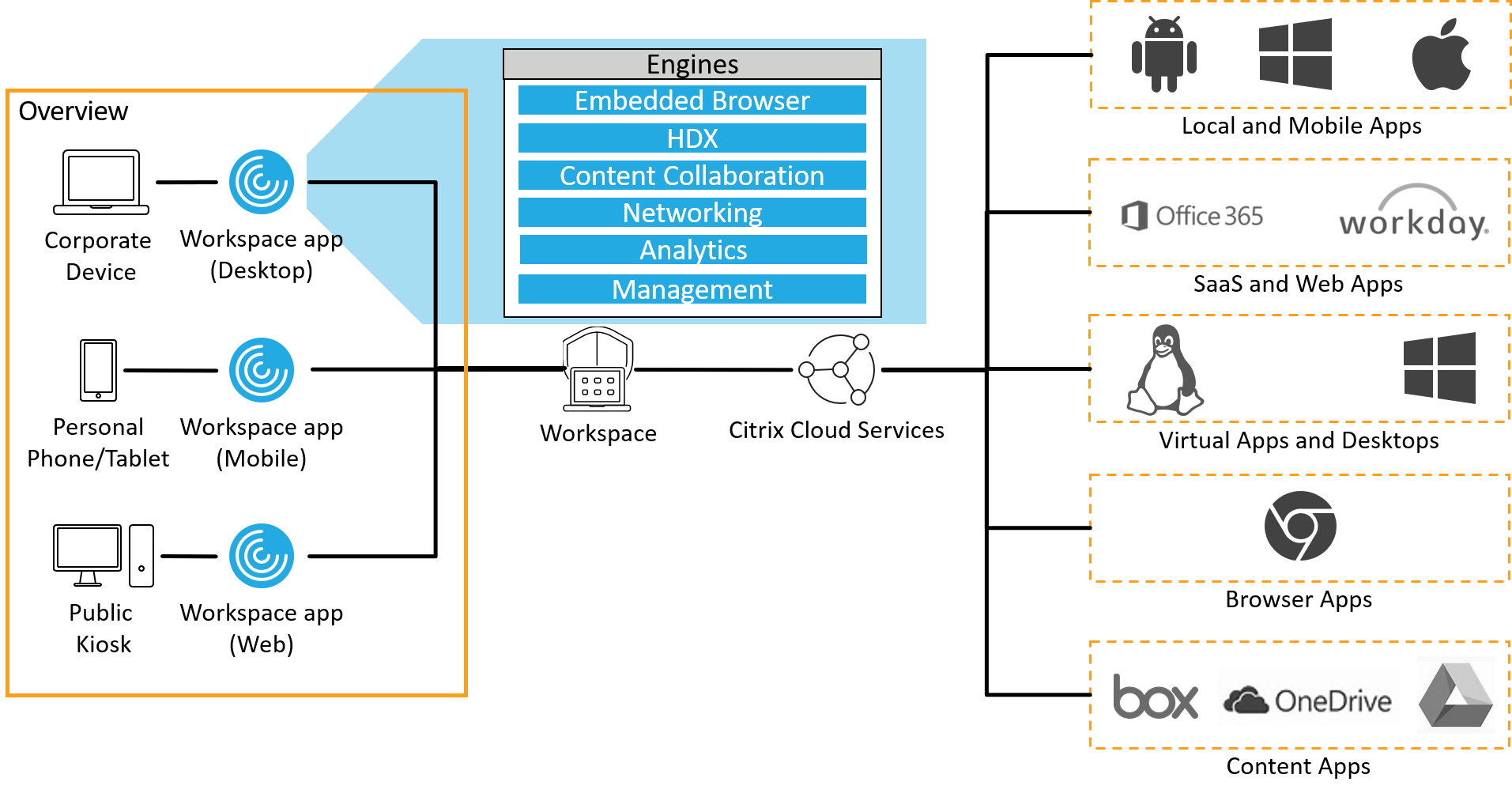
Citrix has secure remote access solutions
- Citrix Secure Private Access provides zero trust network access for all of an organization's applications, meaning their...
