
Can I connect remotely to a control system?
Connecting remotely to a control system has some specific considerations. There is existing literature on the topic of remote access to control systems, such as international standard IEC 62443-4-1:2018 and advice from ICS-CERT. This publication is broken into three sections:
Can industrial control system employees access SCADA from their phones?
Industrial control system (ICS) employees can access systems control and data acquisition (SCADA) systems from their phones. While remote access enables agility and fast response times, it also begets questions about cyber security.
How can remote users access Automation Components connected to the local router?
Once connected, remote users can access automation components connected to the local router through the VPN tunnel. Unlike option 1, there is no cloud server between the two devices with either method of connection: VPN router to VPN router, or VPN router to VPN software client.
How can industrial control systems ensure safety and integrity?
In the past decade, the connectivity level of industrial control systems has increased. In parallel with these digital transformations, ensuring the safety and integrity of these environments is imperative. Previously isolated infrastructure is now easily accessible via remote tools.
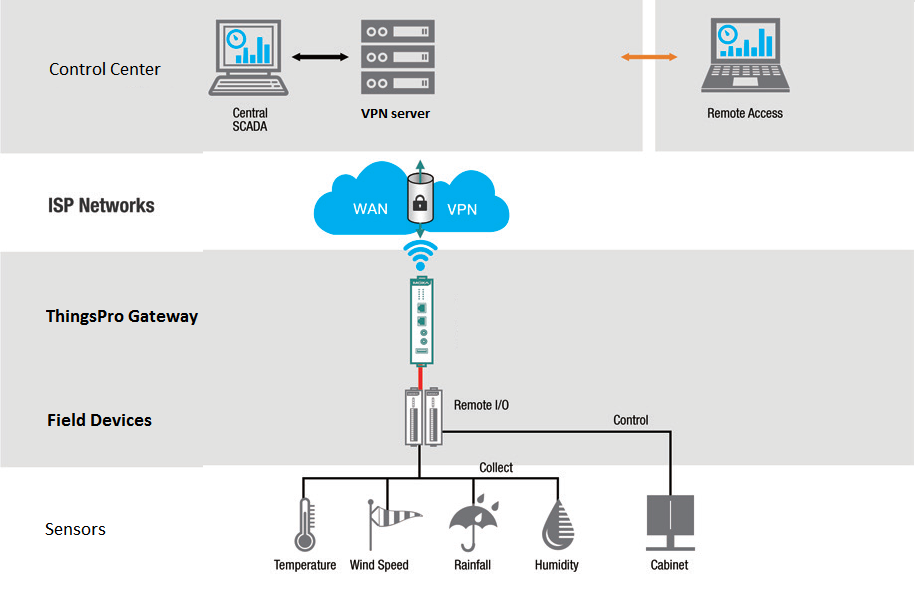
What is remote access management?
Remote access control refers to the ability to monitor and control access to a computer or network (such as a home computer or office network computer) anywhere and anytime. Employees can leverage this ability to work remotely away from the office while retaining access to a distant computer or network.
What are the different types of remote access methods?
Types of remote access: virtual private network. SaaS remote desktop tools. common remote service ports.
What is a preferred security measure for remote access?
Virtual Private Networking (VPN) is often considered the best approach in securing trans-network communication.
What are the five elements of a remote access security readiness review?
The review examined cybersecurity at the governance layer and identified five critical pillars key to cybersecurity readiness: culture, people, structure, processes, and resources.
Which technology is used in remote access?
virtual private network (VPN) technologyRemote access software is usually accomplished using a virtual private network (VPN) technology. This type of method is more available compared to others since it is a more secure remote access software that connects the user and the enterprise's networks through an internet connection.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
How do I setup a secure remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
What is required for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
How do I ensure secure remote access?
How to Ensure Secure Remote Access for Work-from-Home EmployeesIssue Secure Equipment to Remote Employees.Implement a Secure Connection for Remote Network Access.Supply a VPN for Secure Remote Access.Empower Remote Employees through Education and Technology.
