
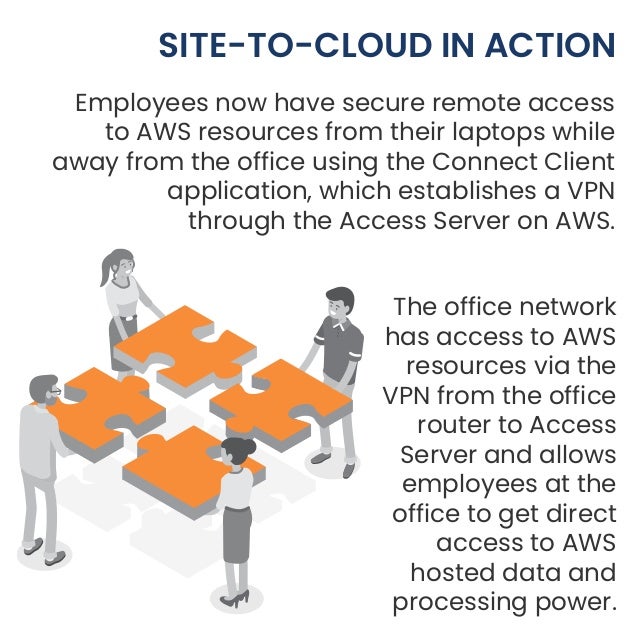
How to extend your network to Cloudflare over secure links?
Extend your network to Cloudflare over secure, high-performance links Mobile Device Management Partnerships Secure endpoints for your remote workforce by deploying Cloudflare’s client with MDM vendors of your choice Network On-ramp Partnerships Connect to Cloudflare using your existing WAN or SD-WAN infrastructure Peering Portal Peering Portal
How does Cloudflare’s remote browser work?
Not your average remote browser. Legacy remote browserssend a slow and clunky version of a web page to the user. Cloudflare draws an exact replica of the page on the user’s device, and then delivers that replica so quickly it feels like a regular browser.
What is Cloudflare zero trust network access?
Learn how Cloudflare's Zero Trust solution works together to provide secure, optimized connectivity for remote workforces. Zero Trust Network Access can empower your technical teams to work faster, while strengthening the security of your build environment.
How do I connect to machines over RDP using Cloudflare for teams?
You can connect to machines over RDP using Cloudflare's Zero Trust platform. First, navigate to the Cloudflare for Teams dashboard to create a new application. Select the Applications page from the sidebar. Click Add application. Choose Self-hosted on the next page. Input a subdomain where your application will be availble to users.
See more
How do I optimize Cloudflare?
How can developers get their websites to load faster? ... Test website performance. ... Use a CDN (content delivery network) ... Optimize images. ... Minify CSS and JavaScript files. ... Reduce the number of HTTP requests if possible. ... Use browser HTTP caching. ... Minimize the inclusion of external scripts.More items...
Does Cloudflare allow remote work?
Cloudflare Zero Trust enables seamless, identity- and context- based application access and software-defined security, allowing you to secure your remote teams, devices, and data without sacrificing performance or user experience.
How does Cloudflare optimize web content?
We will go over how Cloudflare optimizes your content to ensure your users have a superior customer experience. Cloudflare does this by supporting the latest and fastest web protocols, optimizing images and video for fastest delivery, and using modern compression techniques to reduce file size.
Is Cloudflare Zero Trust safe?
For instance, Cloudflare One is a SASE platform that combines networking services with a built-in Zero Trust approach to user and device access. With Cloudflare One, customers automatically implement Zero Trust protection around all their assets and data.
How many employees work at CloudFlare?
CloudflareTypeenterprise, technology company, public company, online serviceTotal equityUS$811.4 million (2021)Number of employees2,440 (2021)SubsidiariesArea 1 SecurityWebsitewww.cloudflare.com12 more rows
Why do you want to work for CloudFlare?
The two most important reasons to think of CloudFlare are... because of who your colleagues would be and who our customers are (and who their customers are). It's the people, inside and outside the company, that make CloudFlare a fascinating and stimulating place to work.
Does Cloudflare speed up website?
CloudFlare speeds up your website and protects it from security threats. According to CloudFlare, on average a website using CloudFlare loads twice as fast, uses 60% less bandwidth, has 65% fewer requests and is more secure.
Is Cloudflare good for SEO?
