
To configure SSH on Cisco router, you need to do:
- Enable SSH on Cisco router.
- Set Password for SSH.
- Force remote access to use SSH.
- Enable Password Encryption.
- Add domain name Server (DNS).
- Add Username and Password.
- Step 1: Generate SSH Keys. Open the terminal on your local machine. ...
- Step 2: Name your SSH keys. ...
- Step 3: Enter a passphrase (optional) ...
- Step 4: Move the public key to the remote machine. ...
- Step 5: Test your connection.
How to enable SSH access?
- You should see an "active" status. If you don't, you may need to restart your system and try again.
- To stop SSH, enter systemctl stop sshd and you'll see an "inactive" tag.
- If you want SSH to automatically start whenever you reboot the system, enter: sudo systemctl enable sshd. Change "enable" to "disable" if you want to cancel the automatic setting.
How to use SSH to connect to a remote server?
Start the SSH server
- Open a browser on your technician PC and navigate to the URL of your Factory OS device.
- Once connected to Device Portal, navigate to the SSH tab in the left-hand pane. The SSH tab is at the bottom of the list.
- Select Enable SSH.
How do I Secure my SSH access?
- Use the built in VPN server on your Windows machine to additionally secure your traffic. ...
- Set client connection encryption level. ...
- Employ two-factor authentication using a third-party tool, such as Duo Security. ...
- Enforce firewall rules to limit exposure of open RDP ports to the Internet, especially if you are using the default RDP TCP port 3389. ...
How do I use SSH to Access MySQL remotely?
Perform the following steps to create an SSH tunnel to the MySQL server with PuTTY:
- Launch Putty and enter the IP Address of the server in the Host name (or IP address) field:
- Under the Connection menu, expand SSH and select Tunnels. ...
- Go back to the Session page to save the settings so that you do not need to enter them again. ...
- Select the saved session and log in to the remote server by clicking on the Open button. ...
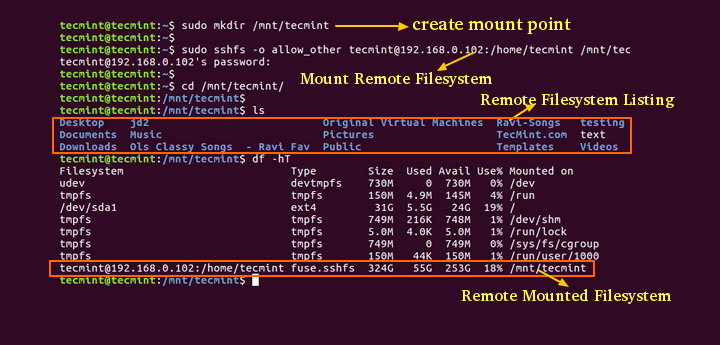
How do I setup a remote SSH server?
How to Connect via SSHOpen the SSH terminal on your machine and run the following command: ssh your_username@host_ip_address. ... Type in your password and hit Enter. ... When you are connecting to a server for the very first time, it will ask you if you want to continue connecting.More items...•
Is SSH used for remote access?
RDP and SSH are both used to remotely access machines and other servers. They're both essential for securely accessing cloud-based servers, and aid remote employees in leveraging infrastructure on-prem as well.
How do I use remote desktop through SSH?
Create an SSH Tunnel for Remote DesktopCreate a new session to one of the remotely accessible servers.Open the session properties.Select Port Forwarding under the Connection section.Click Add.Enter a descriptive name, such as RDP to myhost.In the Local section, enter a port number to use, such as 33389.More items...•
How do I setup SSH between two computers?
To create an ssh key between two machines, perform the following steps:Generate the keys. On the machine from which you will be connecting, type: $ ssh-keygen -t dsa -f {to_machine} ... Move the public key to the receiving machine. ... Authorize the public key. ... Move your identity to a safe place. ... Test the keys.
Is SSH better than RDP?
Though they are quite similar, there are fundamental differences between them. SSH is considered more secure because it does not require additional tools such as a Virtual Private Network (VPN) or Multi-factor authentication (MFA) as RDP does.
Is SSH the same as RDP?
A Major Difference between RDP and SSH RDP and SSH are designed to provide two distinct solutions for connecting to remote computer systems. RDP furnishes users with a tool for managing remote connections via a GUI. SSH offers a Secure Shell and is used for text-based management of remote machines.
