Configure a VPN
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
Full Answer
How to configure VPN device tunnels in Windows 10?
Configure VPN device tunnels in Windows 10 1 Device Tunnel Requirements and Features. You must enable machine certificate authentication for VPN connections and define a root certification authority for authenticating incoming VPN connections. 2 VPN Device Tunnel Configuration. ... 3 Deployment and Testing. ... 4 Additional Resources. ...
Why do I need Two VPN tunnels for site-to-site?
It is important to configure both tunnels for redundancy. When one tunnel becomes unavailable (for example, down for maintenance), network traffic is automatically routed to the available tunnel for that specific Site-to-Site VPN connection. The following diagram shows the two tunnels of the Site-to-Site VPN connection.
What happens when one VPN tunnel becomes unavailable?
When one tunnel becomes unavailable (for example, down for maintenance), network traffic is automatically routed to the available tunnel for that specific Site-to-Site VPN connection. The following diagram shows the two tunnels of the Site-to-Site VPN connection.
Why is it important to configure both tunnels for redundancy?
It is important to configure both tunnels for redundancy. When one tunnel becomes unavailable (for example, down for maintenance), network traffic is automatically routed to the available tunnel for that specific Site-to-Site VPN connection.

How do I create a VPN tunnel?
In the Google Cloud console, go to the VPN page. ... Click Create VPN tunnel.From the drop-down menu, select the gateway that requires the second tunnel, and then click Continue.Choose a Cloud Router. ... For Peer VPN gateway, select On-prem or Non Google Cloud.More items...
What are 3 types of VPN tunnels?
We'll look at three of the most common: IPsec tunnels, Dynamic multi point VPNs, and MPLS-based L3VPNs.IPsec Tunnels. In principle, a network-based VPN tunnel is no different from a client-based IPsec tunnel. ... Dynamic Multi point VPN (DMVPN) ... MPLS-based L3VPN.
What is a VPN tunneling?
A VPN is a secure, encrypted connection over a publicly shared network. Tunneling is the process by which VPN packets reach their intended destination, which is typically a private network. Many VPNs use the IPsec protocol suite. IPsec is a group of protocols that run directly on top of IP at the network layer.
What are the 2 types of tunneling in VPNs?
What are the different types of VPN tunnel protocols?PPTP. You can thank Microsoft for PPTP (Point-to-Point Tunneling Protocol). ... L2TP/IPsec. ... OpenVPN.
Can a VPN tunnel be hacked?
Their success comes from a combination of technical trickery, computing power, cheating, court orders, and behind-the-scenes persuasion. VPNs can be hacked, but it's hard to do so. Furthermore, the chances of being hacked without a VPN are significantly greater than being hacked with one.
What are the 4 types of VPN?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs....How Personal VPNs WorkInstall software from your VPN service provider onto your device. ... Connect to a server in your VPN provider's network.More items...•
How does site to site VPN tunnel work?
A site-to-site Virtual Private Network (VPN) provides this by creating an encrypted link between VPN gateways located at each of these sites. A site-to-site VPN tunnel encrypts traffic at one end and sends it to the other site over the public Internet where it is decrypted and routed on to its destination.
Which tools are tunneling protocols?
Tunneling protocols, such a GRE and L2TP, are common tools for interconnecting two similar networks over a different network.
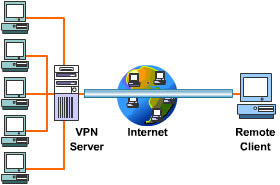
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
Why do we need VPN tunnel?
A VPN tunnel — short for virtual private network tunnel — can provide a way to cloak some of your online activity. How? A VPN tunnel connects your smartphone, laptop, computer, or tablet to another network in which your IP address is hidden and all the data you generate while surfing the web is encrypted.
How secure is a VPN tunnel?
A VPN tunnel is an encrypted connection between your device and a VPN server. It's uncrackable without a cryptographic key, so neither hackers nor your Internet Service Provider (ISP) could gain access to the data. This protects users from attacks and hides what they're doing online.
What is VPN and its types?
Virtual Private Network (VPN) is basically of 2 types: Remote Access VPN: Remote Access VPN permits a user to connect to a private network and access all its services and resources remotely. The connection between the user and the private network occurs through the Internet and the connection is secure and private.
What type of VPN is AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
What is a B2B VPN tunnel?
A cost-effective way to setup these connections is to create a business to business virtual private network also known as a B2B VPN. VPN is a technology that allows for two geographically separate networks to connect and share data across insecure networks like the Internet.
Which type of VPN is best?
The Best VPN Service for 2022NordVPN - Best VPN for Privacy.Surfshark - Best VPN for Security.Private Internet Access VPN - Best VPN for Windows.IPVanish - Best VPN for Android.Ivacy - Most Affordable.Atlas VPN - Best Data Breach Monitoring.ExpressVPN - Best Encryption.PureVPN - Best Server Base.More items...
What is a full tunnel VPN?
Full Tunnel (recommended) routes and encrypts all request through the VPN regardless of where the services is hosted. Prevent man-in-the-middle attacks. Make sure your VPN has a certificate. This helps validate that users are connecting to the correct VPN gateway and not a malicious site.
What is Remote Access VPN?
A remote access VPN (Virtual Private Network) enables users to access enterprise applications that reside in the corporate data center or headquarters remotely. All the traffic is encrypted, making sure that communication is not compromised. Think of it as a virtual cable that is connecting the remote user directly to the data center.