Does using Cloudflare hurt my SEO? The short answer is, no. When asked whether or not Cloudflare can damage search rankings, John Mueller from Google stated CDNs can work great for both users and search engines when properly configured.
Does Cloudflare increase site speed?
So, if you're looking to boost your websites performance or your customer's website performance, and you're looking for one solution to handle it all — CloudFlare is your best option. It increases your speed, keeps your site secure, saves on bandwidth and infrastructure costs and more.
Is Cloudflare access free?
Free Options Secure access to Internet, self-hosted and SaaS applications for up to 50 users for free. Deploy serverless code, up to 100k requests per day, across all Cloudflare data centers.
Is Cloudflare for teams a VPN?
Cloudflare for Teams is built around two complementary products: Access and Gateway. Cloudflare Access™ is the modern VPN — a way to ensure your team members get fast access to the resources they need to do their job while keeping threats out.
What is the difference between zscaler and Cloudflare?
Cloudflare sells for more than 100 times sales, compared with a price-to-sales (P/S) ratio of around 60 for Zscaler. Nonetheless, Zscaler sells for substantially more than Checkpoint Software or Palo Alto Networks, which support sales multiples of eight and 12, respectively.
Does Cloudflare optimize images?
Cloudflare Polish is a one-click image optimization product that automatically optimizes images in your site.
What will Cloudflare compress?
In addition to Cloudflare's CDN caching static content and auto-minification of CSS, JS & HTML to speed up your site, Cloudflare also provides gzip and brotli compression to help site owners.
How do I optimize my website speed?
Best Practices to Speed Up Your WebsiteReduce the Number of HTTP Requests. ... Switch to HTTP/2. ... Optimize Image Sizes. ... Use a Content Delivery Network (CDN) ... Write Mobile-First Code. ... Minimize Time to First Byte. ... Choose the Right Hosting Service Plan. ... Implement Gzip Compression.More items...•
Why is my site slower with Cloudflare enabled?
Slowness for only the first request of a resource indicates your server took too long to generate a response. The first time a resource is requested, it is likely uncached at Cloudflare and the request has to go to your origin server. Investigate slowness with your hosting provider.
What's slowing down your workforce?
The larger and more distributed your workforce becomes, the harder it is to secure remote users, devices, and data. Legacy security tools, like hardware firewalls and VPNs, are not built to handle hybrid infrastructure, remote teams, or a constantly-evolving threat landscape.
Expand your security perimeter to fit your workforce
Hardware limitations shouldn’t dictate the strength of your security posture. As your remote workforce expands beyond on-premise offices and devices, you need security tools that can scale alongside it.
Swap slow VPNs for a global edge network
Modern enterprises require solutions capable of securing user access to on-premise, cloud-based, and SaaS applications from any location. Eliminate the headache of maintaining slow, outdated VPN infrastructure by authenticating and securing employee tools using a global edge network — accessible from wherever your users are located.
Protect all applications with Zero Trust access policies
The Zero Trust model requires user identity and multiple contextual factors to authorize access, making it difficult for attackers to impersonate employees and gain access to internal resources.
Demo: Secure remote workforces with Cloudflare Zero Trust
In this four minute demo, see how easy it is for administrators to securely connect remote workers to applications with Zero Trust rules for application access and Internet browsing. You'll see the administrator experience of policy administration, and what end users experience when connecting through Cloudflare.
7 Ways to Work From Anywhere
As your business decides where employees will work in the future, your security controls must meet them where they are. This ebook shares 7 best practices that effective organizations can use to protect their global workforce without sacrificing productivity.
Where does Cloudflare Access fit?
Cloudflare Access adds stronger authentication to RDP sessions by first locking down access to the remote machine via Argo Tunnel, then enforcing identity-based policies to determine who can gain access. Whether your organization uses Okta, Azure AD, or another provider, your users will be prompted to authenticate with those credentials before starting any RDP sessions.
How does Cloudflare bastion work?
That bastion will reach out to the two closest Cloudflare edge data centers and create a long-lived HTTP2 session. Once set up, cloudflared will wait for incoming connections from clients to specify which final origin to connect to. This is unlike conventional cloudflared tunnel behavior, which immediately creates a single outgoing connection to a pre-configured origin.
Why does RDP matter?
RDP is one of the most popular protocols used by employees to access their office computers from remote devices. It is installed by default on Windows, and is supported on *nix and MacOS operating systems. Many companies rely on RDP to allow their employees to work from home.
