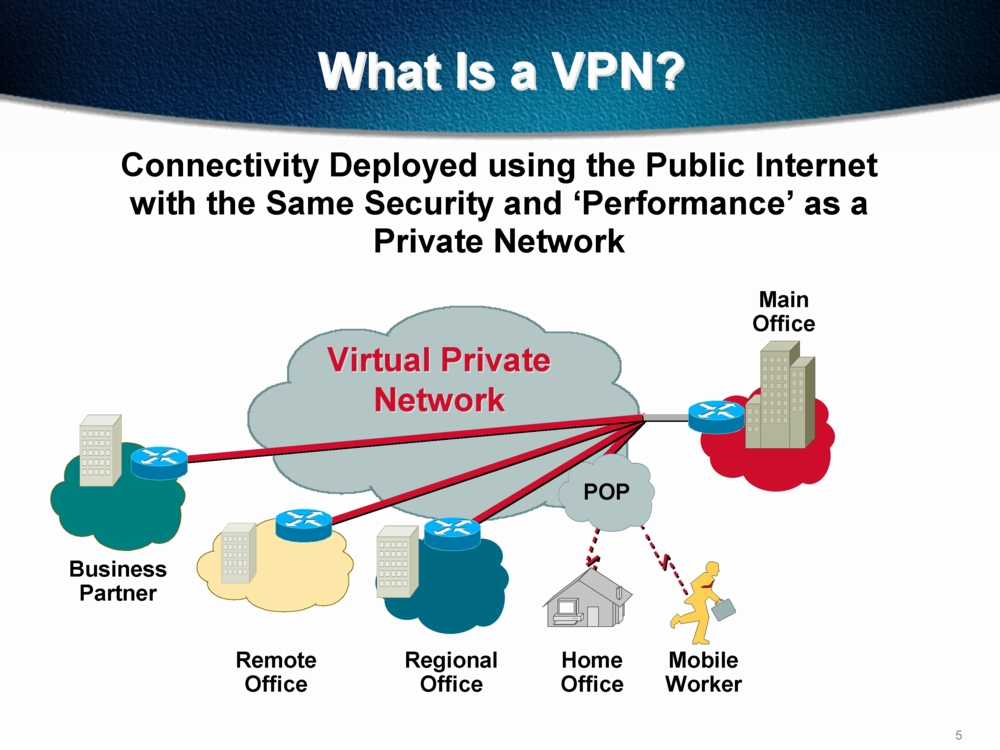
To define the VPN Remote Access community and its participants:
- From the Objects Bar, click VPN Communities.
- Double-click RemoteAccess. ...
- On the Participating Gateways page, click the Add button and select the Security Gateways that are in the Remote Access Community.
- On the Participating User Groups page, click the Add button and select the group that contains the Remote Access users.
- Click OK.
- Publish the changes.
How to access remote computer via VPN?
Knowledge How do I remote into my computer at work from home using the VPN?
- Enable remote connection on your work computer. ...
- See How do I download and install the Cisco AnyConnect VPN client? ...
- Reboot your home computer
- After the reboot, go to your home computer's Windows Start Menu, search for Cisco AnyConnect VPN Client and open the program
- The AnyConnect window will come up and indicate that the VPN is "Ready to connect". ...
Why use a VPN for remote access in the cloud?
Why is a VPN Needed?
- Reduces Risk. A Clark School study is one of the first to quantify the near-constant rate of hacker attacks on computers with Internet access—every 39 seconds on average—and the non-secure ...
- Secures & Extends Private Network Services. ...
- Leverages Existing Security Investments. ...
- Increases Employee Productivity. ...
Can connect to VPN, cannot access remote resources?
If you cannot access some resources using only the VPN (e.g., it’s behind a departmental firewall), Millward said you should connect to the GlobalProtect client first to verify your identity, then use your preferred remote access management client.
How do access remote network with OpenVPN?
Using OpenVPN to Securely Access Your Network Remotely
- Visit http://tplinkwifi.net, and log in with your TP-Link ID or the password you set for the router.
