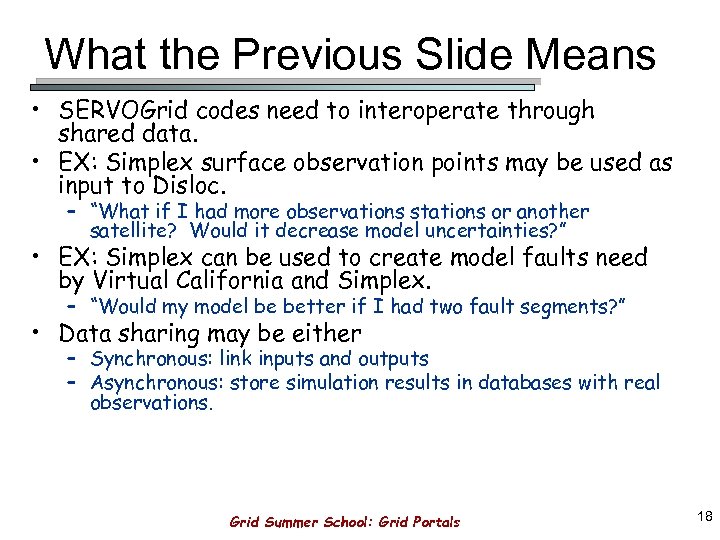
| Name | Type | Operating Systems |
|---|---|---|
| TeamViewer | Remote Administration Tool | Windows, Mac OSX, Linux, Android, iOS. |
| VNC Connect | Remote Access Tool | Windows, Mac, Linux. |
| Desktop Central | Remote Access Tool | Windows, Mac, Linux. |
| Remote Desktop Manager | Remote Access Tool | Windows, Mac, Android, iOS. |
What is the most common form of remote access?
remote access virtual private network (VPN)One common method of providing remote access is via a remote access virtual private network (VPN) connection. A VPN creates a safe and encrypted connection over a less secure network, such as the internet.
What are types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What are remote control tools?
Remote support software can be defined as a tool allowing technicians or support teams to connect to a remote device via the internet, to access it and to perform certain operations.
What is example of remote access?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What are the three main types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What is remote access app?
Remote desktop software, more accurately called remote access applications or remote access software, let you remotely control any computer in another location. With the help of these remote access applications, you can take over the mouse and keyboard of another computer and use it just like your own.
What is the name of an old remote access tool?
Remote Access tools, when used for malicious purposes, are known as a Remote Access Trojan (RAT).
Which of the following are the tools for Remote Desktop?
Top 9 Tools of Remote DesktopTightVNC. VNC is a graphical desktop sharing system that uses the remote buffer protocol to monitor another computer remotely. ... LogMeIn. Logmen has great features and is also one of the most popular remote desktop sharing tools. ... GoToMyPC. ... Mikogo. ... UltraVNC. ... TeamViewer. ... Radmin. ... Splashtop.More items...
What is Remote Desktop access?
A remote desktop is a program or an operating system feature that allows a user to connect to a computer in another location, see that computer's desktop and interact with it as if it were local.
What is remote server access?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
What is remote access security?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What is remote desktop software used for?
Remote desktop software lets users, typically IT professionals or administrators, access and control another user’s computer remotely. This allows...
What’s the best remote desktop software?
According to end-user feedback on TrustRadius, the top-rated remote desktop tools for 2020 include: BeyondTrust Remote Support (Legacy)ConnectWise...
What are the benefits of using a remote desktop tool?
The main benefit of using a remote desktop tool is that an organization can provide support to their employees, customers, or other end-users witho...
What are the best free remote desktop tools?
There are multiple free remote desktop tools available, but the three most popular free products on TrustRadius are: TeamViewerChrome Remote Deskto...
How much does remote desktop software cost?
Free remote desktop software is a great option if you plan on using it for one or two devices. However, free products often don’t have the capacity...
What is remote access tool?
Remote Access Tool is a piece of software used to remotely access or control a computer. This tool can be used legitimately by system administrators for accessing the client computers. Remote Access tools, when used for malicious purposes, are known as a Remote Access Trojan (RAT). They can be used by a malicious user to control the system without the knowledge of the victim. Most of the popular RATs are capable of performing key logging, screen and camera capture, file access, code execution, registry management, password sniffing etc.
How can an attacker remotely control a system?
An attacker can remotely control the system by gaining the key logs, webcam feeds, audio footage, screen captures, etc . RATs normally obfuscate their presence by changing the name, size, and often their behavior or encryption methods. By doing this they evade from AV, firewalls, IDS, IPS and security defense systems.