Why are RDP servers exposed to the internet?
Many RDP servers are inadvertently exposed directly to the open Internet due to incomplete enforcement of firewall rules or unpatched vulnerabilities. Quickly exposing desktop fleets in a rush to help employees work from home might result in more security oversights.
Does Cloudflare need tunneling?
Setting Tunnel up initially required installing the Cloudflare daemon, cloudflared, on each RDP server. However, as the adoption of remote work increased we learned that installing and provisioning a new daemon on every server in a network was a tall order for customers managing large fleets of servers.
Is RDP password protected?
Second, most RDP servers are not protected with corporate SSO tools. When users connect over RDP, they often enter a local password to login to the target machine. However, organizations don't always manage these credentials properly. Instead, users set and save passwords on an ad-hoc basis outside of the single sign-on credentials used for other services. That oversight leads to outdated, reused, and ultimately weak passwords that are potentially securing Internet-exposed resources.
Can you RDP to a resource not yet protected?
Previously, if a user wanted to RDP to a resource not yet protected with a dedicated cloudflared tunnel, they would have to reach out to a member of their infrastructure team and request that it be provisioned manually. For larger enterprises managing thousands of network assets, this could pose a significant burden, involving new configuration management manifests and implementing tunnel health monitoring.
What is Cloudflare certificate optimization?
Cloudflare’s certificate optimization logic examines the browser’s capabilities, and then serves the most modern certificate it can support.
Can everyone benefit from Cloudflare?
Everyone’s Internet application can benefit from using Cloudflare.
Does Cloudflare have a limit?
Our mission is to build a better Internet. We believe every website should have free access to foundational security and performance. Cloudflare's Free plan has no limit on the amount of bandwidth your visitors use or websites you add.
Here's how it Works
Getting started with Automatic Platform Optimization for WordPress is Easy.
Detailed Explanation of How This Works
Automatic Platform Optimization puts your website into Cloudflare’s network that is within 10 milliseconds of 99% of the Internet-connected population in the developed world, all without having to change your existing hosting provider.
Powered by the Cloudflare's Edge
Automatic Platform Optimization serves both static and dynamic content from Cloudflare edge reducing costly round trips to the origin and server processing time. All the communication occurs between the user’s device and Cloudflare edge and
Professional, Business, and Enterprise Plans
Included, at no additional cost, in our Professional, Business, and Enterprise plans.
Users have left the building. So what is your perimeter protecting?
Employees and third parties connect to corporate resources from everywhere.
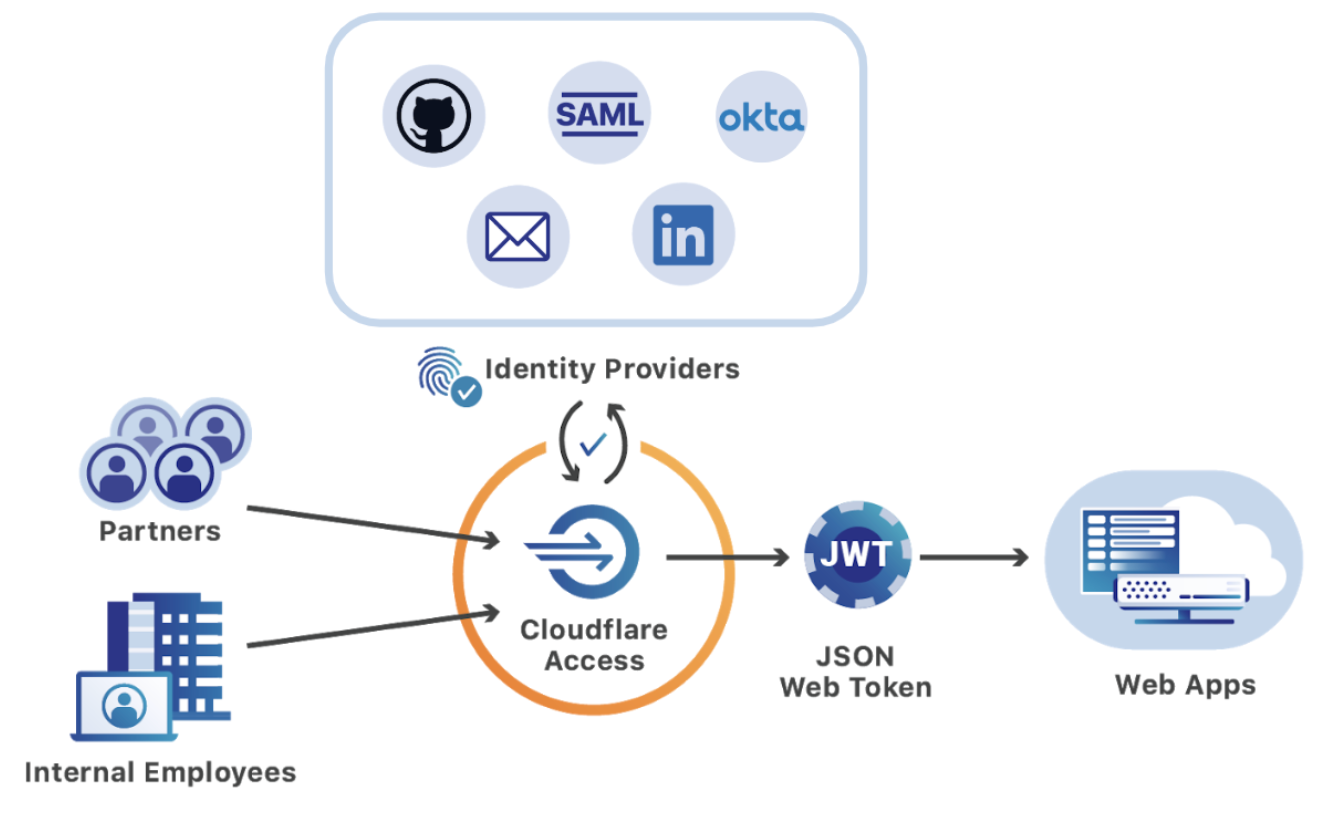
