The first is through a VPN (virtual private network) that allows the user access to remotely log in easily and quickly. The other way is through a dial up remote connection; this way is a bit easier to set up but can become very costly in the long run.
What is the difference between VPN and RDP?
VPNs provide encrypted access between a remote user and your network. With desktop sharing software, you can gain access to a remote computer—like a mirror image of your computer for use at home. With RDP, you can access your files and use capabilities on that remote computer. A VPN only provides access to the network.
What is a remote-access VPN?
With remote-access VPNs, the device of the remote user is in charge of encrypting and decrypting data that is either sent or received. A remote-access VPN requires a NAS (network access server), or VPN gateway, to authenticate the credentials of any device attempting to sign into the VPN.
What is the difference between site to site VPN and remote access VPN?
Both Site to site VPN and Remote access VPN are the types of VPN which stands for Virtual Private Network. Site-to-Site VPN is also known as Router-to-Router VPN. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer.
What is the difference between roaming remote access VPN and DirectAccess?
However, there are some significant differences between the roaming remote access VPN client and the DirectAccess client: The DirectAccess client is always managed.
What is the difference between remote access and VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
Which is better VPN or RDP?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
What is dial-up remote access?
What is Remote Access? Remote access is the ability to communicate with a computer or network that is located some distance away over a dial-up connection. Remote access was the term originally used to describe connecting users to the Internet using a dial-up connection over traditional POTS or ISDN telephone lines.
What is dial-up VPN?
A virtual private dial-up network (VPDN) is a type of VPN that provides remote access services and capabilities to private networks' dial-in service in addition to a shared infrastructure.
Why would you use RDS instead of VPN?
Unlike VPN, RDP typically enables users to access applications and files on any device, at any time, over any type of connection. The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
Who still uses dial-up?
Over a quarter million Americans still use dial-up internet, and just over 8 million rely on satellite internet. That so many people still use dial-up is concerning.
Which protocol is used for dial-up and create VPN?
Some common remote access and virtual private network (VPN) tunneling protocols include: PPP. Point-to-Point Protocol is used to create dial-up connections between a dial-up client and a remote access server, or between a dial-up client and an Internet Service Provider (ISP).
What are the main disadvantages of dial-up modems?
DisadvantagesIt has slow transfer speeds and so it can take very long time to download or upload files.You cannot use the phone while using the internet.It is too slow to successfully view video files.
How do I get rid of dial-up and VPN?
Delete and Recreate Manual Dial-Up Networking (DUN) Connections - Windows® 10Close any open apps then ensure the wireless device is inserted/connected to the computer.Tap or click the. ... Tap or click the. ... Tap or click. ... Tap or click. ... From the Dial-up tab, tap or click. ... Right-click the connection you wish to remove then click.More items...
What is Fortissl used for?
FortiClient is software that is designed for VPN capability along with security on your network from malware attacks. This platform also includes web filtering, content filtering and web security. Even this platform acts as an antivirus and also provide endpoint security.
What is dial-up in laptop?
Laptops have been slower to make the transition.\nRare today is the laptop that features a built-in dialup modem. If your laptop sports one, you can use it to dial into the Internet or dial into any computer with a dedicated phone line.
Is RDP secure without VPN?
Remote Desktop Protocol (RDP) Integrated in BeyondTrust Establishing remote desktop connections to computers on remote networks usually requires VPN tunneling, port-forwarding, and firewall configurations that compromise security - such as opening the default listening port, TCP 3389.
Do you need a VPN to use RDP?
By default, Windows Remote Desktop will only work on your local network. To access Remote Desktop over the Internet, you'll need to use a VPN or forward ports on your router.
Does VPN work with RDP?
With Remote Desktop, you remotely control another PC and automatically access its LAN. But you can use a VPN and Remote Desktop at the same time to increase your security and privacy. Is RDP safe with VPN? Yes, RDP is safer when using a VPN to encrypt your data traffic.
Can I use RDP and VPN at the same time?
There's nothing wrong with VPN connection to the network then RDP to LAN while on the VPN. That's very common as it adds security. This person is a verified professional. Verify your account to enable IT peers to see that you are a professional.
