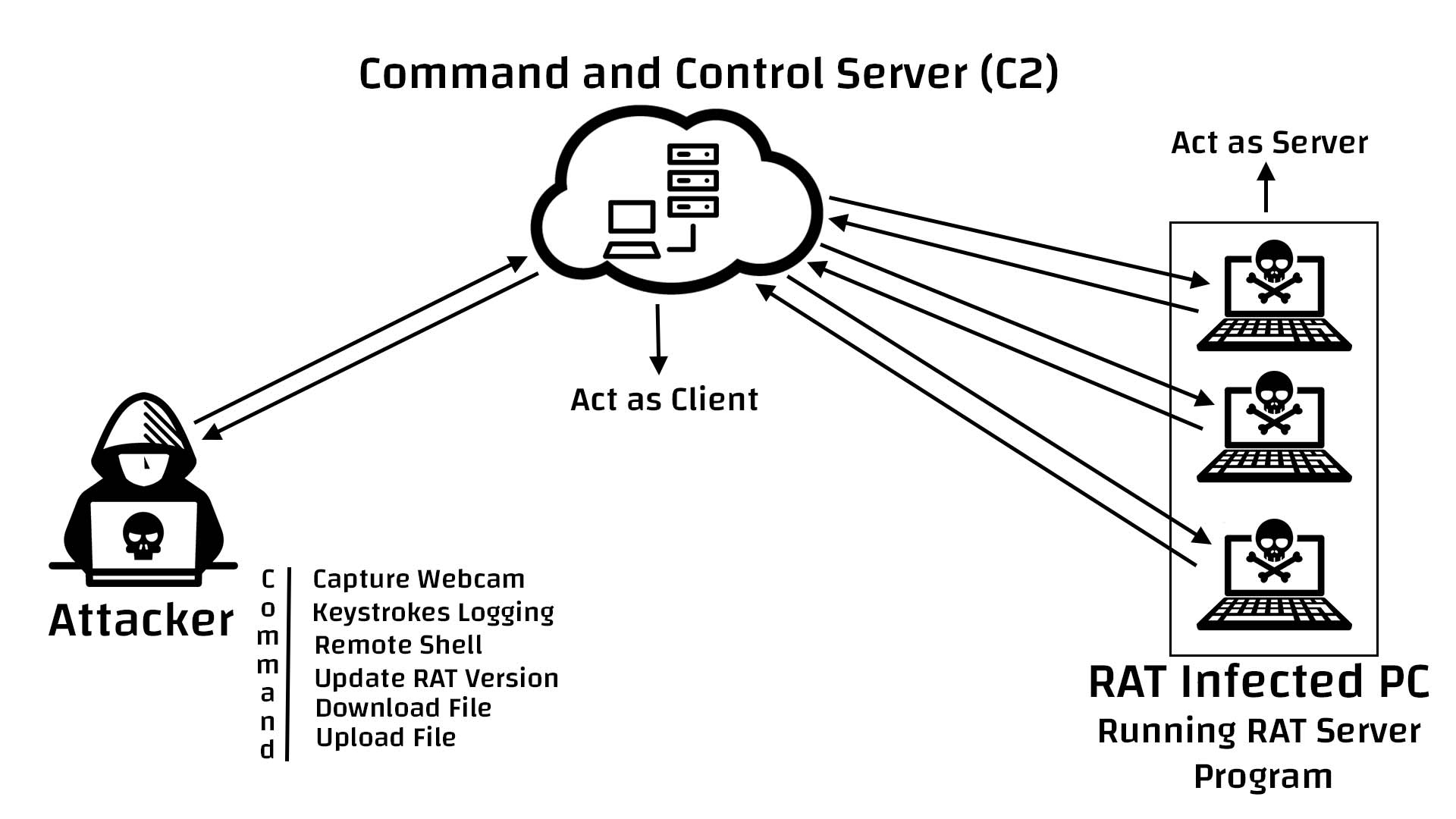
Remote access trojan
A Remote Access Trojan is a type of malware that controls a system through a remote network connection. While desktop sharing and remote administration have many legal uses, "RAT" connotes criminal or malicious activity. A RAT is typically installed without the victim's knowledge, often as payload of a Trojan horse, and will try to hide its operation from the victim and from security software and other anti-…
Full Answer
What is remote access trojan (RAT)?
