Cloud security and secure remote access The cloud is instrumental in managing a remote workforce, enabling users to access resources regardless of location. Cloud access can improve productivity, collaboration and employee satisfaction, but clouds also introduce security challenges that must be addressed.
Full Answer
How to access my Cloud remotely?
- Power up the My Cloud device
- Connect the My Cloud device to a router
- From your computer, access the My Cloud device’s web configuration dashboard: Windows: Open a web browser and type in http://devicename (e.g http://mycloudex2ultra ) or the My Cloud device’s IP address ...
- Setup your administrator username & password for local account access
How to setup WD my Cloud for remote access?
So here is that information:
- Access the My Cloud Dashboard. To open your My Cloud Dashboard: Windows: Open a web browser and type in //devicename/ (or device IP address) to the browser address bar. ...
- Click on the settings option on the top menu.
- Scroll the page to Cloud Access and verify it is set to off (or turn off if it is on).
How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
Can someone help me with remote access?
Windows Remote Assistance lets someone you trust take over your PC and fix a problem from wherever they are. Before you can use it, you'll need to enable access. In the search box on the taskbar, type remote assistance, and then select Allow Remote Assistance invitations to be sent from this computer from the list of results.
What is secure remote access?
How to secure your cloud?
What is cloud app security?
Why is cloud app security important?
Why is it important to have cloud apps?
Why is it important to secure your business?
Why is encryption important for cloud?
See 2 more
About this website

How do I create a secure remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What is a secure remote access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
What is ITarian remote access?
ITarian Remote Access and Control empowers technicians and administrators to manage servers, desktops, applications and mobile devices remotely so they can solve problems more efficiently. They can review performance data and roll out patches, updates and service configurations to address issues remotely.
Is cloud a remote access?
Both remote desktop and cloud computing allow users to access data and information remotely – without having to install applications on their devices or systems.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
Why is secure remote access important?
A secure remote access system protects your employees from web-based threats such as phishing attacks, ransomware and malware while they're logged in to your company's network. These cyber incidents can lead to unauthorized access and use of both the company's business data and the employee's personal data.
What are the benefits and disadvantages of using remote administration applications?
Advantages of Remote Access1) Flexible Access. ... 2) Flexible Set-Up and Costs. ... 3) Full Control on Authorization and Access. ... 4) Centralized Storage and Backups. ... 5) Shared Resources; Greater Efficiency and Collaboration. ... 1) Security Issues. ... 2) Version Problems and Data Liabilities. ... 3) Hardware Issues Still Need On-Site Work.More items...•
How remote access can help you and what its limitations?
Features of Remote AccessSave you from extra expenditure of purchasing USB drive.No copying / Pasting on CD or floppy to carry the data with you.Accessibility to your computer like, you are sitting in front of it at home.Managing office work even if you are not in office.More items...
What is remote control management?
Definition of Remote Management Remote Management is managing a computer or a network from a remote location. It involves installing software and managing all activities on the systems/network, workstations, servers, or endpoints of a client, from a remote location.
Is the cloud a remote server?
A cloud server is a compute server that has been virtualized, making its resources accessible to users remotely over a network.
What is the difference between a remote server and a cloud?
Web Server primarily consists of space which has been leased or purchased by the owner, whereas with cloud computing, you're using applications (like email, word processing, spreadsheet, photo editing) that are located on a remote server somewhere, but using them as if they were programs on your computer.
What is remote cloud?
Remote storage, alternatively referred to as cloud storage, is a description of storage accessed over a network (remotely). For example, a networked computer may utilize remote storage to hold video files that take up a lot of disk space. Remote storage may also be used as a place for offsite backup.
Should I give remote access to my computer?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
Is remote access security secure?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
Which is the secure standard function for remote access?
MFA is imperative to authenticate users for secure remote access. Many regulations and compliance standards require MFA for privileged remote access.
Why do organizations need remote users?
Organizations need to provide remote users with more than just a secure connection back to the core network or datacenter resources they are used to be remotely connecting to. An increasing number of applications are also being hosted in the cloud, and rather than backhauling those applications through the core network, ...
What is Fortinet security fabric?
The Fortinet Security Fabric for AWS helps organizations maintain consistent security protection from on-premises to the cloud.
Secure Remote Access for Employees and Vendors
Traditional remote access methods, such as RDP, Virtual Private Networks, and legacy remote desktop tools lack granular access management controls. These processes enable easy exploits via stolen credentials and session hijacking. Extending remote access to your vendors makes matters even worse.
Privileged Remote Access: Use Cases
BeyondTrust Privileged Remote Access controls, manages, and audits remote privileged access to critical IT systems by authorized employees and third-party vendors. No VPN required.
Remote Support: Use Cases
BeyondTrust Remote Support allows help desk teams to securely access and fix any remote device on any platform, located anywhere in the world. All with the same solution.
Secure Remote Access and Remote Support Features
BeyondTrust Remote Support and Privileged Remote Access solutions work hand-in-hand to secure remote access points within the enterprise, including employees, vendors, third-parties, and more.
What is Zscaler private access?