What is VPN in telecommunications?
Introduction A virtual private network (VPN) is a system that utilizes public telecommunication infrastructure, such as the Internet, to offer remote offices or single users with safe access to their institution's network ( Collins, Keeley & Waye,2000). A virtual private network can be compared to an expensive system of held or rented lines that can only be utilized by a single organization. The aim of a VPN is to offer the institution with similar capabilities, but at very low costs (Hulsebosch
What is Allied too?
of the area where access to Internet has been made or where the transaction has finally taken place. Allied too is the issue where the income has been generated and who should tax such income. There are still no definite answers to these issues. 1.1.5 Security of i-banking transactions is one of the most important areas of concerns to the regulators. Security Issues include questions of adopting internationally accepted state-of-the art minimum technology standards for access control, encryption
Why do vendors need remote access?
And though there are many reasons a vendor might need remote access, mostly this is to provide technical support. Because of this growing requirement, there have been many tools developed to enable this activity. Some have evolved from existing tools, others have been built precisely to allow vendors onto networks.
What are the downsides of having full access to a machine on the network?
There are also security downsides to having full access to a machine on the network, including access to local files as well as network resources with the full permissions of that user. There may be sensitive files on the machine that could be viewed if the attendant isn’t watching closely. The host could also be used as a beachhead to do reconnaissance or even attack other computers on the network. This is a frequent tactic of hackers, where they get low-level access on a single network node, but expand out from there by finding other vulnerable machines or services visible on the network.
What is desktop sharing?
Desktop sharing evolved out of the shortcomings of VPNs for remote support. Additional capabilities were needed to be able to access any or all of an enterprise’s desktops without needing credentials on each machine. Most remote desktop sharing tools provide an encrypted tunnel much like VPNs, usually using SSL or similar methods, ...
What happens if a VPN is stolen?
And if a user’s credentials are stolen or coopted, the amount of damage that can be caused is greatly increased by a VPN’s broad network access.
What is a network extender?
This “network extender” was intended to be used over a public network, such as the internet, and uses encryption to keep the session safe and secure. The technology operates at the network level and typically provides a user with access to servers and machines that are only accessible within the corporate firewall.
Is remote desktop sharing better than VPN?
However, while remote desktop sharing offers more functionality for the purpose of support than VPNs, it also has shortcomings of its own. It only provides access to the desktop and is not as useful for enterprise support, such as database or server support or those using a command line. While a VPN sometimes offers too much access, ...
Is VPN a third party?
However, for a third-party needing access to provide support, a VPN is merely the first step. Additional layers of access would need to be added in order for them to access the servers or hosts to be supported. For instance, if you will be supporting a server, you need credentials on that server and the proper rights-levels to do the work. This is, at minimum, a two-step process (you might need credentials on multiple hosts) which allows for human error and active maliciousness to cause issues or problems. On the converse side, they may be provided with too much access and that access may not be tracked adequately. Once the job is done and the contract’s terminated, credentials and VPN access must be removed in a timely manner. If not, this provides a window of vulnerability into those services and devices. And if a user’s credentials are stolen or co-opted, the amount of damage that can be caused is greatly increased by a VPN’s broad network access.
What is a Remote-Access VPN?
Remote-access VPNs are more closely related to the consumer VPNs we use to protect our personal identities and data.
What is a Site-to-Site VPN?
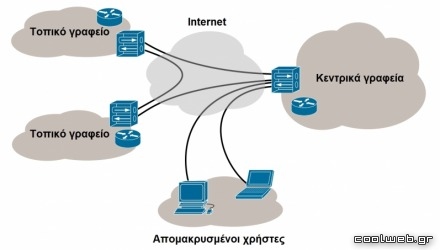
Whereas remote-access VPNs securely connect individual devices to a remote LAN, site-to-site VPNs securely connect two or more LANs in different physical locations. Site-to-site VPNs use the public internet to extend your company’s network across multiple office locations.
What is MPLS VPN?
Unlike internet-based site-to-site site VPNs in which a company uses its own infrastructure, MPLS VPN uses proprietary infrastructure owned by the VPN. This MPLS network, including its cloud, functions as the tunnel by which a company creates virtual connections between office sites.
