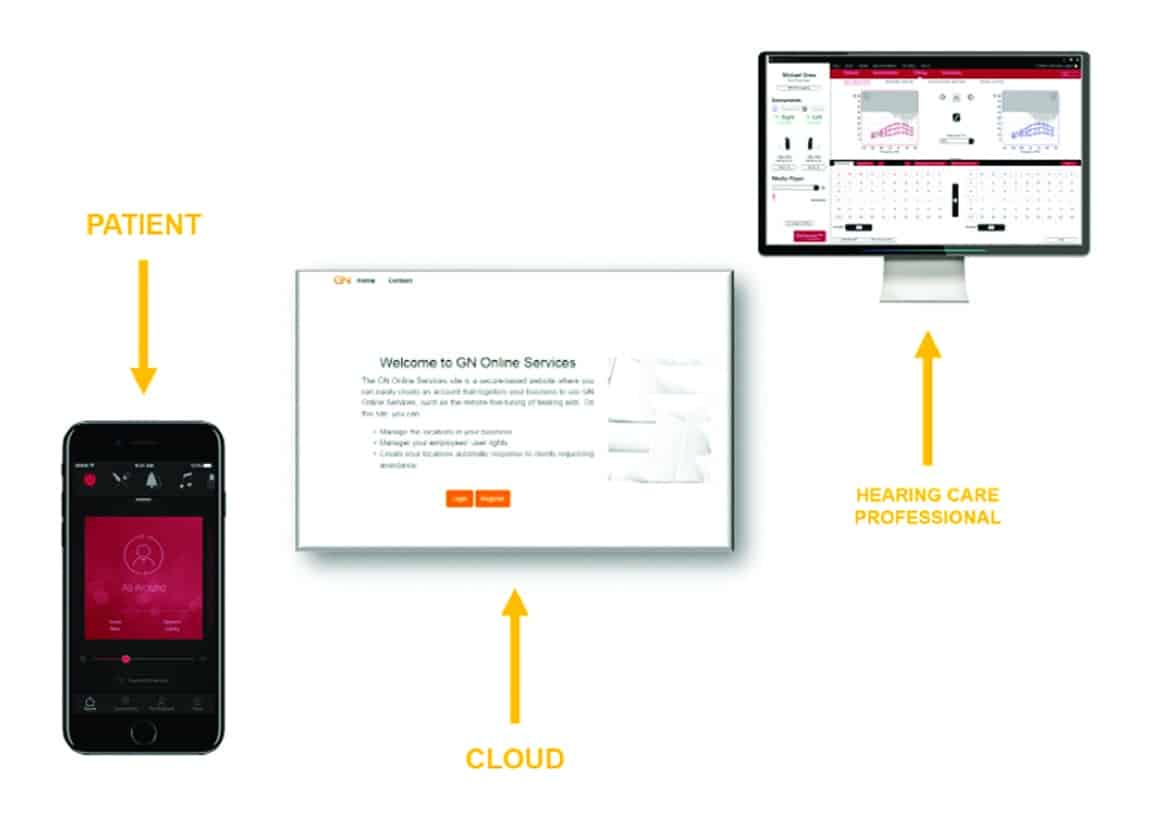
Full Answer
What is remote access technology and how does it work?
To begin, its important that we define what remote access technology means in the context of this article. Remote access technology refers to any IT toolset used to connect to, access, and control devices, resources, and data stored on a local network from a remote geographic location.
What are the different options for secure remote access?
Let’s look at a few of the common options for secure remote access: A common remote access technology in use today is the IPsec VPN. A piece of software called a VPN client is installed on the end user’s computer and is configured with details about the target network, such as the gateway IP address and a pre-shared security key.
How did the Tennessee Department of Health use Remote Desktop Access?
The Tennessee Department of Health used remote desktop access to electronic health records (EHRs) to review data regarding known affected patients and identify the background rate of adverse events from the procedures of concern.
Should SMBs use RDS or remote access software?
Many SMBs opt to use Remote Access Software to receive a secure RDS-like experience to computers that are already in the office. While an attractive solution, this can prove more expensive and intricate to manage with several users compared to alternatives.
What is Remote Access Technology?
Why do organizations use remote access?
What Is Remote Access Software?
What Is a Virtual Private Network?
What is remote desktop service?
What is the most common application used with RDS?
Why is remote access important?
See 2 more

What is the technology used in remote access?
virtual private network (VPN) technologyRemote access software is usually accomplished using a virtual private network (VPN) technology. This type of method is more available compared to others since it is a more secure remote access software that connects the user and the enterprise's networks through an internet connection.
What are the different types of remote access methods?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What is the most sophisticated form of remote access?
Remote Desktop SoftwareRemote Desktop Software The most sophisticated form of remote access enables users on one computer to see and interact with the desktop user interface of another computer.
What is example of remote access?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What are the three main types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What is the purpose of remote access?
Remote access enables remote users to access files and other system resources on any devices or servers that are connected to the network at any time. This increases employee productivity and enables employees to better collaborate with colleagues around the world.
What is required for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
What are the pros and cons of remote desktop access?