The Zscaler Private Access (ZPA) service provides secure remote access to internal applications in the cloud without placing users on the corporate network. The cloud service requires no complex remote access VPN gateway appliances, and uses cloud-hosted policies to authenticate access and route user traffic to the closest application location to them. ZPA is a true software-defined solution that can work in conjunction with direct access technology. It directly connects customer data centers with cloud service provider data centers.
Can remote users be on the network?
Remote users are never placed on the network, but instead are given access to apps based on policy.
What is secure remote access?
Secure remote access describes the ability to securely access networks, devices, and applications from a “remote” location, which means “off the network.”
What is Zscaler private access?
Looking more closely, Zscaler Private Access (ZPA) service provides secure remote access to internal applications in the cloud without placing users on the corporate network. The cloud service requires no complex remote access VPN gateway appliances and uses cloud-hosted policies to authenticate access and route user traffic to the closest application location to them. ZPA is a true software-defined solution that can work in conjunction with direct access technology. It directly connects customer data centers with cloud service provider data centers.
Why are IPs never exposed to the internet?
IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find. Apps segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
How does ZTNA improve security?
ZTNA improves your security posture by drastically reducing your attack surface. Application access is decoupled from network access. ZTNA moves away from network-centric security and instead focuses on securing the connection between user and application.
What is ZTNA security?
ZTNA takes a user-to-application approach rather than a network-centric approach to security . The network becomes deemphasized, and the internet becomes the new corporate network, leveraging end-to-end encrypted TLS micro-tunnels instead of MPLS.
Can a VPN attack be zero trust?
They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data. In contrast, the zero trust approach treats all traffic, including traffic already inside the perimeter, as hostile.
Can IoT services be hosted on premises?
IoT services that are hosted on-premises can benefit from optimized speeds. Performance speeds can increase if local users do not have to connect out to the internet to access apps that are hosted on-premises. The other option is ZTNA as a service, such as Zscaler Private Access.
Why use Microsoft Cloud App Security?
Use Microsoft Cloud App Security to monitor session risk, gain visibility into usage, and enforce app and file usage policies in real time. Maintain productivity by educating and guiding workers to access the cloud resources they need through more secure methods.
What is Azure AD conditional access?
Azure AD Conditional Access is the Microsoft identity security policy hub. Create Conditional Access policies according to user, device, application, and risk. Enforce controls that allow a device trying to access a specific resource only if it’s compliant.
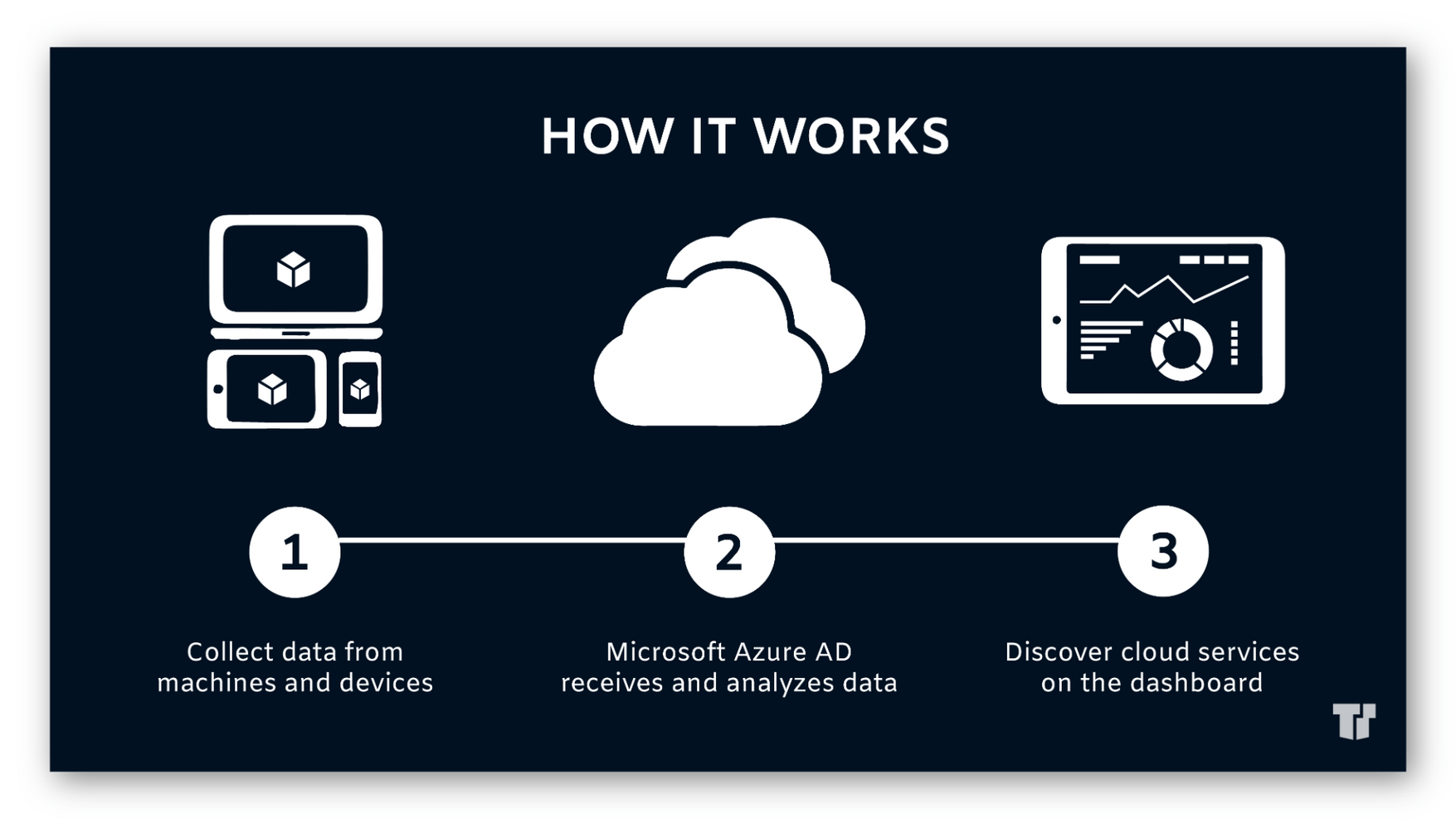
What is Azure AD?