- Citrix Secure Internet Access creates a safe way for users to access SaaS and web applications, protecting them from...
- Citrix Web App and API Protection provides protection against both known security...
Full Answer
How to install and configure Citrix remote PC?
This guide will showcase how to perform the following actions:
- Create a Citrix Cloud account (if you don’t have one already)
- Obtain a Citrix Virtual Desktops service account
- Create a new Resource Location (your office) and install the Citrix Cloud Connectors in it
- Install Citrix Virtual Delivery Agent on the Remote PC Access hosts
- Create a Machine Catalog in Citrix Virtual Desktops service
- Create a Delivery Group
How to access Citrix?
How to Access Citrix From Windows. Google Chrome, Mozilla Firefox, or Edge provide the best experience for this. Go to URL: https://citrix.wcsu.edu. If prompted for a username and password, log in with your full WCSU email address as the username and your current WCSU email password for the password. If prompted, you also want to complete the ...
How to enable remote access for remote management?
To set up remote management:
- Launch a web browser from a computer or mobile device that is connected to your router’s network.
- Enter http://www.routerlogin.net. ...
- Enter the router user name and password. ...
- Select ADVANCED > Advanced Setup > Remote Management. ...
- Select the Turn Remote Management On check box.
How to access the remote connection?
- The remote computer must be turned on at all times and have a network connection.
- The client and server applications need to be installed and enabled.
- You need the IP address or the name of the remote machine you want to connect to.
- You need to have the necessary permissions to access the remote computer.
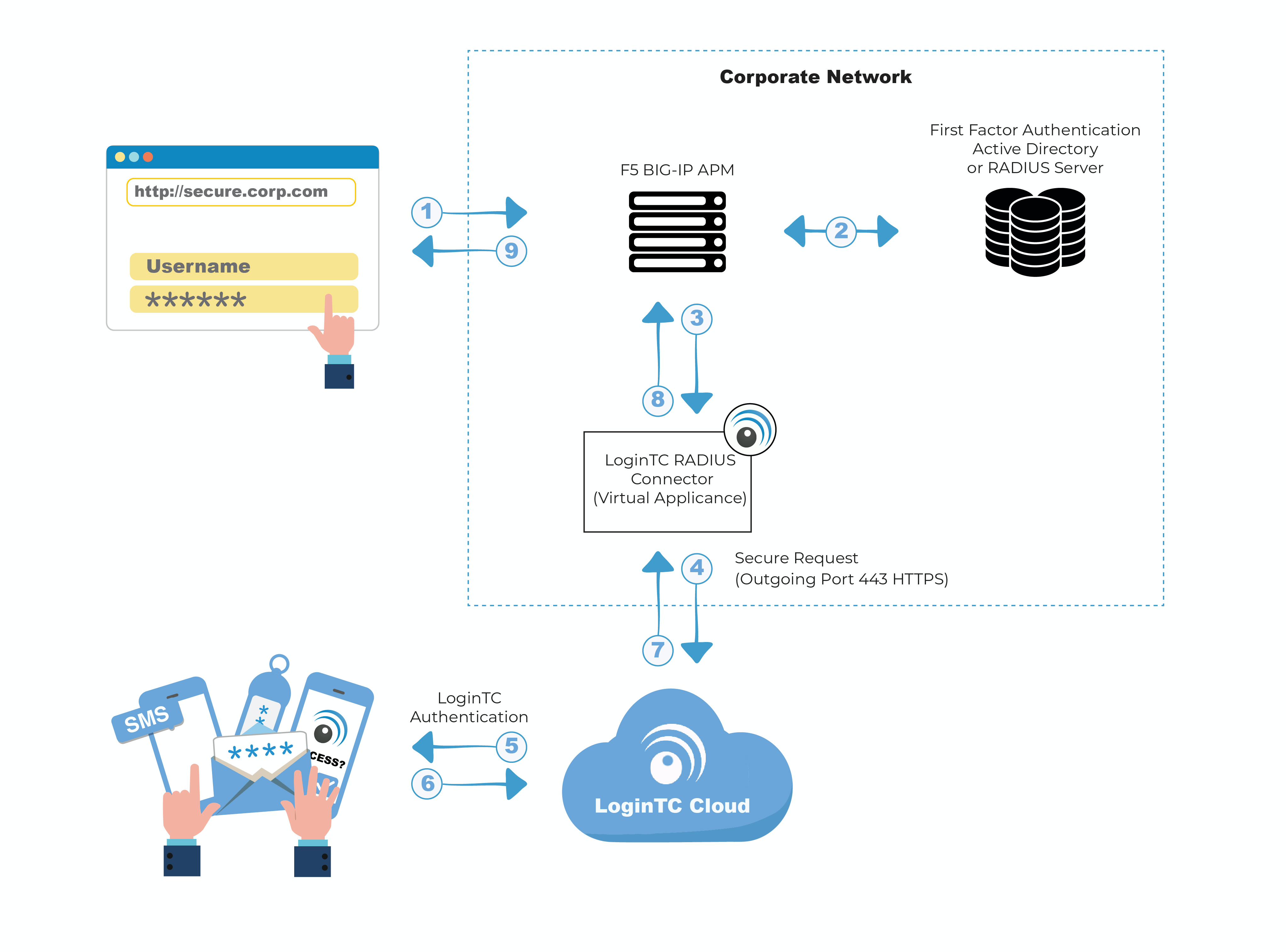
Is Citrix remote desktop secure?
Citrix ADC is a secure and unified front-end for all applications that provides administrators granular application and device-level control, while enabling users to single sign-on across all applications from one URL, and giving them access to these applications from anywhere, and by using any device.
Does Citrix provide security?
Citrix Web App and API Protection service offers holistic, layered protection against known and zero-day application attacks. This cloud-based service combines a web app firewall, bot management, and DDoS protection to keep all application types secure and help you maintain a consistent security posture.
How do I use Citrix secure Access?