Advantages of Remote Access1) Flexible Access. ... 2) Flexible Set-Up and Costs. ... 3) Full Control on Authorization and Access. ... 4) Centralized Storage and Backups. ... 5) Shared Resources; Greater Efficiency and Collaboration. ... 1) Security Issues. ... 2) Version Problems and Data Liabilities. ... 3) Hardware Issues Still Need On-Site Work.More items...•
What is remote GUI?
Remote GUI allows you to access your router's online settings, also known as the graphical user interface (GUI), through a WAN connection. To access your modem remotely, you will enter https:// followed by the modem IP in the URL field of a browser. 1.
What is remote access and its advantages?
Remote access technology gives users the ability to access a computer, device or network from a remote location. Remote access is now commonly used for corporate networks that give their employees the ability to remote access a computer and perform their tasks even without being physically present in the office.
Which tool is used to connect a remote computer?
Comparison of Top Remote Desktop Access ToolsTool NameOS & DevicesOur RatingTeam ViewerWindows, Linux, iOS, & Android4.2/5VNC ConnectWindows, Mac, Linux, Raspberry Pi, iOS, Android4.2/5LogMeInWindows & Mac4.3/5GoToMyPCWindows & Mac4.2/58 more rows•6 days ago
What is remote access security?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What are the secure methods the remote users can use to connect to the internal network to perform file operations?
Most commonly, remote workers will use a remote access VPN client to connect to their organization's VPN gateway to gain access to its internal network, but not without authenticating first. Usually, there are two choices when using VPNs: IP Security (IPsec) or Secure Sockets Layer (SSL).
What are remote devices?
Remote Device means any device acceptable to us from time to time that provides for the capture of images from Items and for transmission through the clearing process.
Which type of cable is used for remote access?
coaxial cable1.1) Accessing the Internet through a cable network is a popular option that teleworkers use to access their enterprise network. The cable system uses a coaxial cable that carries radio frequency (RF) signals across the network. Coaxial cable is the primary medium used to build cable TV systems.
What is the best technology for remote work?
Best Technology for Working Remotely. 1. Cloud Computing . If you haven't invested in cloud computing by 2020, like those companies that didn't embrace the internet back in 2000, you've already fallen behind your competition. Cloud computing increases safety and gives users access to a remote virtual work environment.
Why is remote work so convenient?
Convenient: Remote employees have easy access and the cloud makes for easy collaborative and file sharing experiences.
How to make it easier for employees to use mobile devices?
For instance, make it easier for your employees to use mobile devices by deploying mobile-based apps or providing them with VPN remote access. You can also give employees portable WiFi devices so they can have a stable connection no matter where they are.
Why is it important to work remotely?
In the age of the anywhere office, we believe it is crucial to identify and implement the latest remote technologies that will keep your team connected, organized and safe. With 44% of companies not allowing remote work, but employees feeling happier and more productive when given the option to work remotely, employers need to join the movement to attract and retain the best talent. Here are the top technologies transforming the way people work remotely and why your hybrid company should consider integrating them into your processes.
What are some tools to help you collaborate?
Try tools like Google Suite, Slack, and Skype for live idea-sharing and collaborating.
What is unified communication?
Unified communications allow you to integrate interconnected communication channels to simplify access. Using virtual communication tools comes with many benefits:
Is it worth integrating apps for remote workers?
Integrating apps for remote workers takes some planning and thoughtfulness, but the rewards and payoffs are worth it.
What is remote access technology?
A common remote access technology in use today is the IPsec VPN. A piece of software called a VPN client is installed on the end user’s computer and is configured with details about the target network, such as the gateway IP address and a pre-shared security key. Each time the user wants to connect to the corporate network, they start the VPN client, which creates a secure connection to the corporate firewall.
Is DirectAccess going to be widespread?
DirectAccess is not going to gain widespread adoption until the OS licensing requirements are revised and the networking is reworked to be more straightforward. While IPv6 is the future of networking, we currently live and work in an IPv4 world, especially on the LAN (as of May 2014, IPv4 still carried more than 96% of Internet traffic worldwide, according to Google ). Setting up a new remote access technology should not require one or more potentially expensive projects before it can be deployed.
Why is telehealth important in rural areas?
Offering easier access to healthcare in rural areas of the US. In some rural areas of the United States, patients must travel hours to access care, particularly when they need specialized diagnostic and treatment services for complex diseases. Innovative telehealth technology can ease this burden for rural patients.
What is digital maternal care?
Overall, this helps create a more connected maternal care ecosystem in which pregnant moms in remote locations have better access to the care they need. A digital maternal care ecosystem allows doctors, midwives, and community healthcare workers to share patient data, including lab tests and ultrasound data.
Is image guided therapy available in China?
Bringing image-guided therapy to rural communities in China. The geographical divides that make healthcare access a challenge in rural parts of the US and Kenya also exist in China. Like other countries, China’s medical institutions and highly qualified healthcare providers have historically concentrated in cities.
Can a heart attack be treated in a remote area?