Zero Trust Network Access
Zero Trust Network Access (ZTNA) technologies create secure boundaries around applications. When resources are protected with ZTNA, users are only allowed to access resources after verifying the identity, context, and policy adherence of each specific request.
Protect internal assets without a VPN
ZTNA replaces VPN connections with universal policies that grant access based on a user’s identity and context.
Accelerate DevOps workflows
Engineers and related functions often need SSH access to your infrastructure to keep your business moving - and they don’t like to be slowed down. ZTNAs allow privileged technical users to access your critical infrastructure remotely - without experiencing tradeoffs.
Give every user seamless authentication - even contractors and partners
ZTNA saves room in your corporate directory by simultaneously integrating with multiple identity providers. External users can authenticate with a broad variety of corporate or personal accounts and still benefit from the same ease-of-use available to internal employees.
ZTNA Resources
Yes, you really can replace your VPN with Zero Trust Network Access. Download this technical whitepaper to compare alternative remote access approaches and find the best option for your organization.
Start Now
Secure access to your corporate applications without a VPN. Getting started with Access takes minutes. With our free plan, your first 50 users are free.
What happens when a cloudflared client launches?
When the client launches, cloudflared will launch a browser window and prompt the user to authenticate with your SSO provider.
How to create a tunnel in Cloudflare?
Navigate to dash.cloudflare.com and choose the hostname where you want to create a Tunnel. This should match the hostname of the Access policy. Click + Add record.
What is Cloudflare Tunnel?
Cloudflare Tunnel creates a secure, outbound-only connection between this machine and Cloudflare's network. With an outbound-only model, you can prevent any direct access to this machine and lock down any externally exposed points of ingress. And with that, no open firewall ports.
What port is used to connect to Cloudflare?
Run the following command to create a connection from the device to Cloudflare. Any available port can be specified, but in this example we will use 3389 as it is the default port for RDP connections.
Where is YAML file cloudflared?
Create a YAML file that cloudflared can reach. By default cloudflared will look for the file in the C:Users%USERNAME%.cloudflared folder of your Windows machine.
Can you connect to a machine over RDP?
You can connect to machines over RDP using Cloudflare's Zero Trust platform.
Can cloudflared be run on start?
We recommend that you run cloudflared as a service that is configured to launch on start.
What is Cloudflare's platform?
Cloudflare’s global cloud platform is uniquely suited to remote browsing isolation. Seamless integration with our cloud-native performance, reliability and advanced security products and services provides powerful capabilities for our customers.
What is compliance in telemetry?