How users connect with the Citrix Secure Access agent.Full VPN setup on a Citrix Gateway appliance.Select the user access method.Deploy Citrix Secure Access agent for user access.Select the Citrix Secure Access agent for users. ... Integrate the Citrix Secure Access agent with Citrix Workspace app.More items...•
Is Citrix a security risk?
Vulnerabilities have been identified in Citrix Workspace app and Citrix Receiver for Windows that could result in a local user escalating their privilege level to administrator during the uninstallation process. The issues have the following identifiers: CVE-2020-13884. CVE-2020-13885.
Are Citrix connections encrypted?
Citrix DaaS handles four types of credentials: User Credentials: When using a customer-managed StoreFront, the Cloud Connector encrypts user credentials using AES-256 encryption and a random one-time key generated for each launch.
What is Citrix Access Control?
Access control identifies users by verifying various login credentials, which can include usernames and passwords, PINs, biometric scans, and security tokens. Many access control systems also include multifactor authentication (MFA), a method that requires multiple authentication methods to verify a user's identity.
Is Citrix considered VPN?
Citrix Workspace provides a cloud- based, VPN-less solution to access all intranet web, SaaS, mobile, and virtual applications—whether using managed, unmanaged, or bring-your-own devices (BYOD) over any network.
Whats the difference between VPN and Citrix?
The primary difference is that on Citrix, users gain access to their virtual workstation and resources. Meanwhile, the VPN operates directly with the device used and all of its software and applications.
Is Citrix more secure than VPN?
Because of the limited data transmission, Citrix is much more secure than a VPN. The remote server protects you from external threats that can compromise your devices or data. Also, server administrators can control which data is allowed to leave the corporate network.
What is the benefit of using Citrix?
Citrix Virtual Desktops – easily enable remote access The ability to easily access your desktop on any device. Easily being able to access your desktop remotely. Being able to manage everything centrally, instead of manually updating devices individually.
What is Citrix application delivery and security?
Citrix application delivery and security solutions are designed to ensure that business-critical applications perform well and remain secure. Centered around a comprehensive application delivery controller and advanced WAN, these solutions help companies succeed by ensuring an optimal user experience.
What is Citrix encryption?
