Who can use the Sedi-SSL VPN service?
USER RESPONSIBILITIES Installation and Usage a) Only authorized personnel may use the SSL VPN service to access the SEDI website/portal on the DHHS network. b) The SEDI - SSL VPN service is for work-related activities only.
What is an remote access VPN Server?
Remote-access VPN servers allow off-site users to tunnel into protected networks, making these entry points vulnerable to exploitation by malicious cyber actors. Arbitrary reads of sensitive data (e.g., configurations, credentials, keys) from the device
How do I get VDI access to SSL VPN?
You will need to request access to your agency's VDI pool. Please contact the Enterprise Service Desk or your local Service Desk and request access. The following Agencies currently have access to SSL VPN which is accessed with the directions below.
What is SSL VPN (SSL VPN)?
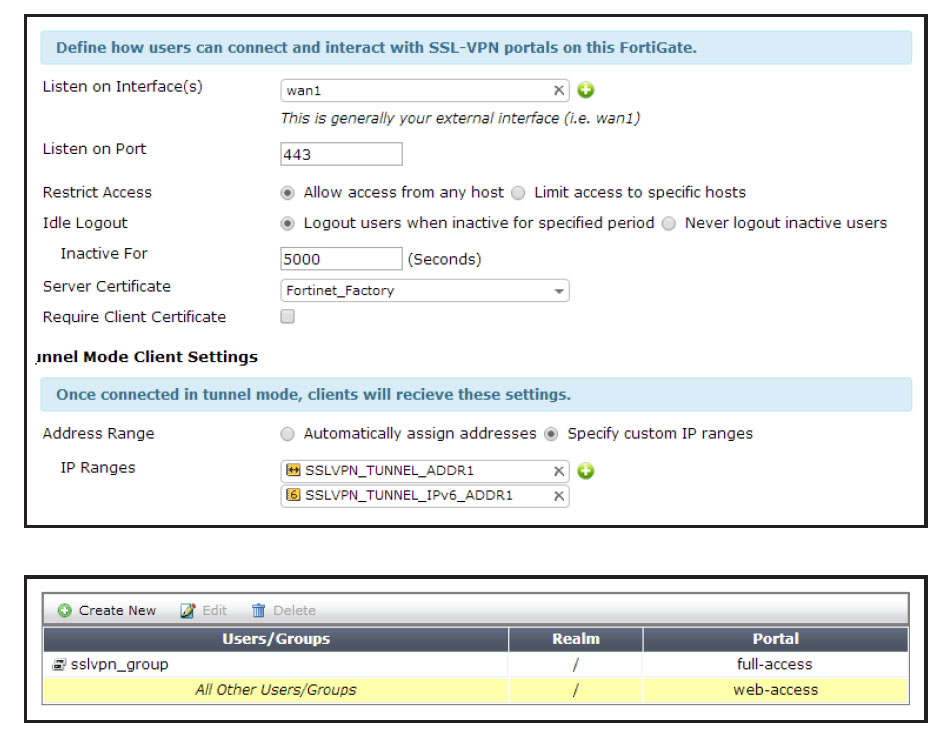
This guide is provided to introduce you to the County of Sacramento’s Secure Socket Layer (SSL) Virtual Private Networking (VPN) solution, otherwise known as SSL VPN. SSL VPN is a “clientless” solution in that it does not require a formal client installation as past County VPN solutions have required.
What is ITS working remotely?
To work remotely is to access your agency's network while you are away from your primary workstation. This site contains resources and common troubleshooting tips to support individuals who may be working remotely.
What is RSA SecurID?
RSA SecurID is a multi-factor authentication technology that is used to protect network services. The RSA SecurID authentication mechanism consists of an assigned hardware or software "token" that generates a dynamic authentication number code at fixed intervals. Users provide the unique number code when logging into a protected service from any network outside the State network.
What is RSA token?
An activated RSA SecurID authentication token will enable you to access programs such as the Outlook Web Application (OWA), Office 365 (O365) products including SharePoint, and Virtual Desktop Infrastructure (VDI).
What to do if you enter too many passcodes?
After entering too many incorrect passcodes, you may be required to enter a next Token code. If using a Soft Token, wait and then enter the next available passcode shown. If using a Hard Token, wait and then enter the next available Token code shown (random 6 digits). Do NOT enter PIN + Token code.
What is ITSM self service portal?
The ITSM Self-Service Portal can be used to check the status of a ticket or request assistance. Please click the link above and sign into the self-service portal.
Can you work remotely with an agency?
Your Agency may or may not provide you with any additional hardware for the sole purpose of working remotely. Subject to your agency's discretion, employees who have been approved to work remotely may be permitted to use their personal devices, such as a personal desktop computer, laptop, tablet, and/or smartphone.
Can I use a VPN to connect to my work computer?
Yes. The connections are encrypted which prevents data from being intercepted. The use of SSL VPN, VDI, or OWA only grants your personal computer limited access to remote connect to your work computer, the VDI system, or Microsoft Office and does not allow your work computer to access your personal computer.
How to deploy SSL VPN?
The five phases of the recommended approach are as follows: 1. Identify Requirements. Identify the requirements for remote access and determine how they can best be met. 2. Design the Solution. Make design decisions in five areas: access control, endpoint security, authentication methods, architecture, and cryptography policy. 3. Implement and Test a Prototype. Test a prototype of the designed solution in a laboratory, test, or production environment to identify any potential issues. 4. Deploy the Solution. Gradually deploy the SSL VPN solution throughout the enterprise, beginning with a pilot program. 5. Manage the Solution. Maintain the SSL VPN components and resolve operational issues. Repeat the planning and implementation process when significant changes need to be incorporated into the solution.
What is VPN in security?
Secure Sockets Layer (SSL) virtual private networks (VPN) provide secure remote access to an organization’s resources. A VPN is a virtual network, built on top of existing physical networks, that can provide a secure communications mechanism for data and other information transmitted between two endpoints.
What is section 2 of the VPN?
The remainder of this document is organized into the following six major sections: Section 2 provides a general introduction to network and transport layer security. Section 3 gives describes the fundamentals of SSL VPNs and their services and features. Section 4 explores in depth each of the SSL VPN planning and implementation phases. Section 5 provides a consolidated list of recommended practices for SSL VPN deployment in terms of the system development life cycle approach. 1-1
How are VPN tunnels different from SSL tunnels?
The tunnels are quite different in that SSL/VPN tunnels are usually created in SSL using a non-standard tunneling method, while IPsec tunnels are created with methods described in the IPsec standard. The tunneling in an SSL tunnel VPN allows a wide variety of protocols and applications to be run through it.
Where to find IPsec information?
1Detailed information on the IPsec components may be found in NIST Special Publication (SP) 800-77, Guide to IPsec VPNs, available from http://csrc.nist.gov/publications/nistpubs/.
What are security controls in TCP/IP?
Security controls exist for network communications at each layer of the TCP/IP model. As previously explained, data is passed from the highest to the lowest layer, with each layer adding more information. Because of this, a security control at a higher layer cannot provide protection for lower layers, because the lower layers perform functions of which the higher layers are not aware. Security controls that are available at each layer include: Application Layer. Separate controls must be established for each application. For example, if an application needs to protect sensitive data sent across networks, the application may need to be 2-1
Do VPNs need FIPS?
Federal agencies deploying SSL VPNs must configure them to only allow FIPS-compliant cryptographic algorithms, cipher suites, and versions of SSL.
