Connect to the remote desktop
- Run the following command to create a connection from the device to Cloudflare. ...
- Open your RDP client and configure the client to point to localhost:3389. Do not input the hostname.
- When the client launches, cloudflared will launch a browser window and prompt the user to authenticate with your SSO provider.
Full Answer
How does Cloudflare access secure RDP?
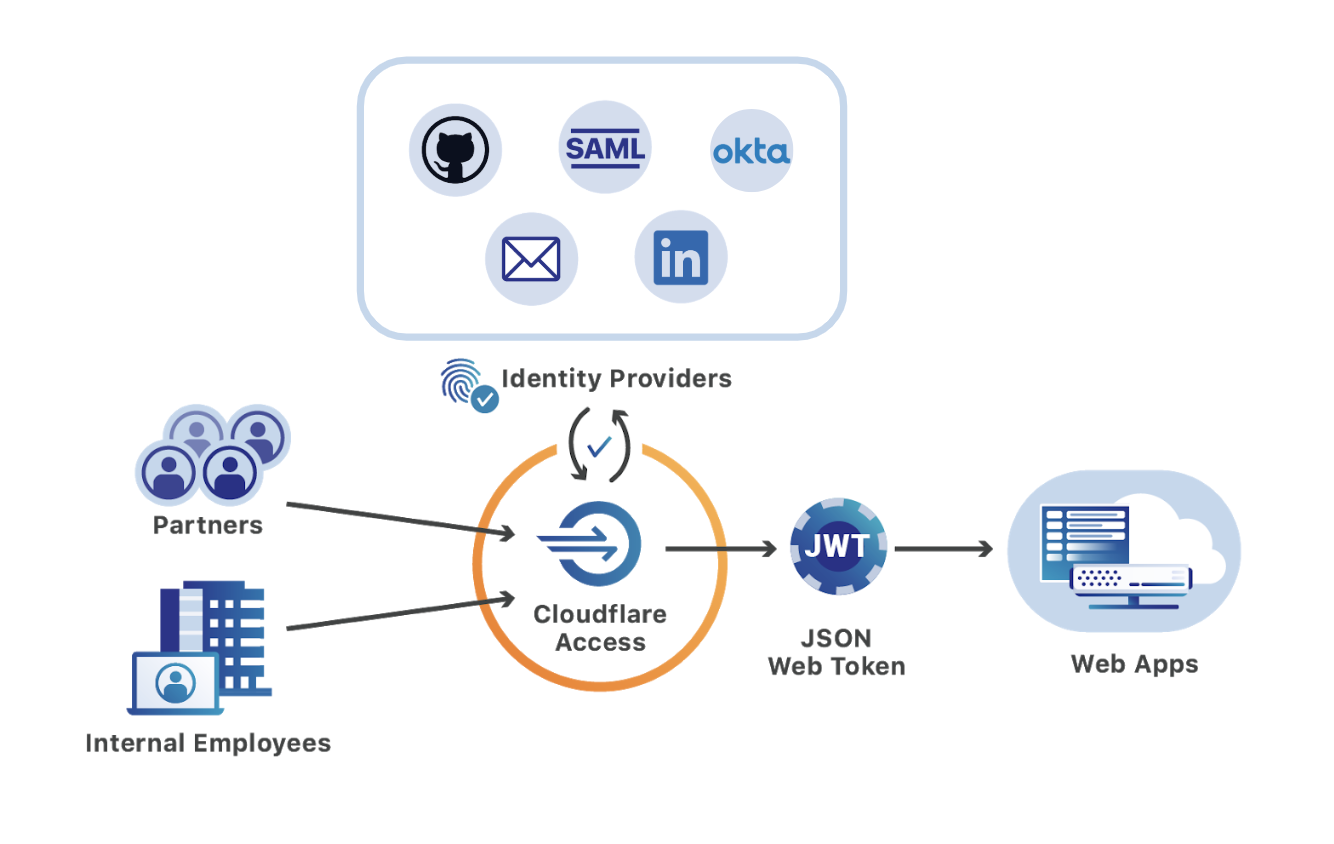
Cloudflare Access secures RDP ports and connections by relying on Argo Tunnel to lock down any attempts to reach the desktop. Argo Tunnel connects your machine to the Cloudflare network without the need for custom firewall or ACL configurations.
