Under System, click Trusted Platform Module Services. In the details pane, double-click Configure the list of blocked TPM commands. Click Enabled, and then click Show.
Full Answer
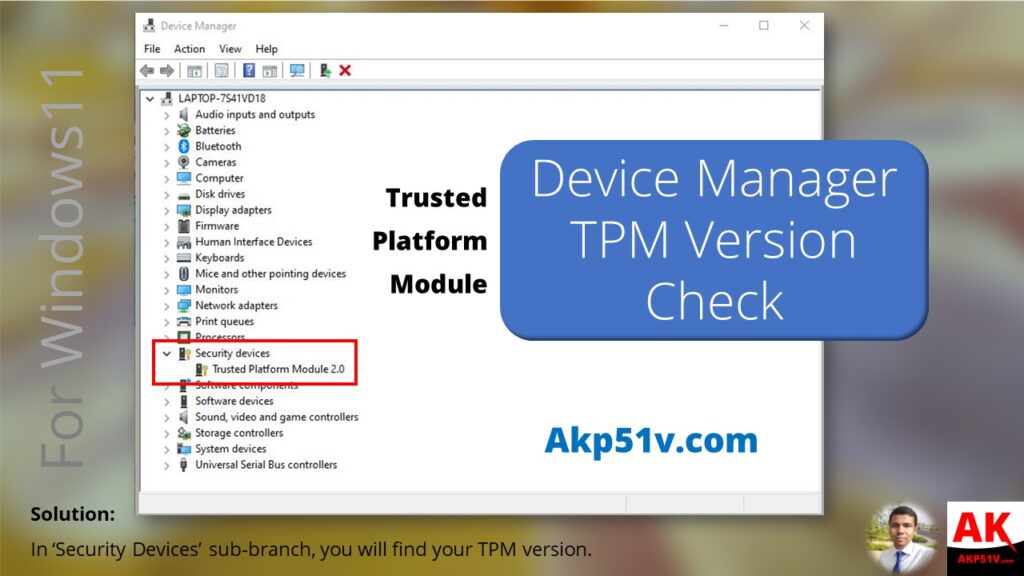
What is a Trusted Platform Module (TPM)?
To enhance security when provisioning certificates for DirectAccess (computer) or Windows 10 Always On VPN (user) it is recommended that private keys be stored on a Trusted Platform Module (TPM) on the client device. A TPM is a dedicated security processor included in nearly all modern computers.
How do I Turn Off the TPM security hardware?
In the Action pane, click Turn TPM Off to display the Turn off the TPM security hardware page. In the Turn off the TPM security hardware dialog box, select a method to enter your owner password and turning off the TPM:
How does a TPM protect the operating system?
The operating system can load and use the keys in the TPM without copying the keys to system memory, where they are vulnerable to malware. The Platform Crypto Provider can also configure keys that a TPM protects so that they are not removable.
How do I restrict workspaces access to trusted devices?
By default, users can access their WorkSpaces from any supported device that is connected to the internet. If your company limits corporate data access to trusted devices (also known as managed devices), you can restrict WorkSpaces access to trusted devices with valid certificates.
What does enabling TPM actually do?
The TPM is a cryptographic module that enhances computer security and privacy. Protecting data through encryption and decryption, protecting authentication credentials, and proving which software is running on a system are basic functionalities associated with computer security.
Should I enable or disable TPM?
Turn on or turn off the TPM (available only with TPM 1.2 with Windows 10, version 1507 and higher) Normally, the TPM is turned on as part of the TPM initialization process. You do not normally need to turn the TPM on or off. However, if necessary you can do so by using the TPM MMC.
Does enabling TPM affect anything?
The TPM cannot do anything without your operating system or programs doing work with it. Just "enabling" the TPM will do absolutely nothing and will not by itself make files inaccessible.
Can TPM lock me out of my computer?
The TPM will lock itself to prevent tampering or malicious attacks. TPM lockout often lasts for a variable amount of time or until the computer is turned off. While the TPM is in lockout mode, it generally returns an error message when it receives commands that require an authorization value.
What happens if you turn off TPM?
If you turn off TPM after Windows 11, you will stop receiving automatic Windows Updates.
Does Windows 10 need TPM?
TPM 2.0 and UEFI firmware is required. Windows 10, version 1507 (End of Life as of May 2017) only supported TPM 2.0 for Credential Guard. Beginning with Windows 10, version 1511, TPM 1.2 and 2.0 are supported. Paired with Windows Defender System Guard, TPM 2.0 provides enhanced security for Credential Guard.