Citrix Files Encrypted Email allows you to encrypt the body of your message to your recipient, along with any attachments, with industry-standard AES 256 bit encryption.
What is secure remote access?
Secure remote access represents any security policy, program, or strategy that safeguards a specific application or network from unauthorized access. Rather than utilizing one cybersecurity strategy, secure remote access incorporates multiple security solutions to ensure your business’s confidential information is protected, no matter where your network is being utilized.
Why is remote access important?
Remote access security is crucial for businesses that have a remote workforce, as these employees need to safely access corporate networks from multiple places. As many remote employees work from home, an unsecured network could lead to massive data breaches on both personal and company servers. If your business shares sensitive data to clients via a corporate network, the proper security precautions need to be implemented to protect both parties from malicious code.
What is cloud app security?
Cloud app security refers to the security measures taken to protect corporate assets and data stored within a cloud-based application. Much like establishing secure remote access, cloud app security involves implementing multiple independent strategies to mitigate vulnerabilities within your cloud-based apps.
Why is cloud app security important?
Ensuring your cloud apps are utilizing built-in security options will help mitigate data loss and protect your organization from remote threats. It’s also important to select cloud services that align with your business’s unique security needs, especially if you have a remote work force.
How to secure your cloud?
This includes identifying which applications you are currently using, as well those you plan to integrate into your network in the future. Once identified, it’s important to assess these services for any potential cybersecurity risks or vulnerabilities so you can get started implementing the right security measures. Some of the most common cloud app security strategies include:
What is endpoint security?
Endpoint security is the process of securing endpoints — or end-user devices like desktops, laptops, smartphones, and tablets — on a network. Endpoint security solutions often include antivirus software, firewall checks, keeping patches of operating systems up-to-date, and ensuring sensitive information is not being cached.
Why is it important to adjust user permissions?
Adjusting user permissions within your cloud apps allows you to assign or prevent access to sensitive data. Similarly, it’s important to regulate what devices can securely access your cloud network. Many cloud-based services allow you to restrict certain devices from designated applications.
Why is Citrix remote access important?
Remote access is great for teleworkers, contractors, those who work from home , or individuals displaced from their home office due to natural disaster or other circumstances. It is valuable for businesses to have a strategy for allowing remote access to their users. Employees may have the flexibility to work from home, or have a plan in place if they are not able to go into the office during a natural disaster. View Citrix Remote PC Access
What is Citrix Networking?
With Citrix Networking and SmartAccess, organizations have the capability to control printers, client devices, session connectivity, and reactive security postures. Admins are also able to leverage the full capabilities of Citrix Analytics to collect data for improving app performance, supporting continuous operations, and enhancing security.
How does remote access benefit a business?
Remote access can bring many benefits to your business, from lowering costs to increasing worker satisfaction and productivity.
What is remote access?
Remote access is the act of connecting to IT services, applications or data from a location other than headquarters or a location closest to the data center. This connection allows users to access a network or computer remotely via an internet connection or telecommunications. Secure remote access benefits include: ...
What are the benefits of remote access?
Remote access can bring many benefits to a business, from lowering costs to increasing worker satisfaction and productivity.
What is Citrix Secure Internet Access?
Citrix Secure Internet Access is a cloud-delivered security service for securing remote workers from any location or device. A full replacement for hardware security stacks, it integrates 10+ threat intelligence feeds for robust malware defense.
What does modern remote work security require?
More specifically, remote workers need access to data and applications from virtually anywhere, and often from multiple devices.
What are the key elements for securing remote environments?
To mitigate the device and data security risks facing remote workers, organizations must protect cloud and on-premises corporate applications, while simultaneously securing SaaS and web access . The best remote worker security solutions for these purposes will be tightly integrated within a single-pass architecture that reduces latency and maximizes performance.
What is SaaS security?
Secure access to a full range of SaaS applications, such as collaboration software and productivity suites, within remote work environments, whether those applications are being used for work-related or personal purposes.
What is the third issue with VPNs?
The third issue, with VPNs, highlights the overall challenge in enabling modern remote work security — na mely, how to balance airtight application and data protection with acceptable performance and streamlined access for legitimate end users across the company WAN.
