- Step 1: First step in configuring SSH to securely access the CLI interface of a Cisco Router or Switch remotely is to...
- Step 2: Cisco devices use RSA public key encryption algorithm for SSH connectivity. Before generating RSA encryption...
- Step 3: Next important step you have to do is to configure router/switch to use local user database for authentication...
Full Answer
How to configure SSH to remotely access a Cisco router or switch?
Step 1: First step in configuring SSH to securely access the CLI interface of a Cisco Router or Switch remotely is to create a local user database for user authentication. Follow these steps to create a local user with username "jajish" and password as "OmniSecuPass" and with a privilege level 15.
How do I configure an SSH server for RSA based authentication?
Complete these steps in order to configure the SSH server to perform RSA based authentication. Specify the Host name. Define a default domain name. Generate RSA key pairs. Configure SSH-RSA keys for user and server authentication. Configure the SSH username. Specify the RSA public key of the remote peer. Specify the SSH key type and version.
How do I secure SSH on my server?
That can be a single IP address, an IP range, or a hostname: sshd : 10.10.0.5, LOCAL. Make sure to keep your log in information secure at all times and to apply security at multiple layers. Use different methods to limit SSH access to your servers, or use services that will block anyone who tries to use brute force to gain access to your servers.
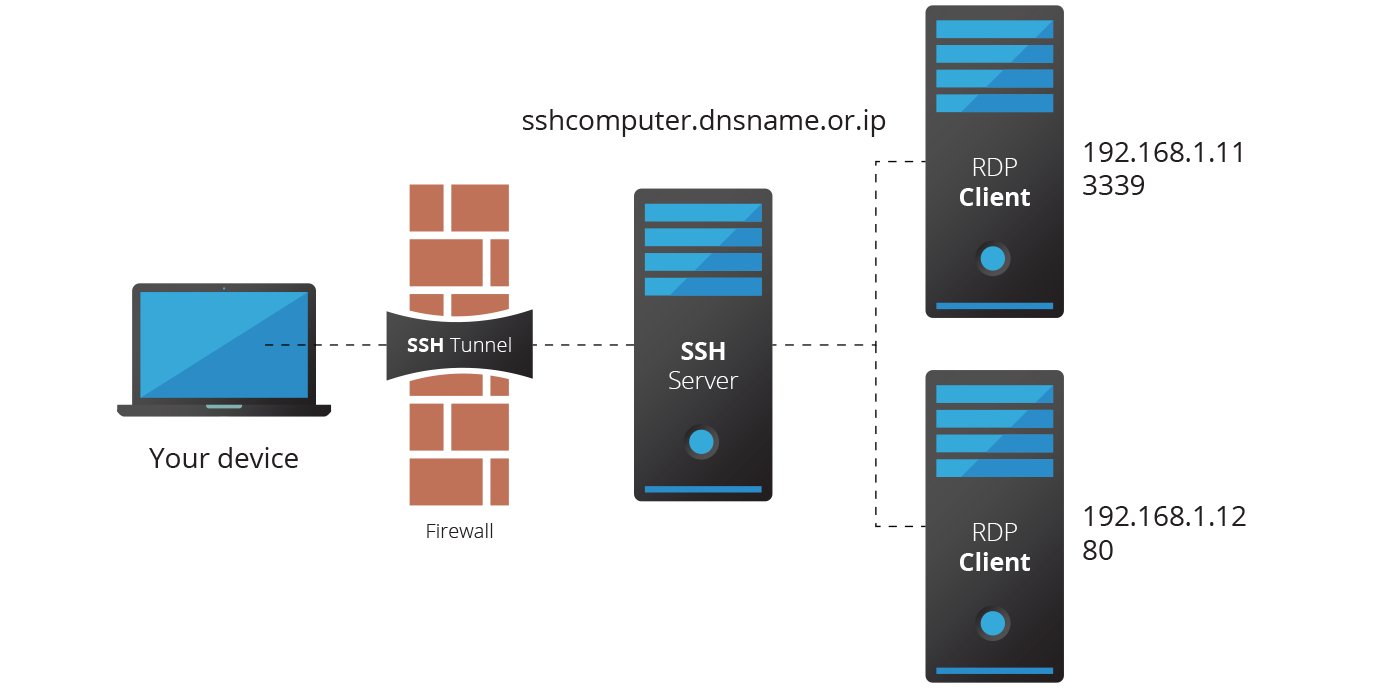
How do I connect to a remote server via SSH tunnel?