What is B02K client interface?
B02K client interface has a list of servers that displays the list of compromised servers and this server has its name, IP address, and connection information. Several commands can be used to gather data from victim machine and this command can be executed using the attacker machine by giving the intended parameters. The responses can be seen using the Server Response window.
Do remote access tools require multifactor authentication?
All remote access tools that allow communication to and from the Internet must require multi-factor authentication.
Can an antivirus be disabled?
All antivirus, data loss prevention, and other security systems must not be disabled, interfered with, or circumvented in any way.
What is remote access?
Remote Access is the process of accessing your system from a remote location. When you are not physically near to a system to access it, then you can make use of remote administration to do so. In this process, the remote location may be in the next room, next building or anywhere worldwide.
What is remote administration service?
If the person is not at your place, he can make use of remote administration services to access your system by establishing a secure session between your system and the remote server. They are used to access multiple systems at a given team session to handle multiple tasks with multiple business entities.
What is Solarwinds Dameware Remote Support?
SolarWinds Dameware Remote Support is an easy-to-use package of remote control and systems management tools.
What is remote access plus?
Remote Access Plus is a comprehensive troubleshooting tool that comes in handy for system administrators and IT help desk technicians in resolving issues. Remote Access Plus is built on an intuitive interface that makes it easy to set-up and easy to use.
What is remote desktop software?
Remote Desktop Software is a kind of software or a feature which grants permission to the local system desktop environment to run remotely in one of the systems while it is actually on some other system.
What is Zoho Assist?
Zoho Assist is multi-functional remote support software that helps you with remote support, access to unattended computers, and screen sharing. Zoho Assist supports Windows, Mac, and Linux computers, Android and iOS devices, Raspberry Pi devices, and Chromebooks, so you can support a wide range of clients. Technicians can initiate sessions ...
What are the features of a remote desktop?
Multiple features that aid troubleshooting include file transfer, text chat, VoIP, run as service, multi-monitor navigation, and quick launch options to access the command prompt, control panel, and other essential aspects of the remote computer.
What is remote connection?
The word “Remote” – refers to a local connection .
When a user starts a remote desktop session, the client system transmits a signal through a standard listening?
When a user starts a remote desktop session, the client system transmits a signal through a standard listening port via the internet to the system which is acting as a host asking for access to connect and login.
Can you remotely troubleshoot a computer?
You will be able to remotely troubleshoot computers without launching a full remote control session as it provides system tools and TCP utilities.
What is remote access technology?
A common remote access technology in use today is the IPsec VPN. A piece of software called a VPN client is installed on the end user’s computer and is configured with details about the target network, such as the gateway IP address and a pre-shared security key. Each time the user wants to connect to the corporate network, they start the VPN client, which creates a secure connection to the corporate firewall.
Which operating system do you need for client?
Clients are required to use either the Ultimate or Enterprise versions of Microsoft’s Operating Systems.
Is DirectAccess going to be widespread?
DirectAccess is not going to gain widespread adoption until the OS licensing requirements are revised and the networking is reworked to be more straightforward. While IPv6 is the future of networking, we currently live and work in an IPv4 world, especially on the LAN (as of May 2014, IPv4 still carried more than 96% of Internet traffic worldwide, according to Google ). Setting up a new remote access technology should not require one or more potentially expensive projects before it can be deployed.
What is remote desktop software?
One of the first steps in choosing a remote desktop tool is making sure it supports the operating system your devices use whether it’ s Windows, Mac, iOS, Android, Linux, or Ubuntu. 2.
What is remote administration?
Remote administration tools allow IT professionals to be deployed remotely. Users can perform IT tasks without leaving their physical desk. End-users can receive help and updates to their machines more quickly and efficiently. This can save companies time and money.
What is Dameware remote support?
DameWare Remote Support from Austin IT company SolarWinds is remote administration software for the remote control of desktops, laptops, and servers behind or outside the firewall, allowing registry editing, restart services, logging activity, account and password management, and…
What is remote desktop?
Remote desktop software lets users, typically IT professionals or administrators, access and control another user’s computer remotely. This allows companies to perform IT support and maintenance for specific devices without needing to have an IT professional physically present. These types of tools typically include features such as: 1 screen viewing and capture 2 ability to initiate remote access from mobile 3 file management 4 instant messaging 5 monitoring and alerts
What is Connectwise Control?
ConnectWise Control is a remote support, access, and meeting solution. With ConnectWise Control, users can utilize remote support and access to repair computers, provide updates, and manage machines. Users can also conduct online seminars and presentations using remote meetings.
