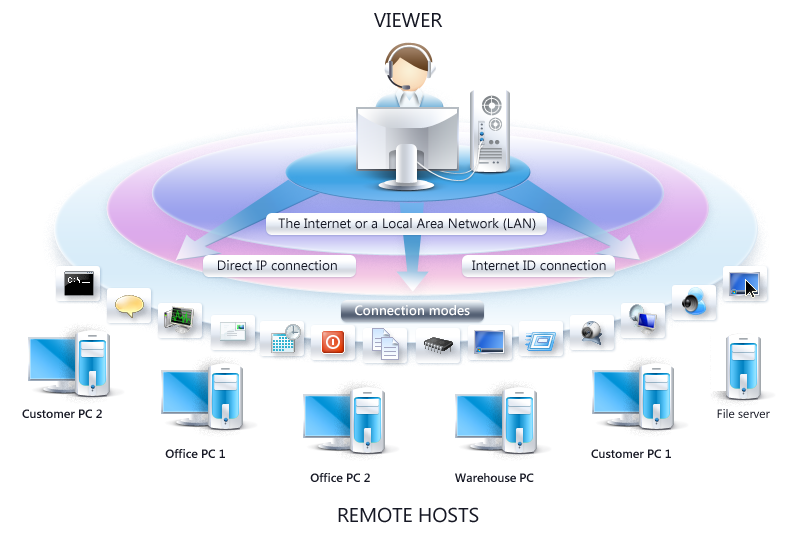
How do I turn off remote access in Windows 10?
Part 4: Disable Remote Desktop Service in Windows 10 with System Genius
- Get iSunshare System Genius downloaded and installed properly in your Windows 10 PC.
- Launch it and take the choice of System Service on the left menu column. Then it will display all the Windows services for you.
- Locate to Remote Desktop Service and click the Disable button to turn off this service on your PC.
How to enable remote access for remote management?
To set up remote management:
- Launch a web browser from a computer or mobile device that is connected to your router’s network.
- Enter http://www.routerlogin.net. ...
- Enter the router user name and password. ...
- Select ADVANCED > Advanced Setup > Remote Management. ...
- Select the Turn Remote Management On check box.
How to enable remote control?
- Go back to System Preferences and click Security & Privacy.
- Click the Firewall tab.
- Click Firewall Options or Advanced.
- If "Remote Management" doesn’t appear in the box with the phrase "Allow incoming connections," click the + to add it, and then select Allow incoming connections.
How to access a Windows 10 computer remotely?
Steps To Remotely Control Another Computer Without Any Tool In Windows 10
- First of all, in your Windows 10 got to your system settings by clicking on the Windows button on your keyboard and then entering ‘System.’
- In a system setting, you need to select the Remote Settings on the left of the screen.
- Now there enable the Allow remote connections to this computer option.
What is remote access explain with example?
Remote access refers to the ability to access a computer, such as a home computer or an office network computer, from a remote location. This allows employees to work offsite, such as at home or in another location, while still having access to a distant computer or network, such as the office network.
What is remote access types?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What is remote access and its advantages?
Remote access technology gives users the ability to access a computer, device or network from a remote location. Remote access is now commonly used for corporate networks that give their employees the ability to remote access a computer and perform their tasks even without being physically present in the office.
What are remote devices?
Remote Device means any device acceptable to us from time to time that provides for the capture of images from Items and for transmission through the clearing process.
What are the two types of remote access servers?
Remote Access Methods1- Remote Access Server: It's one server in organization network that it is the destination of all remote access connections.2- Remote Access Client: All computers that remote connect to network, called remote access client or remote computer.More items...•
What are the three main types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What is access control?
Access control is a fundamental component of data security that dictates whoís allowed to access and use company information and resources. Through...
How does access control work?
There are four main types access control. Organizations typically choose the method that makes the most sense based on their unique security and co...
Why is access control important?
Access control keeps confidential information, including customer data, personally identifiable information, and intellectual property, from fallin...
How does remote access work?
Remote access is accomplished with a combination of software, hardware and network connectivity.
What are the types of remote access?
Traditionally, enterprises used modems and dial-up technologies to allow employees to connect to office networks via telephone networks connected to remote access servers. Devices connected to dial-up networks use analog modems to call assigned telephone numbers to make connections and send or receive messages.
What is access control?
Access control is a fundamental component of data security that dictates who’s allowed to access and use company information and resources. Through authentication and authorization, access control policies make sure users are who they say they are and that they have appropriate access to company data. Access control can also be applied ...
Why is access control important?
Access control keeps confidential information such as customer data, personally identifiable information, and intellectual property from falling into the wrong hands. It’s a key component of the modern zero trust security framework, which uses various mechanisms to continuously verify access to the company network. Without robust access control policies, organizations risk data leakage from both internal and external sources.