Is VPN safe for enterprise?
Depending on your firewall software release you might be limited to lower encryption and hashing algorithms, which would make your VPNs less safe. Most importantly , the enterprise could be exposed to known vulnerabilities. How many users does your device support? VPN support is dependent on hardware.
What are the advantages of a stand alone VPN?
How healthy the budget is might determine that. One of the advantages of purchasing a stand alone specialty VPN appliances is that ' typically ' they might have more flexibility when it comes to user policy and security settings. Some appliances also might have more robust client applications.
Why is SSL VPN called SSL VPN?
I believe the name SSL VPN came back from the inception of the concept because users would connect via a web browser using SSL to a web page to login. Although the web page based VPN method is still used, most vendors have released client applications that install on a computer which facilitates the secure connection.
Is remote access part of a business continuity plan?
In general remote access should be a part of a business continuity plan. That alone could be the reason you justify deployment, which would mean you'd need to ensure there is some language about remote access and how the design works to meet the BC plan needs.
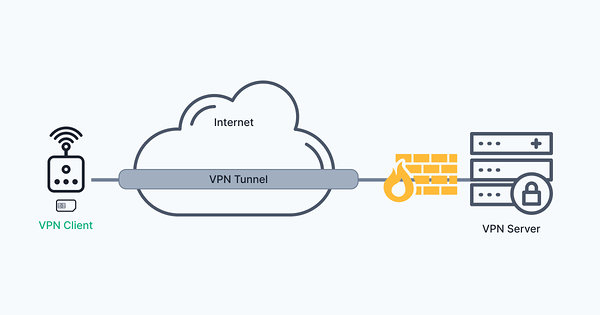
What is a VPN Tunnel?
When you connect to the internet with a VPN, it create s a connection between you and the internet that surrounds your internet data like a tunnel, encrypting the data packets your device sends.
What is the most common VPN protocol?
Let’s take a closer look at them. 1. PPTP. Point to Point Tunneling Protocol (PPTP) is one of the oldest protocols still being used by VPNs today.
What is OpenVPN encryption?
OpenVPN. Saving the best for last, we have OpenVPN, a relatively recent open source tunneling protocol that uses AES 256-bit encryption to protect data packets. Because the protocol is open source, the code is vetted thoroughly and regularly by the security community, who are constantly looking for potential security flaws.
What is L2TP in IPSec?
Layer 2 Tunneling Protocol (L2TP) is used in conjunction with Internet Protocol Security (IPSec) to create a more secure tunneling protocol than PPTP. L2TP encapsulates the data, but isn’t adequately encrypted until IPSec wraps the data again with its own encryption to create two layers of encryption, securing the confidentiality of the data packets going through the tunnel.
Which VPN is the best to keep your internet secure?
OpenVPN, with its open source code, strong encryption, and ability to bypass firewalls, is the best tunneling protocol to keep your internet data secure. While it requires third-party software that isn’t available on all operating systems, for the most secure VPN connection to the internet, you’ll want to use the OpenVPN protocol.
Is PPTP the fastest VPN?
PPTP is one of the easiest protocols to configure, requiring only a username, password, and server address to connect to the server. It’s one of the fastest VPN protocols because of its low encryption level. While it boasts fast connection speeds, the low level of encryption makes PPTP one of the least secure protocols you can use ...
Is L2TP/IPSEC faster than PPTP?
This double encapsulation does, however, make it a little slower than PPTP. It can also struggle with bypassing restrictive firewalls because it uses fixed ports, making VPN connections with L2TP easier to block. L2TP/IPSec is nonetheless a very popular protocol given the high level of security it provides.
How to configure VPN tunnel?
You can configure device tunnels by using a Windows PowerShell script and using the Windows Management Instrumentation (WMI) bridge. The Always On VPN device tunnel must be configured in the context of the LOCAL SYSTEM account. To accomplish this, it will be necessary to use PsExec, one of the PsTools included in the Sysinternals suite of utilities.
What VPN feature can be configured with the device tunnel?
Depending on the needs of each particular deployment scenario, another VPN feature that can be configured with the device tunnel is Trusted Network Detection.
What is always on VPN?
Always On VPN gives you the ability to create a dedicated VPN profile for device or machine. Always On VPN connections include two types of tunnels: Device tunnel connects to specified VPN servers before users log on to the device. Pre-login connectivity scenarios and device management purposes use device tunnel.
What is a user tunnel?
User tunnel connects only after a user logs on to the device. User tunnel allows users to access organization resources through VPN servers.
Can you use traffic filters in Windows Remote Management?
For server-initiated push cases, like Windows Remote Management (WinRM), Remote GPUpdate, and remote Configuration Manager update scenarios – you must allow inbound traffic on the device tunnel, so traffic filters cannot be used. If in the device tunnel profile you turn on traffic filters, then the Device Tunnel denies inbound traffic. This limitation is going to be removed in future releases.
Can you use a device tunnel on Windows 10?
Device tunnel can only be configured on domain-joined devices running Windows 10 Enterprise or Education version 1709 or later. There is no support for third-party control of the device tunnel. Device tunnel does not support using the Name Resolution Policy table (NRPT). Device tunnel does not support Force tunnel.
Do you need a certificate for VPN?
You must enable machine certificate authentication for VPN connections and define a root certification authority for authenticating incoming VPN connections.