Which companies use Cloudflare for remote development?
Replicated is an infrastructure software company that uses Cloudflare Access to embrace remote development work. Their team of developers is spread out across the continental US. Before they found Cloudflare Access, IT provisioned new MacBook pros to each member of their development team.
How do I lock down remote desktops on the Cloudflare network?
Once on the Cloudflare network, Access enforces the rules you need to lock down remote desktops. To begin, configure Argo Tunnel on the machine you need to secure by using cloudflared. cloudflared serves as an agent on the machine to open a secure connection from the desktop to the Cloudflare network.
What is Cloudflare zero trust network access?
Learn how Cloudflare's Zero Trust solution works together to provide secure, optimized connectivity for remote workforces. Zero Trust Network Access can empower your technical teams to work faster, while strengthening the security of your build environment.
See more
What is Cloudflare access?
Cloudflare Access lets end users authenticate with their single sign-on (SSO) provider and connect to shared files over RDP without being on a VPN. Other Protocols. You can use Access to add authentication to Secure Messaging Block (SMB) fileshares or applications that use arbitrary TCP.
Does Cloudflare replace VPN?
Blog: Cloudflare's own journey replacing its VPN Cloudflare first built Access because our engineers were fed up with their VPN experience. Read about our journey to replace our own VPN.
Is Cloudflare for teams a VPN?
Cloudflare for Teams is built around two complementary products: Access and Gateway. Cloudflare Access™ is the modern VPN — a way to ensure your team members get fast access to the resources they need to do their job while keeping threats out.
How secure is Cloudflare access?
Cloudflare Zero Trust As requests are routed and accelerated through Cloudflare's edge, they are evaluated against Zero Trust rules incorporating signals from your identity providers, devices, and other context.
Is Cloudflare better than VPN?
A VPN's goal is to prevent anyone from seeing your data, while Cloudflare seeks to provide improved, but not maximalist, privacy. VPNs also provide more control over where your data goes, and they sometimes include additional privacy tools, like multihop connections.
Is Cloudflare VPN safe?
Cloudflare's website network is secure as it is a security company with roots in DDOS protection services and improving online privacy. So, if you want to have a secure connection with decent speeds, then WARP is a great VPN to use.
Which is better Cloudflare or Google DNS?
Speed and Performance In terms of speed, Google Public DNS outperforms Cloudflare. This is because of several things, including global coverage, more servers, and a shared cache. Most of the time, DNS lookups create a bottleneck, slowing down your browsing.
Is Cloudflare warp VPN?
From a technical perspective, WARP is a VPN. But it is designed for a very different audience than a traditional VPN. WARP is not designed to allow you to access geo-restricted content when you're traveling. It will not hide your IP address from the websites you visit.
Which free VPN is best?
Best free VPN for mobile You may pick the classic Atlas VPN and ProtonVPN as they're the best free VPNs for Android. Though, there are some other options. For example, Windscribe and Hide.me are also worth a shot.
How do I use VPN with Cloudflare?
1:443:06How to use Cloudflare 1.1.1.1 DNS and WARP VPN on Windows 10YouTubeStart of suggested clipEnd of suggested clipYou can go ahead and this icon click that and you can change it with warp. So this setting is goingMoreYou can go ahead and this icon click that and you can change it with warp. So this setting is going to use the 1.1. Dns at the same time it's going to take you to a vpn.
Is Cloudflare a load balancer?
Cloudflare Load Balancing is a DNS-based load balancing solution that actively monitors server health via HTTP/HTTPS requests. Based on the results of these health checks, Cloudflare steers traffic toward healthy origin servers and away from unhealthy servers.
Is Cloudflare Zero Trust safe?
Zero Trust security means that no one is trusted by default from inside or outside the network, and verification is required from everyone trying to gain access to resources on the network. This added layer of security has been shown to prevent data breaches.
What is the difference between 1.1 1.1 and VPN?
1.1. 1.1, as you say, is a DNS server, not a VPN. It is not like a VPN because DNS only converts domain names to an IP address, a VPN connects you to a remote network, and a VPN service will be a full tunnel VPN which routes all of your internet traffic through the VPN.
How do I use VPN with Cloudflare?