- Go to Advanced > VPN Server > OpenVPN, select the checkbox to enable VPN Server.
- Select the Service Type (communication protocol) for OpenVPN Server: UDP, TCP.
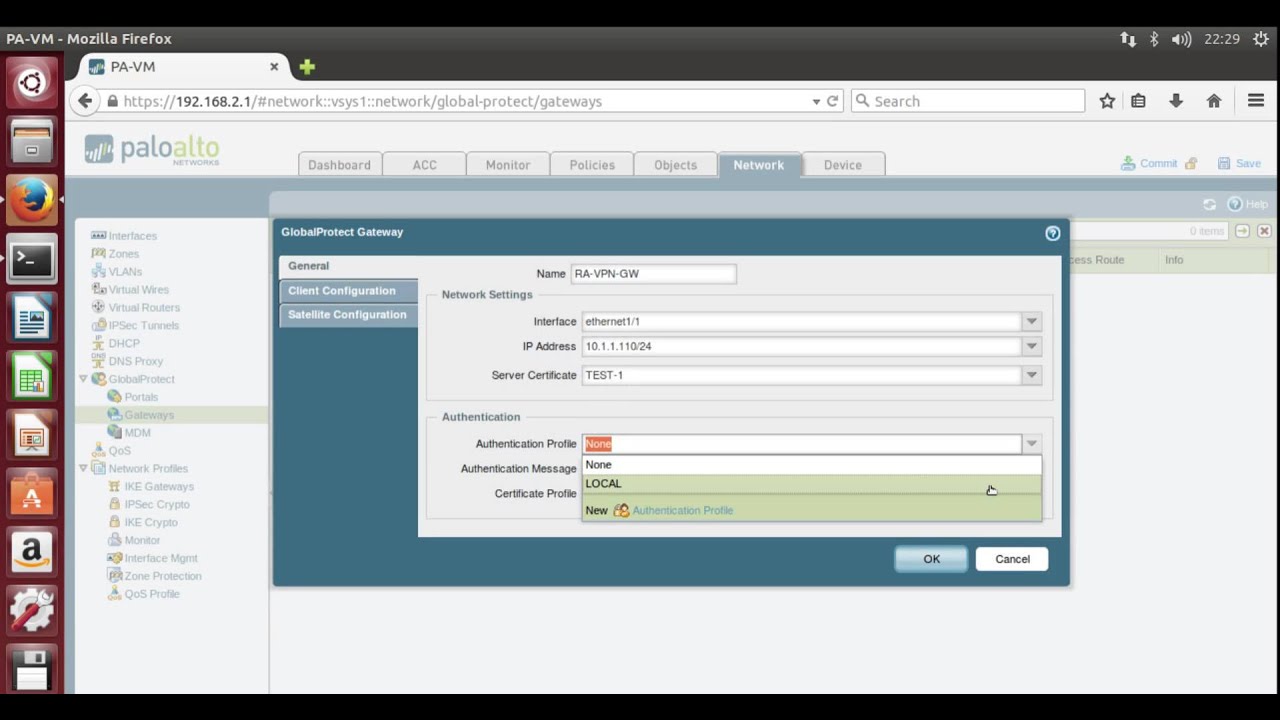
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
How do you define remote access?
Definition(s): Access to an organizational information system by a user (or an information system) communicating through an external, non-organization-controlled network (e.g., the Internet). Access by users (or information systems) communicating external to an information system security perimeter.
Is VPN remote access secure?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is the simple definition of VPN?
VPN stands for "virtual private network" — a service that helps you stay private online. A VPN establishes a secure, encrypted connection between your computer and the internet, providing a private tunnel for your data and communications while you use public networks.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What are the disadvantages of using a VPN?
What are the disadvantages of a VPN?With some VPNs, your connection can be slower.Certain websites block VPN users.VPNs are illegal or questionable in certain countries.There's no way of knowing how well a VPN encrypts your data.Some VPNs log and sell browsing data to third parties.More items...
How can I use VPN remotely?