Establishing identity management in the cloud is your first step. Microsoft Azure Active Directory (Azure AD) lets you manage authentication across devices, cloud apps, and on-premises apps. With single sign-on, your employees can access resources from any device while working remotely.
What is MFA in remote work?
Multi-factor authentication (MFA) is the single best thing you can do to improve security for remote work. If you’re not able to distribute hardware security devices, use biometrics or mobile device authentication apps like Microsoft Authenticator as the second factor. Enable MFA and create Conditional Access policies.
Is remote work important?
Now, more than ever, remote work capabilities are vital . Ensure your workforce is as efficient working from home as they were at the office. In this webinar you’ll learn how Microsoft Azure Active Directory helps improve efficiency while maintaining the right balance of productivity and security for remote workers.
Author: Haris Khan
Remote work is the new normal for IT teams around the globe, and there is no surprise as to why remote work is becoming so increasingly popular for organizations. The modern employee workforce is no longer restricted to one physical location.
What is secure remote access?
Secure remote access refers to the technology used for securely accessing a system or application remotely. Cybercriminals and malicious actors are consistently looking out for vulnerabilities and loopholes in remote work infrastructures to exploit and plan cyber attacks.
Which technologies are used for remote work access?
Secure remote access can be effectively implemented by utilizing a collection of highly innovative, secure, and flexible technologies while accessing a system or application from a remote location A few prominent examples of such technologies are listed below:
10 Best Practices for Secure Remote Work Access
Some of the best practices that you can adopt to improvise remote access security in your organization are described below:
Why cloud desktops are an optimal choice for secure remote access?
Cloud desktop solutions offer greater flexibility and ease of access as all of your files, applications and desktop reside on the cloud. Cloud desktops are one of the most resilient and secure forms of remote access.
All-In-One Secure Remote Access with V2 Cloud
As the organizational trend keeps transitioning to remote work, it’s crucial to comprehend the numerous cybersecurity risks and threats that are associated with remote access security. Remote work has become an increasingly viable option with tons of advantages.
What is secure remote access?
Secure remote access represents any security policy, program, or strategy that safeguards a specific application or network from unauthorized access. Rather than utilizing one cybersecurity strategy, secure remote access incorporates multiple security solutions to ensure your business’s confidential information is protected, no matter where your network is being utilized.
How to secure your cloud?
This includes identifying which applications you are currently using, as well those you plan to integrate into your network in the future. Once identified, it’s important to assess these services for any potential cybersecurity risks or vulnerabilities so you can get started implementing the right security measures. Some of the most common cloud app security strategies include:
What is cloud app security?
Cloud app security refers to the security measures taken to protect corporate assets and data stored within a cloud-based application. Much like establishing secure remote access, cloud app security involves implementing multiple independent strategies to mitigate vulnerabilities within your cloud-based apps.
Why is cloud app security important?
Ensuring your cloud apps are utilizing built-in security options will help mitigate data loss and protect your organization from remote threats. It’s also important to select cloud services that align with your business’s unique security needs, especially if you have a remote work force.
Why is it important to have cloud apps?
Ensuring your cloud apps are utilizing built-in security options will help mitigate data loss and protect your organization from remote threats. It’s also important to select cloud services that align with your business’s unique security needs, especially if you have a remote workforce.
Why is it important to secure your business?
As an organization with a remote workforce, protecting your business’s sensitive data online is crucial. Establishing secure remote access is an effective way to control which users and devices have access to your corporate network while boosting cybersecurity efforts on employee endpoints. If your business utilizes cloud-based applications, harnessing built-in security settings and promoting cloud app security best practices can help protect your organization from malicious threats, data loss, and unauthorized users.
Why is encryption important for cloud?
Encrypting sensitive information and securing all network connections prevents data loss or leaks from your cloud apps. This ensures any information lost in a security breach is undecipherable and keeps suspicious or malicious traffic out of your corporate network.