What is ubiquitous remote working?
Ubiquitous remote working means that the classic network perimeter model of cyber security — under which initial remote access is granted via VPN, and any subsequent activity within the corporate WAN is deemed safe — no longer works. More specifically, remote workers need access to data and applications from virtually anywhere, and often from multiple devices.
Can a corporate network assume that a remote access request is legitimate?
Remote employees are using personal devices instead of company hardware, complicating endpoint management. Corporate networks cannot assume that any remote access request is legitimate until multiple remote security measures have been applied, as it might come from any number of unmanaged device types. Moreover, users within VPNs have discretion to move laterally through a network, spreading malware. Context-aware “just in time” and just enough” access models are needed instead.
What are Windows login rights?
The Windows logon rights are: log on locally, log on through Remote Desktop Services, log on over the network (access this computer from the network), log on as a batch job, and log on as a service. For computer accounts, grant computers only the logon rights they require.
How to resume local access?
To resume local access, the user presses Ctrl-Alt-Del on the local PC and then logs on with the same credentials used by the remote session. The user can also resume local access by inserting a smart card or leveraging biometrics, if your system has appropriate third-party Credential Provider integration. This default behavior can be overridden by enabling Fast User Switching via Group Policy Objects (GPOs) or by editing the registry.
What is a logon rights?
Manage logon rights. Logon rights are required for both user accounts and computer accounts. As with Microsoft Windows privileges, logon rights continue to be applied to desktops in the usual way: configure logon rights through User Rights Assignment and group memberships through Group Policy.
How to prevent non-admin users from performing malicious actions?
To prevent non-admin users from performing malicious actions, we recommend that you configure Windows AppLocker rules for installers, applications, executables and scripts on the VDA host and on the local Windows client.
How to check XML trust setting?
To check the XML trust setting’s current value, run Get-BrokerSite and inspect the value of TrustRequestsSentToTheXMLServicePort.
What is pooled desktop?
If a desktop is a pooled desktop rather than a dedicated desktop, the user must be trusted in respect of all other users of that desktop, including future users. All users of the desktop need to be aware of the potential permanent risk to their data security posed by this situation.
What is managed user device?
Managed user devices are under administrative control; they are either under your own control, or the control of another organization that you trust. You may configure and supply user devices directly to users; alternatively, you may provide terminals on which a single desktop runs in full-screen-only mode. Follow the general security best practices described above for all managed user devices. This release has the advantage that minimal software is required on a user device.
Why is remote access important?
An access control solution that employees and stakeholders can use safely will simplify operations and increase productivity. Ensure employees have seamless access to the applications and resources they need even when they move across devices, and improve efficiency with the flexibility to store and access data securely.
Why do companies need to have secure access to data?
With the increase of hybrid workforces, both remote and in-house employees need easy and secure access to applications and data. Companies cannot risk their data over dispersed devices without a central security system.
Why do you need to secure your workspace?
Workspace security ensures that workforces can function from anywhere at any time without compromising the organization’s security. The more solution providers, systems, and data connecting to an organization, the greater the security risks.
What is contextual network security?
A contextual network security solution can provide zero-trust functionality while enabling BYOD policies. With an on-premises connector, you can have a single control channel to the company’s environment. Your employees can connect to business web apps without the need for a VPN, improving security and user experience.
What is workspace security?
Workspace security refers to the application of tools and solutions to protect sensitive data, networks, and access in digital workspaces without disrupting the user experience.
Why is secure internet important?
In addition, secure internet access simplifies IT by eliminating multiple password problems or resetting access privileges. Unifying the access through a centralized collaborative workspace provides a seamless user experience for employees.
Why is it important to have a security solution?
As more people use their own devices for work, there can be a mix of operating systems and mobile devices connecting to the same workspace. For this reason, it’s important to choose an endpoint security solution that can secure every endpoint and enable management from one console. Using a single console makes it easier to be proactive and prevent threats. When an IT security team doesn’t need to handle dozens of different security tools, they can act quickly to identify threats and sound alerts.