Simply go to Start -> Accessories -> Remote Desktop Connection and enter the IP address of the other Windows computer. desktop software. From HOME Mac to OFFICE Windows: Connect with VPN, then use Remote Desktop Client. From HOME Windows to OFFICE Mac: Connect with VPN, then use VNC client.
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What are the advantages of using a VPN?
Pros of VPN: What are the advantages of using a VPN?Secure Your Network. The benefits of using a VPN are vast. ... Hide Your Private Information. ... Prevent Data Throttling. ... Avoid Bandwidth Throttling. ... Get Access to Geo-blocked Services. ... Network Scalability. ... Reduce Support Costs.
Why you should use a VPN?
In basic terms, a VPN provides an encrypted server and hides your IP address from corporations, government agencies and would-be hackers. A VPN protects your identity even if you are using public or shared Wi-Fi, and your data will be kept private from any prying internet eyes.
What is VPN and its types?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs. In this guide, we explain how each of these VPN types work and when to use them. A VPN is a service that creates a private tunnel within a public connection (e.g. the internet).
How do I set up remote access to my computer?
On your Windows, Android, or iOS device: Open the Remote Desktop app (available for free from Microsoft Store, Google Play, and the Mac App Store), and add the name of the PC that you want to connect to (from Step 1). Select the remote PC name that you added, and then wait for the connection to complete.
Why is remote access important?
With remote access, employees can safely work from any device, platform, or network at their home office or abroad. Remote desktop functions allow them to remotely access important files and share their screen for meetings and troubleshooting.
How do companies do remote access?
You have two main options here – a VPN or the cloud. VPN – Virtual Private Network – You can restrict access so that employees must exclusively connect through a VPN, providing a direct, encrypted connection between their remote device and the main office server.
How can I remotely access my computer?
Set up remote access to your computerOn your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What are the advantages of remote access VPN?
Another advantage of remote access VPNs is that they provide companies with an affordable way to secure data sent by offsite employees. The initial investment needed to set up a remote access VPN is minimal and they can easily be scaled as a company grows and this is especially true if a VPN service provider is used.
Why is VPN important for business?
The most important benefit though is data security. When an offsite employee sends data through a VPN, it is encrypted, so even if a hacker is able to intercept that data, they won’t be able to use it. This is particularly important if an employee accesses their companies’ network using public Wi-Fi while traveling because traffic sent over these networks is usually not encrypted.
What is a network access server?
A network access server could be a dedicated server or it might be a software application running on a shared server. Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.
Why do businesses use VPNs?
Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
Is it good to work remotely?
The ability to work remotely is one of the perks that many businesses offer employees to help sweeten the deal. The recent coronavirus outbreak has only exacerbated that, leading many more organizations to allow their employees to work remotely. While this is good news for employees, it could end up causing a great deal of disruption to organizations that aren’t prepared and one way to do so is to look into remote access VPN solutions.
What is a header in a VPN?
headers including fields that allow the VPN devices to make the traffic secure. The VPN devices also encrypt the original IP packet, meaning that the original packet’s contents are indecipherable to anyone who happens to see a copy of the packet as it traverses the Internet.
What is IPsec used for?
The first approach uses IPsec, IPsec is used to create authentication and encryption services between endpoints on an IP network. The second way is via tunneling protocols, which allow you to establish a tunnel between endpoints on a network.
Is VPN as secure as WAN?
Security: Internet VPN solutions can be as secure as private WAN connections.
Does a VPN gateway encrypt data?
Whenever the host tries to send any information, the VPN client software encapsulates and encrypts the information before sending it over the Internet to the VPN gateway at the edge of the target network. On receipt, the VPN gateway handles the data in the same way as it would handle data from a site-to-site VPN.
Why is remote access VPN important?
It also ensures to protect your online privacy. Remote access VPNs restrict user access to just one, which signifies the fact that it is designed for personal use. Nevertheless, if you are a digital nomad that remotely communicates with your organization’s network, remote access VPN could be the pick of the litter.
Which VPN supports remote access?