For patients in remote areas who experience sudden heart attack or stroke, accessing treatment may mean travelling hours to reach the nearest big-city hospital where clinicians can perform image-guided, minimally invasive procedures. This access barrier can severely decrease the chances of timely care and survival .
How does technology help in field deployment?
Technology will not solve insufficient levels of physical and human resources. Technology decisions to support field deployments often are based, not on the best technology to support the response, but rather on the knowledge and comfort level among staff. The location of the data collection (e.g., from a desk telephone, at a clinic or hospital, or through door-to-door interviews) is a key factor in determining the acceptable technology, as is the acceptance of technology by those under investigation who might be asked to use the instruments or tools directly. If large amounts of data need to be collected manually, not having adequate data entry staff can be a limitation. Necessary data entry staffing is often underestimated, and the data entry process can become a bottleneck. Field team staffing concerns to consider include the following:
Why should public health agencies use modern technology?
Because field investigations evolve rapidly, description of specific technologies or programs to support outbreaks, surveillance, and data collections can become outdated quickly ( Table 5.1 ). Ideally, public health agencies should use modern technologies to facilitate public health practice. In reality, public health agencies may struggle to incorporate new technology, in part because of the lack of resources and availability of savvy informatics staff in the field ( 15 ). Many health departments have restrictive lists of approved software, although exceptions or new approvals can often be expedited during outbreak responses if the need or role the desired software will serve can be demonstrated.
Why do field investigators need to manage noncase data?
Field investigators might need to manage noncase data stored in different systems, requiring field teams to have access or collect and aggregate the information; in other situations, the field team might need to create a means of tracking data from multiple sources. For example,
Why do outbreaks need routine data management?
In an outbreak setting, routine data management often changes because of new stressors or novel circumstances, particularly the need to almost immediately gather data, produce reports, and inform decision makers and the public (see also Chapters 2 and 3 ). To assess population groups at highest risk, geographic extent, and upward or downward trends of disease incidence throughout a confirmed outbreak, investigators can use existing surveillance mechanisms. However, such mechanisms might need to be enhanced; for example, investigators might need to
What are the factors that affect data collection and management during an emergency response?
Important factors that affect data collection and management during an event response—compared with business as usual—include time constraints; immediate pressure to both collect and instantaneously summarize substantial amounts of data, typically in fewer than 24 hours; limited human resources; often insufficient data preparedness infrastructure; and unfamiliar field deployment locations and logistics (see also Chapter 2 ).
What is Remote Access Technology?
Remote access technology refers to any IT toolset used to connect to, access, and control devices, resources, and data stored on a local network from a remote geographic location. This is different from using a cloud solution, as it provides access to an on-premises environment rather than being hosted offsite in a shared environment and available via the internet. This makes remote access crucial for businesses of all sizes which have not moved to a cloud-first model, or which require access to on-premises machines or resources. Three of the most common remote access technologies – Remote Desktop Services, Remote Access Software, and Virtual Private Networks – are examined in detail in this article.
Why do organizations use remote access?
Now more than ever, organizations of all sizes are turning to remote access technology to ensure business operations can continue , even when access to a physical office is limited or impossible. Increasing access to your network to your employees comes with the risk of unauthorized access by cyber-miscreants who may use this as an opportunity to gain access or infect you with ransomware. However, by taking the correct precautions and selecting the right remote access solutions for their specific needs, organizations can minimize their risk while maximizing their ability to work effectively in remote-only or remote-first conditions.
What Is Remote Access Software?
Remote Access Software offers an alternative to RDS and leverages a dedicated software to remotely connect users to an endpoint device from anywhere in the world via the internet. This method of remote access is typically the easiest to implement, as it only requires the user to install the software on the computer to be accessed. This type of remote access is especially useful when most of the organization’s endpoint devices are desktops.
What Is a Virtual Private Network?
A Virtual Private Network (VPN) is a technology which creates a smaller, private network on top of a larger public network – most commonly the internet. By logging into the VPN, users can gain internet-based access to applications that would otherwise only work on local networks. The goal of any client-based VPN solution is to provide remote employees with the same level of access as onsite. However, this is functionally different from an RDS session, as it does not allow full access to an entire desktop, but only specific applications, software, and other resources which the user has been given access to.
What is remote desktop service?
Remote Desktop Services (RDS), also known as Terminal Services, is one of the most common methods used by SMBs to enable remote work. By using RDS, individuals can remotely connect to an endpoint device or server which supports Remote Desktop Protocol (RDP) via a Terminal Server. The connection can be made over a local network or internet connection and gives the user full access to the tools and software installed on the machine they connect to. This method is frequently used by IT departments to remotely access servers, or to provide easy local software access to multiple employees.
What is the most common application used with RDS?
One common business application which is frequently used with RDS is Intuit Quickbooks. Many companies install the application on a central Terminal Server instead of individual computers, allowing multiple users to connect to the software on a remote device via RDS and access the toolset.
Why is remote access important?
For organizations whose employees do require remote access to the network, it is crucial to ensure that all access permissions are properly evaluated before being assigned and properly documented once given. It's as simple and logging those permitted to access remotely, using what method, and for how long.