features Managed Through The Registry
Session Management Logging
- Remote PC Access now has logging capabilities that log when someone tries to access a PC with an active ICA session. This allows you to monitor your environment for unwanted or unexpected activity and be able to audit such events if you need to investigate any incidents. Events are logged using Windows Event Viewer and are in Applications and Servi...
Wake on Lan
Wake on Lan – Sccm-Integrated
Considerations
Deployment Considerations
Machine Catalog Considerations
Linux VDA Considerations
Technical Requirements and Considerations
Configuration Sequence
Features Managed Through The Registry
- Sleep mode
To allow a Remote PC Access machine to go into a sleep state, add this registry setting on the VDA, and then restart the machine. After the restart, the operating system power saving settings are respected. The machine goes into sleep mode after the preconfigured idle timer passes. Aft… - Session management
By default, a remote user’s session is automatically disconnected when a local user initiates a session on that machine (by pressing CTRL+ATL+DEL). To prevent this automatic action, add the following registry entry on the office PC, and then restart the machine. HKEY_LOCAL_MACHINE\…
Wake on Lan
Troubleshoot
More Resources