2) SSL VPN – Also known as mobile access VPN, SSL VPN supports only remote access connections. While both the blades offer an equal amount of data confidentiality, integrity and authenticity, let’s see the other features that differentiate each other. IPSec VPN. SSL VPN. Supports both TCP and UDP.
What is VPN client?
A VPN client installed on the remote user’s desktop recognizes the destination network as a part of remote VPN encryption network.
What is VPN encryption?
In other words, your information that travels through the internet gets encrypted and encapsulated by a secure VPN gateway. This encryption technique plays a vital role in communicating your information to the remote destination. It scrambles your data and keeps it out of reach from notorious third parties like hackers and snoopers.
Why do businesses use VPN?
Hence every organization aims at offering comprehensive resource accessibility, even to its remote workers. That’s when a remote access VPN comes into the picture. It shares your organization’s responsibility of granting secure access to the business resources.
Is VPN clientless?
It is clientless and just requires a browser. Seamless to use. Not seamless, requires multilevel authentication. Other than the data security it offers, setting up a remote access VPN is cost-effective. With multiple VPN providers offering competitive business VPN plans, it also easy to upgrade your subscription plan as your business grows.
What is remote access VPN?
Remote access. A remote access VPN securely connects a device outside the corporate office. These devices are known as endpoints and may be laptops, tablets, or smartphones. Advances in VPN technology have allowed security checks to be conducted on endpoints to make sure they meet a certain posture before connecting.
What is VPN security?
Security. What Is a VPN? - Virtual Private Network. A virtual private network, or VPN, is an encrypted connection over the Internet from a device to a network. The encrypted connection helps ensure that sensitive data is safely transmitted. It prevents unauthorized people from eavesdropping on the traffic and allows the user to conduct work ...
How does a virtual private network (VPN) work?
A VPN extends a corporate network through encrypted connections made over the Internet. Because the traffic is encrypted between the device and the network, traffic remains private as it travels. An employee can work outside the office and still securely connect to the corporate network. Even smartphones and tablets can connect through a VPN.
What is secure remote access?
Secure remote access provides a safe, secure way to connect users and devices remotely to a corporate network. It includes VPN technology that uses strong ways to authenticate the user or device. VPN technology is available to check whether a device meets certain requirements, also called a device’s posture, before it is allowed to connect remotely.
What is site to site VPN?
A site-to-site VPN connects the corporate office to branch offices over the Internet. Site-to-site VPNs are used when distance makes it impractical to have direct network connections between these offices. Dedicated equipment is used to establish and maintain a connection. Think of site-to-site access as network to network.
Is VPN traffic encrypted?
Yes, traffic on the virtual network is sent securely by establishing an encrypted connection across the Internet known as a tunnel. VPN traffic from a device such as a computer, tablet, or smartphone is encrypted as it travels through this tunnel.
Remote Access VPN Overview
You can use Firepower Device Manager to configure remote access VPN over SSL using the AnyConnect client sofware.
Licensing Requirements for Remote Access VPN
Your base device license must meet export requirements before you can configure remote access VPN. When you register the device, you must do so with a Smart Software Manager account that is enabled for export-controlled features. You also cannot configure the feature using the evaluation license.
Guidelines and Limitations for Remote Access VPN
Please keep the following guidelines and limitations in mind when configuring RA VPN.
Configuring Remote Access VPN
To enable remote access VPN for your clients, you need to configure a number of separate items. The following procedure provides the end to end process.
Managing the Remote Access VPN Configuration
Remote access VPN connection profiles define the characteristics that allow external users to make a VPN connection to the system using the AnyConnect client.
Monitoring Remote Access VPN
To monitor and troubleshoot remote access VPN connections, open the CLI console or log into the device CLI and use the following commands.
Troubleshooting Remote Access VPNs
Remote access VPN connection issues can originate in the client or in the Firepower Threat Defense device configuration. The following topics cover the main troubleshooting problems you might encounter.
How does remote access work?
Remote access is accomplished with a combination of software, hardware and network connectivity.
What are the types of remote access?