Can I use Windows 11 without TPM?
Windows 11's hardware requirements are mainly about security, even if many people believe they're being too strict. Using an operating system that's not designed to work without a TPM chip or Secure Boot is a risk, although you're likely to get away with it if your device meets most of the requirements.
Does Windows 11 still require TPM?
Windows 11's demands for a TPM 2.0 PC may seem odd, but it's for a good cause. Microsoft hopes to make Windows more secure with the technology, which is why it has set it as a minimum requirement for its new operating system.
When resetting a computer should I clear the TPM?
Warning: clearing erases information stored on TPM. You will lose all created keys and access to data encrypted by these keys. Press ok to clear the tpm.
What causes TPM lockout?
A TPM lockout can occur if a user enters an incorrect PIN too many times. The number of times that a user can enter an incorrect PIN before the TPM lockout is based on the computer manufacturer's specification.
How long does TPM lockout last?
24 hoursTPM lockout is set for 24 hours while the failure tries exceeds the maximum value.
How do I clear my TPM remotely?
Clear TPM status via PowerShell using Clear-TPM To clear TPM status, launch the PowerShell as administrator and run the command clear-tpm . This command resets the TPM. The command uses the owner authorization value stored in the registry instead of specifying a value or using a value in a file.
Does TPM affect performance?
Windows 11 is suffering from more performance issues, with AMD devices once again affected. Commonly reported problems include frequent stuttering and audio glitches, with affected users expressing their frustration. The issues appear to be caused by the TPM 2.0 module, one of Windows 11's key hardware requirements.
Is TPM necessary for Windows 11?
TPM 2.0 is required to run Windows 11, as an important building block for security-related features. TPM 2.0 is used in Windows 11 for a number of features, including Windows Hello for identity protection and BitLocker for data protection. In some cases, PCs that are capable of running TPM 2.0 are not set up to do so.
Can I use Windows 11 without TPM?
Windows 11's hardware requirements are mainly about security, even if many people believe they're being too strict. Using an operating system that's not designed to work without a TPM chip or Secure Boot is a risk, although you're likely to get away with it if your device meets most of the requirements.
Will disabling TPM turn off BitLocker?
It is possible to use BitLocker without TPM, though the option needs to be enabled first. In that case, clearing the TPM will not make a difference.
How to turn off TPM?
To turn off the TPM (TPM 1.2 with Windows 10, version 1507 or 1511 only) Open the TPM MMC (tpm.msc). In the Action pane, click Turn TPM Off to display the Turn off the TPM security hardware page. In the Turn off the TPM security hardware dialog box, select a method to enter your owner password and turning off the TPM:
How to turn on TPM on Windows 10?
To turn on the TPM (TPM 1.2 with Windows 10, version 1507 or 1511 only) Open the TPM MMC ( tpm.msc). In the Action pane, click Turn TPM On to display the Turn on the TPM Security Hardware page. Read the instructions on this page. Click Shutdown (or Restart ), and then follow the UEFI screen prompts.
What version of Windows 10 does TPM not work?
If you have Windows 10, version 1507 or 1511, or Windows 11, the initialization of the TPM cannot complete when your computer has network connection issues and both of the following conditions exist:
What happens when you toggling TPMs?
For example, toggling TPMs will cause BitLocker to enter recovery mode. We strongly recommend that, on systems with two TPMs, one TPM is selected to be used and the selection is not changed.
What does TPM 2.0 mean?
If the TPM is a TPM 2.0 and is not detected by Windows, verify that your computer hardware contains a Unified Extensible Firmware Interface (UEFI) that is Trusted Computing Group-compliant. Also, ensure that in the UEFI settings, the TPM has not been disabled or hidden from the operating system.
How to clear TPM?
Click Security processor details. Click Security processor troubleshooting. Click Clear TPM. You will be prompted to restart the computer. During the restart, you might be prompted by the UEFI to press a button to confirm that you wish to clear the TPM. After the PC restarts, your TPM will be automatically prepared for use by Windows 10.
What happens when Bitlocker is turned back on?
When it is turned back on, Windows will re-initialize it. If you are attempting to set up BitLocker with the TPM, check which TPM driver is installed on the computer. We recommend always using one of the TPM drivers that is provided by Microsoft and is protected with BitLocker.
Why use TPM in Chrome?
