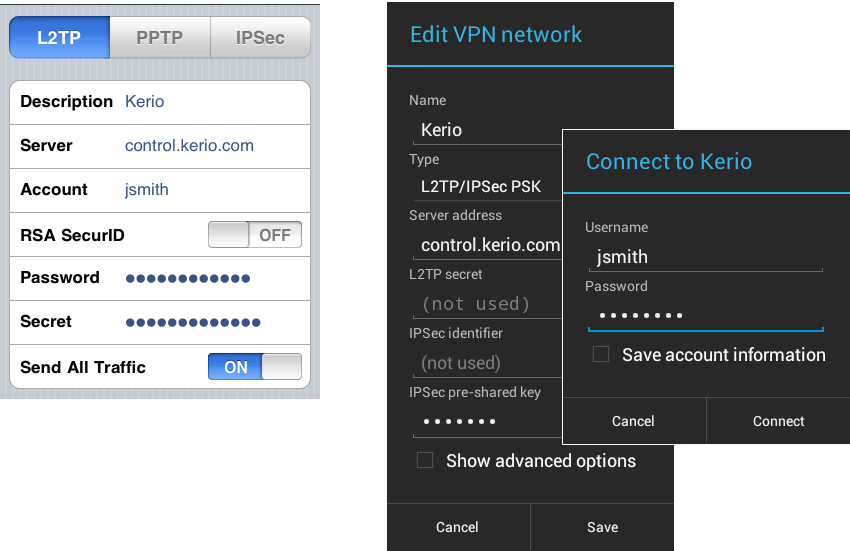
Configure IPsec (remote access)
- Go to VPN > IPsec (remote access) and click Enable.
- Specify the general settings.
- Specify the client information.
- Specify the advanced settings you want and click Apply.
- Click Export connection at the bottom of the page.
- Send the .scx file to users.
- Optionally, download the client and send it to users.
How to configure the IPsec VPN?
Configuring the IPsec VPN To create the VPN, go to VPN > IPsec Wizard and create a new tunnel using a pre-existing template. Name the VPN. The tunnel name cannot include any spaces or exceed 13 characters. Set Template to Remote Access, and set... Set the Incoming Interface to wan1 and ...
What are remote access VPNs?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network. The Internet Security Association and Key Management Protocol, also called IKE, is the negotiation protocol that lets the IPsec client on the remote PC and the ASA agree on how to build an IPsec Security Association.
What VPN license do I need to use IPSEC remote access VPN?
IPsec remote access VPN using IKEv2 requires an AnyConnect Plus or Apex license, available separately. IPsec remote access VPN using IKEv1 and IPsec site-to-site VPN using IKEv1 or IKEv2 uses the Other VPN license that comes with the base license.
How do I set up a VPN tunnel on my Device?
Set Local Interfaceto lanand set Local Addressto the local network address. Enter a Client Address Rangefor VPN users. The IP range you enter here prompts FortiOS to create a new firewall object for the VPN tunnel using the name of your tunnel followed by the _range suffix (in the example, IPsec-FCT_range).
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
What is IPsec remote access VPN?
The IPsec Remote Access feature introduces server support for the Cisco VPN Client (Release 4. x and 5. x) software clients and the Cisco VPN hardware clients. This feature allows remote users to establish the VPN tunnels to securely access the corporate network resources.
How do I configure IPsec remote access VPN in Sophos XG?
Configure IPsec remote access VPN with Sophos Connect clientSpecify the settings on the Sophos Connect client page.Send the configuration file to users.Add a firewall rule.Send the Sophos Connect client to users. ... Users install the client, import the configuration file into the client, and establish the connection.
How is IPsec VPN configured?
To configure a route-based or policy-based IPsec VPN using autokey IKE:Configure interfaces, security zones, and address book information. ... Configure Phase 1 of the IPsec VPN tunnel. ... Configure Phase 2 of the IPsec VPN tunnel. ... Configure a security policy to permit traffic from the source zone to the destination zone.More items...
Is IPSec the same as VPN?
The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
What ports need to be open for IPSec VPN?
Mobile VPN with IPSec requires the client to access the Firebox on UDP ports 500 and 4500, and ESP IP Protocol 50. This often requires a specific configuration on the client's internet gateway, so clients might not be able to connect from hotspots or with mobile Internet connections.
What type of authentication can be used for IPsec site to site VPN Sophos?
preshared keyWe want to create and deploy an IPsec VPN between the head office and a branch office. We use a preshared key for authentication.
