
- Log into NCOS. For help with logging in see NCOS: Accessing the Setup Pages of a Cradlepoint router.
- Click on Networking, select Tunnels, and then select IPSec VPN.
- Click the Global Settings tab, select Enable VPN Service, and then click Save.
- Click the Tunnels tab, and then click Add.
How do I connect a computer to a Cradlepoint router?
- Log into the router’s NCOS Page. For help with logging in please view NCOS: Accessing the Setup Pages of a Cradlepoint router.
- Click Connection Manager on the navigational pane.
- Select the EVDO Modem, click Control.
- Click the Activate.
How to set up a Cradlepoint router?
NCOS: How to setup a Cradlepoint router to send info to a Syslog Server
- Log into the router's NCOS Page. For help with logging in see NCOS: Accessing the Setup Pages of a Cradlepoint router.
- Navigate to SYSTEM > Administration > System Logging. Figure 1: Path to System Logging Page
- Select Enable Logging to a Syslog Server to send log messages to a specified Syslog server.
- Select a Logging Level. ...
How to set up Cradlepoint?
How do I set up the CradlePoint AER 2100?
- Basic AER2100 Setup Instructions. Insert an activated SIM. ...
- Accessing the Administration Pages. Once you are connected, open the Cradlepoint AER2100’s GUI-based administration pages to make configuration changes to your router.
- First Time Setup Wizard. ...
- Using NetCloud Manager. ...
How do I setup VPN on my router?
- Pick a VPN provider that is compatible with your router. ...
- Find out your router’s IP address. ...
- Visit that IP address in your web browser
- Log in to your router’s software with the correct credentials
- Get the OpenVPN configuration files from your VPN service and set up your router by following their guides
- Test the connection to verify that everything works
How do I access Cradlepoint remotely?
Complete the following steps to remotely access the local user interface of a Cradlepoint device:Log into NetCloud Manager.Click DEVICES on the left-side navigation panel.Select the device to whose local user interface you want to connect.Click Remote Connect.Select Connect to Device UI.
Is Cradlepoint a VPN?
CradlePoint VPN tunnels use IPsec (Internet Protocol security) to authenticate and encrypt packets exchanged across the tunnels. To set up a VPN tunnel with a CradlePoint router on one end, there must be another device (usually a router) that also supports IPsec on the other end.
What is IP passthrough Cradlepoint?
IP Passthrough mode, simply stated, disables the router functionality and provides the cellular WAN address directly to one attached network client. A new Cradlepoint device will display the "First Time Setup Wizard" the first time you connect to the modem.
How do I connect to Cradlepoint locally?
Click START.Click CONTROL PANEL.Click NETWORK AND INTERNET.Click CONNECT TO A NETWORK (under network and sharing center) You'll see a list of available wireless networks.Click the CradlePoint Network.Click CONNECT.
How do I set up IPsec tunnel cradlepoint?
ConfigurationLog into NCOS. For help with logging in see NCOS: Accessing the Setup Pages of a Cradlepoint router.Click on Networking, select Tunnels, and then select IPSec VPN.Click the Global Settings tab, select Enable VPN Service, and then click Save.Click the Tunnels tab, and then click Add.
What is Auto VPN?
Auto VPN is a proprietary technology developed by Meraki that allows you to quickly and easily build VPN tunnels between Meraki MX devices at your separate network branches with just a few clicks. Auto VPN performs the work normally required for manual VPN configurations with a simple cloud based process.
When should I use IP passthrough?
IP Passthrough on a router from an ISP means the router bridges all traffic through to whatever is on the other side (whatever device is connected to the routers LAN port). This is useful if you have a device connected to the router and you want the global IP address from WAN on the router.
Is IP passthrough the same as bridge mode?
IP pass-through works essentially the same as the bridged mode where customer can use their own router behind the ISP-provided gateway. However, in IP pass-through mode the signal is terminated (bridge mode signal is not terminated) at the gateway and allows the ISP to connect to the gateway with its own IP.
What is the purpose of IP passthrough?
The IP Passthrough feature allows a single PC on the LAN to have the Router's public address assigned to it. It also provides Port Address Translation (PAT)–Network Address Port Translation (NAPT) via the same public IP address for all other hosts on the private LAN subnet.
How do I find my Cradlepoint IP address?
Look at the sticker on the device, note the MAC Address.Connect Ethernet Cable to Ethernet Port on Windows PC.Connect other end of Ethernet Cable to LAN Port on Cradlepoint Device.Open Windows Command Prompt.Type " arp -a " and press " enter/return " on your keyboard.More items...•
How does Cradlepoint hotspot work?