How do I SSH into a friend's computer?
How to setup SSH keysStep 1: Generate SSH Keys. Open the terminal on your local machine. ... Step 2: Name your SSH keys. ... Step 3: Enter a passphrase (optional) ... Step 4: Move the public key to the remote machine. ... Step 5: Test your connection.
How do I enable SSH on my server?
Enable the ssh service by typing: # sudo systemctl enable ssh. Start the ssh service by typing: # sudo systemctl start ssh. Test it by login into the system using:# ssh userName@Your-server-name-IP.
How do I use SSH on Windows?
How to use an SSH clientStart PuTTY.In the Host Name (or IP address) text box, type the hostname or IP address of the server where your account is located.In the Port text box, type 7822. ... Confirm that the Connection type radio button is set to SSH.Click Open.More items...
Can you SSH into a computer on a different network?
Yes, it is absolutely possible. You typically use port forwarding for that (for different residential routers, the way you do port forwarding may vary).
How do I SSH between two computers without a password in Linux?
How to Set Up Passwordless SSH LoginBefore You Start: Check for Existing SSH Keys.Step 1: Generate SSH Key Pair.Step 2: Upload Public Key to Remote Server. Option 1: Upload Public Key Using the ssh-copy-id Command. ... Step 3: Log in to Server Without Password.Optional: Troubleshooting Remote Server File Permissions.
How do I access a server remotely?
Remote Desktop to Your Server From a Local Windows ComputerClick the Start button.Click Run...Type “mstsc” and press the Enter key.Next to Computer: type in the IP address of your server.Click Connect.If all goes well, you will see the Windows login prompt.
What is SSH remote server?
SSH is used by anyone who needs to remotely manage a computer in a secure manner, as well as system and network administrators. Secure Shell SSH provides public key authentication and password authentication, and encrypted data communications between the two computers connected over an open network.
How do you SSH into a device?
ConnectOpen a Command prompt window on your technician PC.Connect to the device: To connect using a username and password: cmd Copy. ssh user@192. 168. ... Enter the password for your user if you're connecting with a username and password, or if you configured your key to require a password.
Why is SSH so popular?
It has been over a decade since OpenSSH became the de facto standard of remote access protocols, and in that time, Internet connectivity has changed dramatically. For reliable, low-latency LAN and Internet connections, SSH is still the king due to its simplicity, speed, and security.
How do I access a Linux server remotely?
Connect to Linux Remotely Using SSH in PuTTYSelect Session > Host Name.Input the Linux computer's network name, or enter the IP address you noted earlier.Select SSH, then Open.When prompted to accept the certificate for the connection, do so.Enter the username and password to sign in to your Linux device.
What is SSH in Linux?
SSH, or Secure Shell, is a protocol used to securely log onto remote systems. It is the most common way to access remote Linux servers. In this guide, we will discuss how to use SSH to connect to a remote system.
Why is SSH so popular?
SSH has remained popular because it is secure, light-weight, and useful in diverse situations.
How does key based authentication work?
Key-based authentication works by creating a pair of keys: a private key and a public key. The private key is located on the client machine and is secured and kept secret. The public key can be given to anyone or placed on any server you wish to access.
Can you use SSH to log into a server?
If you have created SSH keys, you can enhance your server’s security by disabling password-only authentication. Apart from the console, the only way to log into your server will be through the private key that pairs with the public key you have installed on the server.
What is SSH client?
An SSH client is an application you install on the computer which you will use to connect to another computer or a server. The client uses the provided remote host information to initiate the connection and if the credentials are verified, establishes the encrypted connection.
How to enable remote access in Windows 7?
Enabling Remote Access in Windows 7, 8, 10 and Windows Server Versions. Step 1: Allow Remote Connections. Step 2: Add Users to the List of Remote Users. How to Use the Remove Desktop Connection Client.
How to get remote desktop on Windows 7?
You can find it in a couple of different ways: For Windows 7, click on Start -> All Programs, go to the ‘Accessories’ folder and click on Remote Desktop Connection.
What is the protocol used to connect to a remote machine?
There are many ways to establish a connection with a remote machine depending on the operating system you are running, but the two most used protocols are: Secure Shell (SSH) for Linux-based machines. Remote Desktop Protocol (RDP) for Windows-based machines.