You can also connect to a remote server via SSH tunnel from a Windows machine by using PuTTY. In the PuTTY configuration window: Go to Connection -> SSH -> Tunnels. In the Source port field type in 5901. In the Destination field type in localhost:5901. Start the SSH session as you normally would.

How do I make SSH more secure?
10 Steps to Secure Open SSHStrong Usernames and Passwords. ... Configure Idle Timeout Interval. ... Disable Empty Passwords. ... Limit Users' SSH Access. ... Only Use SSH Protocol 2. ... Allow Only Specific Clients. ... Enable Two-Factor Authentication. ... Use Public/Private Keys for Authentication.
Is SSH a secure remote access protocol?
The SSH protocol (also referred to as Secure Shell) is a method for secure remote login from one computer to another. It provides several alternative options for strong authentication, and it protects the communications security and integrity with strong encryption.
Which mode is used to secure the SSH remote connection?
Using SSH to Securely Copy Files SSH handles the authentication and encryption. SFTP is an extension of the SSH protocol and requires an additional SFTP server on the server-side.
How do I setup a remote SSH server?
How to Connect via SSHOpen the SSH terminal on your machine and run the following command: ssh your_username@host_ip_address. ... Type in your password and hit Enter. ... When you are connecting to a server for the very first time, it will ask you if you want to continue connecting.More items...•
What is SSH remote access?
SSH or Secure Shell is a network protocol that connects users to a remote computer over a secure connection. This allows administrators and other authorized users to connect to secure computers over a network that is not secure, like the Internet. This is accomplished through the use of encryption.
What is the difference between SSL and SSH?
The key difference between SSH vs SSL is that SSH is used for creating a secure tunnel to another computer from which you can issue commands, transfer data, etc. On the other end, SSL is used for securely transferring data between two parties – it does not let you issue commands as you can with SSH.
What features of SSH makes it more secure?
SSH can increase the security of other TCP/IP-based applications such as telnet, ftp, and the X Window System. A technique called port forwarding or tunneling reroutes a TCP/IP connection to pass through an SSH connection, transparently encrypting it end to end.
Which one is more secure https or SSH?
While SSH is usually considered more secure, for basic usage of Github, HTTPS authentication with a password is acceptable enough. In fact, Github themselves defaults to and recommends most people use HTTPS.
How do I enable SSH?
Activate or deactivate the SSH serversudo rm -f /etc/ssh/sshd_not_to_be_run sudo systemctl enable ssh sudo systemctl start ssh.sudo mv /etc/init/ssh.conf.back /etc/init/ssh.conf sudo start ssh.sudo systemctl stop ssh sudo systemctl disable ssh.sudo stop ssh sudo mv /etc/init/ssh.conf /etc/init/ssh.conf.back.
What is required to establish an SSH connection?
To establish an SSH connection, you need a client machine and an agreeing server-side component. SSH enables a secure connection between these two. The application you install on the computer and connect to another computer is called an SSH client. The client uses the remote host information to start the connection.
What is SSH server used for?
SSH or Secure Shell is a network communication protocol that enables two computers to communicate (c.f http or hypertext transfer protocol, which is the protocol used to transfer hypertext such as web pages) and share data.
What is SSH config file?
Your SSH config file allows you to define specific settings for each SSH host that makes connecting to that host far easier. By defining many of these common, or uncommon, properties within the file, it eliminates the need to remember this parameter set each and every time a connection is needed.
What is the importance of using SSH in remote management and administration of network devices?
In addition to providing strong encryption, SSH is widely used by network administrators to manage systems and applications remotely, enabling them to log in to another computer over a network, execute commands and move files from one computer to another.
What is Identityfile in SSH?
Identity file is simply a private key (or cert), usually created by running ssh-keygen . This will by default create an RSA key, but you can change that with the -t option. According to your output, you have an RSA and an ECDSA key.