1:443:06How to use Cloudflare 1.1.1.1 DNS and WARP VPN on Windows 10YouTubeStart of suggested clipEnd of suggested clipYou can go ahead and this icon click that and you can change it with warp. So this setting is goingMoreYou can go ahead and this icon click that and you can change it with warp. So this setting is going to use the 1.1. Dns at the same time it's going to take you to a vpn.
Which is better Cloudflare or Google DNS?
Speed and Performance In terms of speed, Google Public DNS outperforms Cloudflare. This is because of several things, including global coverage, more servers, and a shared cache. Most of the time, DNS lookups create a bottleneck, slowing down your browsing.
Which free VPN is best?
Best free VPN for mobile You may pick the classic Atlas VPN and ProtonVPN as they're the best free VPNs for Android. Though, there are some other options. For example, Windscribe and Hide.me are also worth a shot.
What's slowing down your workforce?
The larger and more distributed your workforce becomes, the harder it is to secure remote users, devices, and data. Legacy security tools, like hardware firewalls and VPNs, are not built to handle hybrid infrastructure, remote teams, or a constantly-evolving threat landscape.
Expand your security perimeter to fit your workforce
Hardware limitations shouldn’t dictate the strength of your security posture. As your remote workforce expands beyond on-premise offices and devices, you need security tools that can scale alongside it.
Swap slow VPNs for a global edge network
Modern enterprises require solutions capable of securing user access to on-premise, cloud-based, and SaaS applications from any location. Eliminate the headache of maintaining slow, outdated VPN infrastructure by authenticating and securing employee tools using a global edge network — accessible from wherever your users are located.
Protect all applications with Zero Trust access policies
The Zero Trust model requires user identity and multiple contextual factors to authorize access, making it difficult for attackers to impersonate employees and gain access to internal resources.
Demo: Secure remote workforces with Cloudflare Zero Trust
In this four minute demo, see how easy it is for administrators to securely connect remote workers to applications with Zero Trust rules for application access and Internet browsing. You'll see the administrator experience of policy administration, and what end users experience when connecting through Cloudflare.
7 Ways to Work From Anywhere
As your business decides where employees will work in the future, your security controls must meet them where they are. This ebook shares 7 best practices that effective organizations can use to protect their global workforce without sacrificing productivity.
Why does RDP matter?
RDP is one of the most popular protocols used by employees to access their office computers from remote devices. It is installed by default on Windows, and is supported on *nix and MacOS operating systems. Many companies rely on RDP to allow their employees to work from home.
Where does Cloudflare Access fit?
Cloudflare Access adds stronger authentication to RDP sessions by first locking down access to the remote machine via Argo Tunnel, then enforcing identity-based policies to determine who can gain access.
How does it work?
On the origin side, an admin will configure a single cloudflared instance to run in bastion mode. That bastion will reach out to the two closest Cloudflare edge data centers and create a long-lived HTTP2 session. Once set up, cloudflared will wait for incoming connections from clients to specify which final origin to connect to.
What is a replicated team?
Replicated is an infrastructure software company that uses Cloudflare Access to embrace remote development work.
Is it hard to work remotely?
Working remotely can be difficult for users doing their job on browser-based applications. It becomes much more difficult for engineers and developers who need to do their work over RDP or SSH.
What are some examples of security policies for remote access?
Virtual private network (VPN) usage, anti-malware installation on employee devices, and multi-factor authentication (MFA) are all examples of things that can be included in a security policy for remote access.
Why is remote access important for a business?
When some or all of a business's employees and contractors work from home, internal data protection teams can have less control and visibility of data security. Strong remote access security policies can help safeguard the personal and confidential data that is protected by the GDPR.
Why do remote employees need to be protected?
Remote employee endpoint devices (such as laptops, desktop computers, and smartphones) must be protected from cyber attacks, because a malware infection could result in a data breach . Devices should have anti-malware software installed at a minimum. A secure web gateway can also help protect employees as they browse the Internet.
What is the key technology for protecting data?
Access control and encryption are the key technologies for protecting data. Remote employees, like all employees, must have good reason for having access to personal data, and their access to that data has to be tracked and managed. Identity and access management (IAM) technologies help prevent unauthorized persons from viewing and altering data.
