
Top 5 Considerations for Secure Remote Access Control.
- 1. Use the Zero-Trust Model. A zero-trust model limits the access of information to employees on a need-to-know basis. So, if an employee doesn’t need ...
- 2. Protect All Endpoints (Including Servers and Other Critical IT Infrastructure)
- 3. Raise Cybersecurity Awareness Among Employees.
- 4. Protect Data in Transit.
- 5. Set Up a Secure Network Connection.
- Lack of information. ...
- Password sharing. ...
- Software. ...
- Personal devices. ...
- Patching. ...
- Vulnerable backups. ...
- Device hygiene. ...
- Phishing attacks.
What is remote access without technical configuration?
Plug and play remote access without technical configuration: In a cloud-based remote access solution, security parameters-such as hash functions, encryption/decryption algorithms, etc.-are configured automatically. Machine builders do not need to configure these parameters; they just need to click on a button to establish a remote connection.
Why OEMs and machine builders need remote access solutions?
Conclusion: OEMs and machine builders require a secure, easy-to-use, and scalable remote access solution to enable on-demand remote access to their machines deployed in the field. Traditional VPN and RDC solutions are cumbersome and require IT/networking knowledge as well as changes in security/firewall policies.
What are the benefits of cloud-based remote access solutions?
a) End-to-end encryption prevents data leaks: Cloud-based remote access solutions provide end-to-end data encryption between a piece of remote equipment and an engineer’s PC. The cloud server only routes the traffic and does not decrypt or store the data that is passing through.
What do I need to set up a remote key exchange?
Multiple parameters, including IP address, domain name, key ID, authentication mode, a suitable encryption algorithm, and an efficient hash function, all need to be configured to properly establish connectivity with remote machines and to be able to exchange the necessary authentication keys and data.

What do you need to consider when determining your remote access needs?
You should consider these security factors when making your decision: Prompt, automated security updates and patches. Multi-level authentication and authorization steps each time users log in on any device. End-to-end encryption of all connections.
What should a remote access policy consider?
A remote access policy should cover everything—from the types of users who can be given network access from outside the office to device types that can be used when connecting to the network. Once written, employees must sign a remote access policy acceptance form.
What are security considerations for remote users examples?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What constraints are available for use in a remote access policy?
Once a remote access policy has authorized a connection, it can also set connection restrictions (called constraints) based on the following: Encryption strength. Idle timeout. IP packet filters.
Why is remote access important?
With remote access, employees can safely work from any device, platform, or network at their home office or abroad. Remote desktop functions allow them to remotely access important files and share their screen for meetings and troubleshooting.
Is IT safe to allow remote access?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
What are the security considerations?
The Security Considerations Assessment (SCA) process ensures security-related vulnerabilities are considered across a range of activities and processes within an organisation. This includes physical, personnel, cyber and cross-cutting security measures.
What is the risk of remote access?
The overriding risk of remote access services and software is a hacker gaining deeper access to your organization, exposing you to a host of IT security threats. Once they gain privileged access to your system, it will be difficult to prevent data loss, prevent phishing, protect against ransomware, etc.
What are the most common remote work security risks?
Top Security Risks of Remote WorkingGDPR and remote working. Remote work means an employer has less control and visibility over employees' data security. ... Phishing Emails. ... Weak Passwords. ... Unsecured Home Devices. ... Unencrypted File Sharing. ... Open Home WiFi Networks.
Which of the following is a method of controlling remote access?
VPNs use the Internet to connect remote sites and users and use encryption and tunneling techniques to access a company's network. This option is ideal for smaller organizations.
Which helps a user to have remote access to an application from a server?
Internet Proxy Servers: Internet proxy servers are used to facilitate a connection outside of a corporate network or firewall. Though this option is instrumental when it comes to creating outside connections, a remote access connection is usually made over a secure VPN.
What is a remote access domain?
... is the domain in which a mobile user can access the local network remotely, usually through a VPN (Figure 7). ...
What does a network policy include?
Network policies are sets of conditions, constraints, and settings that allow you to designate who is authorized to connect to the network and the circumstances under which they can or cannot connect.
Which of the following is a method of controlling remote access?
VPNs use the Internet to connect remote sites and users and use encryption and tunneling techniques to access a company's network. This option is ideal for smaller organizations.
What is access policy?
An AccessPolicy defines the permissions and duration of access to an Asset. This topic gives an overview of the AccessPolicy entity and also demonstrates how to execute various operations with the Media Services REST API.
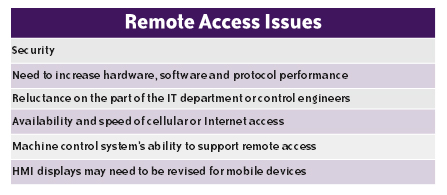
Security Considerations for Remote Access
Recent ransomware attacks have put the spotlight on potential security vulnerabilities of some industrial Remote Access solutions. Around the world, users are scrambling to understand and mitigate these vulnerabilities.
Workgroup Methodology
The material in this document is from direct member comments. Identities are not revealed to allow for a free flow of opinions and observations from direct experience.