Compliance. The inability to control data and activity across geographies or capture required audit telemetry to meet increasingly strict regulatory requirements. This results in significant exposure to penalties and fines.
What is browser isolation?
The core concept behind browser isolation is security-through-physical-isolation to create a “gap” between a user’s web browser and the endpoint device thereby protecting the device (and the enterprise network) from exploits and attacks. Unlike secure web gateways, antivirus software, or firewalls which rely on known threat patterns or signatures, this is a zero-trust approach.
How does a remote browser work in RBI?
The remote browser sends the rendered contents of a web page to the user endpoint device ❹ using a specific protocol and data format ❸. Actions by the user, such as keystrokes, mouse and scroll commands, are sent back to the isolation service over a secure encrypted channel where they are processed by the remote browser and any resulting changes to the remote browser webpage are sent back to the endpoint device.
Why is my HiDPI display fuzzy?
HiDPI displays may render at lower resolutions. Pixel density increases exponentially with resolution which means remote browser sessions (particularly fonts) on HiDPI devices can appear fuzzy or out of focus.
What is the current approach to mitigating security issues inherent in browsing the web?
Current approaches to mitigating security issues inherent in browsing the web are largely based on signature technology for data files and executables, and lists of known good/bad URLs and DNS addresses. The challenge with these approaches is the difficulty of keeping current with known attacks (file signatures, URLs and DNS addresses) and their inherent vulnerability to zero-day attacks. Hackers have devised automated tools to defeat signature-based approaches (e.g. generating hordes of files with unknown signatures) and create millions of transient websites in order to defeat URL/DNS blocklists.
Which department has the least amount of control over the most ubiquitous app in the enterprise?
Paradoxically, IT departments have the least amount of control over the most ubiquitous app in the enterprise – the web browser . The most common complaints about web browsers from enterprise security and IT professionals are:
What makes protecting employees from Internet threats so difficult?
No secure web gateway can possibly block every threat on the Internet. In an attempt to limit risks, IT teams block too many websites, and employees feel overly restricted.
Attacks will strike. Mitigate the impact
Browser Isolation executes all browser code in the cloud, instead of on the endpoint. When users inevitably run into Internet threats, Zero Trust browsing stops malware from infecting their devices and causing chaos in your network.
Not your average remote browser
Legacy remote browsers send a slow and clunky version of a web page to the user. Cloudflare draws an exact replica of the page on the user’s device, and then delivers that replica so quickly it feels like a regular browser.
Verify. Filter. Inspect. Isolate
With Cloudflare Zero Trust, administrators set Zero Trust browsing rules in the same place they design Zero Trust application access policies. Filtering, inspection and isolation rules are applied in one lightning-fast single pass inspection architecture, with minimal latency.
Whitepaper: Common browser isolation challenges, and how to overcome them
Learn the most common challenges associated with traditional browser isolation approaches, and how Cloudflare's Zero Trust platform helps overcome them.
Blog: Browser Isolation for teams of all sizes
Why are remote browsers not a common technology used by everyone? What makes Cloudflare's approach to Browser Isolation unique? Read Tim Obezuk's announcement blog for an overview.
WIRED: Browser Isolation takes on advanced entrenched threats
WIRED magazine's Lily Hay Newman explores the rise of Browser Isolation services, and Cloudflare's debut in the market.
Why Does RDP Matter?
Where Does Cloudflare Access Fit?
- Cloudflare Access adds stronger authentication to RDP sessions by first locking down access to the remote machine via Argo Tunnel, then enforcing identity-based policies to determine who can gain access. Whether your organization uses Okta, Azure AD, or another provider, your users will be prompted to authenticate with those credentials before star...
How Does It Work?
- On the origin side, an admin will configure a single cloudflared instance to run in bastion mode. That bastion will reach out to the two closest Cloudflare edge data centers and create a long-lived HTTP2 session. Once set up, cloudflared will wait for incoming connections from clients to specify which final origin to connect to. This is unlike conventional cloudflaredtunnel behavior, w…
What’s Next?
- While today we are proxying just RDP traffic in bastion mode, we will eventually be expanding this functionality to protocols like FTP, SSH, and generic TCP. In the effort to make protecting internal resources easier than ever before, cloudflared can now also be conveniently found in the Cloudflare package repo, in tagged releases on the cloudflared Github repo, and in the cloudflare…