Can you encrypt a VNC connection?
For users who are used to working in a graphical desktop environment with Virtual Network Computing (VNC), it is possible to completely encrypt connections using SSH tunneling. In order to tunnel VNC connections over SSH, you will need to run this command in the terminal on your Linux or UNIX machine:
How to find my IP address?
To determine which public IP address a computer is using: From your web browser, go to com or use its search bar. Type in “what is my IP” or simply “ my IP” and hit Enter.
Can you use ECDSA fingerprint on remote server?
An ECDSA key fingerprint is now added and you are connected to the remote server. If the computer you are trying to remotely connect to is on the same network, then it is best to use the private IP address instead of the public IP address. Otherwise, you will have to use the public IP address only.
What is SSH in a network?
Secure Shell (SSH) is a protocol which provides a secure remote access connection to network devices. Communication between the client and server is encrypted in both SSH version 1 and SSH version 2. Implement SSH version 2 when possible because it uses a more enhanced security encryption algorithm. This document discusses how to configure and ...
What is SSH authentication?
SSH uses either local security or the security protocol that is configured through AAA on your router for user authentication. When you configure AAA, you must ensure that the console is not running under AAA by applying a keyword in the global configuration mode to disable AAA on the console.
Why isn't the connect button enabled?
The Connect button is not enabled if you do not enter the host name and username. This screenshot shows that the login banner is displayed when Secure Shell connects to the router. Then, the login banner password prompt displays. The PuTTY client does not require the username to initiate the SSH connection to the router.
Can you test authentication without SSH?
Authentication Test without SSH. First test the authentication without SSH to make sure that authentication works with the router Carter before you add SSH. Authentication can be with a local username and password or with an authentication, authorization, and accounting (AAA) server that runs TACACS+ or RADIUS.
What is SSH protocol?
SSH (Secure Shell) is a protocol which define how to connect securely over a network. The catch us Securely. Unlike telnet which is not secure, SSH protocol provides the three main concepts of security; authentication- Authentication to reliably determine the identity of the connecting computer. confidentiality (via encryption) ...
What is SSH encryption?
confidentiality (via encryption) – , encryption to scramble data so that only the intended recipient can read it. integrity of data transfer over a network – to guarantees the data sent over the network is not changed along the way by a third party. SSH has two main versions, SSH1 and SSH2.
Does SSH2 use TCP?
SSH uses TCP as its transport layer protocol and uses well-known port number 22. Now, to allow Telnet or SSH access to any device like a router or a switch, the device needs an IP address.
What is SSH on Cisco router?
The Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. The best-known example application is for remote login to computer systems by users.
What is SSH in network?
SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with an SSH server. Common applications include remote command-line login and remote command execution, but any network service can be secured with SSH.
Background
SSH should replace Telnet for management connections. Telnet uses insecure plain text communications. SSH provides security for remote connections by providing strong encryption of all transmitted data between devices. In this activity, you will secure a remote switch with password encryption and SSH.
Instructions
a. Using the command prompt on PC1, Telnet to S1. The user EXEC and privileged EXEC password is cisco. b. Save the current configuration so that any mistakes you might make can be reversed by toggling the power for S1.
1. Multi-Factor Authentication (MFA) for employee access
Option 1) Leverage your existing LDAP user directory, for example an on-premise Active Directory together with a Time-based One-time Password (TOTP) to enforce Multi-Factor Authentication (MFA) for your employees.
2. Temporary access to authorized targets - without passwords
PrivX provides role-based access controls (RBAC) to authorized targets that consist of both the target host and target account.
3. Restricted Windows RDP access to targets or applications
You can also grant limited RDP access to specific targets, for example RDP without file transfer or clipboard could be allowed for some PrivX users to login as self to access their Windows workstations. You can restrict access even further.
4. Restricted SSH access
Any target host running a secure shell server can be configured with PrivX Roles to allow restricted access. Secure Shell access via the PrivX GUI is restricted by design to Shell (terminal) and File Transfers only.
Remote access management made easy
Our solution, PrivX, is a quick-to-implement and scalable privileged access management (PAM) solution that extends to all employees working from home for establishing secure remote access to web applications. It’s a viable alternative for VPNs and other traditional remote secure access tools.