What the members say
"A solid disaster recovery policy should also be developed (backup/restore) to allow a system to be returned to a known state quickly if the security controls don’t prevent an attack."
1. Define Your Goals
Identify who needs access and what, specifically, they need access to.
2. Select Your Solution
There are a million ways to set up remote access, from a technical standpoint. So, which one is right for you? When choosing a platform, consider the following four aspects:
3. Plan Your Attack
Before you install the new system, you’ll want to lay out a clear, precise plan with as much advance notice as possible.
4. Execute the Plan
While most people think the execution is the bulk of the work, if you have done well in your planning process, this step should be the easiest.
Why is remote access not required?
Remote access to machines and equipment is typically not required on a continuous basis and hence can be used on an as-needed basis to minimize security issues and reduce costs , especially in cases where remote connectivity is based on a volume-dependent pricing option, such as with cellular technology.
What is remote access for machine builders?
Some machine builders have adopted traditional remote access methods such as Virtual Private Networking (VPN) and Remote Desktop Connection (RDC) to improve their service levels and to provide quick response times for their customers. However, these traditional remote access solutions have various limitations and constraints that prevent machine builders from achieving their maximum service potential.
What is cloud based remote access?
Cloud-based remote access is a new type of remote access solution that enables flexible remote access to field machines. The network topology of a cloud-based remote access solution is composed of three components: a remote gateway, a cloud server, and client software. Remote gateways are connected to field equipment in order to remotely access and control them. Client software is installed on the engineer’s PC or desktop. The cloud server can be installed on a cloud-based platform such as Amazon Web Services or Microsoft Azure. The remote gateway and client software will both initiate outbound secure connection requests to the cloud server.
What is VPN and RDC?
VPN and RDC solutions can facilitate secure connections to remote machines. However, many of these solutions lack the flexibility or the intelligence to meet the specific needs of industrial machine builders. The five key elements that such machine builders have to consider when they use VPN and RDC solutions are: ...
How to achieve a higher level of security?
One way to achieve a higher-level of security is to have different pre-shared keys or X.509 certificates for each VPN tunnel. When the number of VPN tunnels/connections required are few, it is easy to manage the keys or certificates for these connections. However, as the number of VPN tunnels grows, it becomes very hard to manage these keys and certificates. When VPN servers or client systems are changed, certificates have to be regenerated. When a certificate expires, a new certificate has to be assigned and reloaded to the system, which further complicates maintenance.
What is a RDC?
Virtual Private Networking (VPN) and Remote Desktop Connection (RDC), the latter of which uses Virtual Network Computing (VNC), are two common methods used to remotely access machines and equipment at field sites.
Does VPN have a limit?
VPN servers typically have a limitation on the number of VPN tunnels they can support. When a business grows, more and more machines and devices are connected to the network with an increasing number of engineers supporting business operations. This leads to an increase in the number of VPN connections required.
What to do if you cannot control all aspects of the administration of a user request?
If you cannot control all aspects of the administration of a user request, at least you will have a record of it for auditing and reporting. Update your firewall policies with the service ticket number and review by date. Audit what a user has access to before you allow them to work from home.
What is the first mismanaged area in IAM?
The daily disciplined administration of users is usually the first mismanaged area in IAM when a crisis hits. IT teams become reactive to “fires” and simply do not proactively manage some of the most critical aspects of operations, such has who has access and why. The best solution to this type of situation is to try and automate administration as much as possible, so that enforcement and security risks do not get overlooked that may increase security costs and risks:
Threats
- Where do threats come from? The paper discusses some of the major vectors: 1. Insiders 2. Hacktivists 3. Cybercriminals 4. Terrorists 5. Enthusiasts 6. Nation-states Each type of threat actor is discussed in the guide. While we generally think of hackers trying to steal IP or money, the threats could just as easily be accidental operations by employees. A technician accidentally ca…
External Connections
- The External Connections section focuses on some of the common connection methods in use today: 1. Cell modems – Generally some form of direct connection into a machine over a cellular network. This could be a direct cellular gateway or a technician tethering their maintenance laptop to their cellphone. 2. VPN – Virtual Private Network is a tunnel through the plant firewall. This re…
Challenges Inside The OT Network
- Now that you’ve opened your network for remote access, there are risks to be considered: 1. Can an external user accidentally introduce malware to your system? 2. What if they access and download to the wrong equipment or, worse, download a dangerous change that could injure someone? 3. HMI devices have been running variants of Windows for 20+ year...
Policies and Procedures
- This section covers some of the ways you can mitigate the challenges in the previous section. This covers the following concepts and more: 1. Zero trust – Every point of access must require authentication. There is no more leaving the barn door open as soon as you’ve entered the one shared password that gets you into the network. 2. Limit accessibility – The access should be fo…
Summary
- There is no one right way to go about remote access, much less, cybersecurity as a whole. The methodology for your organization might be obvious to you and your team. Even obvious solutions can be difficult to implement, and DMC can helpyou improve your remote access capabilities and processes. Learn more about DMC's cybersecurity expertise.