- On the VPN server, in Server Manager, select the Notifications flag.
- In the Tasks menu, select Open the Getting Started Wizard. ...
- Select Deploy VPN only. ...
- Right-click the VPN server, then select Configure and Enable Routing and Remote Access.
Does VPN allow remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What is remote access VPN Cisco?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network such as the Internet. Remote access VPNs for IPsec IKEv2. 8.4(1) Added IPsec IKEv2 support for the AnyConnect Secure Mobility Client.
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is configuration of VPN?
Since this is Android, your setup menu may vary. Just hit “OK” and you've got a VPN. Head into “Settings” > “Network & Internet” > “Advanced” > “VPN.” If you don't see “Network & Internet” in the Settings menu (which may depend on your Android overlay), then do a search within Settings for VPN. Press the “Add” button.
Is Cisco AnyConnect a VPN?
cisco connect Anyconnect is a secure mobility client solution for secure VPN access for remote works, highly secure access to the enterprise's network from any device from anywhere at any time.
How do I setup a VPN on my Cisco router?
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel. ... Step 2: Create IPSec Transform (ISAKMP Phase 2 policy) ... Step 3: Create Crypto Map. ... Step 4: Apply Crypto Map to the Public Interface.
What is the difference between VPN and remote access?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How do I fill out a VPN configuration?
Set up a VPN on Android smartphonesOpen the Settings menu of the phone. ... Tap on Wi-Fi & Internet or Wireless & networks. ... Tap on VPN. ... Tap on the plus sign at the top right corner. ... Enter the necessary information like the server address, username, and password.
What should I write in VPN configuration?
Configure your VPN's information. Connection name — Add the name of the VPN on your computer. Server name or address — Enter or change the VPN's server address. VPN type — Enter or change the connection type. Type of sign-in info — Select a new type of sign-in (e.g., Password) if necessary.
Are VPN configurations safe?
Using a reliable virtual private network (VPN) can be a safe way to browse the internet. VPN security can protect from IP and encrypt internet history and is increasingly being used to prevent snooping on by government agencies. However, VPNs won't be able to keep you safe in all scenarios.
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
What are the two types of VPN connections?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
How to establish a VPN connection?
The user first connects to the internet and then initiates a VPN connection via a locally installed client software or web browser to the VPN server located in the office. The VPN server based on your access level permission grants you access to internal company resources via ...
What is cloud VPN?
The objective of cloud VPN is to give employees and remote workers secure access to cloud resources through a cloud-based VPN infrastructure over the public Internet from any location in the world without undermining security.
What is the most widely used VPN technology?
The two most commonly used technologies in remote access VPNs are IPSec and SSL . IPsec is the most widely used VPN technology.
What is the best remote desktop for a small office?
One key technology that is crucial to enabling secure remote access to your organization’s internal network is a Virtual Private Network (VPN). In a small office where only an individual or two needs to connect to one or two office computers from home, a remote desktop application like GoToMyPC or PCAnywhere may be preferable. However, if business needs require multiple remote connections, a full VPN is the most viable option.
How does a VPN work?
How a VPN Works. A VPN allows you to create a secure virtual tunnel to your office network through the public network such as the internet. It protects confidentiality (data remains secret via encapsulation) and integrity (data remains unaltered via encryption) of data as it travels over the public internet.
Why is IPsec used in VPN?
IPsec is the most widely used VPN technology. Because it provides protection at the IP level layer (Layer 3), it can be deployed to secure communication between the office network and a host computer used at home. A client application is required at the host computer in order to establish a connection. IPsec was designed to ensure data integrity and confidentiality, and offers enterprise-grade security features.
What is VPN tunneling?
You can liken VPN tunneling to the process of moving physical cash from one location to another using an armored transport van along public highways. The cash in this instance is your data, the public highway is the non-secure public network, and the armored van is the VPN tunnel.
How to create a null route for remote access?
create a null route for network used for remote access users, defined in section c. Just go to Devices > Device Management > Edit > Routing > Static Route > Add route:
What version of VPN is Firepower Threat Defense?
This document provides a configuration example for Firepower Threat Defense (FTD) version 6.2.2 and later, that allows remote access VPN to use Transport Layer Security (TLS) and Internet Key Exchange version 2 (IKEv2). As a client, Cisco AnyConnect will be used, which is supported on multiple platforms.
What certificates are needed for AnyConnect?
Certificates are essential when you configure AnyConnect. Only RSA based certificates are supported in SSL and IPSec. Elliptic Curve Digital Signature Algorithm certificates (ECDSA) are supported in IPSec, but it's not possible to deploy new AnyConnect package or XML profile when ECDSA based certificate is used. It means that you can use it for IPSec, but you will have to predeploy AnyConnect package and XML profile to every user and any change in XML profile will have to be manually reflected on each client (bug: CSCtx42595 ). Additionally the certificate should have Subject Alternative Name extension with DNS name and/or IP address to avoid errors in web browsers.
Can VPN traffic come from pool?
This means, that you need to allow traffic coming from pool of addresses on outside interface via Access Control Policy. Although the pre-filter or access-control rule is added intending to allow VPN traffic only, if clear-text traffic happens to match the rule criteria, it is erroneously permitted.
How to add a VPN pool to anyconnect?
Navigate to Objects > Networks > Add new Network. Configure VPN Pool and LAN Networks from FDM GUI. Create a VPN Pool in order to be used for Local Address Assignment to AnyConnect Users as shown in the image.
How to add VPN users to FTD?