Does Cloudflare support RDP?
Cloudflare Access now supports RDP. Last fall, the United States FBI warned organizations of an increase in attacks that exploit vulnerabilities in the Remote Desktop Protocol (RDP). Attackers stole sensitive data and compromised networks by taking advantage of desktops left unprotected.
Can Cloudflare access RDP?
Starting today, you can use Cloudflare Access to connect over RDP without sacrificing security or performance. Access enables your team to lock down remote desktops like you do physical ones while using your SSO credentials to authenticate each connection request.
Block threats on the Internet, known and unknown
Block access to known bad, risky, or unwanted destinations at the DNS or HTTP level with our massive corpus of threat intelligence.
Control the flow of data in and out of your organization
Gain the benefits of data loss prevention (DLP) without the complexity with file type controls that can stop users from uploading files like documents and spreadsheets to unsanctioned apps and sites like social media.
SaaS application control
Cloudflare’s logging capabilities allow you to discover unsanctioned use of SaaS applications, and easily build a policy to block access to such applications.
Near real-time monitoring of traffic across your organization
Cloudflare’s logs provide visibility into your Internet and web traffic — across all users, devices, and locations.
Legacy approach
Teams need to connect to the Internet to do their work. Legacy approaches attempted to force that traffic, which is mostly encrypted, through appliances that could not scale with complex and costly implementations to mitigate hardware failure or software upgrade downtime.
Cloudflare Zero Trust
Cloudflare replaces always outdated boxes with one global network. And in one platform, we unite once-distinct point products including Secure Web Gateway (SWG), DNS Security, and Remote Browser Isolation (RBI) with Cloud Access Security Broker (CASB) and Data Loss Prevention (DLP) use cases.
Cloudflare Gateway and SASE
A secure web gateway is an important component of the Secure Access Service Edge (SASE) network security model. Learn how Cloudflare Gateway integrates seamlessly with the other security and connectivity tools in Cloudflare’s SASE solution, Cloudflare One.
Users have left the building. So what is your perimeter protecting?
Employees and third parties connect to corporate resources from everywhere.
Zero Trust Network Access
Zero Trust Network Access (ZTNA) technologies create secure boundaries around applications. When resources are protected with ZTNA, users are only allowed to access resources after verifying the identity, context, and policy adherence of each specific request.
Protect internal assets without a VPN
ZTNA replaces VPN connections with universal policies that grant access based on a user’s identity and context.
Accelerate DevOps workflows
Engineers and related functions often need SSH access to your infrastructure to keep your business moving - and they don’t like to be slowed down. ZTNAs allow privileged technical users to access your critical infrastructure remotely - without experiencing tradeoffs.
Give every user seamless authentication - even contractors and partners
ZTNA saves room in your corporate directory by simultaneously integrating with multiple identity providers. External users can authenticate with a broad variety of corporate or personal accounts and still benefit from the same ease-of-use available to internal employees.
ZTNA Resources
Yes, you really can replace your VPN with Zero Trust Network Access. Download this technical whitepaper to compare alternative remote access approaches and find the best option for your organization.
Start Now
Secure access to your corporate applications without a VPN. Getting started with Access takes minutes. With our free plan, your first 50 users are free.

Why Does RDP Matter?
Where Does Cloudflare Access Fit?
- Cloudflare Access adds stronger authentication to RDP sessions by first locking down access to the remote machine via Argo Tunnel, then enforcing identity-based policies to determine who can gain access. Whether your organization uses Okta, Azure AD, or another provider, your users will be prompted to authenticate with those credentials before star...
How Does It Work?
- On the origin side, an admin will configure a single cloudflared instance to run in bastion mode. That bastion will reach out to the two closest Cloudflare edge data centers and create a long-lived HTTP2 session. Once set up, cloudflared will wait for incoming connections from clients to specify which final origin to connect to. This is unlike conventional cloudflaredtunnel behavior, w…
What’s Next?
- While today we are proxying just RDP traffic in bastion mode, we will eventually be expanding this functionality to protocols like FTP, SSH, and generic TCP. In the effort to make protecting internal resources easier than ever before, cloudflared can now also be conveniently found in the Cloudflare package repo, in tagged releases on the cloudflared Github repo, and in the cloudflare…