How many remote desktop products are there?
There are over 40 other remote desktop software products listed on TrustRadius.com, visit our software category page to see which tool best meets your business needs.
How much does remote desktop software cost?
It can also be set up as a subscription model. The subscription model is priced by user and number of unattended machines. Prices run between $55 and $500 per month depending on the number of users.
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It’s necessary for desktop sharing and remote access for help desk activities. The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), ...
How to use PPTP?
To use PPTP, you’ll have to set up a PPP session between the server and the client, usually over the internet. Once the session is established, you’ll create a second dial-up session. This dial-up session will use PPTP to dial through the existing PPP session.
What is PPTP in a network?
PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network.
Can you use a RAS modem on a Windows server?
With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, dial-up only, or a combination of the two. RAS can only provide LAN access to remote users. It doesn’t let LAN users use the modem to, for example, dial their AOL account.
Is RDP the same as ICA?
RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients only, while ICA can provide access for numerous platforms. ICA also offers support for automatic client updates, publishing an app to a web browser, and more.
What are the two types of users that need privileged accounts?
Many organizations need to provide privileged accounts to two types of users: internal users (employees) and external users (technology vendors and contractors). However, organizations that use vendors or contractors must protect themselves against potential threats from these sources.
What are some applications that can be shared on desktop?
There are many applications made possible by desktop sharing including remote support, webinars, and online conferences with audio and visual content (presentation sharing), and real-time global collaboration on projects.
Can anyone log into a desktop sharing tool?
Anyone, anywhere, can log into a desktop sharing tool if they have the credentials, meaning they have access to the whole network as if they are in the building. During a remote support session, if an employee surrenders control of their machine to a remote rep whose account has been compromised, your company’s internal sensitive files could become visible to bad actors and used for nefarious purposes.
Is VPN good for remote access?
VPNs may be good for internal employees, but are not optimal for third-party vendors. Desktop sharing tools may be useful for desktop support and helpdesk, but are not good for complex enterprise remote support. PAM provides improvements over VPN and desktop sharing, but there is only one solution that combines the best of all these types of remote access technologies into one and is purpose-built for vendors and doesn’t include any of the drawbacks: VPAM.
Why Use Remote Access Control?
Deploying remote access control provides a secure connection. It minimizes the risk of data theft or loss and malicious activities since you are controlling the connection, therefore not allowing unknown entities to access private or corporate data.
What is remote control software?
Remote control software solutions also have sharing tools that let users share files from one computer to another, allowing a mutual connection to be setup between local computers and remote devices.
What is Parallels RAS?
With Parallels RAS, remote access control becomes simple and easy to achieve. Access control applies before granting connection to the farm by filtering it using MAC address on the Parallels RAS Gateway. Additionally, remote access control applies after connecting to the farm with multiple options. To learn more, download the white paper about how Parallels RAS enhances Microsoft RDS.
What is Remote Desktop Connection Broker?
The Remote Desktop Connection Broker is responsible for the distribution of connections between the different servers in the farm. The technology is minimal because it only distributes the connections based on session count and server weight.
What is the most common method of accessing a company's network?
Virtual Private Network. Another method which is more common is establishing a VPN. VPNs use the Internet to connect remote sites and users and use encryption and tunneling techniques to access a company’s network. This option is ideal for smaller organizations. Some of the limitations are:
Is remote access control software good?
Security. Most remote access control software does its best to incorporate good security features into their organization as remote access needs remote intervention and exposes devices to potential cybersecurity threats.
Is RDS complicated?
Difficult to install, configure, and update. The installation and configuration of virtual desktop and application delivery solutions with Microsoft RDS are lengthy and complicated. Systems administrators are required to install and configure multiple different servers and server roles and install additional software to assist the process.
Why is cybersecurity important in remote work?
Bringing cybersecurity to the top-of-mind for your remote workforce is important in successfully educating employees on the new risks their work environment presents. Conducting training for security best practices, as well as discussing your organization’s cybersecurity standing and vulnerabilities with the entire workforce are both potential ways to combat network threats.
What should be protected using multi-factor authentication?
Any machine that is capable of connecting to your network should be protected using multi-factor authentication, automatic session timeouts, and access monitoring to prevent unauthorized users from getting into the data, even if they have the device.
Can remote workers access sensitive information?
But with remote work and the physical locations of your workforce and sensitive information further apart, the chances of unauthorized users accessing sensitive data through employees’ computers, phones, and tablets increases exponentially .