Suvi Lampila
Suvi Lampila is a Senior Technical Services Engineer at SSH.COM. Suvi has been with SSH since 2001 and she has held various positions in technical support, quality assurance and professional services both in Finland and Hong Kong.
CORE Syntax
- To connect to a remote system using SSH, we’ll use the sshcommand. If you are using Windows, you’ll need to install a version of OpenSSH in order to be able to ssh from a terminal. If you prefer to work in PowerShell, you can follow Microsoft’s documentation to add OpenSSH to PowerShell. If you would rather have a full Linux environment available, ...
How Does Ssh Work?
- SSH works by connecting a client program to an ssh server, called sshd. In the previous section, ssh was the client program. The ssh server was already running on the remote_hostthat we specified. On nearly all Linux environments, the sshdserver should start automatically. If it is not running for any reason, you may need to temporarily access your server through a web-based co…
How to Configure Ssh
- When you change the configuration of SSH, you are changing the settings of the sshd server. In Ubuntu, the main sshd configuration file is located at /etc/ssh/sshd_config. Back up the current version of this file before editing: Open it using nanoor your favourite text editor: You will want to leave most of the options in this file alone. However, there are a few you may want to take a loo…
How to Log Into Ssh with Keys
- While it is helpful to be able to log in to a remote system using passwords, it is faster and more secure to set up key-based authentication.
Client-Side Options
- There are a number of optional flags that you can provide when connecting through SSH. Some of these may be necessary to match the settings in the remote host’s sshdconfiguration. For instance, if you changed the port number in your sshdconfiguration, you will need to match that port on the client-side by typing: If you only want to execute a single command on a remote syst…
Disabling Password Authentication
- If you have created SSH keys, you can enhance your server’s security by disabling password-only authentication. Apart from the console, the only way to log into your server will be through the private key that pairs with the public key you have installed on the server. As root or user with sudo privileges, open the sshdconfiguration file: Locate the line that reads Password Authentica…
Conclusion
- Learning your way around SSH will greatly benefit any of your future cloud computing endeavours. As you use the various options, you will discover more advanced functionality that can make your life easier. SSH has remained popular because it is secure, light-weight, and useful in diverse situations. Next, you may want to learn about working with SFTPto perform command line file tr…
Introduction
Prerequisites
- Requirements
The Cisco IOS image used must be a k9(crypto) image in order to support SSH. For example c3750e-universalk9-tar.122-35.SE5.taris a k9 (crypto) image. - Components Used
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command. The informati…
Test Authentication
- Authentication Test without SSH
First test the authentication without SSH to make sure that authentication works with the router Carter before you add SSH. Authentication can be with a local username and password or with an authentication, authorization, and accounting (AAA) server that runs TACACS+ or RADIUS. (Auth… - Authentication Test with SSH
In order to test authentication with SSH, you have to add to the previous statements in order to enable SSH on Carter and test SSH from the PC and UNIX stations. At this point, the show crypto key mypubkey rsacommand must show the generated key. After you add the SSH configuration, …
Optional Configuration Sets
- Prevent Non-SSH Connections
If you want to prevent non-SSH connections, add the transport input sshcommand under the lines to limit the router to SSH connections only. Straight (non-ssh) Telnets are refused. Test to ensure that non-SSH users cannot Telnet to the router "Carter". - Set Up an IOS Router or Switch as SSH Client
There are four steps required to enable SSH support on a Cisco IOS router: 1. Configure the hostname command. 2. Configure the DNS domain. 3. Generate the SSH key. 4. Enable SSH transport support for the vty. If you want to have one device act as an SSH client to the other, yo…
Debug and Show Commands
- Before you issue the debug commands described here, refer to Important Information on Debug Commands. Certain show commands are supported by the Output Interpreter Tool (registered to customers only), which allows you to view an analysis of showcommand output. 1. debug ip ssh Displays debug messages for SSH. 2. show ssh Displays the status of SSH server connectio…
Sample Debug Output
- Server Debug
Note: This is Solaris machine output.
Tips
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configur…
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configured for the router. Each SSH connection uses a vtyresource.
- SSH uses either local security or the security protocol configured through AAA on your router for user authentication. When you configure AAA, you must ensure that the console is not run under AAA....