What is Isakmp policy?
ISAKMP policies that support IPsec client connections have two policy components: the ISAKMP policy and the IKE Mode Configuration policy. The "client" ISAKMP policy should have the lowest priority if the router is going to support peer relationships between IPsec gateways and IPsec clients.
How does SSL VPN Work?
An SSL tunnel VPN allows a web browser to securely access multiple network services that are not just web-based via a tunnel that is under SSL. These services could be proprietary networks or software built for corporate use only that cannot be accessed directly via the internet.
How do I create a VPN tunnel between two sites?
0:525:14How To Create a Secure Tunnel Between Two RV130W RoutersYouTubeStart of suggested clipEnd of suggested clipIn the policy configuration window give the configuration a name then choose your exchange mode onceMoreIn the policy configuration window give the configuration a name then choose your exchange mode once we've done that we'll select our local identifier from the drop-down menu.
How many steps are there to configuring site to site IPSec VPNS?
Configure IPSec - 4 Simple Steps To configure IPSec we need to setup the following in order: Create extended ACL. Create IPSec Transform. Create Crypto Map.
What is Phase 1 and 2 IPSec VPN?
Phase 1 Security Associations are used to protect IKE messages that are exchanged between two IKE peers, or security endpoints. Phase 2 Security Associations are used to protect IP traffic, as specified by the security policy for a specific type of traffic, between two data endpoints.
What are the 3 protocols used in IPsec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Which is better IPsec or OpenVPN?
In site-to-site connections, OpenVPN functions faster and provides more security than IPsec. IPsec encryption operates on a kernel level, whereas OpenVPN functions in user space. Therefore, in terms of endpoint performance, IPsec is more favorable. With OpenVPN, you're limited to the capacity of the software.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
What happens if a Cisco VPN client has a different preshared key size?
If a Cisco VPN Client with a different preshared key size tries to connect, the client logs an error message indicating it failed to authenticate the peer.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
What is dynamic crypto map?
Dynamic crypto maps define policy templates in which not all the parameters are configured. This lets the ASA receive connections from peers that have unknown IP addresses, such as remote access clients.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
What is IPsec firewall?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301. Use these settings to create and manage IPsec connections and to configure failover.
What is remote access policy?
With remote access policies, you can provide access to network resources by individual hosts over the internet using point-to-point encrypted tunnels. Remote access requires SSL certificates and a user name and password.
What is a bookmark in a VPN?
Bookmarks specify a URL, a connection type, and security settings. Use bookmarks with clientless access policies to give users access to your internal networks or services. For example, you may want to provide access to file shares or allow remote desktop access. Users can access bookmarks through the VPN page in the user portal.
How to enable Sophos Connect?
Go to VPN > Sophos Connect client and click Enable.
What is Sophos Connect?
Sophos Connect client is VPN software that runs on Microsoft Windows 7 SP2 and later, and Mac OS 10.12 and later. It establishes highly secure, encrypted VPN tunnels for off-site employees.
What is firewall rule?
Firewall rules implement control over users, applications, and network objects in an organization. Using the firewall rule, you can create blanket or specialized traffic transit rules based on the requirement. The rule table enables centralized management of firewall rules.
Does XG firewall have a tunnel all policy?
Note By default, XG Firewall implements a Tunnel all policy over the Sophos Connect client, sending all traffic, including traffic to the internet, from the remote user through the tunnel. If you specify the Tunnel all policy, the firewall rule must also have the Destination zone set to WAN.
What is the difference between an outside and inside security appliance?
Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is dynamic crypto map?
The security appliance uses dynamic crypto maps to define a policy template where all the parameters do not have to be configured. These dynamic crypto maps let the security appliance receive connections from peers that have unknown IP addresses. Remote access clients fall in this category.
Resolution For SonicOS 7.x
- This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware. Configure WAN Group VPN on the SonicWall 1. Login to the SonicWall manageme…
Olution For SonicOS 6.5
- This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware. Configure WAN Group VPN on the SonicWall 1. Login to the SonicWall management GUI. 2. Click Managein the top navigation menu. 3. Navigate toVPN | Base Settings. 4. Ensure th…
Related Articles
Categories
- Firewalls> TZ Series> GVC/L2TP
- Firewalls> NSa Series> GVC/L2TP
- Firewalls> NSv Series> GVC/L2TP