Traditionally, enterprises used modems and dial-up technologies to allow employees to connect to office networks via telephone networks connected to remote access servers. Devices connected to dial-up networks use analog modems to call assigned telephone numbers to make connections and send or receive messages.
What is VPN connection?
A VPN connection disguises your data traffic online and protects it from external access. Unencrypted data can be viewed by anyone who has network access and wants to see it. With a VPN, hackers and cyber criminals can’t decipher this data. Secure encryption: To read the data, you need an encryption key .
Why use VPN?
With contemporary VPNs, you can encrypt your IP address so that you appear to be surfing from another country, enabling you to access this content from anywhere.
How does a VPN work?
This means your Internet Service Provider (ISP) and other third parties cannot see which websites you visit or what data you send and receive online. A VPN works like a filter that turns all your data into "gibberish". Even if someone were to get their hands on your data, it would be useless.
What kind of VPNs are there?
There are many different types of VPNs, but you should definitely be familiar with the three main types:
How do I install a VPN on my computer?
Before installing a VPN, it is important to be familiar with the different implementation methods:
How to use VPN on Android?
As already mentioned, there are also VPN connections for Android smartphones and iPhones. Fortunately, smartphone VPN services are easy to use and generally include the following: 1 The installation process usually only downloads one app from the iOS App Store or Google Play Store. Although free VPN providers exist, it’s wise to choose a professional provider when it comes to security. 2 The setup is extremely user-friendly, as the default settings are already mostly designed for the average smartphone user. Simply log in with your account. Most apps will then guide you through the key functions of the VPN services. 3 Switching on the VPN literally works like a light switch for many VPN apps. You will probably find the option directly on the home screen. 4 Server switching is usually done manually if you want to fake your location. Simply select the desired country from the offer. 5 Advanced setup is available for users requiring a higher degree of data protection. Depending on your VPN, you can also select other protocols for your encryption method. Diagnostics and other functions may also be available in your app. Before you subscribe, learn about these features to find the right VPN for your needs. 6 In order to surf the internet safely from now on, all you have to do is first activate the VPN connection through the app.
What is the primary job of a VPN?
These are the features you should expect from a comprehensive VPN solution: Encryption of your IP address: The primary job of a VPN is to hide your IP address from your ISP and other third parties. This allows you to send and receive information online without the risk of anyone but you and the VPN provider seeing it.
How to install Remote Access Role in VPN?
On the VPN server, in Server Manager, select Manage and select Add Roles and Features. The Add Roles and Features Wizard opens. On the Before you begin page, select Next.
How to start remote access?
Select Start service to start Remote Access. In the Remote Access MMC, right-click the VPN server, then select Properties. In Properties, select the Security tab and do: a. Select Authentication provider and select RADIUS Authentication.
How to select a server from the server pool?
On the Select destination server page, select the Select a server from the server pool option. Under Server Pool, select the local computer and select Next. On the Select server roles page, in Roles, select Remote Access, then Next. On the Select features page, select Next. On the Remote Access page, select Next.
How many Ethernet adapters are needed for VPN?
Install two Ethernet network adapters in the physical server. If you are installing the VPN server on a VM, you must create two External virtual switches, one for each physical network adapter; and then create two virtual network adapters for the VM, with each network adapter connected to one virtual switch.
What is NAS in a network?
A NAS is a device that provides some level of access to a larger network. A NAS using a RADIUS infrastructure is also a RADIUS client, sending connection requests and accounting messages to a RADIUS server for authentication, authorization, and accounting. Review the setting for Accounting provider: Table 1.
Can you assign a VPN to a pool?
Additionally, configure the server to assign addresses to VPN clients from a static address pool. You can feasibly assign addresses from either a pool or a DHCP server; however, using a DHCP server adds complexity to the design and delivers minimal benefits.
Is RRAS a router or a server?
RRAS is designed to perform well as both a router and a remote access server because it supports a wide array of features. For the purposes of this deployment, you require only a small subset of these features: support for IKEv2 VPN connections and LAN routing.