What are the four basic elements of a remote access policy?
Remote access policies consist of the following elements: conditions, permissions, and profiles. We'll discuss each of these elements in turn, and list how each can be used to control remote access attempts by your network clients.
What are the examples of remote user security policy best practices?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
What cryptographic methods can be used in securing remote work setups?
Virtual Private Network Usually, there are two choices when using VPNs: IP Security (IPsec) or Secure Sockets Layer (SSL). IPsec VPNs are manually installed and configured on the remote device.
What is a security management solution for remote access?
Security management of the remote access solution should follow defence-in-depth techniques with multiple layers of defence and should incorporate best-of-breed elements from standards. Although not an exhaustive list, the following are examples of layered defence techniques in relation to remote access:
Why is remote access important?
Because securing remote access is an integral part of any defence-in-depth strategy, the foundation of creating usable guidance as it pertains to control systems environments must include both users and the technology to be accessed remotely. To generalise control system architectures is difficult and to develop a recommended practice for securing remote access that is applicable to all architectures is impossible. It may help organisations to shape their remote access strategy by determining who requires access to certain resources as well as understanding attack vectors that can be created unintentionally.
Why is industrial control important?
Today, business demand has led to the rapid deployment of modern networking technologies, which has accelerated the interconnectivity of these once isolated systems. This new connectivity has empowered asset owners to maximise business operations and reduce costs associated with equipment monitoring, upgrading and servicing, whilst creating a new security paradigm for protecting control systems from cyber incident.
Is remote access secure?
In conclusion, no single secure remote access solution is applicable to all possible architectures and no single remote access solution can provide adequate security without a defence-in-depth approach. However, by exercising caution and generating and implementing concise requirements based on good analysis, secure remote access solutions can be deployed and maintained.
EXECUTIVE SUMMARY
We rely on industrial control systems to sustain our lives; from utilities to manufacturing, to distribution, to water management. In the past decade, the connectivity level of industrial control systems has increased. In parallel with these digital transformations, ensuring the safety and integrity of these environments is imperative.
Industrial control system security: Notable vulnerabilities
1. Connectivity and integration with external platforms and third party systems provide opportunities for backdoor access and malicious activities.
Preventing industrial control system attacks
In the US, the Cybersecurity and Infrastructure Security Agency (CISA) provides information designed to empower industry leaders to combat ICS oriented threats.
Why do external parties need to connect remotely to critical infrastructure control networks?
This access is to allow the manufacturers of equipment used in Australia’s critical infrastructure the ability to maintain the equipment, when a fault is experienced that cannot be fixed in the required timeframe any other method.
What should be the default communication between the vendor and the critical infrastructure control system?
1. By default, there should be no communication between the vendor and the critical infrastructure control system.
What is the Australian Government Information Security Manual?
The Australian Government Information Security Manual is a cyber security framework that organisations can apply to protect their systems and data from cyber threats. The advice in the Strategies to Mitigate Cyber Security Incidents, along with its Essential Eight, complements this framework.
Which end should authenticate the critical infrastructure organisation?
10. The remote end should authenticate the critical infrastructure organisation also, i.e. ‘mutual authentication’.
Why do external parties need to connect remotely?
External parties may need to connect remotely to critical infrastructure control networks. This is to allow manufacturers of equipment the ability to maintain the equipment when a fault is experienced that cannot be fixed in the required timeframe. Such access to external parties will only occur in extraordinary circumstances, ...
When must remote access data be returned?
Ensure contractually that any data viewed or acquired as part of the remote access is used only for the purpose of resolving the issue the remote access was granted for, and must be returned to the critical infrastructure organisation and destroyed at the remote access end either when the issue is resolved, or after the period of 1 year , whichever is sooner.
When should the connection between the control network and any external device be physically disconnected?
2. The connection between the control network and any external device should be physically disconnected when the protocol is not being used. Ideally this would mean removal of a physical cable, however sometimes the location to disconnect the cable may be a significant distance from the control equipment.
What is industrial control system?