What port does SSH use?
port 22By default, the SSH server still runs in port 22.
What is the flag for SSH?
OpenSSH. This is a free implementation of ssh and uses the single command `ssh' only. If you want protocol 2, you use the flag `ssh -2'.
What is SSH client?
An SSH client is an application you install on the computer which you will use to connect to another computer or a server. The client uses the provided remote host information to initiate the connection and if the credentials are verified, establishes the encrypted connection.
What is needed to accept SSH connections?
In order to accept SSH connections, a machine needs to have the server-side part of the SSH software toolkit.
What is SSH?
Secure Shell, sometimes referred to as Secure Socket Shell, is a protocol which allows you to connect securely to a remote computer or a server by using a text-based interface.
How to get remote desktop on Windows 7?
You can find it in a couple of different ways: For Windows 7, click on Start -> All Programs, go to the ‘Accessories’ folder and click on Remote Desktop Connection.
What is the component of SSH?
On the server’s side, there is a component called an SSH daemon that is constantly listening to a specific TCP/IP port for possible client connection requests. Once a client initiates a connection, the SSH daemon will respond with the software and the protocol versions it supports and the two will exchange their identification data. If the provided credentials are correct, SSH creates a new session for the appropriate environment.
How to enable remote access in Windows 7?
Enabling Remote Access in Windows 7, 8, 10 and Windows Server Versions. Step 1: Allow Remote Connections. Step 2: Add Users to the List of Remote Users. How to Use the Remove Desktop Connection Client.
What is the protocol used to connect to a remote machine?
There are many ways to establish a connection with a remote machine depending on the operating system you are running, but the two most used protocols are: Secure Shell (SSH) for Linux-based machines. Remote Desktop Protocol (RDP) for Windows-based machines.
What is SSH authentication?
SSH uses either local security or the security protocol that is configured through AAA on your router for user authentication. When you configure AAA, you must ensure that the console is not running under AAA by applying a keyword in the global configuration mode to disable AAA on the console.
How many steps are required to enable SSH on Cisco router?
There are four steps required to enable SSH support on a Cisco IOS router:
How to prevent non-SSH connections?
If you want to prevent non-SSH connections, add the transport input ssh command under the lines to limit the router to SSH connections only . Straight (non-SSH) Telnets are refused.
What does show ssh mean?
show ssh âDisplays the status of SSH server connections.
What happens if you reject SSH?
If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Make sure you have specified a host name and domain. Then use the crypto key generate rsa command to generate an RSA key pair and enable the SSH server.
What is SSH in a network?
Secure Shell (SSH) is a protocol which provides a secure remote access connection to network devices. Communication between the client and server is encrypted in both SSH version 1 and SSH version 2. Implement SSH version 2 when possible because it uses a more enhanced security encryption algorithm. This document discusses how to configure and ...
Why isn't the connect button enabled?
The Connect button is not enabled if you do not enter the host name and username. This screenshot shows that the login banner is displayed when Secure Shell connects to the router. Then, the login banner password prompt displays. The PuTTY client does not require the username to initiate the SSH connection to the router.
Can you restrict access to specific networks?
You can also restrict access to only to specific networks/target hosts when connecting from the PrivX GUI to websites. Login as self to web target is possible if the user provides own credentials for the web service. Again, optional session recording is possible. If needed, additional PrivX Extender component can be used to access Web targets (as well as SSH and RDP targets) in a private network or virtual private clouds (VPC).
Can you share PrivX credentials?
So even when using shared accounts, the user cannot share any credentials to anyone else.
Who is Suvi Lampila?
Suvi Lampila is a Senior Technical Services Engineer at SSH.COM. Suvi has been with SSH since 2001 and she has held various positions in technical support, quality assurance and professional services both in Finland and Hong Kong.
Can you add videos to your watch history?
Videos you watch may be added to the TV's watch history and influence TV recommendations. To avoid this, cancel and sign in to YouTube on your computer.
Where do you generate SSH keys?
SSH keys should be generated on the computer you wish to log in from. This is usually your local machine.
What is SSH in Linux?