What is a VPN gateway?
The VPN gateway encrypts the incoming traffic (to you) which is then received by your VPN client. Remote-access VPNs are not just a way for out-of-office employees to remotely access your company’s private network.
How does a VPN gateway work?
The VPN gateway then decrypts your traffic and relays the data to the LAN. Not only is all traffic sent through the virtual tunnel secured, but any traffic you receive from the local network (or its servers) also travels through this tunnel in reverse and is secured.
Why do businesses use VPNs?
VPNs were first used by businesses to extend private networks over the public internet, allowing remote workers to connect to a company’s LAN (local area network).
How much does a VPN save?
Despite the VPN’s substantial set-up and maintenance costs, it will save the company hundreds of thousands of dollars per year when compared to the cost of dedicated connections for all locations.
Question
We found we were at the limit of Windows SBS and have begun the process to migrate to Windows Server 2012 R2.
All replies
I assume that the RD Web Access role is installed on OWA server, if that's the case, please check TP's suggestions within this thread below:
What is remote access VPN?
Remote access VPN. 1. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. In remote access VPN, Individual users are connected to the private network. 2.
What is site to site VPN?
Site-to-Site VPN is also known as Router-to-Router VPN. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. Multiple users are not allowed in Site-to-Site VPN.
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What are the advantages of remote access VPN?
Another advantage of remote access VPNs is that they provide companies with an affordable way to secure data sent by offsite employees. The initial investment needed to set up a remote access VPN is minimal and they can easily be scaled as a company grows and this is especially true if a VPN service provider is used.
Why is VPN important for business?
The most important benefit though is data security. When an offsite employee sends data through a VPN, it is encrypted, so even if a hacker is able to intercept that data, they won’t be able to use it. This is particularly important if an employee accesses their companies’ network using public Wi-Fi while traveling because traffic sent over these networks is usually not encrypted.
What is a network access server?
A network access server could be a dedicated server or it might be a software application running on a shared server. Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.
Why do businesses use VPNs?
Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
Is it good to work remotely?
The ability to work remotely is one of the perks that many businesses offer employees to help sweeten the deal. The recent coronavirus outbreak has only exacerbated that, leading many more organizations to allow their employees to work remotely. While this is good news for employees, it could end up causing a great deal of disruption to organizations that aren’t prepared and one way to do so is to look into remote access VPN solutions.
What is dial up remote access?
Dial-up remote access requires only plain old telephone service (POTS) or ISDN lines, and allows users to make connections to many resources, from corporate headquarters, to bulletin board services, to the Internet/Intranet. Dial-up remote access also allows travelling or telecommuting remote users to connect to their network as if they were located on-site.
What is remote access server?
A remote access server that can function as a router can be useful as an intermediate point between a network and an ISP to act as a firewall, particularly if that device can support multiple filtering options. By applying various filters to packets arriving on a dial-up line, a network manager can ensure that no unsolicited or unregulated packet traffic can enter the network via those lines.
What is remote node access?
Remote node network access allows remote users to connect to a network using a modem. Remote node users are typically mobile or telecommuter users who run a remote client software package on their PC or workstation giving them network access through a dial-up server. Remote node access to the network has become easier because of the TCP/IP or IPX support that's been built into Windows95 and other operating systems. Most of the current demand for such services involves either IP (Unix) or IPX (Novell NetWare) protocols.
Why is modem pooling important?
For the network manager, modem pooling provides the added conveniences of easy maintenance because all modems are in one location, and easy management as remote access servers typically have more robust network management than modems. Protocols such as IP and IPX support the sharing of modem resources through software tools available under a host or network operating system ( the remote access device that supports these applications provides ever greater value. INT14 support under IPX and redirection of serial port output to a communications port using IP and IPX protocols are essential features that this type of software should support.
Why is remote control important?
Remote control is useful when a user needs a lot of processing power or number crunching capability, because only the serial information sent to the keyboard, mouse and display need pass over the dial-up link. The drawback of this approach is that the user can only view the information and cannot transfer files or obtain data to be processed on their remote system. Remote control is more frequently used with the IPX (NetWare) protocol; IP users can use terminal servers to achieve the same result when a multi-user host is available.