Adapters receive signals from wireless routers or similar wireless devices and translate them so that users can access the Internet if they are in the range of a wireless network or a WiFi hotspot. Cradlepoint's W4005 Series 5G adapter offers dual connectivity, LAN connectivity, and throughput of 2 Gbps.
How do I connect to Cradlepoint WiFi?
0:031:13Cradlepoint Support - WiFi as WAN - YouTubeYouTubeStart of suggested clipEnd of suggested clipSet the Wi-Fi client mode to wireless as when scroll down to the side survey section and click theMoreSet the Wi-Fi client mode to wireless as when scroll down to the side survey section and click the refresh button to update the list of wireless networks in range.
What is NetCloud perimeter?
NetCloud Perimeter provides a simple, cloud-based alternative to VPN. It allows companies to build and deploy virtual overlay networks in minutes, connecting all their IoT devices and remote and mobile workers to business-critical resources.
Which settings must be matched exactly between the two ends of the ipsec tunnel to ensure a stable VPN connection?
Pre-Shared Key (PSK) – A common key that must match on both ends of the tunnel. Protocol – The upper-layer protocol to match. The following protocols can be set: ICMP, TCP, UDP, GRE or Any.
What is hub and spoke VPN?
Hub and spoke VPN network with a single hub and spokes using full tunnel configuration. In this use-case 100% of spoke generated traffic is encrypted and transported to the hub location. The Auto VPN build results in the hub providing the spoke a default route.
What subnets need to be configured on the spoke router?
All local subnets at the spoke that need access across the Auto VPN network must be configured on the spoke router.
How to set up auto VPN in NCM?
In NCM navigate to the NETWORKS tab on the left side menu, and then click VPN in the top toolbar. Click the Add button and give your new Auto VPN a Network Name. Select an available Encryption Profile from the drop-down menu. Note: Check the NCM Help Panel for algorithm specifics of each encryption profile.
What is auto VPN?
Auto VPN introduces an easy process to build hub and spoke VPN networks from NetCloud Manager. This feature provides secure, resilient VPN sessions over all available WAN sources on each spoke . These VPN sessions can withstand drops in connectivity with automatic failover transition from one WAN interface to another. Auto VPN active path selection is handled automatically via the configured WAN profile priority in Connection Manager. Both Full Tunnel and Split Tunnel topologies for VPN traffic are available in Auto VPN.
How to add a WAN interface to a router?
Click the Add button below the Hub section. Choose an available Hub router and select an available WAN interface.
What is the recommended NCOS version?
Recommended NCOS Version: 7.0.30 and above (for all products other than CVR, 7.0.40 and above for CVR) - for information on upgrading NCOS Version, click Best Practice - NCOS upgrade process.
Does a hub router have a static IP address?
Hub router must have a publicly routable static IP address.
Overview
CP Secure VPN requires NCM Prime. Click here to learn more about NCM PRIME.
Subnet WAN
Cradlepoint Secure VPN Subnet WAN is meant to allow communication to and from each remote Cradlepoint subnet. Given this type of setup, you MUST have a UNIQUE subnet behind each Cradlepoint.
NAT WAN
Cradlepoint Secure VPN NAT WAN is meant to allow communication to and from one client device per site, however multiple clients can be accessed with some configuration.
How to enable remote admin on a cradlepoint router?
Use the following steps to enable Remote Administration of a Cradlepoint device: 1. Log into the devices's NCOS Page. For help with logging in see NCOS: Accessing the Setup Pages of a Cradlepoint router. 2.
How to access a device from the internet?
To access the device from the Internet using a Web browser, enter the device's [protocol] [IP address]: [port number] into your web browser address bar.
How long does it take to allow HTTPS to work?
When using this option, please allow 30 minutes before accessing the device .
Can you use a dynamic DNS hostname instead of an IP address?
If you have a dynamic DNS hostname, you can use it instead of the IP address. See NCOS: How to setup dynamic DNS for more information on configuring dynamic DNS hostnames.
Can remote administration port numbers be changed?
Note: The remote administration port numbers may be changed from their default values for added security. Keep in mind that certain carriers will block some ports.
How to set up VPN with a cradlepoint router?
To set up a VPN tunnel with a CradlePoint router on one end, there must be another device (usually a router) that also supports IPsec on the other end. IKE (Internet Key Exchange) is the security protocol in IPsec. IKE has two phases, Phase 1 and Phase 2. The router has several different security protocol options for each phase, ...