What is dynamic access?
In this dynamic method, access is based on a set of attributes and environmental conditions, such as time of day and location, assigned to both users and resources.
How many types of access control are there?
There are four main types access control. Organizations typically choose the method that makes the most sense based on their unique security and compliance requirements. The four access control models are:
Who sets the policies for who is allowed access?
In this method, the owner or administrator of the protected system, data, or resource sets the policies for who is allowed access.
What is remote access?
Definition (s): Access to an organizational information system by a user (or an information system) communicating through an external, non-organization-controlled network (e.g., the Internet). Source (s):
What is an access system?
Access by users (or information systems) communicating external to an information system security perimeter. Access to an organizational system by a user (or a process acting on behalf of a user) communicating through an external network.
What is access to an organizational system?
Access to an organizational system by a user (or a process acting on behalf of a user) communicating through an external network (e.g., the Internet).
What Does Remote Access Mean?
Remote access refers to the ability to access a computer, such as a home computer or an office network computer, from a remote location. This allows employees to work offsite, such as at home or in another location, while still having access to a distant computer or network, such as the office network.
Techopedia Explains Remote Access
Remote access can be established via a line that runs between a computer and a company's local area network (LAN). A connection can also be established between a company's LAN and a remote LAN using a dedicated line. This type of line provides faster speeds but has the drawback of being more expensive.
What is access control?
Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations.
What is physical access control?
Physical access control is a set of policies to control who is granted access to a physical location. Real-world examples of physical access control include the following:
What is DAC in security?
Discretionary access control (DAC): Once a user is given permission to access an object (usually by a system administrator or through an existing access control list), they can grant access to other users on an as-needed basis. This may introduce security vulnerabilities, however, as users are able to determine security settings and share permissions without strict oversight from the system administrator.
Can a bank have unrestricted access to personal information?
Since the bank handles very sensitive personal information, it’s entirely possible that no one has unrestricted access to the data. Even the bank’s president or head of security may need to go through a security protocol to access the full data of individual customers.
How Does Access Control Work?
Access control can be split into two groups designed to improve physical security or cybersecurity:
What are the Components of Access Control?
At a high level, access control is about restricting access to a resource. Any access control system, whether physical or logical , has five main components:
What is RBAC in a system?
RBAC is common in commercial and military systems , where multi-level security requirements may exist. RBAC differs from DAC in that DAC allows users to control access while in RBAC, access is controlled at the system level, outside of user control. RBAC can be distinguished from MAC primarily by the way it handles permissions.
What is RBAC in security?
It is difficult to manage but its use is justified when used to protected highly sensitive data . Role-based access control (RBAC): In RBAC, an access system determines who can access a resource rather than an owner. RBAC is common in commercial and military systems, where multi-level security requirements may exist.
What is ABAC access control?
Attribute-based access control ( ABAC): Access management systems were access is granted not on the rights of a user after authentication but based on attributes. The end user has to prove so-called claims about their attributes to the access control engine. An attribute-based access control policy specifies which claims need to be satisfied to grant access to the resource. For example, the claim may be the user's age is older than 18 and any user who can prove this claim will be granted access. In ABAC, it's not always necessary to authenticate or identify the user, just that they have the attribute.
What is access once authenticated and authorized?
Access: Once authenticated and authorized, the person or computer can access the resource.
What is authorization in computer?
Authorization: The function of specifying access rights or privileges to resources. For example, human resources staff are normally authorized to access employee records and this policy is usually formalized as access control rules in a computer system. Access: Once authenticated and authorized, the person or computer can access the resource.
What is role based access control?
Role-based access control enables you to provide users with limited access to the machine instead of making them full local administrators. Read more about role-based access control and the available roles.
Who can configure who gets access to the gateway?
Gateway administrators can configure who gets access as well as how users authenticate to the gateway. Only gateway administrators can view and configure the Access settings in Windows Admin Center. Local administrators on the gateway machine are always administrators of the Windows Admin Center gateway service.
Can you control who can access the admin center?
On the Users tab you can control who can access Windows Admin Center as a gateway user. By default, and if you don't specify a security group, any user that accesses the gateway URL has access. Once you add one or more security groups to the users list, access is restricted to the members of those groups.
Is group based access supported in Windows Admin Center?
Group based access in Windows Admin Center is not supported in workgroup environments or across non-trusted domains.
Can you change access permissions on a gateway?
Gateway users can connect to the Windows Admin Center gateway service to manage servers through that gateway, but they can't change access permissions nor the authentication mechanism used to authenticate to the gateway.