Chrome OS uses the TPM to make parallelized attacks and password brute-forcing difficult. One feature and one characteristic of the TPM are exploited here. First, the TPM provides secure key storage for RSA keys. This means that the private key only exists in plain text while it resides on the TPM itself--it can only be stored outside of the TPM in encrypted form. This feature makes parallelizing difficult: decrypt operations involving that key must happen on the TPM itself (unless a vulnerability exists whereby the attacker can obtain the plain-text private key of a TPM-wrapped RSA key). Second, the TPM is a relatively slow device. Private key operations can take over half a second to complete; this provides a level of brute-force protection by effectively throttling the rate at which guesses can be made.
How does TPM work in Chrome?
In normal mode, Chrome OS attempts to establish a TPM owner with a random password, which is generated only after the owner of the Chrome device starts using it. When the owner password is created, there is a period of time in which the user can find out what it is and write it down. After this period, the password is destroyed. However, knowledge of the owner password is not necessary at any point in Chrome OS.
Why is the storage root key unrestricted?
The Storage Root Key (SRK) is unrestricted so that it can be used without the owner password. Since the TPM is used as a generic cryptographic device, and Chrome OS manages clearing the TPM in firmware as necessary, unrestricted use of the SRK is allowable.
How many modes of operation does Chrome have?
The rest of this document first discusses the four different modes of operation of Chrome devices; then it describes how Chrome OS controls TPM ownership; and finally it presents each area of TPM usage in detail.
When is TPM cleared?
On the first power-on after switching to developer mode, the TPM is cleared by the firmware before the OS kernel begins booting. On the first power-on after switching to normal mode, the TPM is also cleared by the firmware before the OS kernel begins booting.
Where are RSA private keys stored?
RSA private keys that are not supported by the TPM and all other PKCS #11 data (certificates, public keys, data objects, TPM-encrypted key blobs, etc.) are encrypted with a symmetric key and stored in /home/chronos/user/.chaps.
Can NVRAM be removed?
This means that physical presence cannot be asserted even by a custom OS. The NVRAM firmware space (see Rollback Prevention below) cannot be removed. The NVRAM kernel space (see Rollback Prevention below) can be removed, but doing so will result in the firmware forcing recovery mode at the next boot.
What is a TPM in Windows 10?
A TPM is a dedicated security processor included in nearly all modern computers. It provides essential hardware protection to ensure the highest levels of integrity for digital certificates and is used to generate, store, and restrict the use of cryptographic keys. It also includes advanced security and protection features such as key isolation, non-exportability, and anti-hammering to prevent brute-force attacks.
What is a TPM?
A TPM is a dedicated security processor included in nearly all modern computers. It provides essential hardware protection to ensure the highest levels of integrity for digital certificates and is used to generate, store, and restrict the use of cryptographic keys. It also includes advanced security and protection features such as key isolation, ...
Can VPN servers accept certificates?
You can really configure the VPN server to only accept certificates with private keys store on a TPM. What you can do is ensure that clients can only use a TPM with this certificate template (as outlined in this post). You can take additional steps to increase assurance that key material is generated and store on a TPM by using key attestation as well.
Does VPN require EC certificate?
I do this all the time and it works perfectly. The only EC certificate that’s required is the certificate on the VPN server. You’ll use RSA certificates on the NPS server and for client authentication (user certificate). If you can’t get it working, reach out to me directly and I’ll provide you with more information.
Does TPM 1.2 need secure boot?
Just TPM 1.2 or later. No need for secure boot.
Can you use TPM with ECDSA?
It does not. If you want to use TPM (recommended) then you must use RSA client authentication certificates. You can still use ECDSA for IPsec though.
Step 1: Create the certificates
This feature requires two types of certificates: root certificates generated by an internal Certificate Authority (CA) and client certificates that chain up to a root certificate.
Step 2: Deploy client certificates to the trusted devices
You must install client certificates on the trusted devices for your users. You can use your preferred solution to install certificates to your fleet of client devices; for example, System Center Configuration Manager (SCCM) or mobile device management (MDM).
Step 3: Configure the restriction
After you have deployed the client certificates on the trusted devices, you can enable restricted access at the directory level. This requires the WorkSpaces client application to validate the certificate on a device before allowing a user to log in to a WorkSpace.
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
How to protect your network from remote access?
You should set up firewalls to restrict access using software or hardware or both.
What is remote computer access?
Many people take their laptops with them to do things like finish a business presentation while waiting for a flight at the airport. But a lot of those laptops may not have bigger, important files on them. You might leave those files at work or at home on your desktop computer.
How to protect remote desktop from hackers?