What is the key attribute of remote access?
No matter what remote access strategy you plan to implement, one key attribute that requires the greatest attention, is that of providing controlled access to your important/proprietary data. When a strategy for networking involves dial-up technology, issues of network security become very important. Each modem is a potential gateway for uninvited users, either by chance or malicious intent, to gain access to the attached network.
What is routing in network?
When a connection is made to another network, routing is the key to this type of functionality ( when a user on the network requests connection to a resource available only on another network, the remote access device recognises the need to dial another network and then automatically dials up the appropriate remote site according to a stored profile. Once the connection has been established, the remote access device will monitor the connection according to the parameters established by the network manager.
Why is DirectAccess better than VPN?
When you compare the DirectAccess client to the remote access VPN client, the DirectAccess client can present a much lower threat profile than the VPN client, because the DirectAccess client is always within the command and control of corporate IT. This is in stark contrast to the roaming remote access VPN clients that may or may not connect to the corporate network for long periods of time, which leads to configuration entropy that can significantly increase the risk of system compromise. In addition, the mitigations mentioned above that apply to the remote access VPN client can also be used with the DirectAccess client.
What is the difference between a roaming VPN and a bolted in VPN?
The key difference between the roaming VPN client and the "bolted-in" corpnet client is that the VPN client is not always managed, and that it is exposed to a greater number of programmatic and physical threats. However, there are ways to mitigate some of these threats and many companies have already introduced methods to do so, such as the following:
Why is roaming VPN bad?
The roaming VPN client falls further and further out of your defined security compliance configuration and the problem becomes magnified because the machine is connected to a number of networks of low and unknown trust. These unmanaged or poorly managed networks might be full of network worms and the computer might be exposed to users who have physical or logical access to the computer and who would otherwise not have access to the computer if it were to never leave the corpnet.
How many tunnels does DirectAccess use?
The DirectAccess client uses two separate tunnels to connect. The DirectAccess client has access only to the management and configuration infrastructure through the first tunnel. General network access isn't available until the user logs on and creates the infrastructure tunnel.
Is DirectAccess always managed?
The DirectAccess client is always managed. As long as the DirectAccess client computer is turned on and connected to the Internet, the DirectAccess client will have connectivity with management servers that keep the DirectAccess client within security configuration compliance.
Is DirectAccess a VPN?
Here is where we reach the point of making a critical distinction: when comparing the roaming remote access VPN client to the DirectAccess client, all the evidence points to the fact that the DirectAccess client poses a lower threat profile. Comparisons between the DirectAccess client and the "bolted-in" corpnet client are probably of academic interest only - since few organizations have these "bolted-in" clients anymore and most firms are enabling users with VPN access to reach corpnet resources,and both VPN clients and DirectAccess clients will move in and out of the corporate network, making the division between the "corpnet client" and the "remote client" virtually meaningless from a security perspective.
What Is A Remote-Access VPN?
What Is A Site-To-Site VPN?
- Whereas remote-access VPNs securely connect individual devices to a remote LAN, site-to-site VPNs securely connect two or more LANs in different physical locations. Site-to-site VPNs use the public internet to extend your company’s network across multiple office locations. There are two common types of site-to-site VPNs: Intranet-based and Extranet...
Which Is Right For Me?
- Choosing between a remote-access VPN and a site-to-site VPN depends entirely on your needs. If you’re just looking for a personal solution to keep yourself safe and anonymous while using the internet, then a remote-access VPN is the perfect choice for you. If you’re choosing a VPN for your business, you can’t overlook the significant financial and human resource demands required by …
Conclusion
- A remote-access VPN allows a device to securely communicate with your company’s private LANno matter where in the world the device or the LAN may be. A site-to-site VPN, however, securely bridges your various LANs – no matter where they are– to allow employees at all LAN locations secure access to the resources of the complete network. A site-to-site VPN certainly p…
Further Reading
- Check out the best VPNs according to Reddit. Find great savings on VPN plans with our VPN deals and coupons. Learn how to secure your business with The Complete Cybersecurity Guide for Small Businesses.