Industrial control systems (ICSs), sometimes referred to as operational technology (OT), are the workhorses for manufacturing and critical infrastructure. They control processes for continuous production (e.g., electricity) and unit production (e.g., automobiles). Industrial control systems have been around for more than 50 years, ...
How long have industrial control systems been around?
Industrial control systems have been around for more than 50 years, but within that period of time, the operating paradigm has changed, which highlights the need for OT-based cybersecurity. configuration control and how it secures ICSs.
What is controller code verification?
c. Full controller code verification: Involves nonintrusive and periodic device integrity checks to verify controller code and configuration information. This typically is performed through active querying technology, which enables authorized personnel to periodically query controllers for their codes and configuration for change management. It identifies changes to each controller’s metadata and backplane, including firmware versions and configuration details, as well as changes in the code and critical memory segments. The frequency and timing of controller code verification should be completely user configurable. An option should exist to either automatically or manually run these device checks.
What is controller baselining?
b. Controller baselining and versioning: Sets a baseline configuration to compare changes while tracking all code versions for quicker incident response. This involves extracting, backing up, and storing code snapshots. With the information gleaned from this operation, you will be able to compare versions down to the rung, routine, or code block level, depending on the programming language. The user can set a specific code version as the baseline and receive alerts upon a change.
What is a PLC?
The core of any OT infrastructure is the programmable logic controller. Much like its namesake, a PLC controls the industrial or manufacturing process. It tells robotic arms how to fabricate units (like an automobile) or defines how to transfer a load to meet demand (as in the case of an electrical generating plant). Defeating a PLC gives an attacker complete control over operations, which is also why PLCs are the prime target for OT attacks or incursions.#N#There are many types of programming changes bad actors can make to PLCs. Some of these changes may consist of: 1 adding in unauthorized commands and processes 2 deleting/ignoring a manufacturing or production process command 3 speeding up or slowing down a process or activity 4 changing upper or lower tolerance thresholds 5 changing a process value 6 creating an unsustainable process that results in damage and shutdown 7 gaining ownership of the process or facility 8 making changes to the operation of the PLC while masking the change.
Is it possible to manually manage a controller?
As industrial processes get more complex, manually managing the code and configuration changes on controllers is virtually impossible. Should the worst happen, having the last known good configuration of all industrial devices is paramount. To enable effective backup and recovery, you need reliable tracking and control of all hardware and configuration changes. For more information regarding OT security visit the Industrial Cybersecurity eBook.
Option 1: Hosted VPN
Hosted VPNs provide a secure connection with simple setup and network configuration. Typical hosted VPN solutions include a VPN router, a hosted VPN server, a VPN client, and connected automation system components (figure 2).
Hosted VPN design considerations
Those considering this solution must have a high level of trust in the hosted VPN vendor, as it will be responsible for securely storing data and making it available to only those who need it. Monthly costs incurred for high data bandwidth usage must also be considered, particularly as those costs are zero for a traditional VPN solution.
Option 2: Traditional VPN
This option requires a local VPN router to connect through the Internet with a secure VPN tunnel to a second remote VPN router or software client (figure 5). Once connected, remote users can access automation components connected to the local router through the VPN tunnel.
Traditional VPN design considerations
The main design consideration for this option is the capability and willingness of an IT team to support this solution at both the local and remote sites for each installation.
Application example: Traditional VPN
Consider two types of OEM machine builders. The first OEM sells very large and complex printing presses with thousands of automation system I/O points, and its customers require the OEM to support the machine, including uptime and throughput guarantees.
Application example: Hosted VPN
The second OEM sells a machine that does not require video monitoring. Local operator interface is provided by an embedded HMI with limited data logging and storage functionality. The OEM machine builder needs two kinds of remote access. The first is VPN access to remotely troubleshoot, debug, and program the machine’s PLC and HMI.
Many considerations
When designing a remote access solution using VPNs, there are many considerations influencing final implementation: initial and sustaining costs, technical expertise during installation and ongoing operation, site control, security risks, and data storage capabilities.