Navigate to Objects > Users > Add User. Add VPN Local users that will connect to FTD via Anyconnect. Create local Users as shown in the image.
How to debug webvpn?
If a user is having initial connectivity issues, enable debug webvpn anyconnect on the FTD and analyze the debug messages. De bugs must be run on the CLI of the FTD. Use the command debug webvpn anyconnect 255
How to configure NAT exemption?
NAT exemption can be configured manually under Policies > NAT or it can be configured automatically by the wizard. Select the inside interface and the networks that Anyconnect clients will need to access as shown in the image.
What version of Firepower Threat Defense is RA VPN?
This document describes how to configure the deploying of Remote Access Virtual Private Network (RA VPN) on Firepower Threat Defense (FTD) managed by the on-box manager Firepower Device Manager (FDM) running version 6.5.0 and above.
Does AnyConnect have split tunneling?
In the group policy, add Split tunnelling so users connected to Anyconnect will only send traffic that is destined to the internal FTD network over the Anyconnect client while all other traffic will go out the user's ISP connection as shown in the image.
Can I monitor AnyConnect users?
As of FDM 6.5.0 there is no way to monitor the Anyconnect users through the FDM GUI. The only option is to monitor the Anyconnect users via CLI. The CLI console of the FDM GUI can be used as well to verify users are connected.
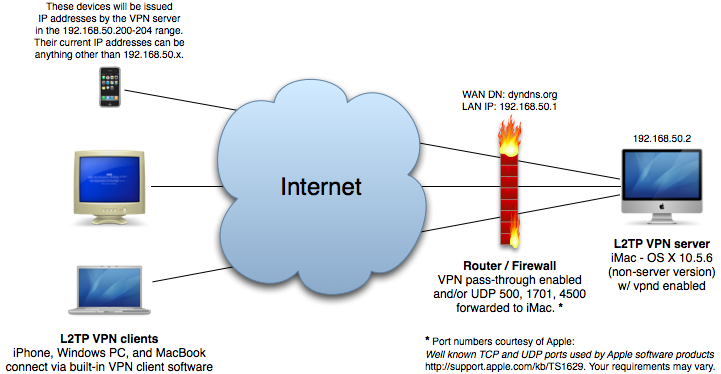
What is remote access VPN?
In remote access VPN, you might want users on the remote networks to access the Internet through your device. However, because the remote users are entering your device on the same interface that faces the Internet (the outside interface), you need to bounce Internet traffic right back out of the outside interface. This technique is sometimes called hair pinning.
How to view VPN configuration?
Click Device, then click View Configuration in the Site-to-Site VPN group.
How to use a VPN on a computer?
Step 1. Using a web browser, open https://ravpn-address , where ravpn-address is the IP address or hostname of the outside interface on which you are allowing VPN connections. You identify this interface when you configure the remote access VPN. The system prompts the user to log in. Step 2.
How to complete a VPN connection?
To complete a VPN connection, your users must install the AnyConnect client software. You can use your existing software distribution methods to install the software directly. Or, you can have users install the AnyConnect client directly from the Firepower Threat Defense device.
What is AnyConnect client profile?
AnyConnect client profiles are downloaded to clients along with the AnyConnect client software. These profiles define many client-related options, such as auto connect on startup and auto reconnect, and whether the end user is allowed to change the option from the AnyConnect client preferences and advanced settings.
How long is a VPN idle?
Idle Timeout —The length of time, in minutes, that the VPN connection can be idle before it is automatically closed, from 1-35791394. The default is 30 minutes. Browser Proxy During VPN Sessions —Whether proxies are used during a VPN session for Internet Explorer web browsers on Windows client devices.
Where does remote access VPN problem originate?
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
Introduction
Requirements
- Cisco recommends that you have knowledge of these topics: 1. Basic VPN, TLS and IKEv2 knowledge 2. Basic Authentication, Authorization, and Accounting (AAA) and RADIUS knowledge 3. Experience with Firepower Management Center
Components Used
- The information in this document is based on these software and hardware versions: 1. Cisco FTD 6.2.2 2. AnyConnect 4.5
Configuration
- 2. Remote access wizard
1. Go to Devices > VPN > Remote Access > Add a new configuration. 2. Name the profile according to your needs, select FTD device: 1. In step Connection Profile, type Connection Profile Name, select Authentication Server and Address Poolswhich you have created earlier: 1. Click o…
Connection
- To connect to FTD you need to open a browser, type DNS name or IP address pointing to the outside interface, in this example https://vpn.cisco.com. Youwill then have to login using credentials stored in RADIUS server and follow instructions on the screen. Once AnyConnect installs, you then need to put the same address in AnyConnect window and click Connect.
Limitations
- Currently unsupported on FTD, but available on ASA: 1. Double AAA Authentication 2. Dynamic Access Policy 3. Host Scan 4. ISE posture 5. RADIUS CoA 6. VPN load-balancer 7. Local authentication (Enhancement: CSCvf92680 ) 8. LDAP attribute map 9. AnyConnect customization 10. AnyConnect scripts 11. AnyConnect localization 12. Per-app VPN 13. SCEP proxy 14. WSA in…
Security Considerations
- You need to remember that by default, sysopt connection permit-vpn option is disabled. This means, that you need to allow traffic coming from pool of addresses on outside interface via Access Control Policy. Although the pre-filter or access-control rule is added intending to allow VPN traffic only, if clear-text traffic happens to match the rule criteria, it is erroneously permitted…