SSH, or Secure Shell, is a protocol used to securely log onto remote systems. It is the most common way to access remote Linux servers. In this guide, we will discuss how to use SSH to connect to a remote system.
How Does SSH Work?
SSH works by connecting a client program to an ssh server, called sshd.
How to uncomment password authentication?
Locate the line that reads Password Authentication, and uncomment it by removing the leading # . You can then change its value to no:
Why is SSH so popular?
SSH has remained popular because it is secure, light-weight, and useful in diverse situations.
Where is the sshd file located?
In Ubuntu, the main sshd configuration file is located at /etc/ssh/sshd_config.
Is it better to use passwords or key based authentication?
While it is helpful to be able to log in to a remote system using passwords, it’s a much better idea to set up key-based authentication.
What is SSH in Linux?
The SSH protocol is an encrypted protocol designed to give a secure connection over an insecure network, such as the internet. SSH in Linux is built on a portable version of the OpenSSH project. It is implemented in a classic client-server model, with an SSH server accepting connections from SSH clients. The client is used to connect ...
What port does SSH listen to?
In its default configuration, an SSH server will listen for incoming connections on Transmission Control Protocol ( TCP) port 22. Because this is a standardized, well-known port, it is a target for threat actors and malicious bots.
Why is there a limit on the number of authentication attempts?
Defining a limit on the number of authentication attempts can help thwart password guessing and brute-force attacks. After the designated number of authentication requests, the user will be disconnected from the SSH server. By default, there is no limit. But that is quickly remedied.
What does SSH stand for?
SSH stands for Secure Shell. The name “SSH” is used interchangeably to mean either the SSH protocol itself or the software tools that allow system administrators and users to make secure connections to remote computers using that protocol. The SSH protocol is an encrypted protocol designed to give a secure connection over an insecure network, ...
How to disable root login?
Disable Root Log Ins 1 If you want to prevent root from logging in at all, replace “prohibit-password” with “no”. 2 If you are going to allow root to log in but force them to use SSH keys, leave “prohibit-password” in place.
When was SSH updated?
In 2006, the SSH protocol was updated from version 1 to version 2. It was a significant upgrade. There were so many changes and improvements, especially around encryption and security, that version 2 is not backward compatible with version 1. To prevent connections from version 1 clients, you can stipulate that your computer will only accept connections from version 2 clients.
How to prevent root from logging in?
If you want to prevent root from logging in at all, replace “prohibit-password” with “no”.
What is SSH authentication?
SSH supports Authentication to reliably determine the identity of the connecting computer, encryption to scramble data so that only the intended recipient only can read it and Integrity to guarantees the data sent over the network is not changed by a third party. SSH has two main versions, SSH1 and SSH2.
What is SSH in network?
Network administrators must disable telnet and use only SSH wherever possible. SSH (Secure Shell) is a protocol which define how to connect securely over a network. SSH (Secure Shell) protocol provides the three main ideas of security authentication, confidentiality (via encryption) and integrity of data transfer over a network.
What port number does SSH use?
SSH uses TCP as its transport layer protocol and uses well-kown port number 22.
What is the default device name for RSA encryption?
Before generating RSA encryption keys, you must change the default hostname of a Cisco Router or Switch. The default device name of a Cisco Router is "Router" and default device name of a Cisco Switch is "Switch". You must configure a domain name also before generating RSA keys. Follow these Cisco IOS CLI commands to configure a hostname, ...
What is SSH on Cisco router?
The Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. The best-known example application is for remote login to computer systems by users.
What is SSH in network?
SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with an SSH server. Common applications include remote command-line login and remote command execution, but any network service can be secured with SSH.
Introduction
Prerequisites
Test Authentication
Optional Configuration Sets
Debug and Show Commands
Sample Debug Output
Tips
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configur…
- If your SSH configuration commands are rejected as illegal commands, you have not successfully generated a RSA key pair for your router. Ensure you have specified a host name and domain. Then use t...
- When you configure RSA key pairs, you can get these error messages:
- The number of allowable SSH connections is limited to the maximum number of vty configured for the router. Each SSH connection uses a vtyresource.
- SSH uses either local security or the security protocol configured through AAA on your router for user authentication. When you configure AAA, you must ensure that the console is not run under AAA....