What Does Remote Access Trojan (RAT) Mean? What Does Remote Access Trojan (RAT) Mean? A remote access Trojan (RAT) is a program used by the intruders to take complete control of the victim's computer for the purpose of performing various malicious activities.
How do intruders get remote access to a computer?
Intruders eventually trigger the server program on the victim's computer. Then, the RAT runs invisibly on the victim's computer and allows the intruder to gain remote access and control of the infected computer.
What happened to remote control PCs in the late 1990s?
In the late 1990s, when the internet was still young, it was common for tech-savvy kids to scare their friends by controlling their PCs remotely. They would eject the CD tray, swap the mouse buttons, or change the desktop colors. To the unwitting user, it looked like a ghost was taking over the machine.
How are Remote Access Trojans Useful to Hackers?
Why do attackers use remote devices?
What is remote control software?
What happens if you remove the internet from your computer?
See 1 more
About this website

What is a remote Trojan?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
Is remote access Trojan illegal?
Law enforcement officials say that simply possessing a remote-access tool isn't illegal. In fact, remote-access tools are often used for IT support purposes in corporate environments.
What are the main features of a remote access Trojan?
RAT (remote access Trojan)Monitoring user behavior through keyloggers or other spyware.Accessing confidential information, such as credit card and social security numbers.Activating a system's webcam and recording video.Taking screenshots.Distributing viruses and other malware.Formatting drives.More items...
What was the first remote access Trojan?
The oldest RAT was first developed in 1996 [10], however legitimate remote access tools were first created in 1989 [11]. Since then, the number of RATs has grown rapidly. The first phase was marked by home-made RATs. In these years, everyone made their own RAT, however these did not prosper and were not heavily used.
How do I know if someone is accessing my computer remotely?
You can try any of these for confirmation.Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.Way 7: Check Your Firewall Settings.More items...•
Can an Iphone get a remote access Trojan?
The iOS Trojan is smart and spies discretely, i.e. does not drain a battery. The RCS mobile Trojans are capable of performing all kinds of spying you can expect from such a tool, including location reporting, taking photos, spying on SMS, WhatsApp and other messengers, stealing contacts and so on.
Is a backdoor malware?
A backdoor is a malware type that negates normal authentication procedures to access a system. As a result, remote access is granted to resources within an application, such as databases and file servers, giving perpetrators the ability to remotely issue system commands and update malware.
What are the variants of remote access Trojan?
Common Remote Access TrojansSakula. Sakula is a seemingly benign software with a legitimate digital signature, yet it allows attackers complete remote administration capabilities over a machine. ... KjW0rm. ... Havex. ... Agent. ... Dark Comet. ... AlienSpy. ... Heseber BOT. ... Sub7.More items...
How can I remotely access another computer over the Internet?
Set up remote access to your computerOn your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
What is remote access software used for?
At its core, remote pc access software essentially lets you teleport to any location (where you have been granted access to a computer). You can use it to literally control a computer from a remote location as if you were sitting in front of it.
What is a remote access tool?
Remote access programs and tools (sometimes referred to as RATs) allow access and manipulation of systems remotely from another location. Many remote access programs are legitimate tools used by all types of users to access files and data on remote computers.
Can you get a RAT on your phone?
RATs in Your Android It's well documented, freely available, and gives an attacker complete control over infected devices. There are even tutorials on how to use the RAT, and free, easy-to-use tools that will inject its malicious code into legitimate apps.
Are PUPs malware?
Type and source of infection. Detections categorized as PUPs are not considered as malicious as other forms of malware, and may even be regarded by some as useful. Malwarebytes detects potentially unwanted programs for several reasons, including: They may have been installed without the user's consent.
What is a logic bomb virus?
A logic bomb is a malicious program that is triggered when a logical condition is met, such as after a number of transactions have been processed, or on a specific date (also called a time bomb). Malware such as worms often contain logic bombs, behaving in one manner, then changing tactics on a specific date and time.
Is a backdoor malware?
A backdoor is a malware type that negates normal authentication procedures to access a system. As a result, remote access is granted to resources within an application, such as databases and file servers, giving perpetrators the ability to remotely issue system commands and update malware.
What is pup in cyber security?
