How do I enable remote access to my Check Point network?
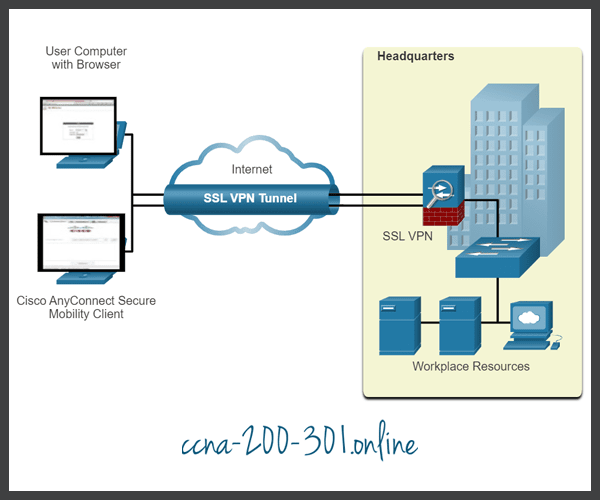
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
Is remote access a weak point in your IT security?
In today's business environment, it is clear that workers require remote access to sensitive information from a variety of locations and a variety of devices. Organizations must also make sure that their corporate network remains safe and that remote access does not become a weak point in their IT security. Types of Solutions
What is a secure remote access solution?
A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go. Each host typically has VPN client software loaded or uses a web-based client.
How does check point ensure privacy and integrity of sensitive information?
Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data. Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
How do I connect to Checkpoint VPN?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
What is SASE checkpoint?
Secure Access Service Edge (SASE) is an emerging WAN model coined by Gartner in The Future of Network Security is in the Cloud that delivers network and security capabilities including SD-WAN, ZTNA, FWaaS, secure web gateway and CASB as services to protect connected entities with a zero-trust security model.
Is checkpoint a VPN?
Remote Access VPN Products Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is mobile checkpoint VPN?
Check Point Mobile VPN for Android devices is an L3 VPN client. It supplies secure connectivity and access to corporate resources using the L3 IPSec/SSL VPN Tunnel. The application is available in the Google Play Store: https://play.google.com/store/apps/details? id=com.checkpoint.VPN&hl=en.
What is the difference between SASE and CASB?
SASE is a suite of solutions to address networking as a service with a suite of features and security as a service with a suite of solutions. CASB is part of the security as a service that covers the service broker for cloud access on data movement between cloud and on-prem.
What's the difference between SD-WAN and SASE?
SD-WAN is an overlay network that backhauls traffic to data centers, while SASE is a cloud platform that inspects data at various PoPs at the edge. As remote work remains a part of everyday life, architectures like SASE are better suited for remote access than SD-WAN.
How does remote access VPN Work?
The remote access VPN does this by creating a tunnel between an organization's network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
What is remote secure access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
What is Checkpoint Endpoint Connect?
Endpoint Connect is Check Point's new lightweight remote access client. Providing seamless, secure (IPSec) VPN connectivity to corporate resources, the client works transparently with VPN-1 and Connectra gateways.
How do I use checkpoint mobile VPN?
5:5410:30Check Point Remote Access VPN Setup and Config - YouTubeYouTubeStart of suggested clipEnd of suggested clipUp. We click trust. And continue then it's going to ask you what vpn client you're going to use theMoreUp. We click trust. And continue then it's going to ask you what vpn client you're going to use the default. One we're going to use a username and password. And then we click finish.
What is Check Point mobile Access?
Check Point Mobile Access is the safe and easy solution to securely connect to corporate applications over the Internet with your Smartphone, tablet or personal computer (PC). Mobile Access allows remote and mobile workers to simply and securely connect to email, calendar, contacts and corporate applications.
Who makes Checkpoint VPN?
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading provider of cyber security solutions to governments and corporate enterprises globally. Its solutions protect customers from 5th generation cyber-attacks with an industry leading catch rate of malware, ransomware and other types of attacks.
What is SASE in simple terms?
SASE is the convergence of wide area networking, or WAN, and network security services like CASB, FWaaS and Zero Trust, into a single, cloud-delivered service model.
What does SASE stand for?
Secure Access Service Edge (SASE) – defined by Gartner – is a security framework prescribing the conversions of security and network connectivity technologies into a single cloud-delivered platform to enable secure and fast cloud transformation.
Is SASE a VPN?
Is SASE a VPN? SASE creates a global private network for your company, replacing the legacy VPN. Unlike the traditional server-based VPN, SASE is offered as a cloud service. Thus, as with other SaaS solutions, you don't need to worry about the operation or maintenance of the underlying infrastructure.
What are three core capabilities of SASE?
These core capabilities include Cloud Access Secure Broker capabilities (CASB), zero trust network access and Firewall as a Service, including IPS capabilities. Being able to identify sensitive data and malware is also essential as well as encryption and decryption capabilities.
What is check point architecture?
Whether it’s employees working from home, contractors working on a limited project, or engineers accessing production environments, your users just want to work. Check Point’s agentless architecture gives users frictionless access to authorized assets, without the need for VPNs.
Is remote work the new normal?
Remote work has become the new normal. Enterprises#N#need a remote access platform based on Zero Trust Access principles. Access rights to any enterprise website, application, database or other corporate resource needs to be confirmed.
What is endpoint security VPN?
Endpoint Security VPN combines Remote Access VPN with Endpoint Security in a client that is installed on endpoint computers. It is recommended for managed endpoints that require a simple and transparent remote access experience together with Desktop Firewall rules. It includes:
What is a capsule connect?
Capsule Connect is a full Layer 3 tunnel app that gives users network access to all mobile applications. It supplies secure connectivity and access to all types of corporate resources. It was previously called Mobile VPN.
Is remote access a weak point?
Organizations must also make sure that their corporate network remains safe and that remote access does not become a weak point in their IT security.
What is checkpoint remote access?
Check Point remote access solutions use IPsec and SSL encryption protocols to create secure connections. All Check Point clients can work through NAT devices, hotspots, and proxies in situations with complex topologies, such as airports or hotels. These are the types of installations for remote access solutions:
What is an on demand client?
On demand client - Users connect through a web browser and a client is installed when necessary. The client supplies access to most types of corporate resources according to the access privileges of the user.
What is secure connectivity?
Secure Connectivity - Traffic is encrypted between the client and VPN Security Gateway. After users authenticate, they can access the corporate resources that are permitted to them in the access policy. All Check Point solutions supply this.
What is a firewall desktop?
Desktop Firewall - Protects endpoint computers at all times with a centrally managed security policy. This is important because remote clients are not in the protected network and traffic to clients is only inspected if you have a Desktop Firewall. Some Check Point solutions supply this
What is client based application?
Client-based - Client application installed on endpoint computers and devices. The client supplies access to most types of corporate resources according to the access privileges of the user.
Can you combine secure connectivity with additional features to protect the network or endpoint computers?
You can combine secure connectivity with additional features to protect the network or endpoint computers.
Is remote access a weak point?
Organizations must also make sure that their corporate network remains safe and that remote access does not become a weak point in their IT security.