What is VPN status page?
The VPN tunnel status page allows you to view the state of the VPN tunnels. If a tunnel fails to connect to the remote site, check the System Logs for more information.
How long does it take for a router to idle?
(Default: 30 seconds. Range: 10 – 3600 seconds .)
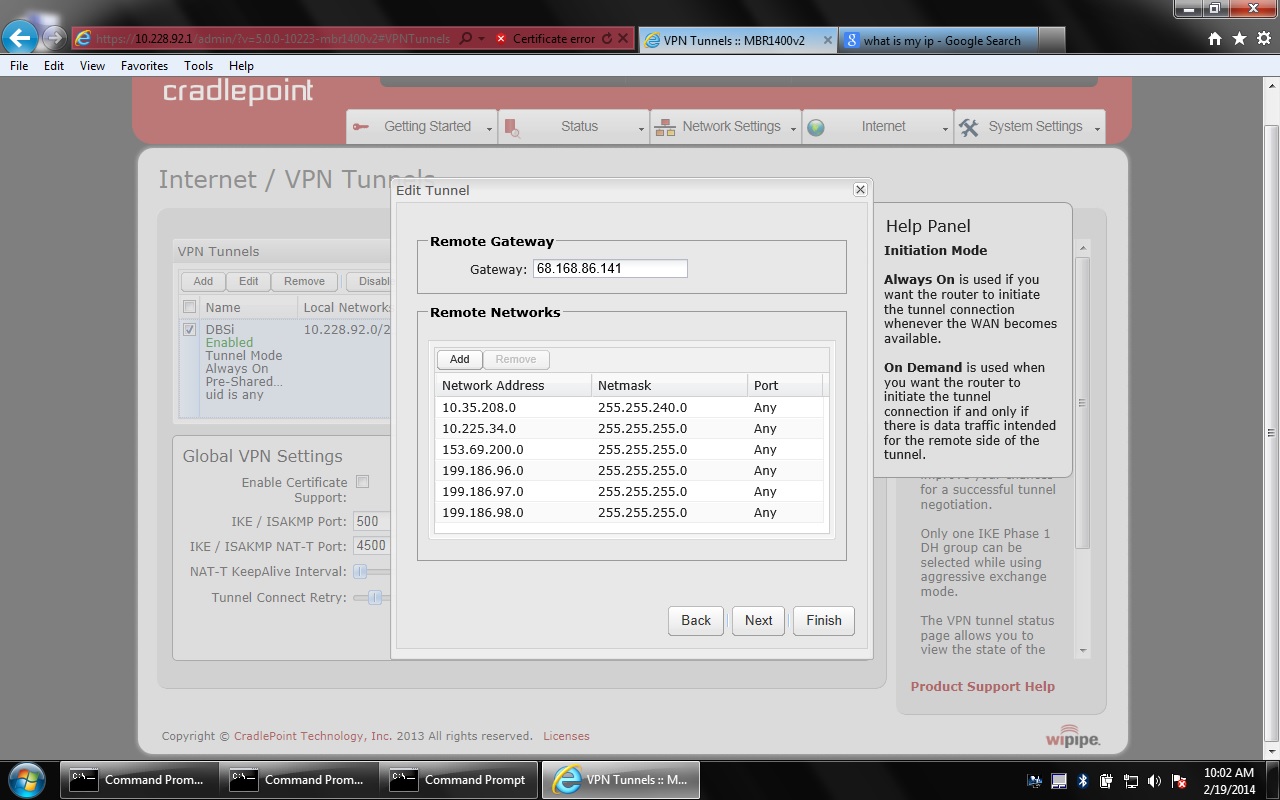
What is VPN tunnel?
VPN Tunnels. VPN (virtual private network) tunnels are used to establish a secure connection to a remote network over a public network. For example, VPN tunnels can be used across the Internet by an individual to connect to an office network while traveling, or by two office networks to function as one network.
How many phases are there in IKE?
Add/Edit Tunnel – IKE Phase 1. IKE security has two phases, Phase 1 and Phase 2. You have the ability to distinctly configure each phase, but the default settings will be sufficient for most users. To set up a tunnel with a remote site, you need to match your tunnel's IKE negotiation parameters with the remote site.
What is responder mode?
Responder Mode: When enabled, the router will not initiate negotiation with peers, otherwise start negotiations as soon as possible.
How many requests can you send before a tunnel is dead?
Maximum Requests: Specify how many requests to send at the selected time interval before the tunnel is considered dead. (Default: 5. Range: 2 – 10.)