A potentially unwanted program (PUP) is a program that may be unwanted, despite the possibility that users consented to download it. PUPs include spyware, adware and dialers, and are often downloaded in conjunction with a program that the user wants.
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
remote access trojan free download - SourceForge
Number one of the biggest security holes are passwords, as every password security study shows. This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system. There are already several login hacker tools available, however, none does either support more than one protocol to ...
Top five remote access trojans - Infosec Resources
Sources. October 2018’s Most Wanted Malware: For The First Time, Remote Access Trojan Reaches Top 10 Threats, Check Point; FlawedAmmyy Malware Information, Trend Micro; QuasarRAT, GitHub; androrat, GitHub; RATs Come to Android: It’s Scary, But You’re (Probably) Safe, PC Magazine
[Tutorial] What’s Remote Access Trojan & How to Detect/Remove It?
Remote Access Trojan Examples. Since spam RAT comes into being, there have existing lots of types of it.. 1. Back Orifice. Back Orifice (BO) rootkit is one of the best-known examples of a RAT. It was made by a hacker group named the Cult of the Dead Cow (cDc) to show the security deficiencies of Microsoft’s Windows 9X series of operating systems (OS).
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data centre. Physical access to the data centre isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What happens if you remove the internet from your computer?
Removing the Internet connection from the device disables remote access to your system by an attacker. After the device can no longer connect to the Internet, use your installed anti-malware program to remove it from local storage and memory. Unless you have monitoring configured on your computer, you won't know which data and files transferred to an attacker. You should always change passwords across all accounts, especially financial accounts, after removing malware from your system.
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
What Does a RAT Virus Do?
Since a remote access trojan enables administrative control , it is able to do almost everything on the victim machine.
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
Is Sub 7 a trojan horse?
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1. Sub7 has not been maintained since 2014. 4.
Can a RAT remote access trojan be used on a computer?
Since RAT remote access trojan will probably utilize the legitimate apps on your computer, you’d better upgrade those apps to their latest versions. Those programs include your browsers, chat apps, games, email servers, video/audio/photo/screenshot tools, work applications…
What Does Remote Access Trojan (RAT) Mean?
A remote access Trojan (RAT) is a program used by the intruders to take complete control of the victim's computer for the purpose of performing various malicious activities. Unlike viruses and worms, RATs can exist well before detection and even remain after removal.
Techopedia Explains Remote Access Trojan (RAT)
A RAT's installation mechanism is usually attached to a legitimate program. RATs are commonly hidden within games or other small programs, as well as in email attachments that users download. Imposters are able to customize RAT features, such as when and where to launch the Trojan.
How Remote Access Trojans (RATs) works
As in the case of most malware types, RATs often infect systems by hiding within seemingly legitimate files such as email attachments, download packages, applications, or web links. When a user opens these files, the hidden RATs will install themselves on the victim’s system.
History of Remote Access Trojans (RATs)
RAT precursors can be traced back to the late 1980s with the advent of early, legitimate remote access software programs, such as NetSupport. By the late 1990s, remote access software was commonplace, and so were RATs.
When was remote access first used?
The oldest legitimate remote access software was built in the late 1980s, when tools such as NetSupport appeared. Soon after that, in 1996, their first malicious counterparts were created. NokNok and D.I.R.T. were among the first, followed by NetBus, Back Orifice and SubSeven.
Who was the law professor that was targeted by NetBus?
In 1999, someone downloaded NetBus and targeted Magnus Eriksson, a law professor at Lund University in Sweden. The attacker planted 12,000 pornographic images on his computer, 3,500 of which featured child pornography. The system administrators discovered them, and the law professor lost his job.
Is NetBus a legit tool?
The developer claimed he didn’t want NetBus to be used maliciously, saying it was “a legit remote admin tool,” security researcher Seth Kulakow wrote in a paper he published with the SANS Institute. “However, if you didn’t already figure it out, it is still a very nice tool to use for the other purpose,” Kulakow wrote.
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data center. Physical access to the data center isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What happens if you remove the internet from your computer?
Removing the Internet connection from the device disables remote access to your system by an attacker. After the device can no longer connect to the Internet, use your installed anti-malware program to remove it from local storage and memory. Unless you have monitoring configured on your computer, you won't know which data and files transferred to an attacker. You should always change passwords across all accounts, especially financial accounts, after removing malware from your system.