Use a secure Virtual Private Network (VPN). If you set up a VPN, your remote desktop server won’t be connected directly to the internet. It will only be exposed on your local network, which could leave it less vulnerable to hackers.
What is remote access software?
Remote computer access software lets you access networks and computers remotely. It can enable file sharing. It’s like having a remote control for a computer or system that isn’t near you. You’ll be able to remotely download files and applications from your desktop or another person’s computer onto your laptop or your cell phone. Remote access also gives you control over that remote device
Why is it important to limit the number of users who can log in?
Remote computer access can help businesses, individuals, and families in a variety of ways. But it’s important to make remote access secure .
Why is remote access important?
Remote access software is helpful when you’re in a meeting at another office with your laptop — or telecommuting — and need an important file that’s on your office computer. Remote computer access can help you assist someone in your personal life who might be far away.
What Problems Arise Without a Remote Access Policy?
Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access. Elements such as firewalls, connectivity guidelines, personal use restrictions, and antivirus updates can help IT prevent both malicious and accidental loss and disruption of corporate information assets. The remote access control policies also provide protections for confidentiality, intellectual property, and information compliance.
Why Is a Remote Access Policy Necessary?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business. They can be company owned and secured, personally owned and authorized by a Bring Your Own Device (BYOD) policy, or a combination. Each class of device has its own set of security challenges. According to the National Institute for Standards and Technology’s Guidelines for Managing the Security of Mobile Devices in the Enterprise, “…Security controls available for laptops today are quite different than those available for smartphones, tablets, and other mobile device types.” Since different devices demand different controls, the policy has to detail what is allowed, compliant, and secure. The policy should answer the following questions:
What Is Remote Access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
What is VPN policy?
Policies for VPN remote access can be standardized. These policies “shore up” and prevent the use of rogue devices and access by non-authorized users , including the worker's family members or housemates. The policy also enforces proper email protocols to protect information from being sent through unsecured or untrusted sources, and also provides rules that limit or prohibit split tunnel configurations that allow mobile users to access both secure and unsecure networks simultaneously.
What is telecommuting?
“Telecommuting,” a term coined in the 1970s, has experienced explosive growth in today’s era of mobile connectivity. Now called distributed offices, remote work, telework, mobile work, smart work, and work shifting, many people are finding flexibility and increased productivity conducting business away from a centralized office environment. Researchers have long studied the benefits of remote work - from the successes that remote work had on traffic reduction during the 1984 Los Angeles Olympics to the 2016 findings by a Gallup survey on the increased hours for remote work.
What percentage of people work remotely?
According to research conducted by Gallup, 43 percent of workers in the U.S. worked remotely at least some of the time in 2016. Remote workers report higher job satisfaction and flexibility, experience fewer distractions and interruptions, and are more productive. Companies experience less absenteeism, less stress on office accommodations, and realize greater employee retention. A recent New York Times article found that finance, insurance, real estate, and transportation were most likely to have and support remote work (retail and education were least likely candidates). The trend is only increasing: the 2016 Gallup poll also found that those who work remotely log more hours away from the office than was reported in their 2012 findings. Not only are people logging more hours, but remote workers are saving money when it comes to commuting costs and businesses are saving on office space expenses.
Why is remote access important?
Software organizations where development engineers need to connect across multiple locations, small organizations lacking office-space, and large, enterprise organizations all want to offer the most flexible work options in order to attract high-ranking candidates and reap the rewards of having such a policy.
What is the role of organizations in enabling secure and direct access to business applications?
Organizations need to enable secure and direct access to business applications for a diverse set of users and devices, but enforcing consistent security policies across managed devices, bringing your own devices (BYOD) and third-party (contractor...
What is a trusted device in Duo?
With Duo’s Trusted Devices and Networks, you can give your users faster access without compromising security. Similar to a “Remember my computer” option, you can designate users’ devices and networks as trusted to allow your users to log in without completing the two-factor process each time.
What is Duo visibility?
To truly protect every application, visibility is critical. Duo provides insight into every device that's accessing your information — whether it's a personal device or corporate-owned. You can access that information easily and at any time with extensive user and device reports, available through Duo’s Admin Panel.
Can Duo protect against malware?
You can also protect against vulnerabilities that exploit known software flaws on your users’ risky devices to install malware or get access to company applications by automatically blocking them with Duo’s Endpoint Remediation.
Can you trust your computer after initial authentication?
Trust your users’ computers after initial authentication, and let users log into your applications without completing two-factor authentication each time.
